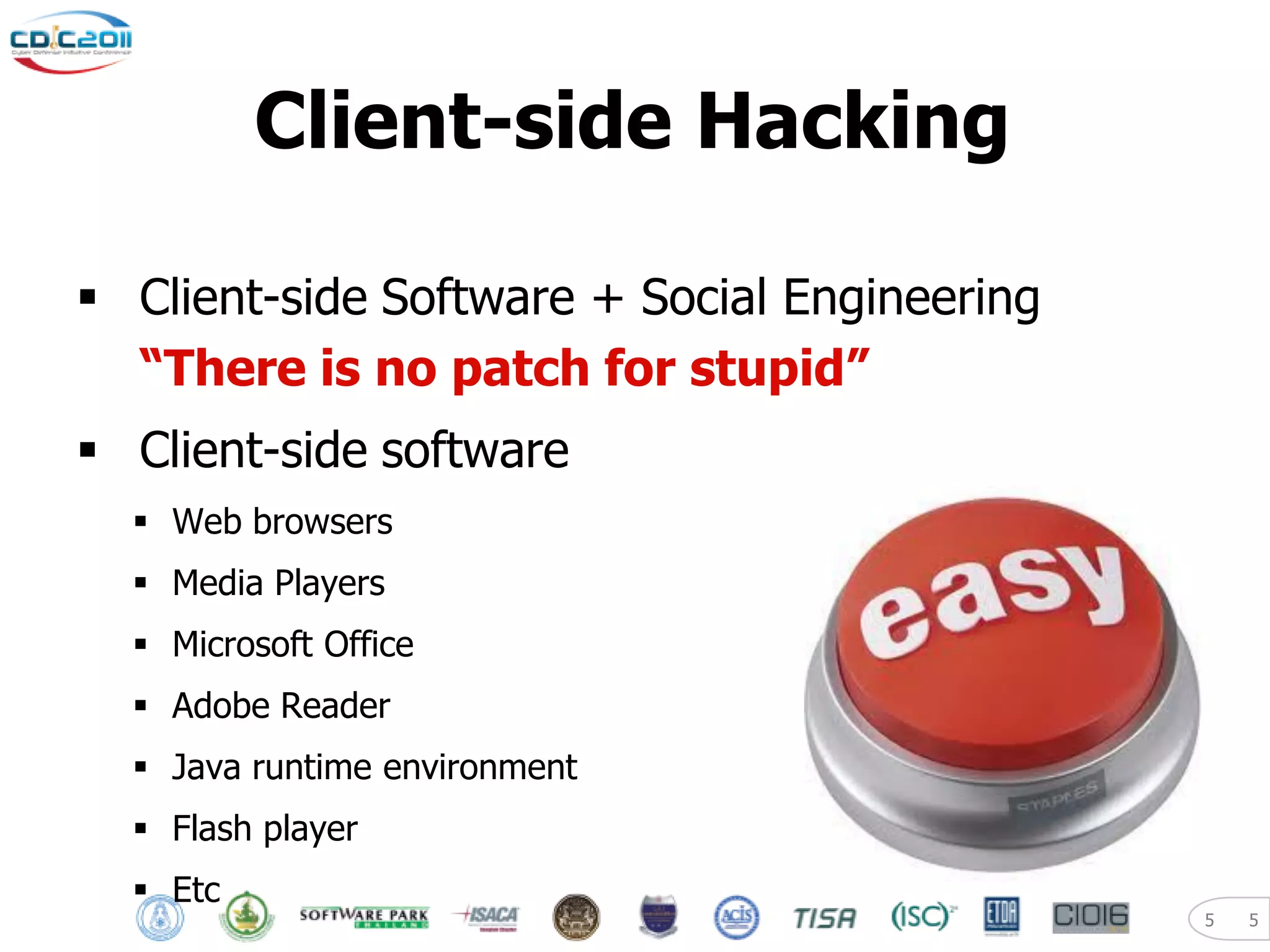
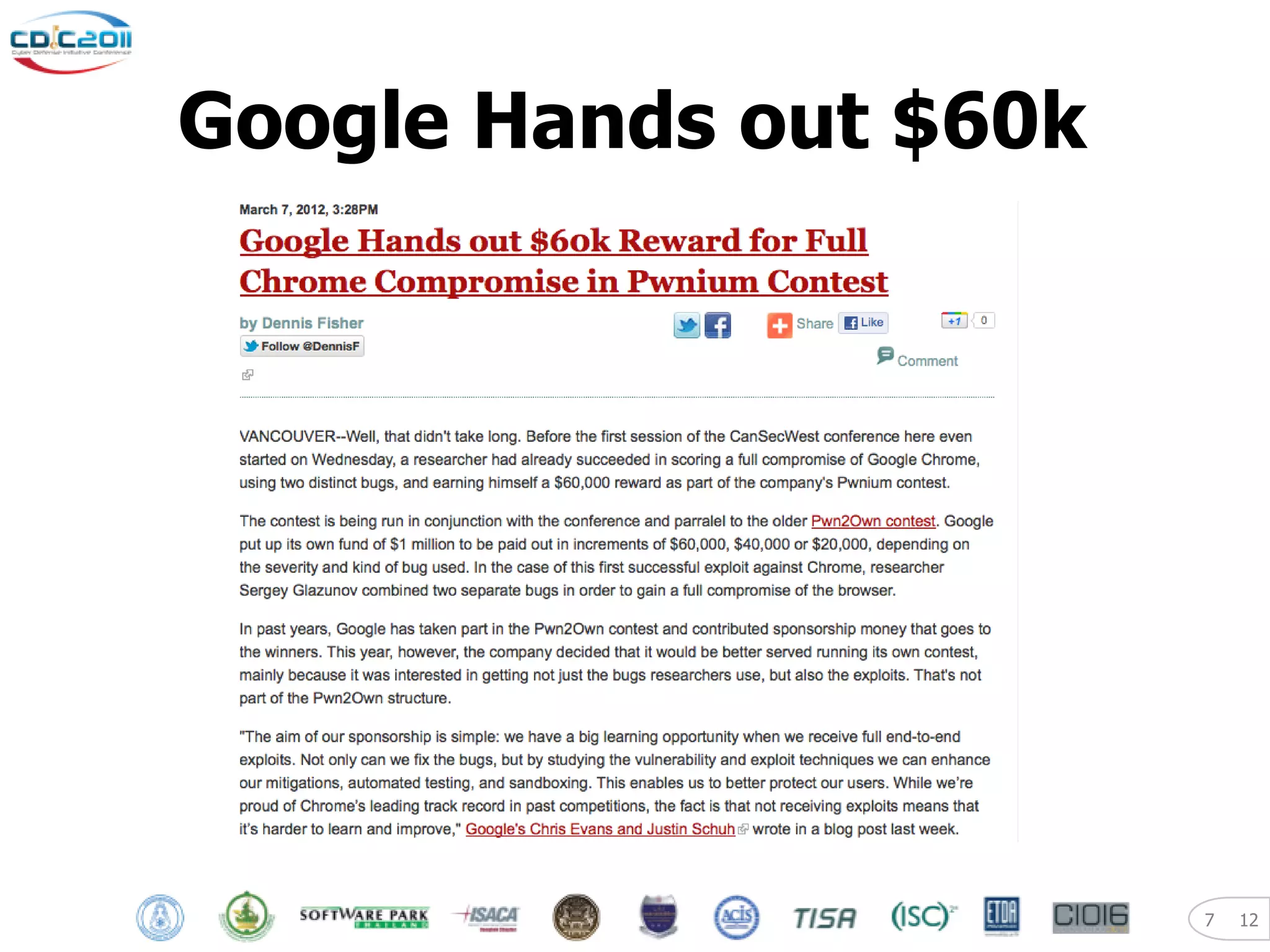
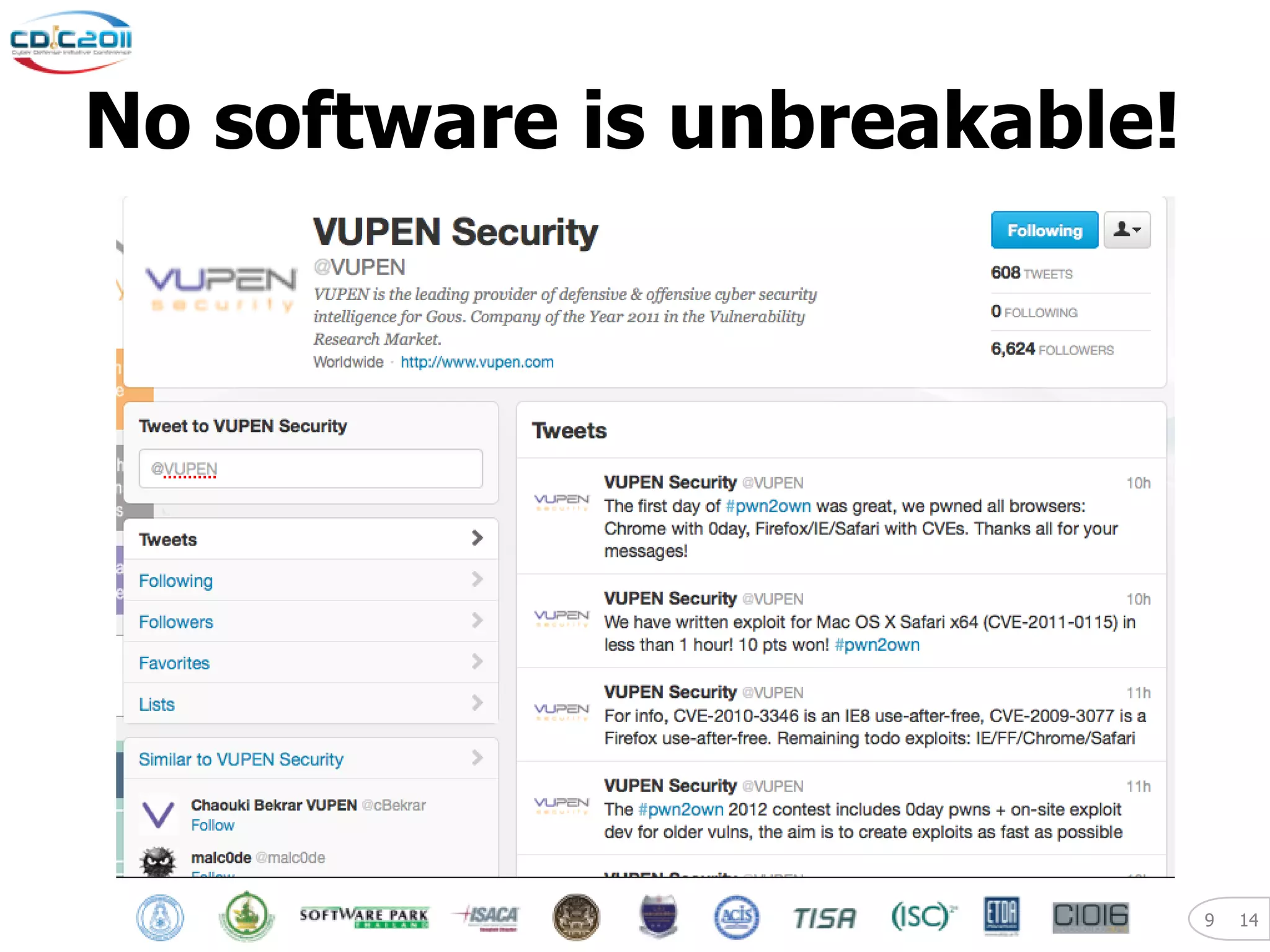
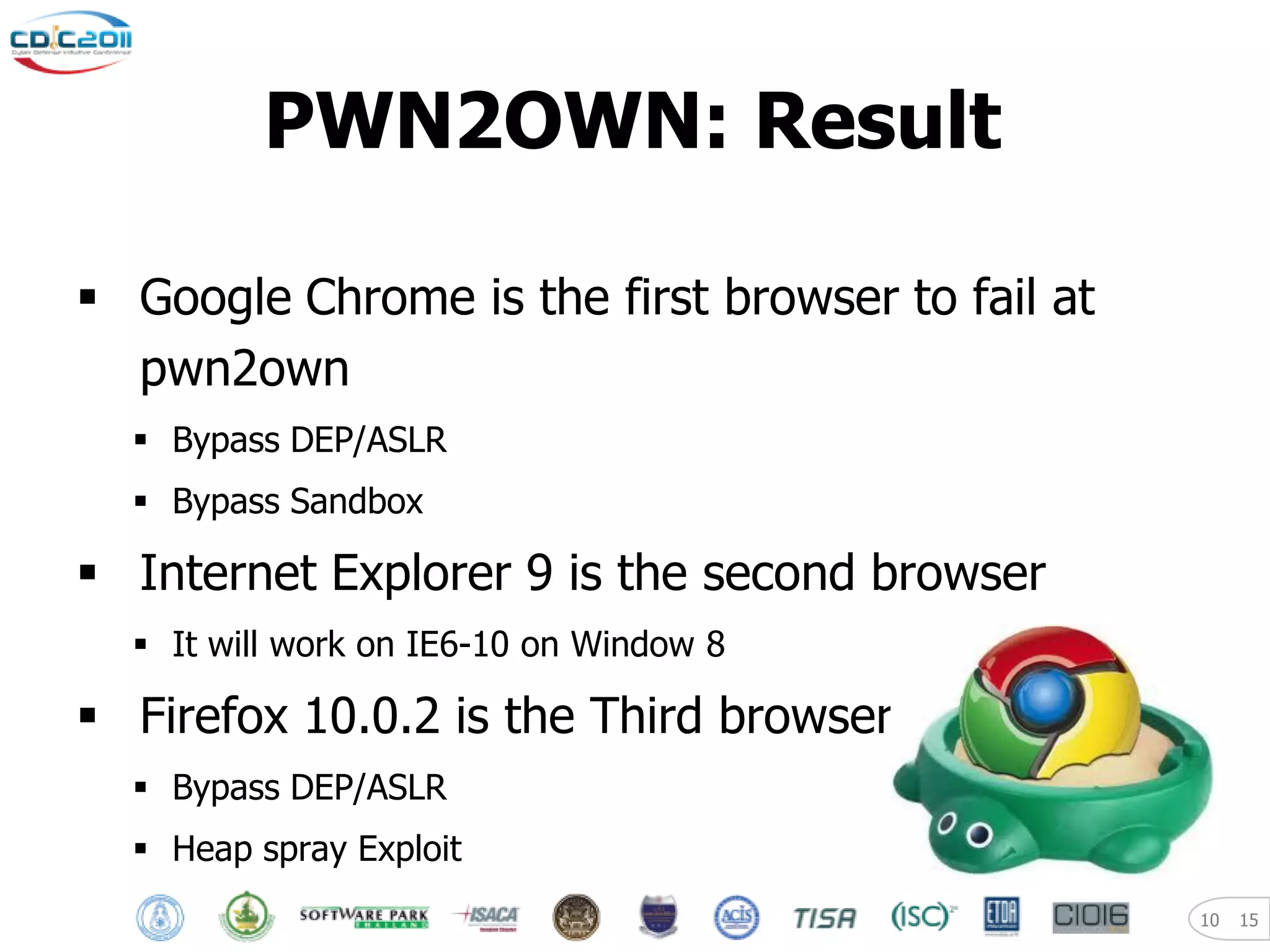
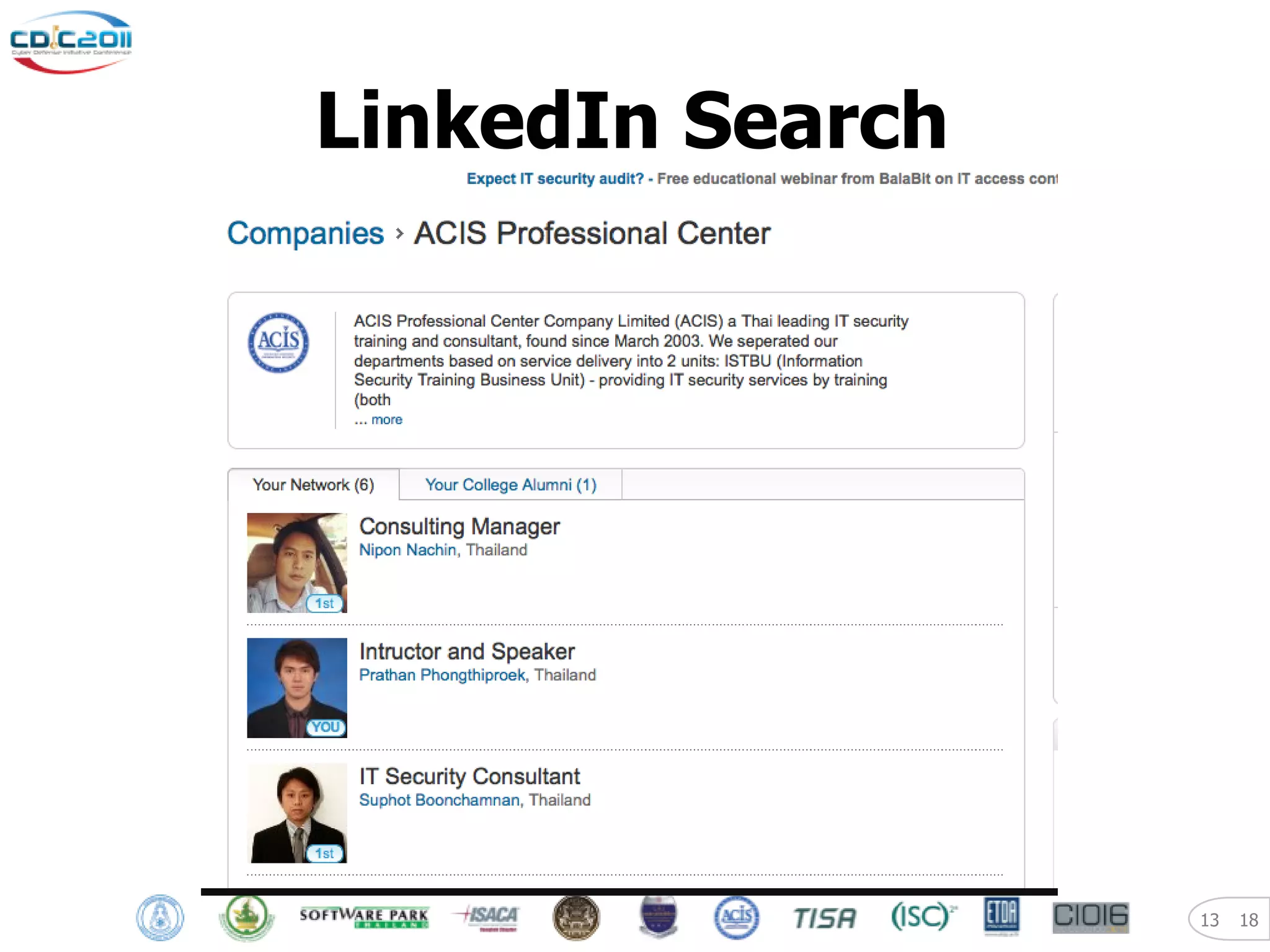
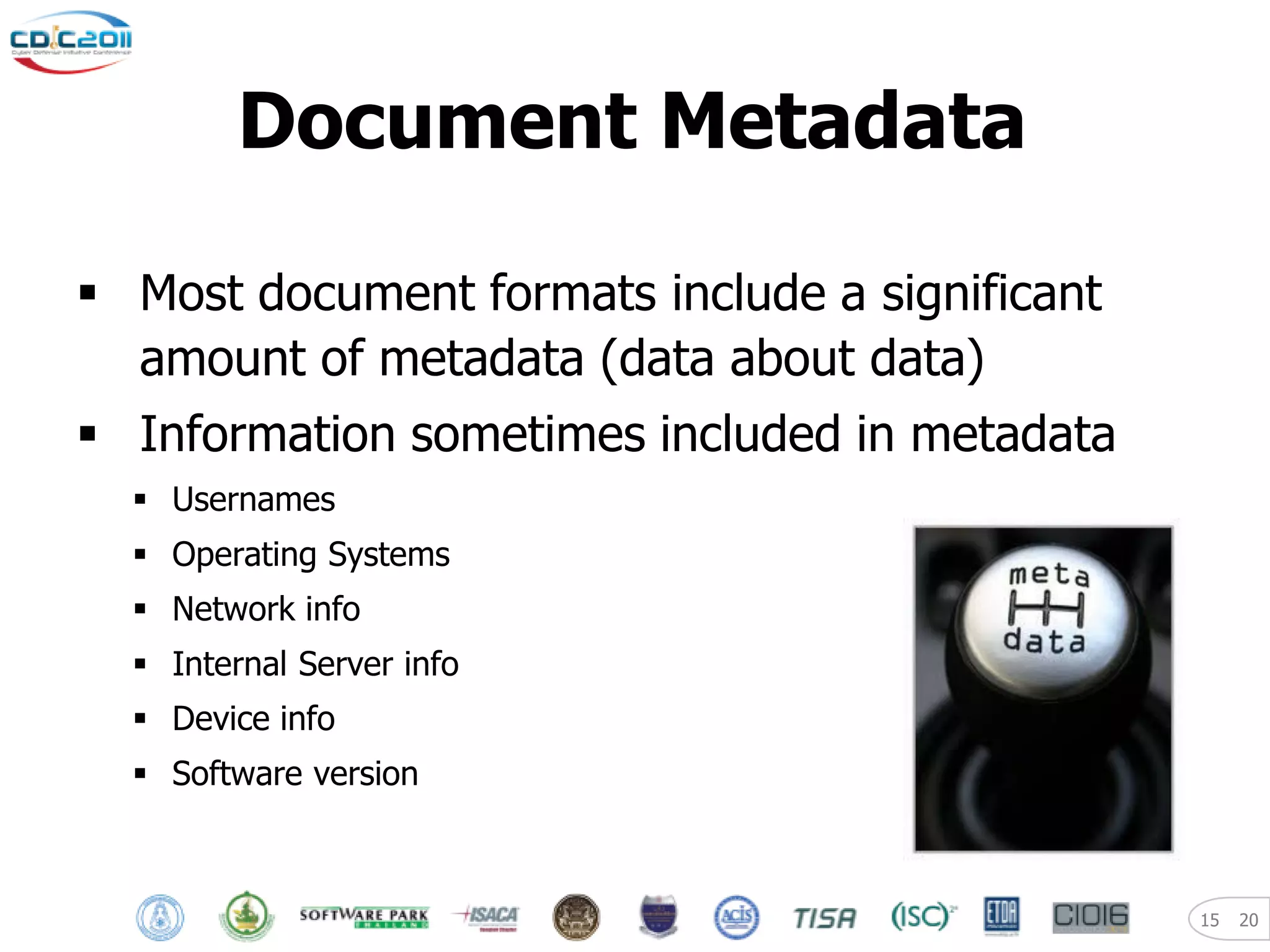
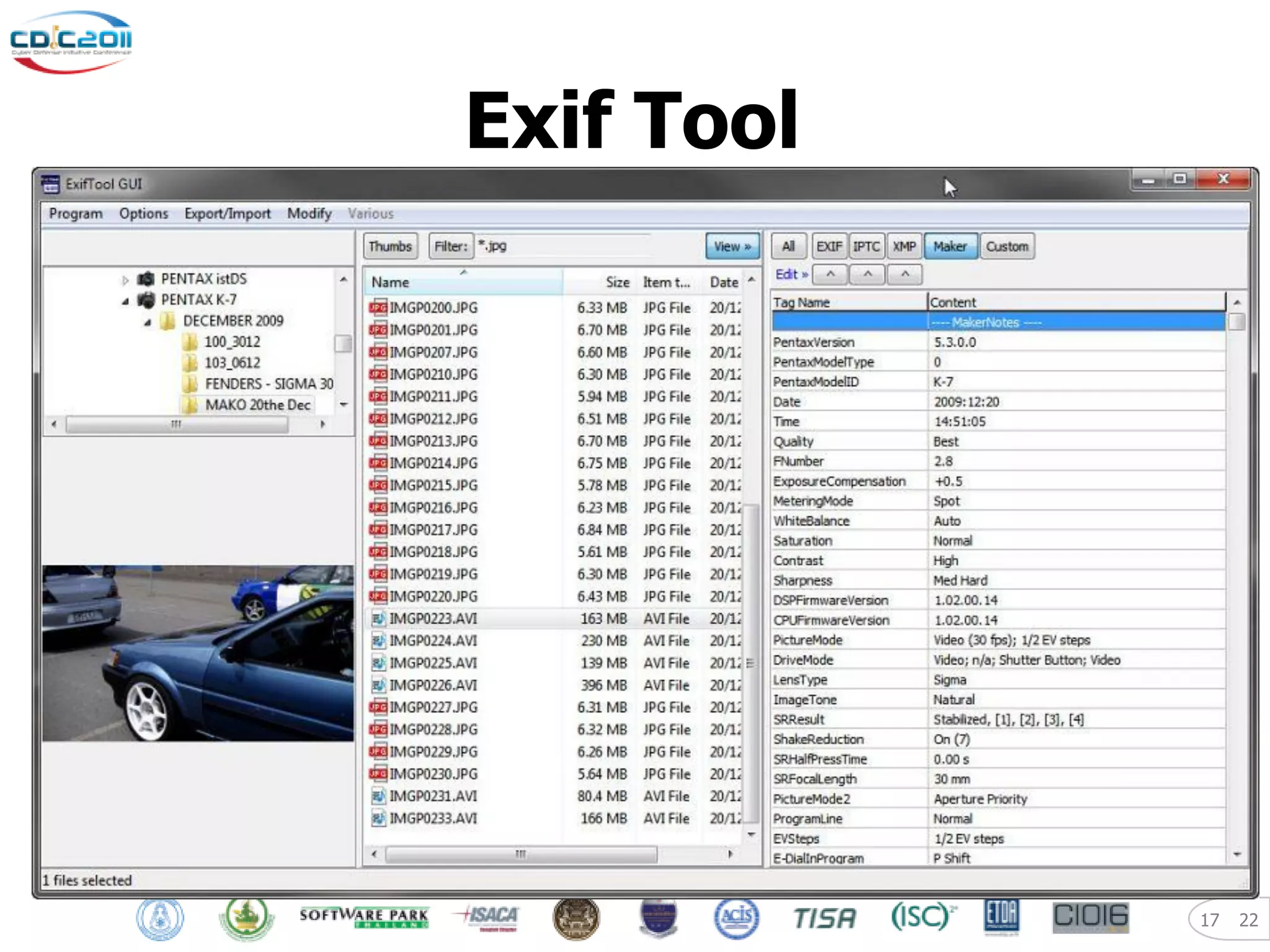
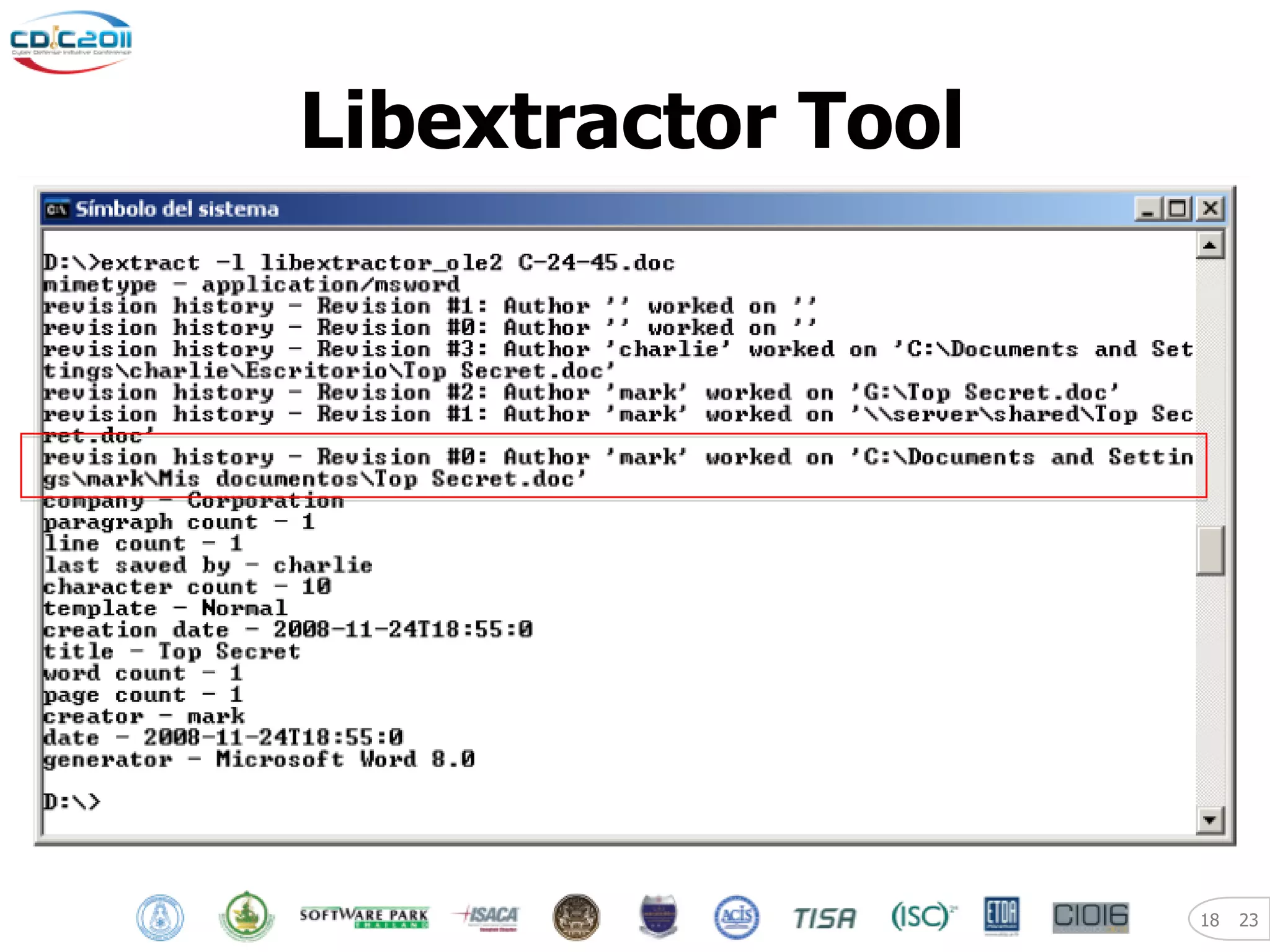
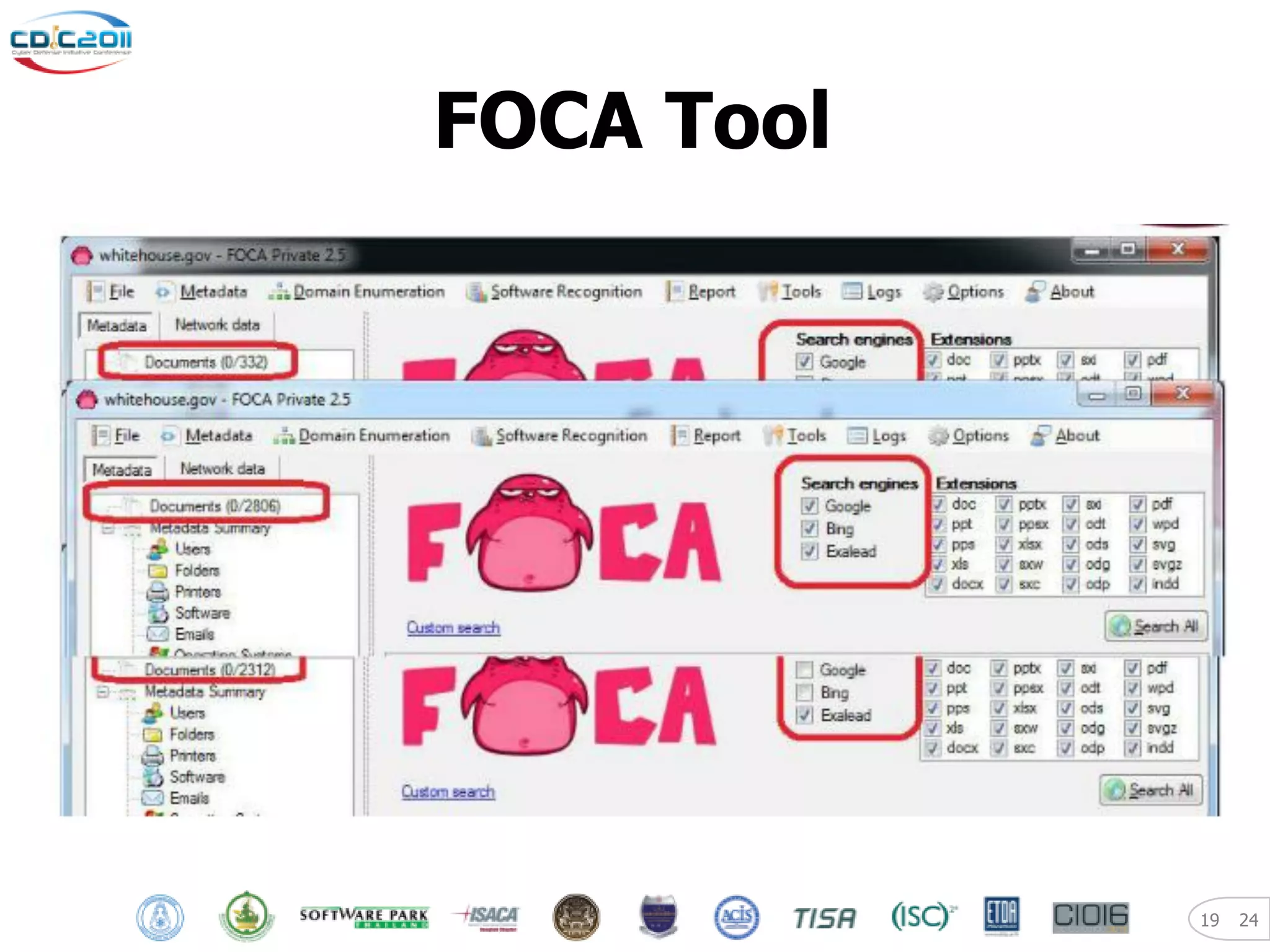
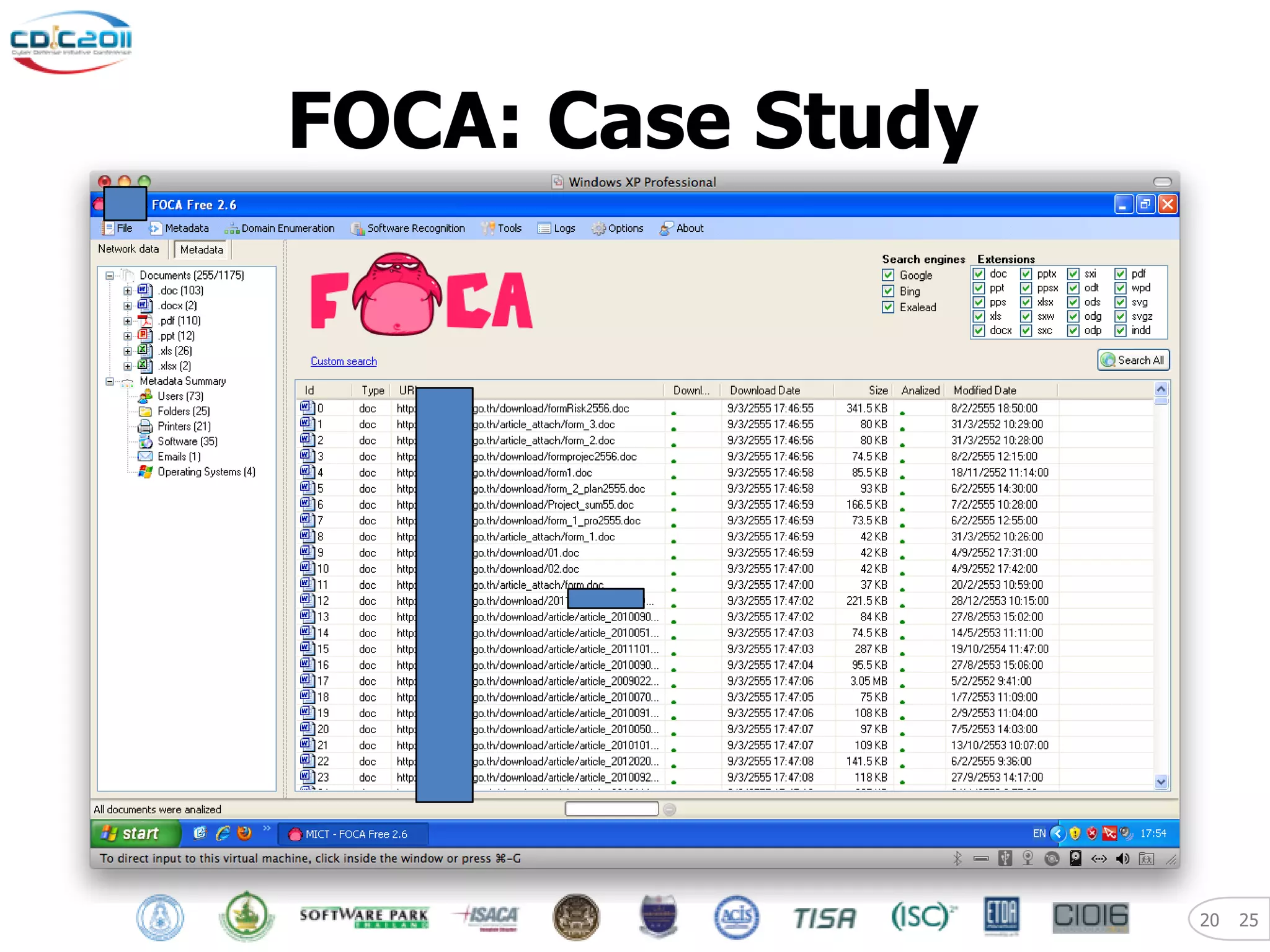
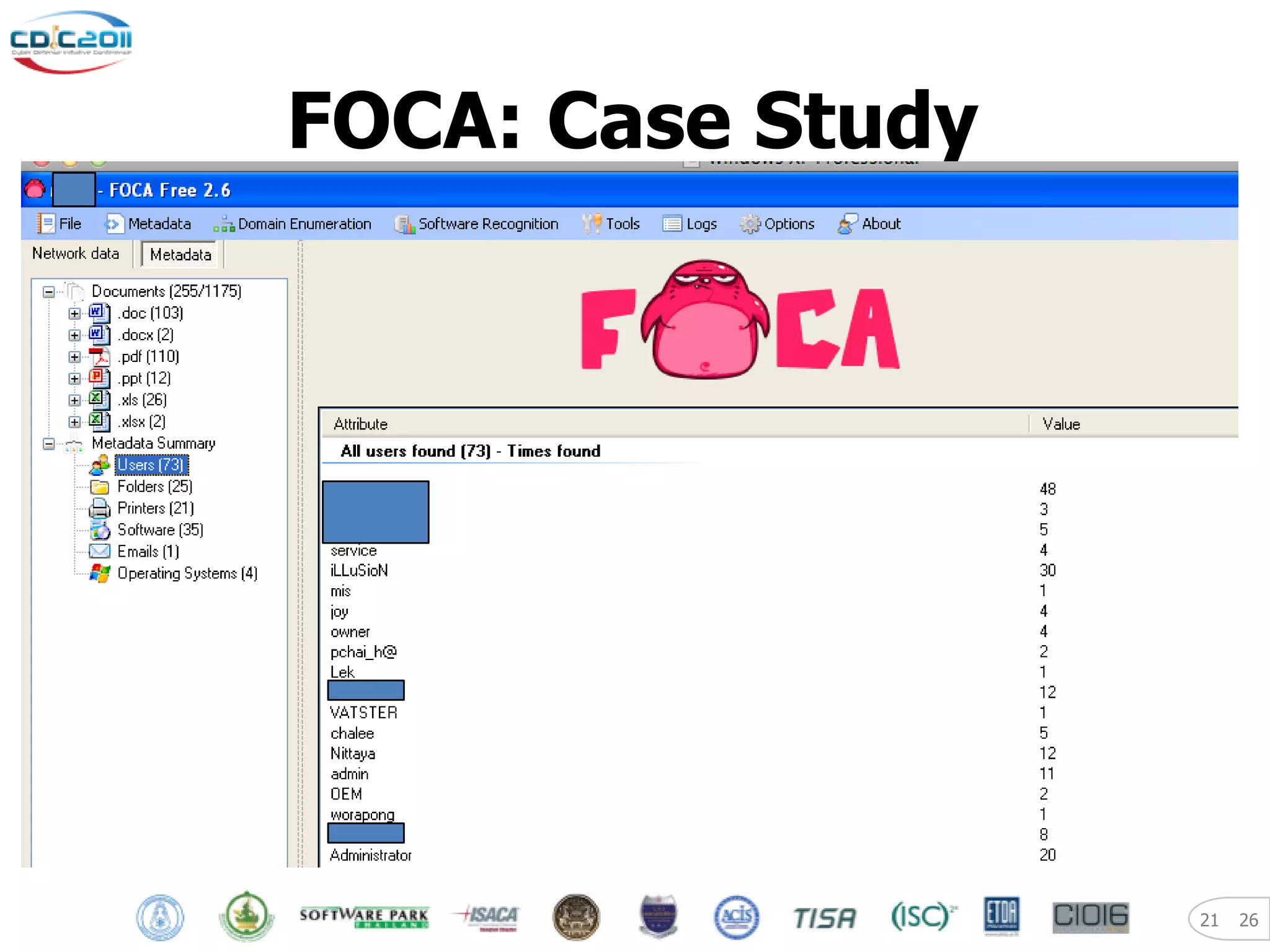
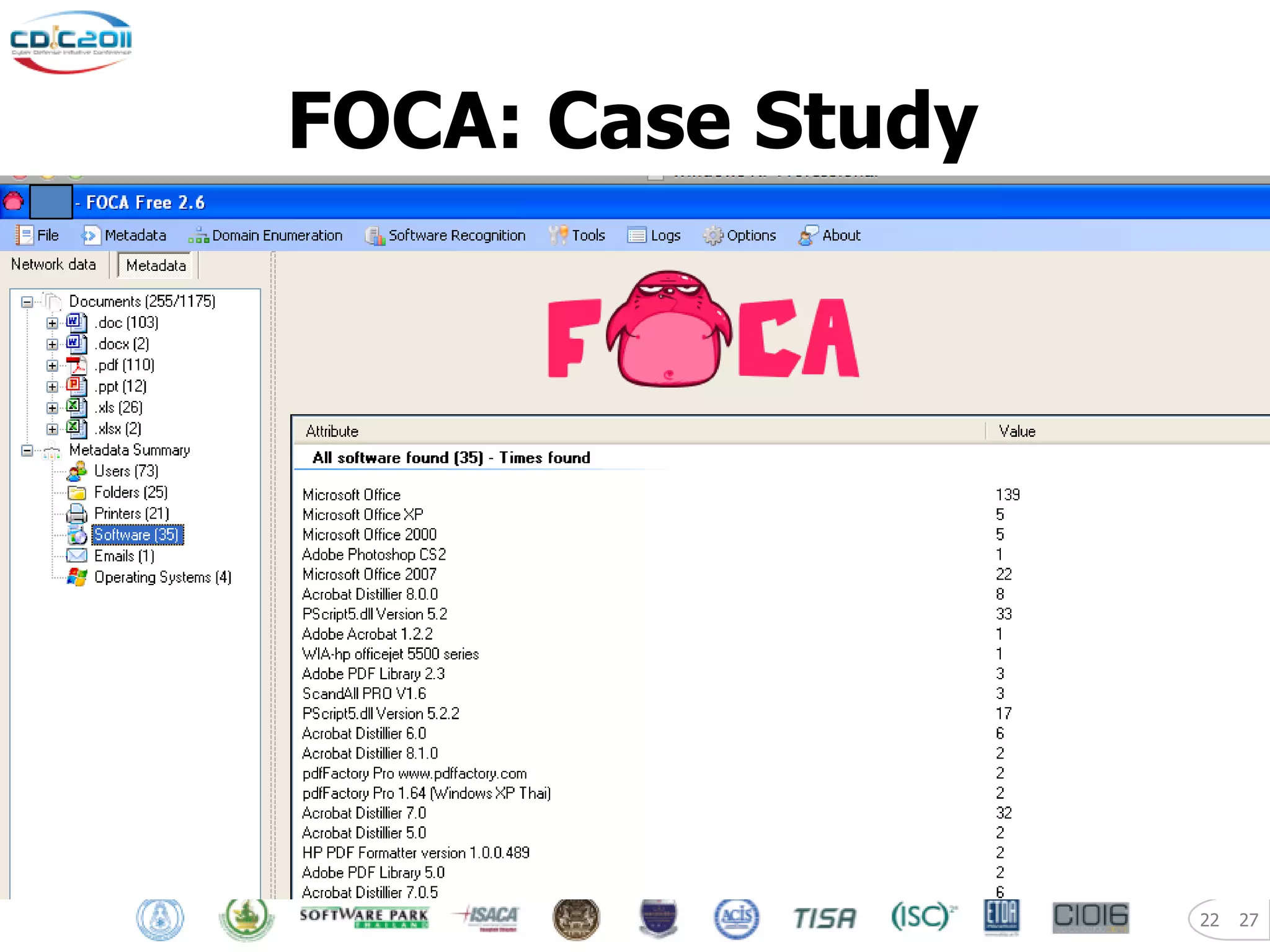
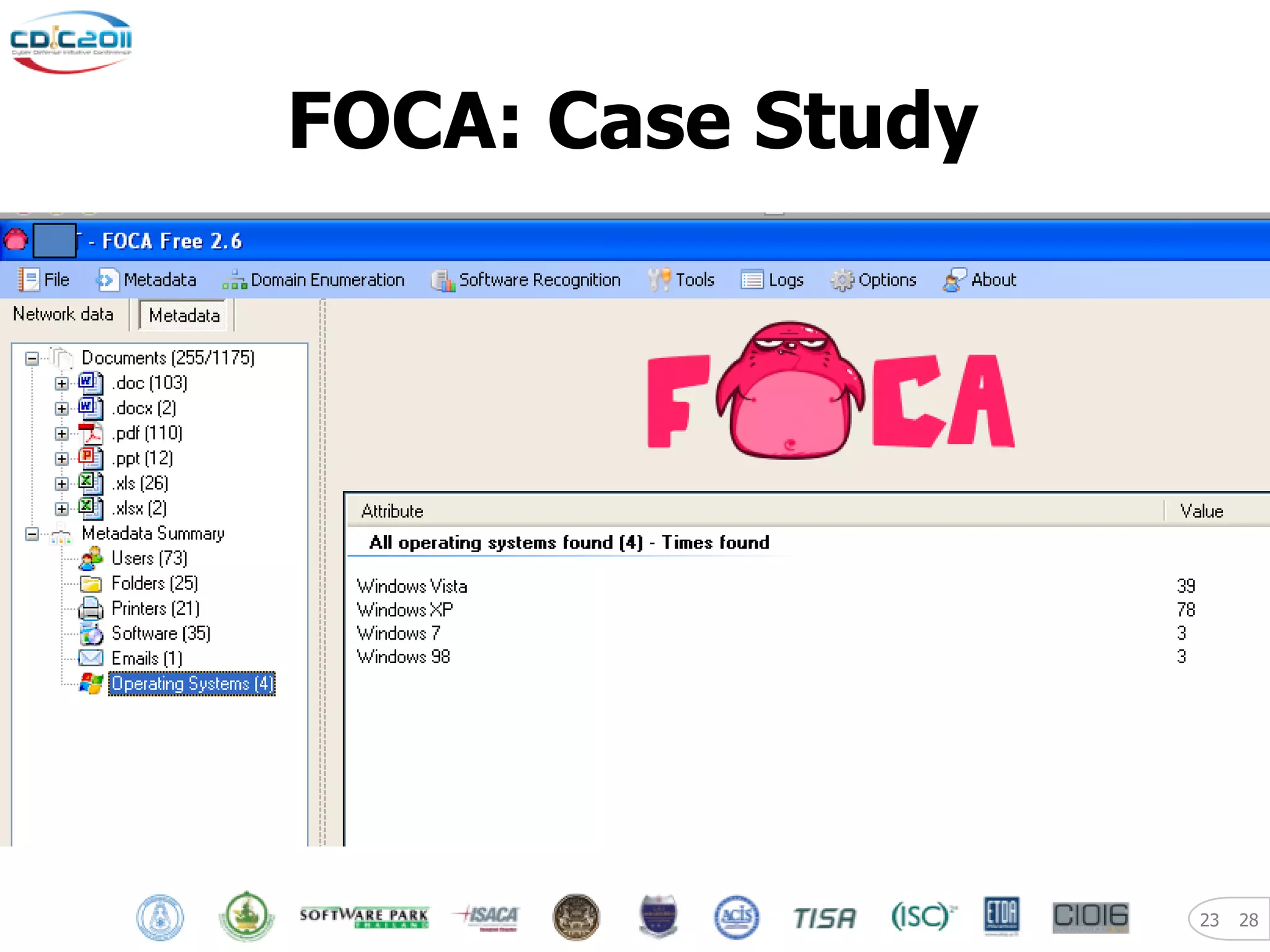
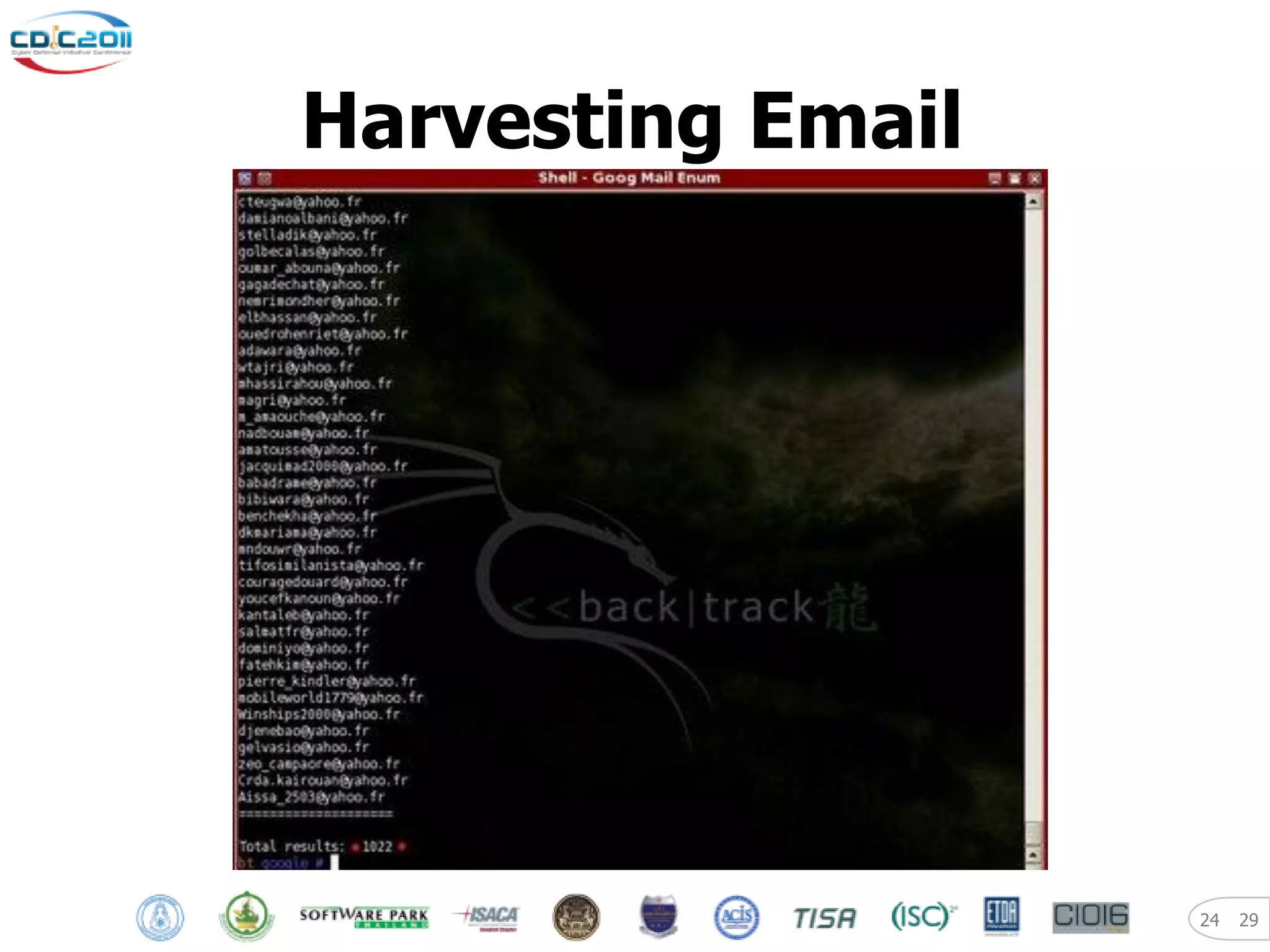
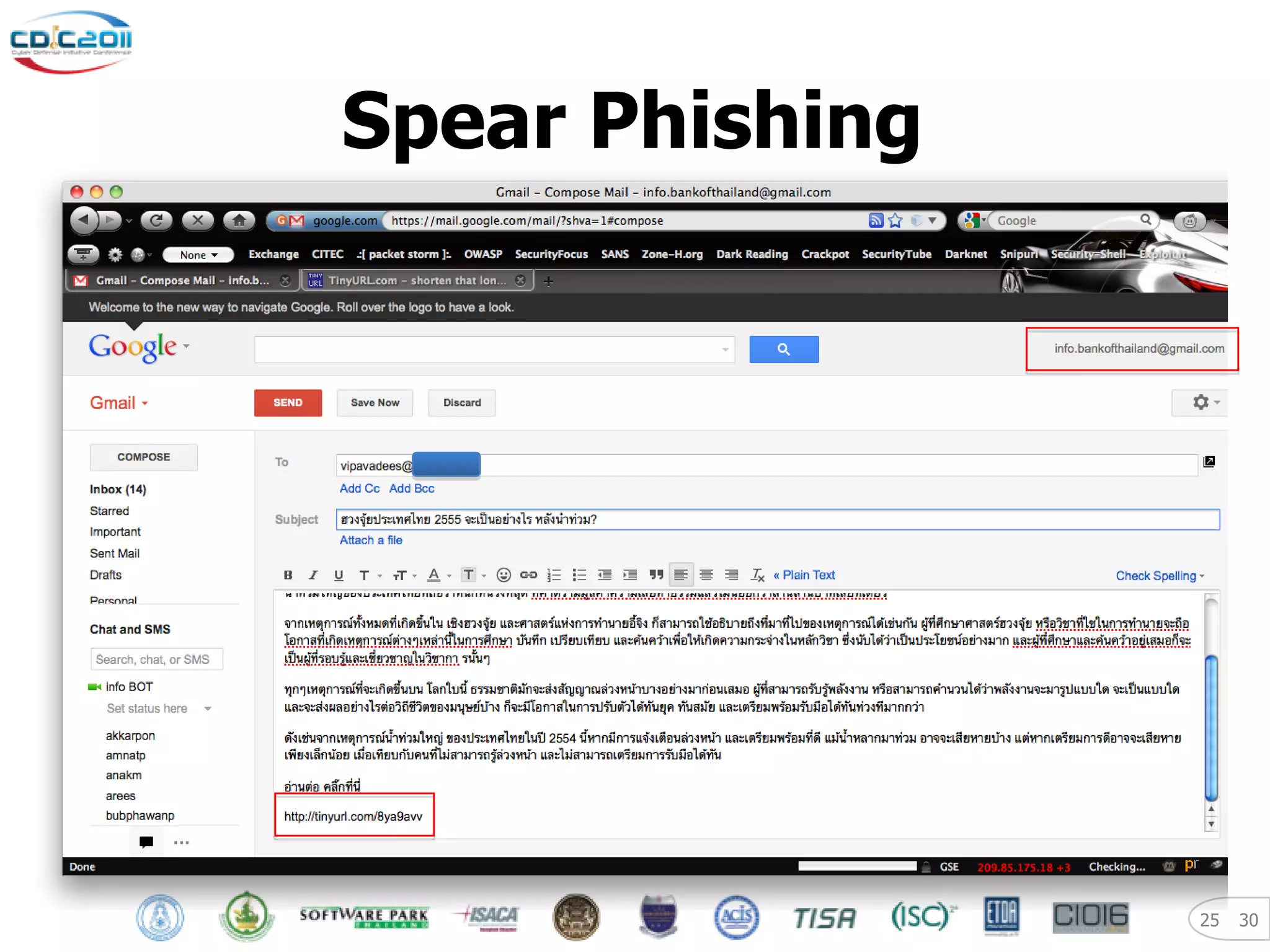
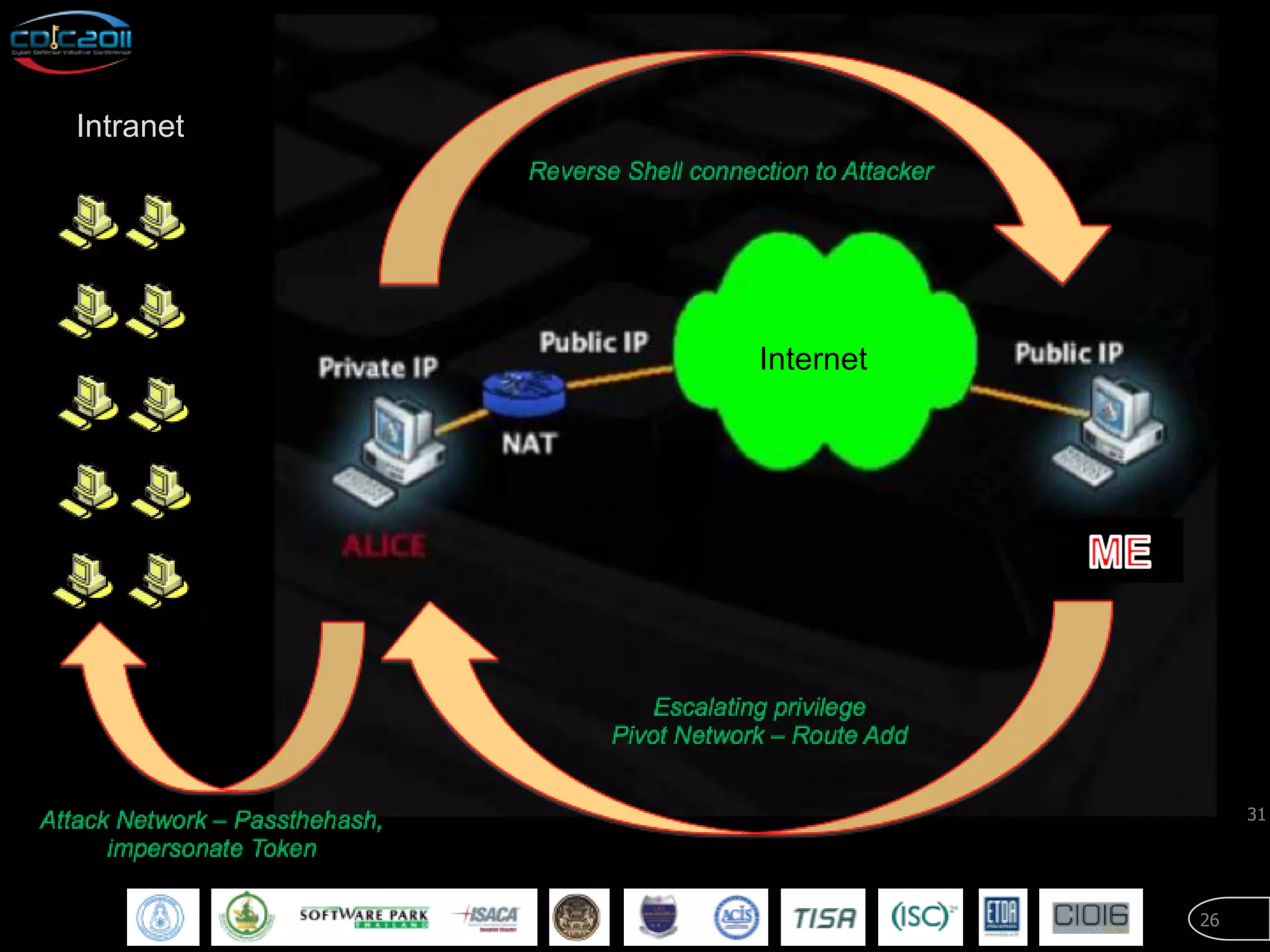
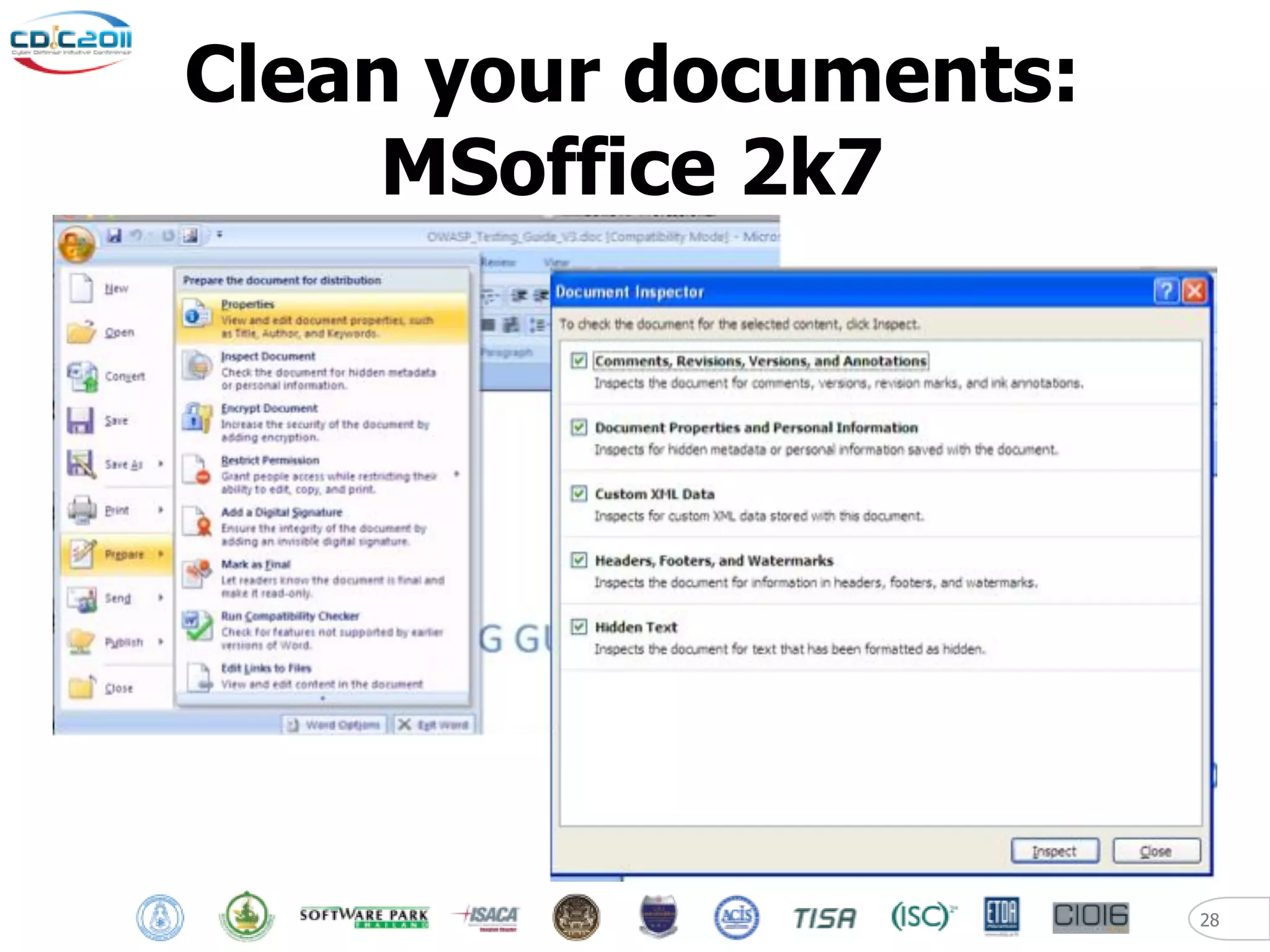
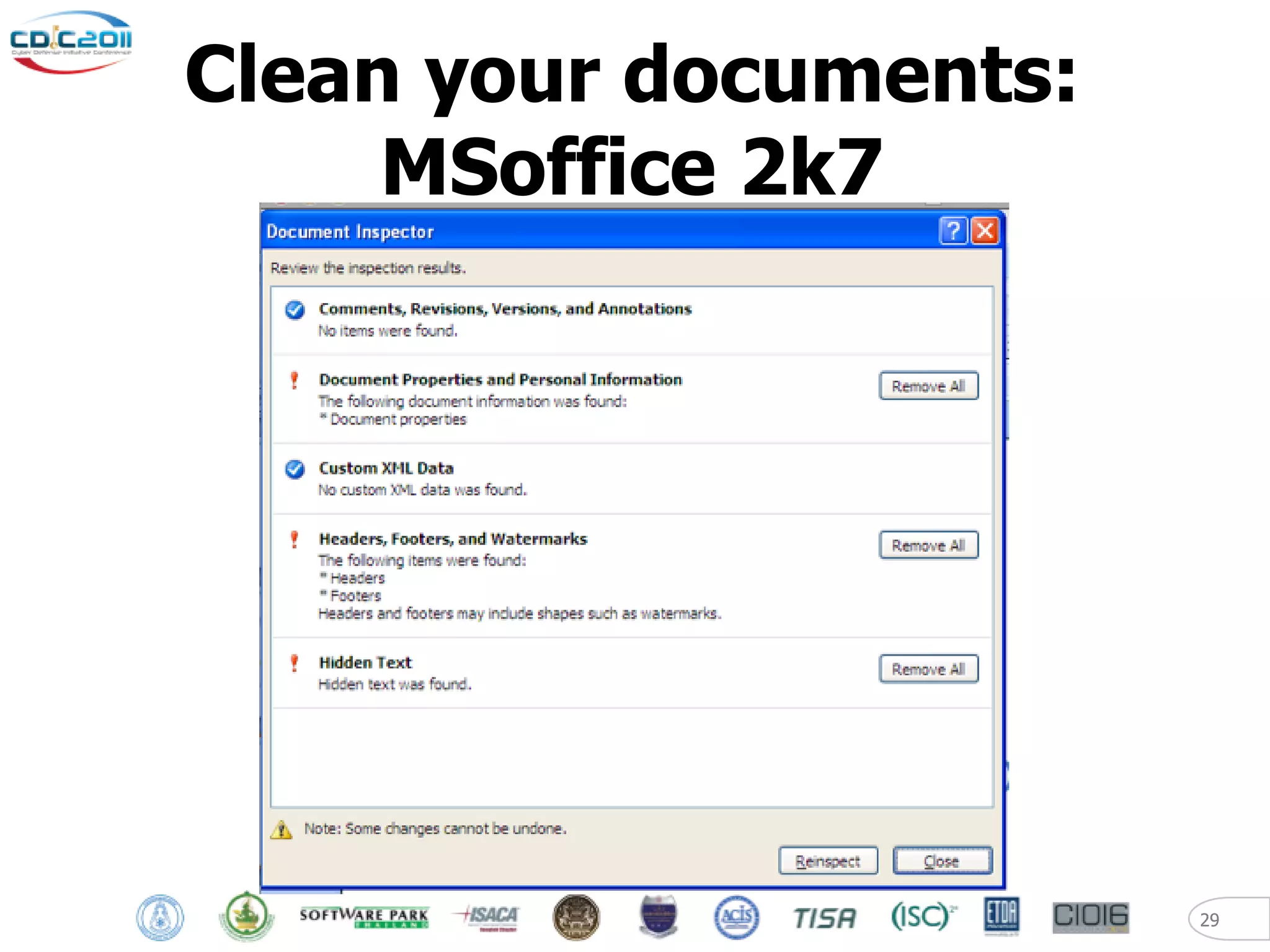
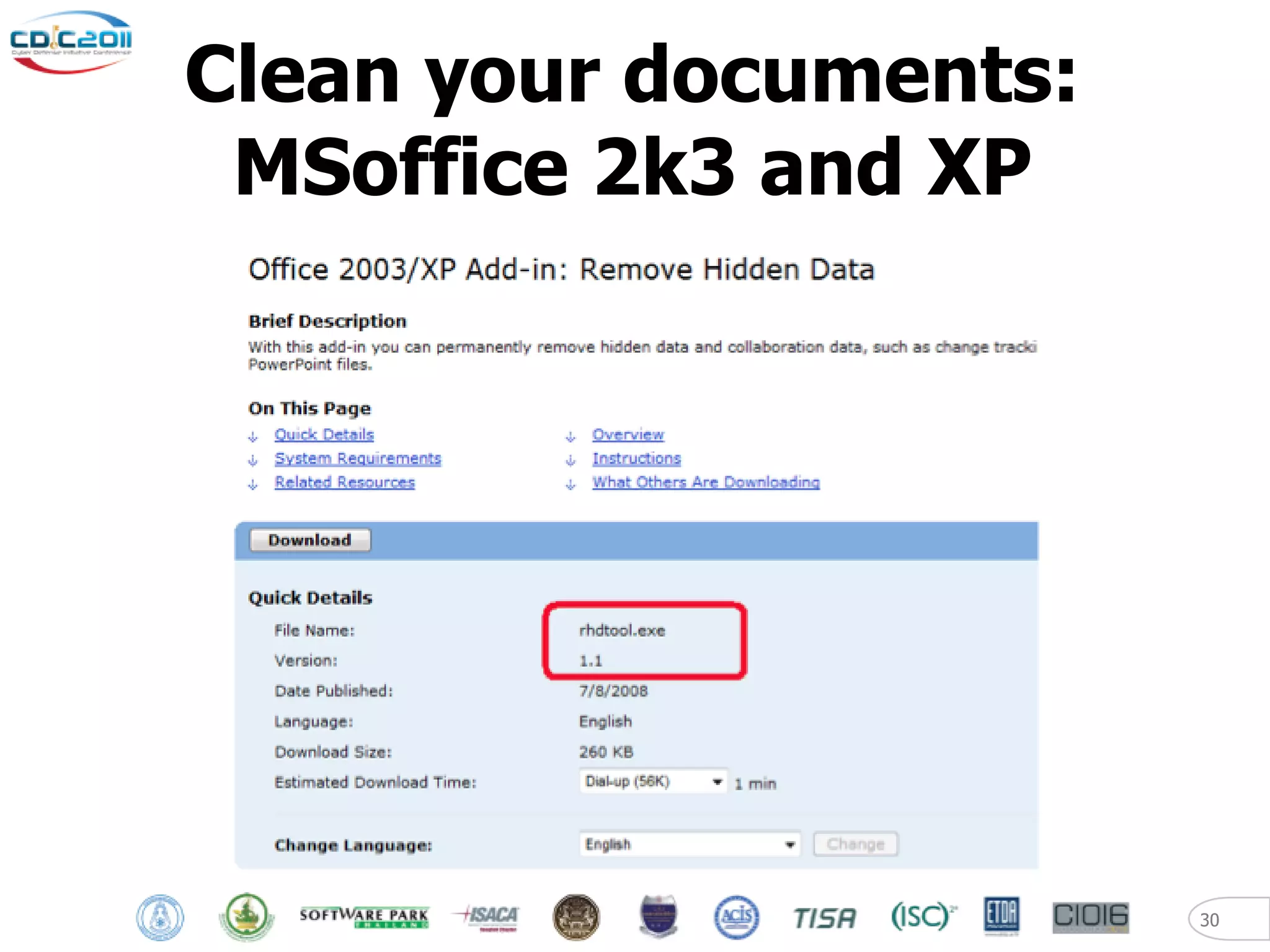
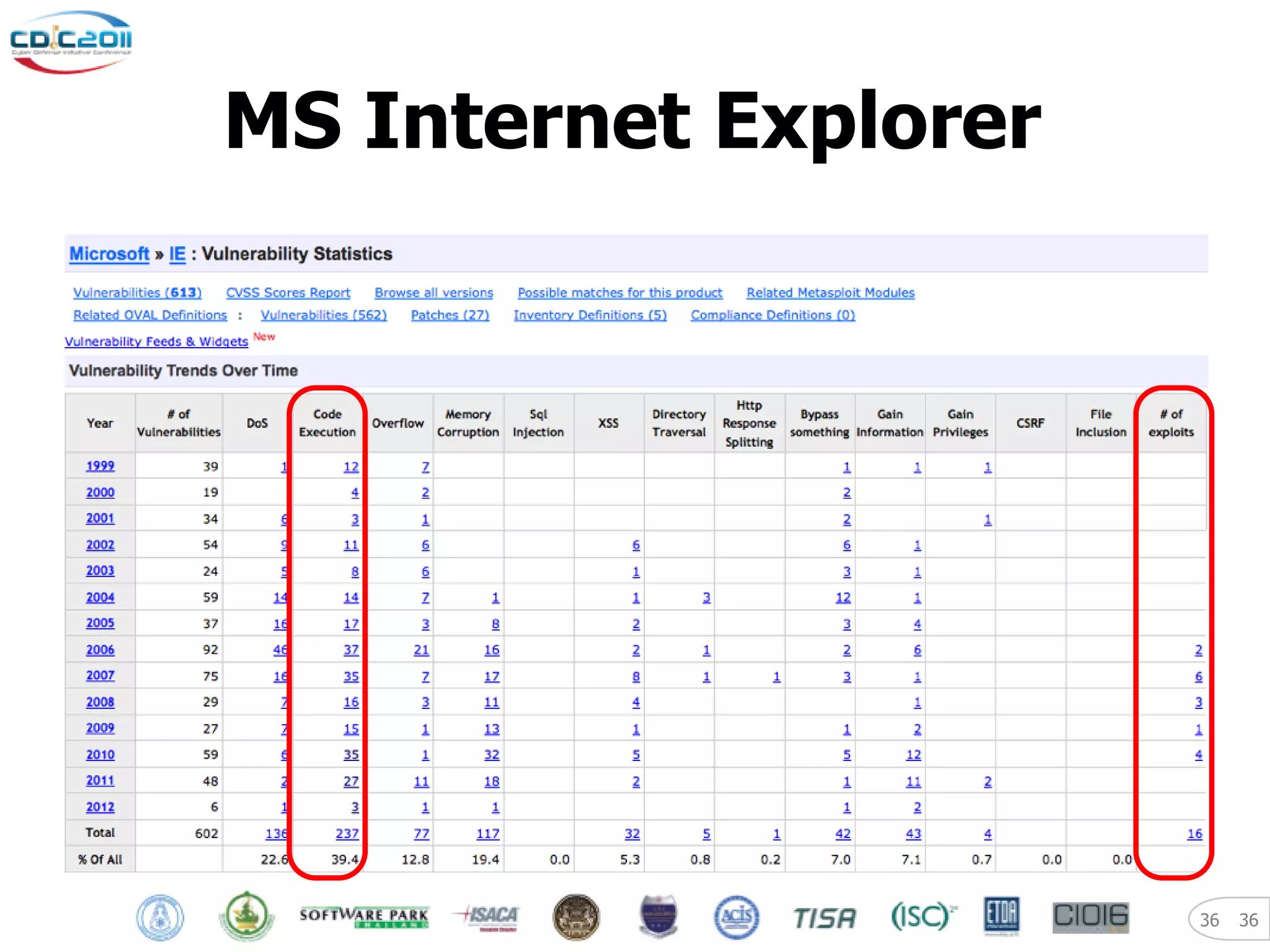
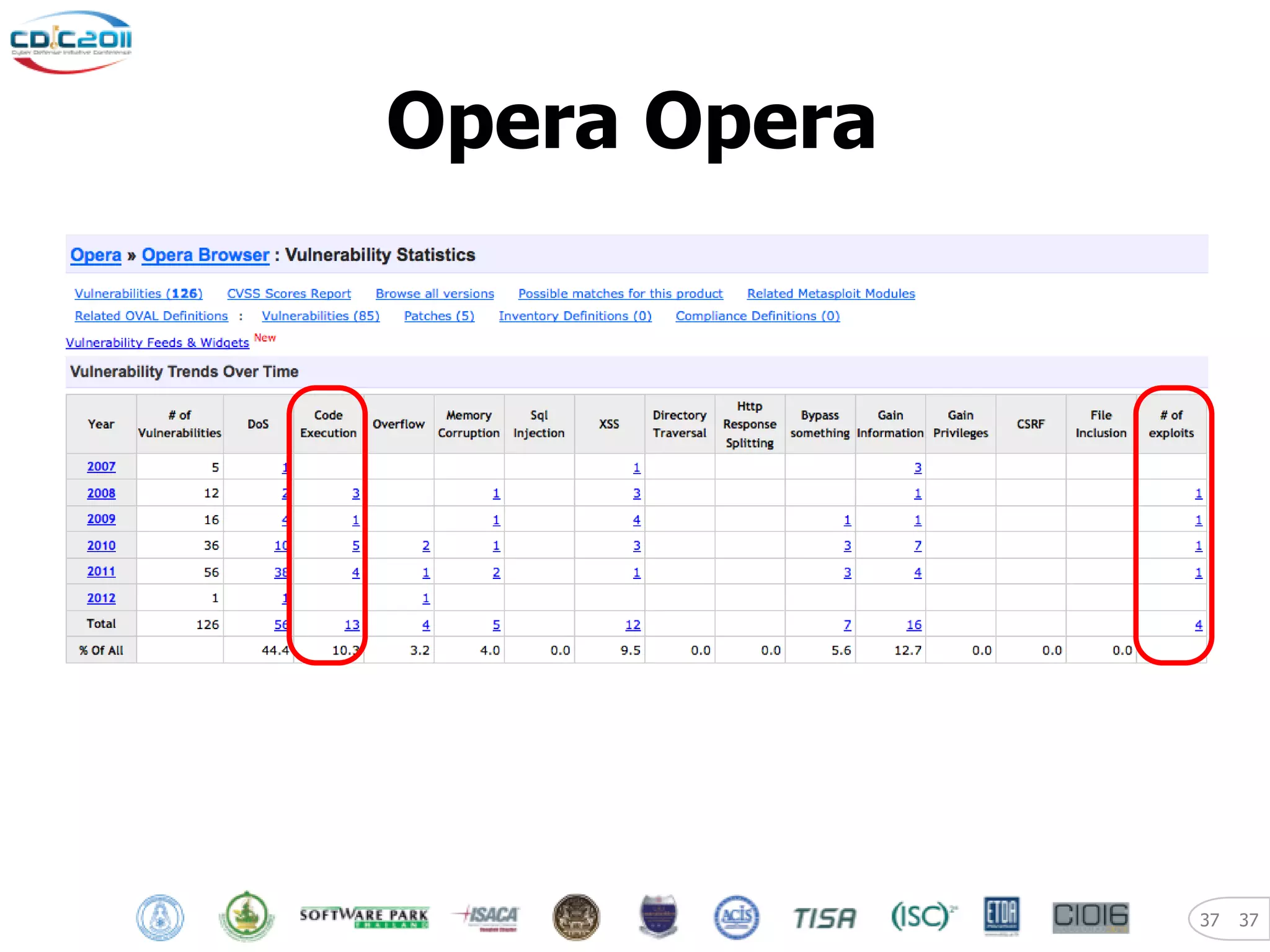
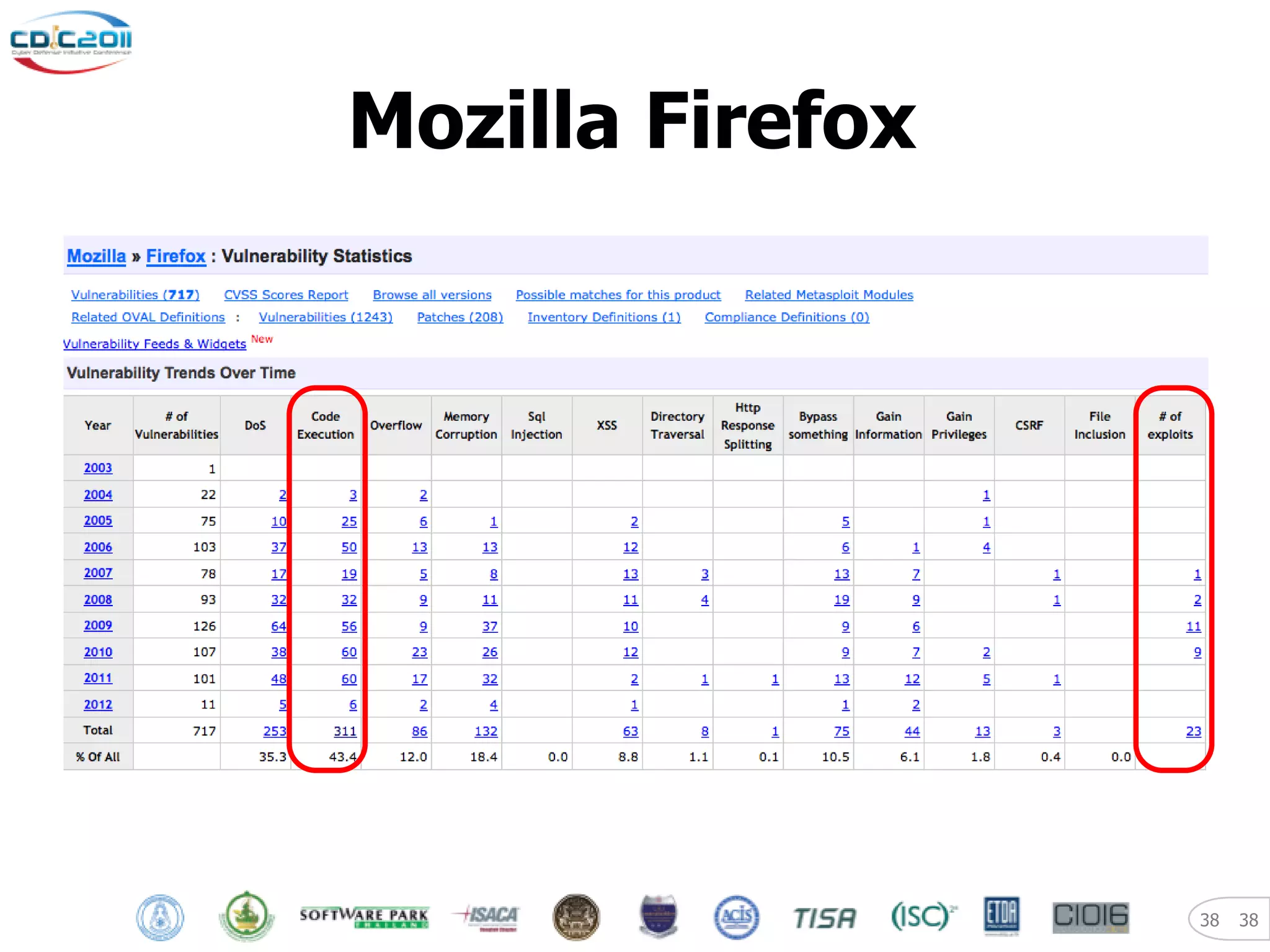
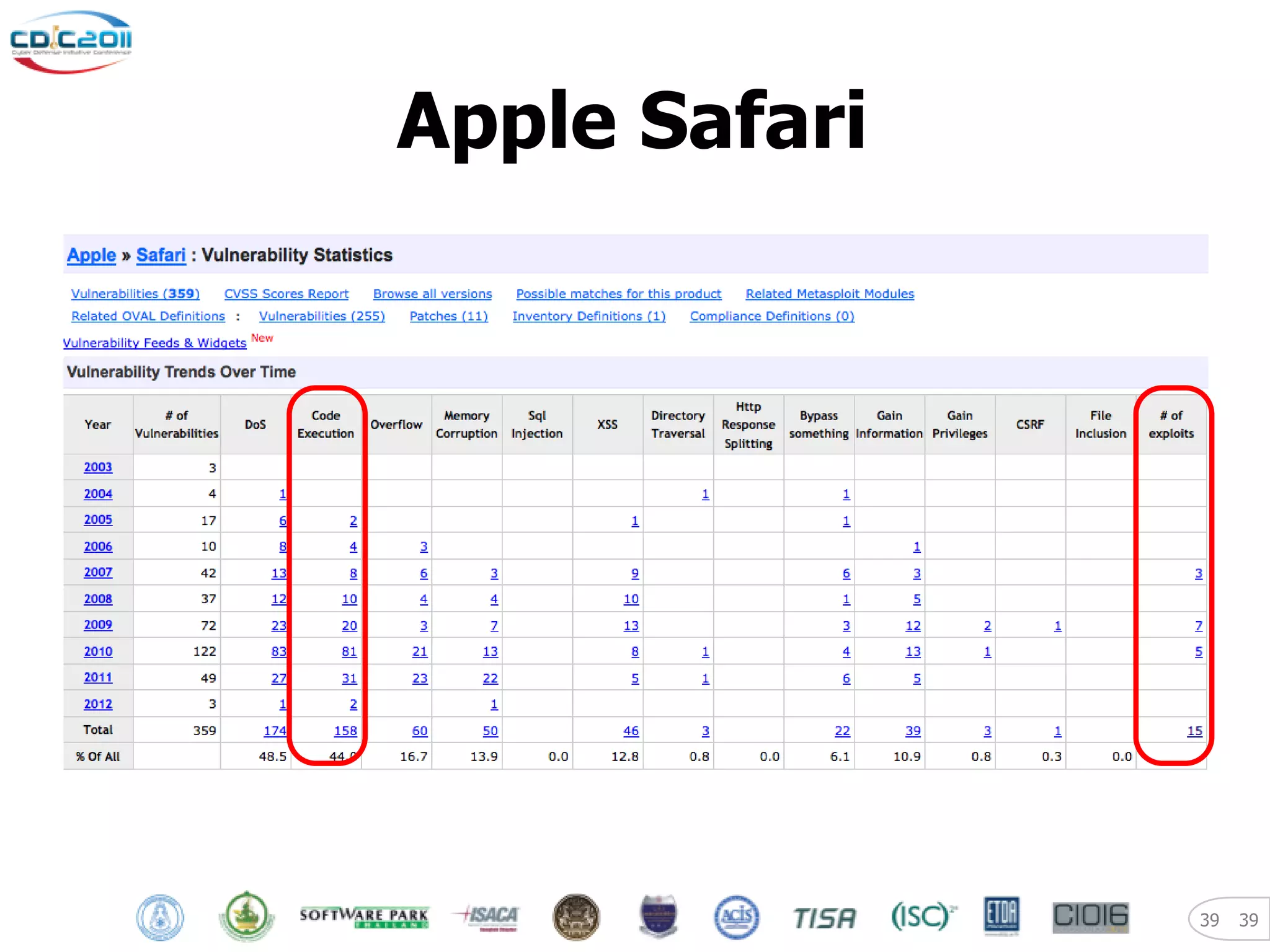
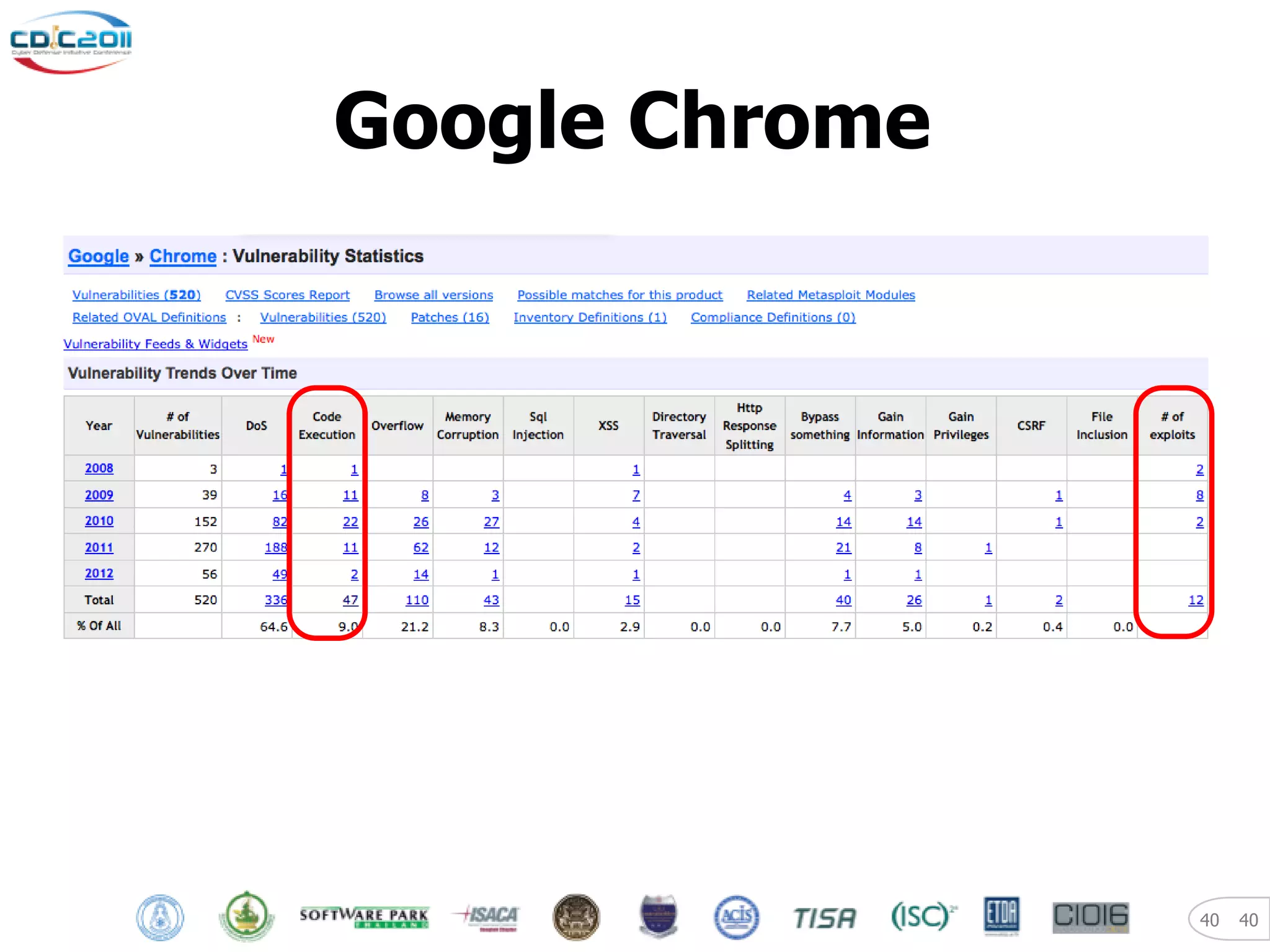
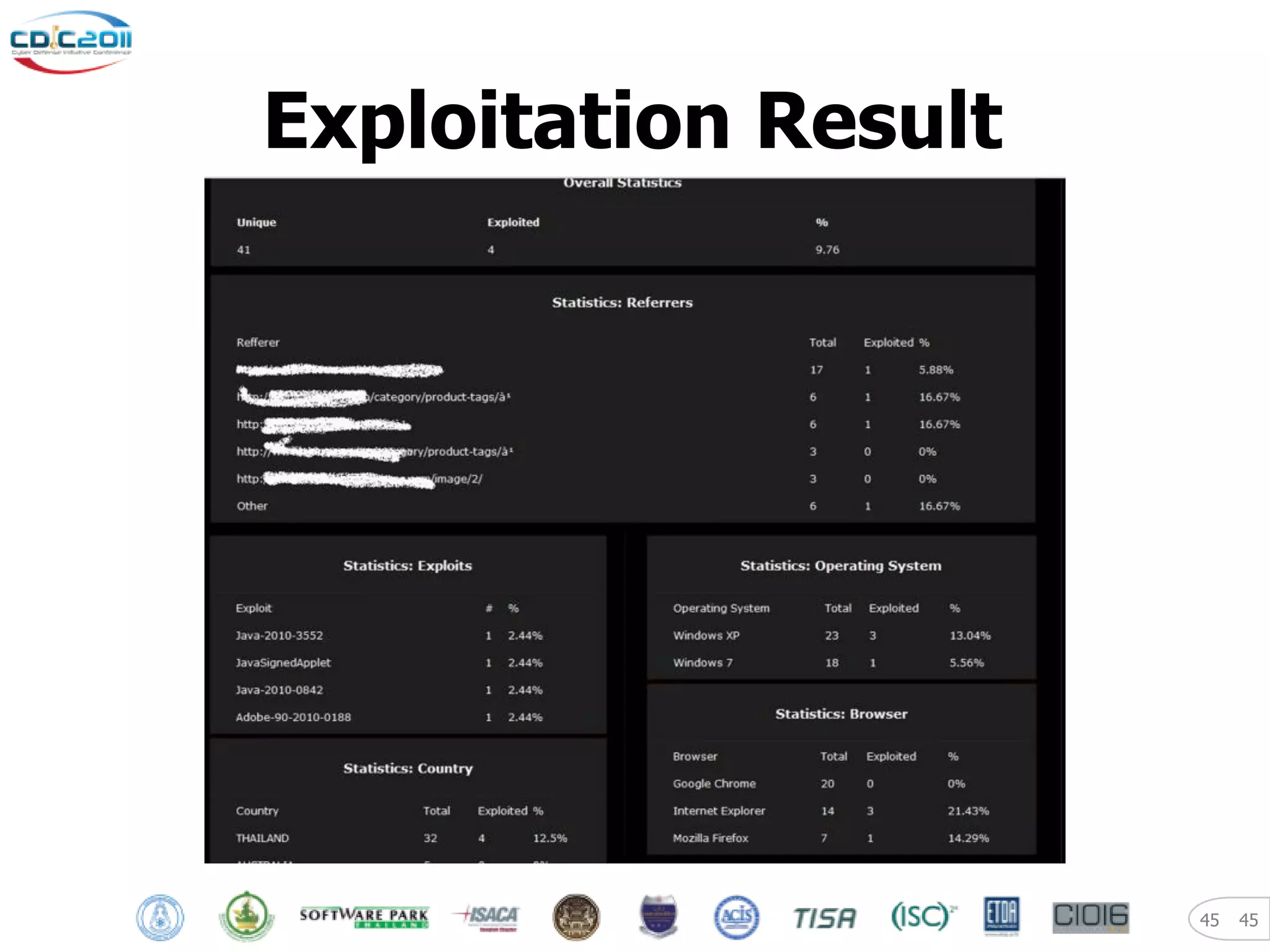
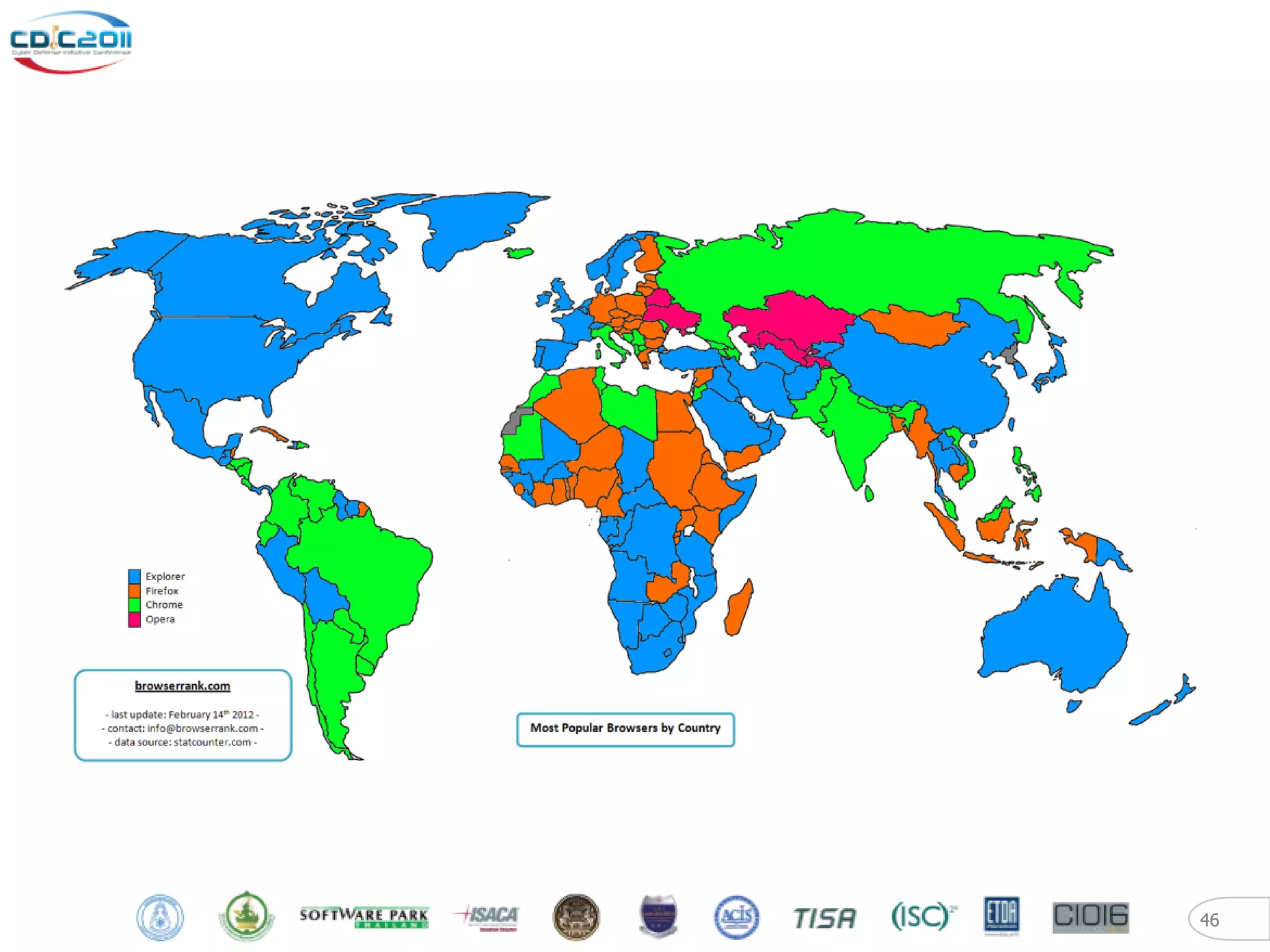
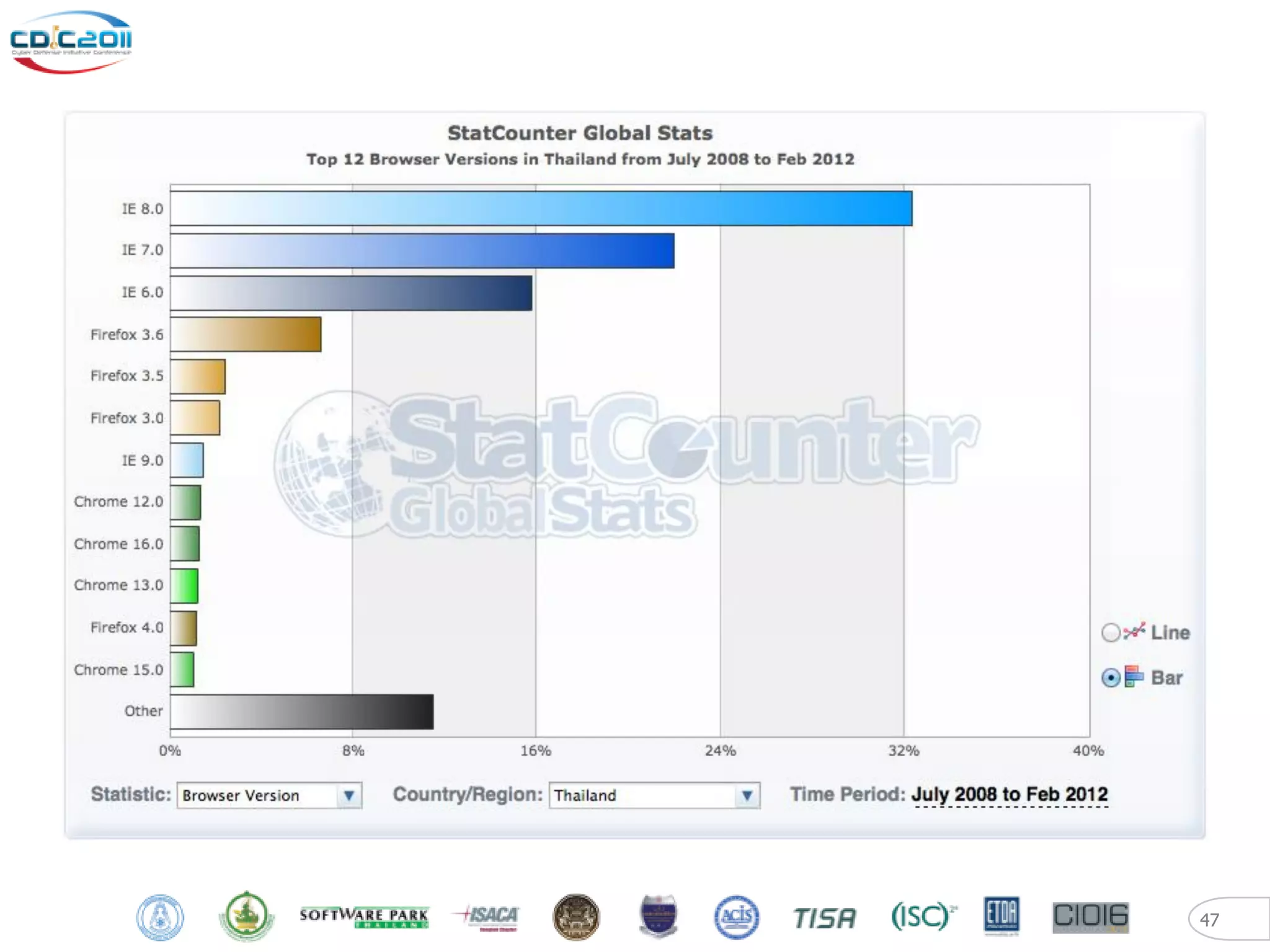
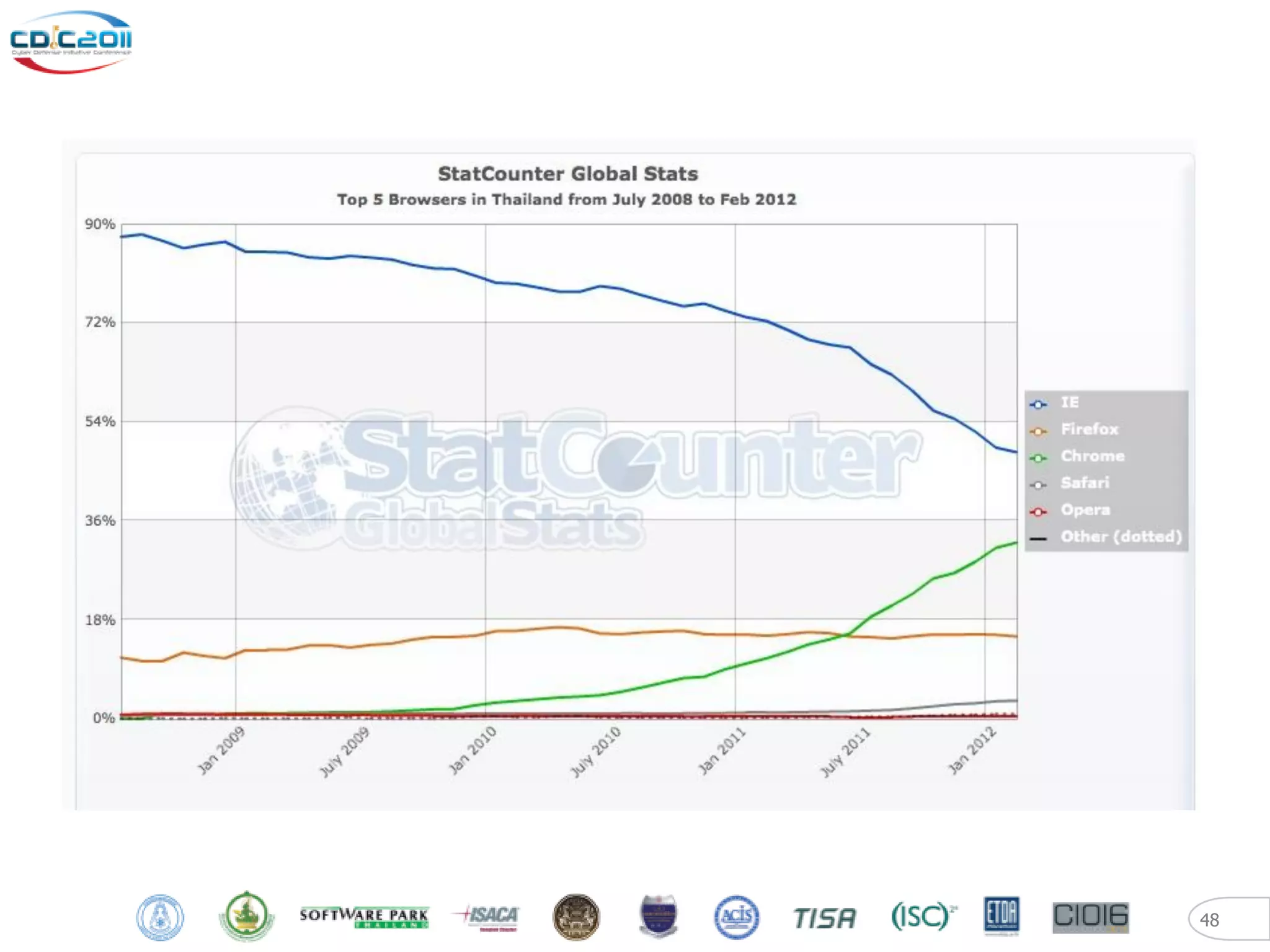
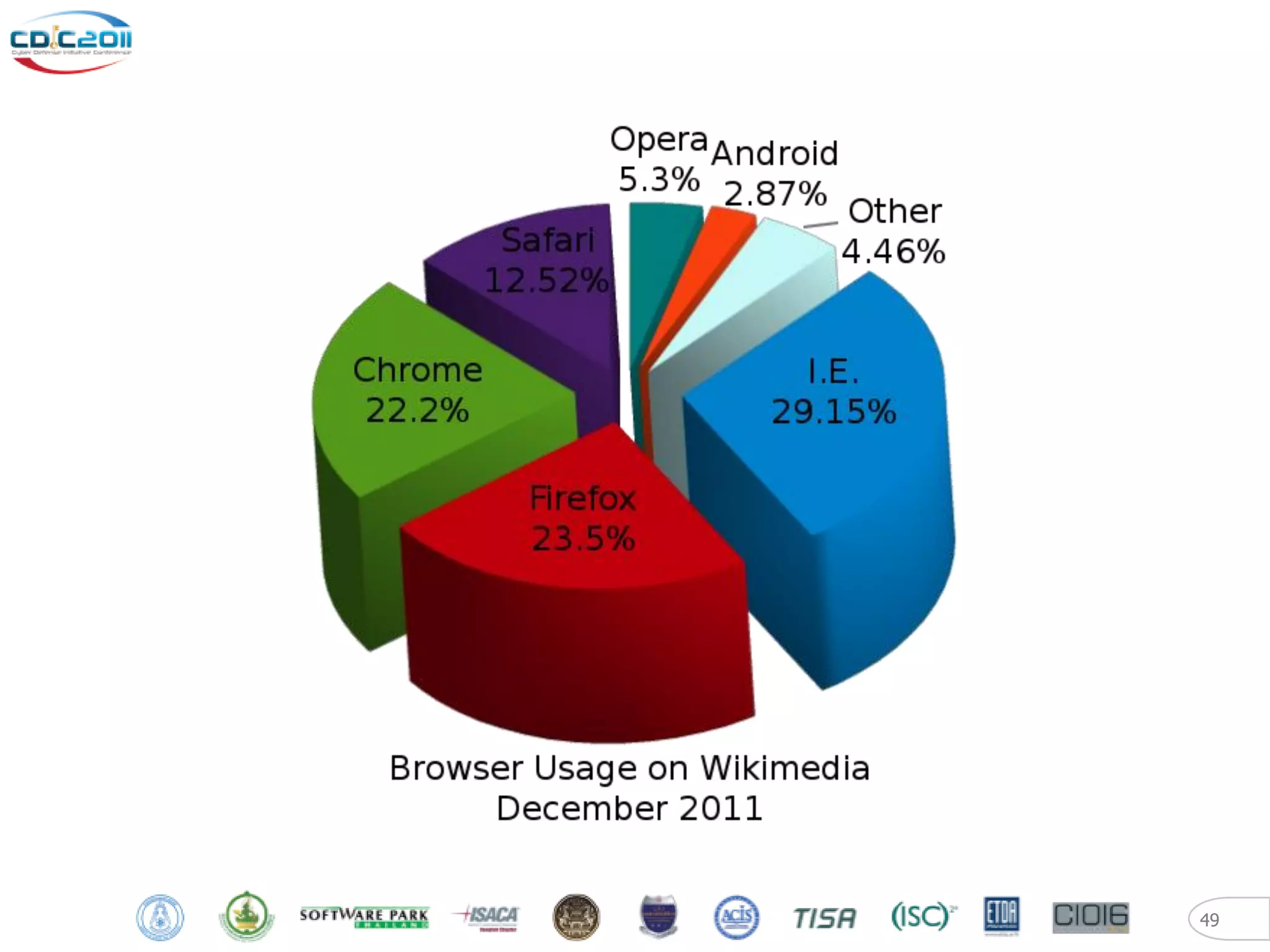
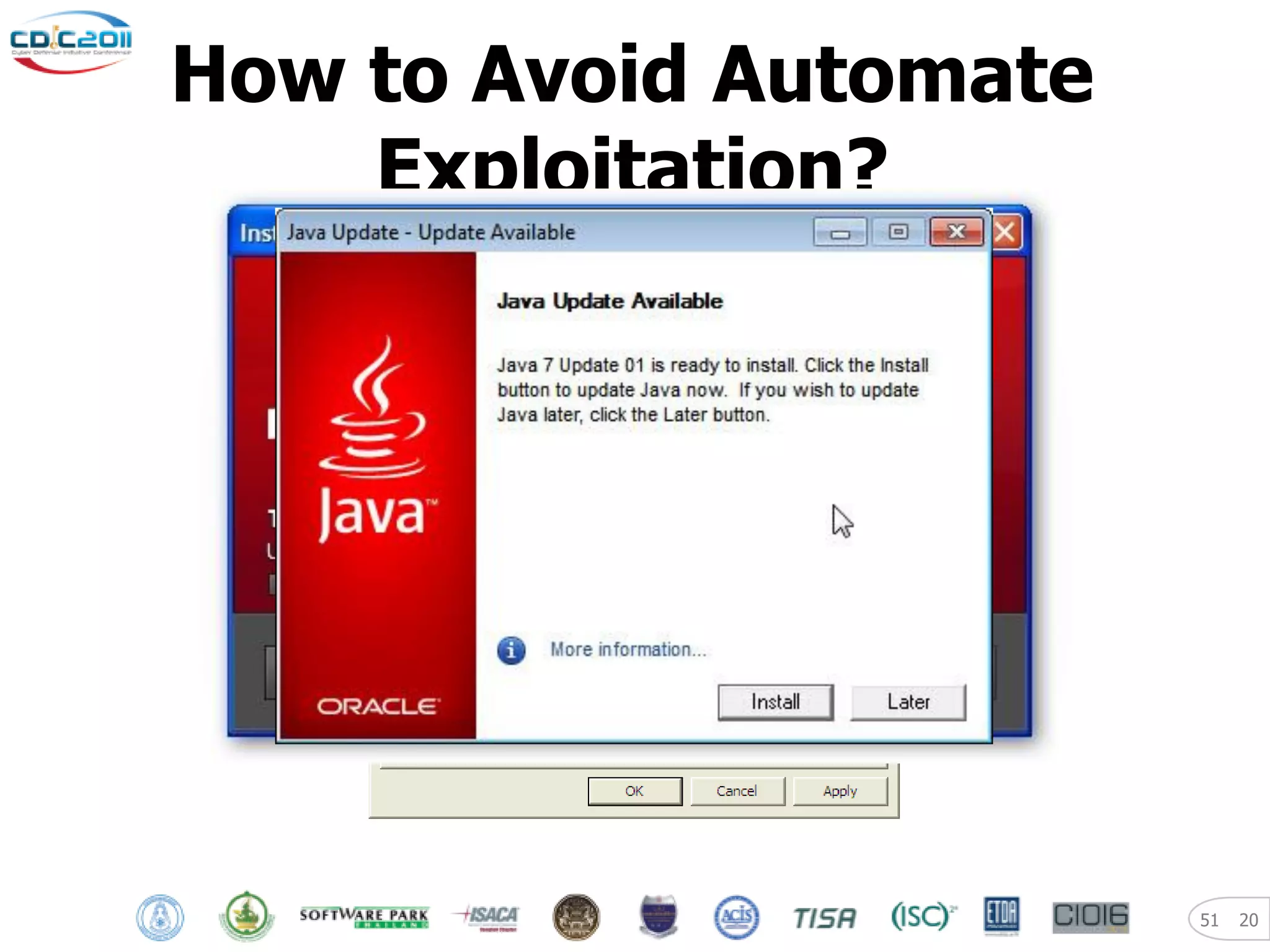
The document discusses security and privacy challenges in the digital age, focusing on client-side or "layer 8" hacking techniques that target human vulnerabilities. It describes how hackers gather information on targets from social media, documents, and email to craft spear phishing attacks. The document also outlines automated exploitation techniques using known vulnerabilities in browsers, plugins and applications, demonstrating how hackers can easily compromise systems without any user interaction. It emphasizes the importance of user awareness training, security policies, and sanitizing public documents and files to reduce the risks of these client-side attacks.