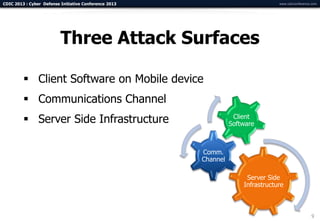
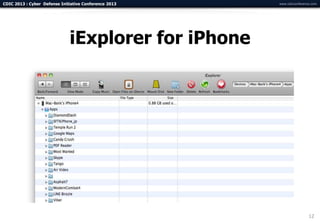
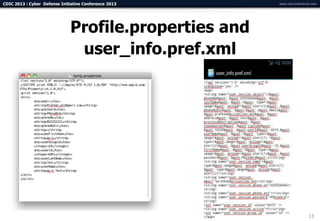
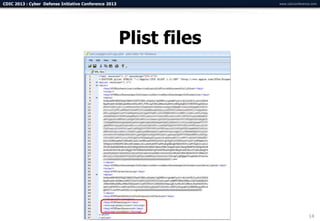
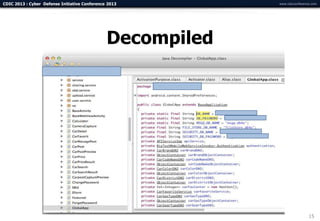
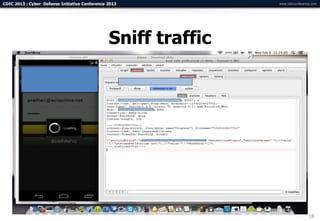
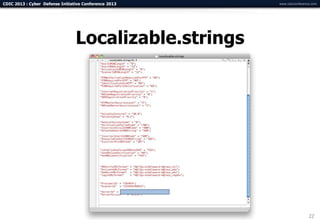
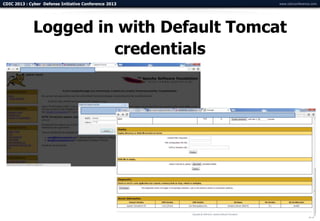
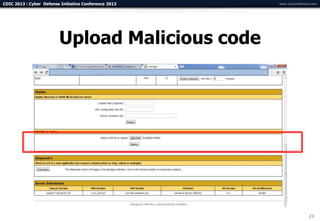
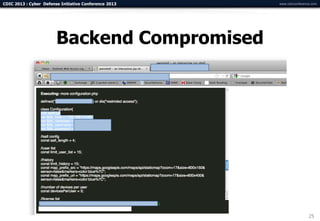
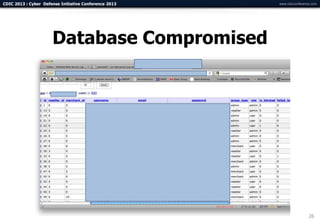
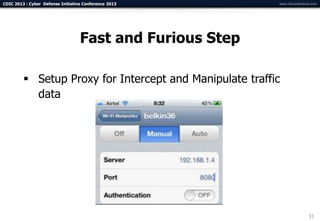
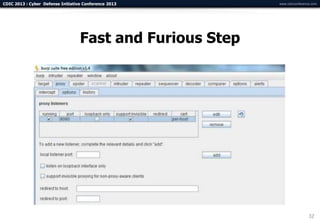
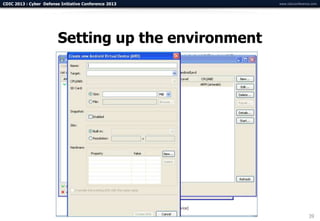
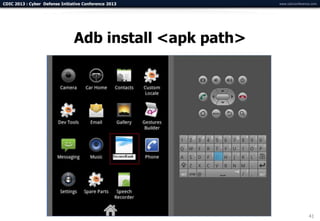
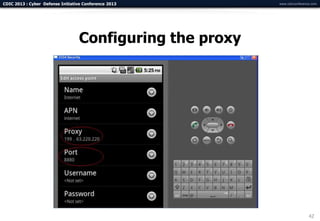
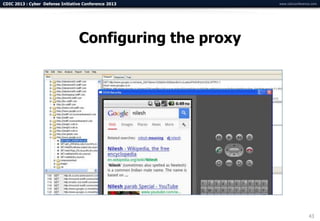
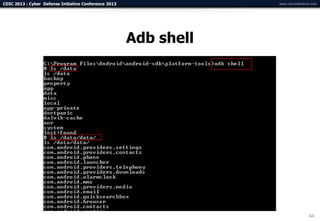
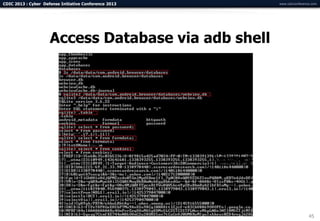
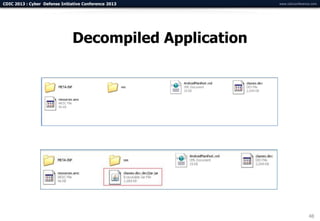
The document summarizes a presentation on advanced mobile penetration testing. It discusses attacking three surfaces: the client software on mobile devices, the communications channel, and server-side infrastructure. It provides examples of exploiting iOS and Android applications, such as decompiling code, intercepting traffic with proxies, and accessing embedded data and databases. The presentation emphasizes fast, hands-on techniques and tools for assessing mobile application security.