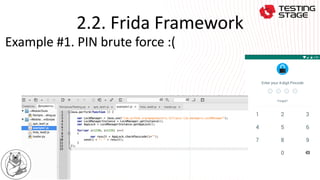
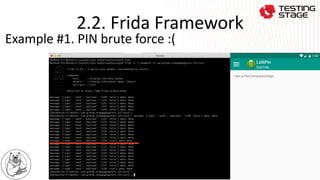
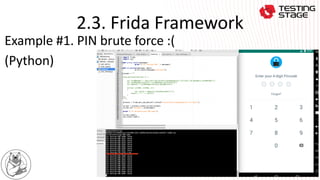
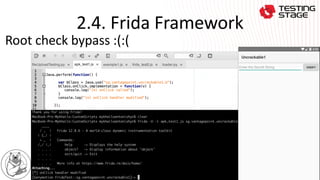
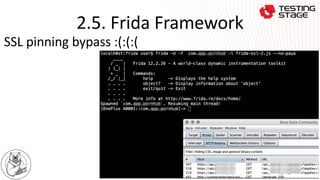
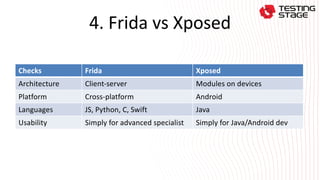
This document summarizes a presentation on advanced Android app security testing. The presentation covers Frida and Xposed frameworks for bypassing security protections like root checks, SSL pinning, and secret codes. It then compares Frida and Xposed frameworks and outlines techniques for protecting apps, including code hardening, runtime application self-protection (RASP), and code optimization.