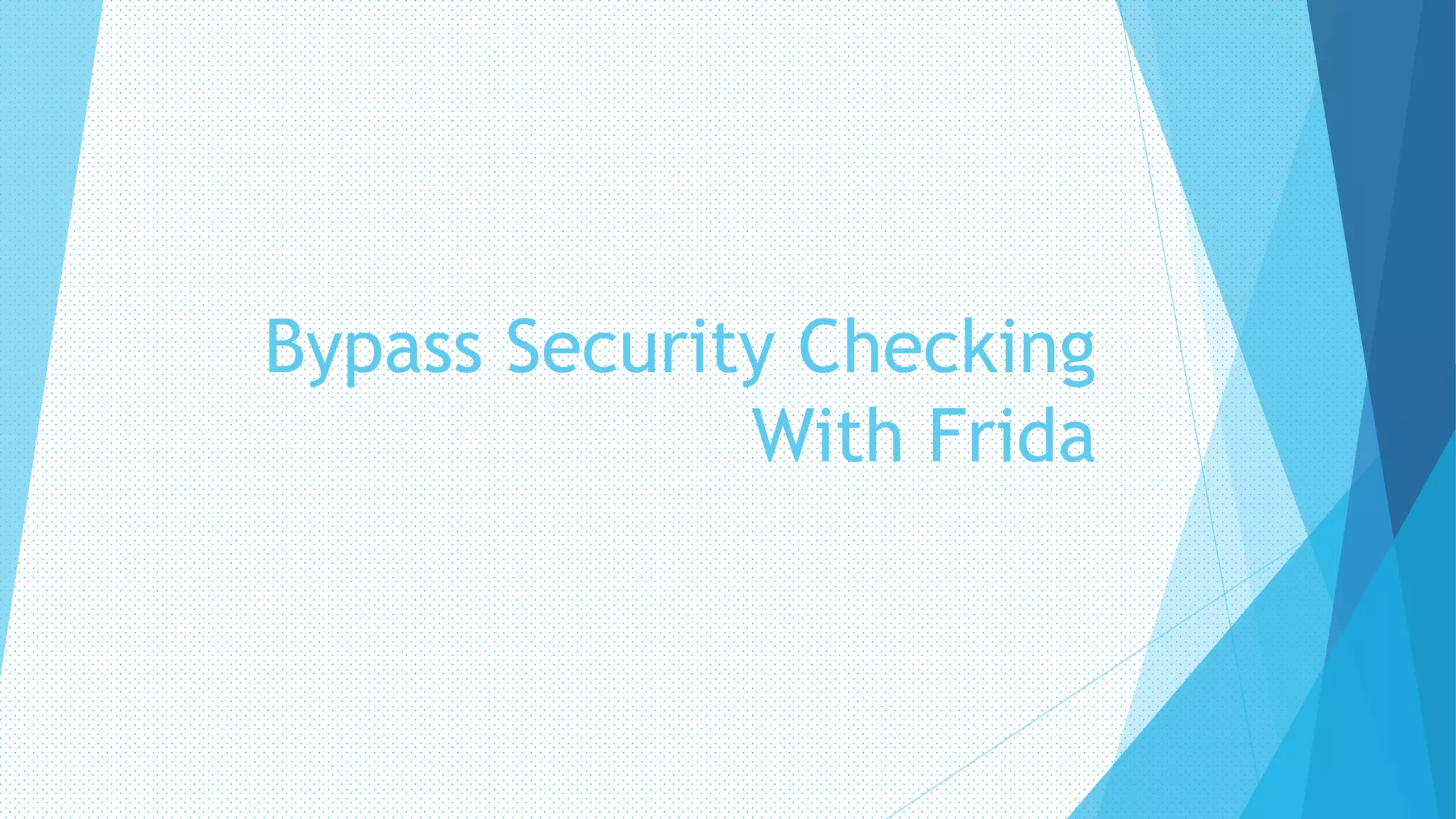
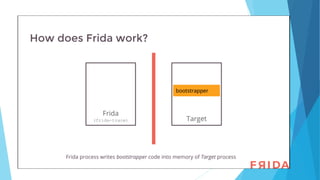
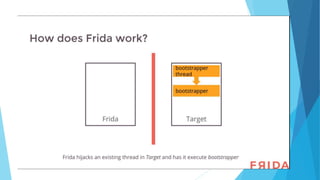
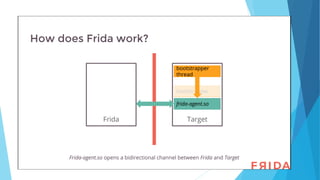
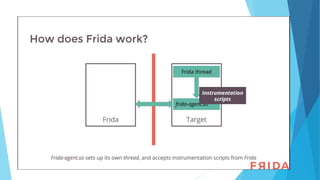
The document discusses the use of Frida, a dynamic instrumentation toolkit, for analyzing binaries and applications by bypassing security mechanisms like encryption, root checks, and SSL pinning. It highlights the advantages of using Frida over traditional code injection techniques, emphasizing its capability to inspect and instrument live processes across multiple platforms. The text provides insights on how to hook functions and modify application behavior at runtime using Frida's JavaScript API and various bindings.