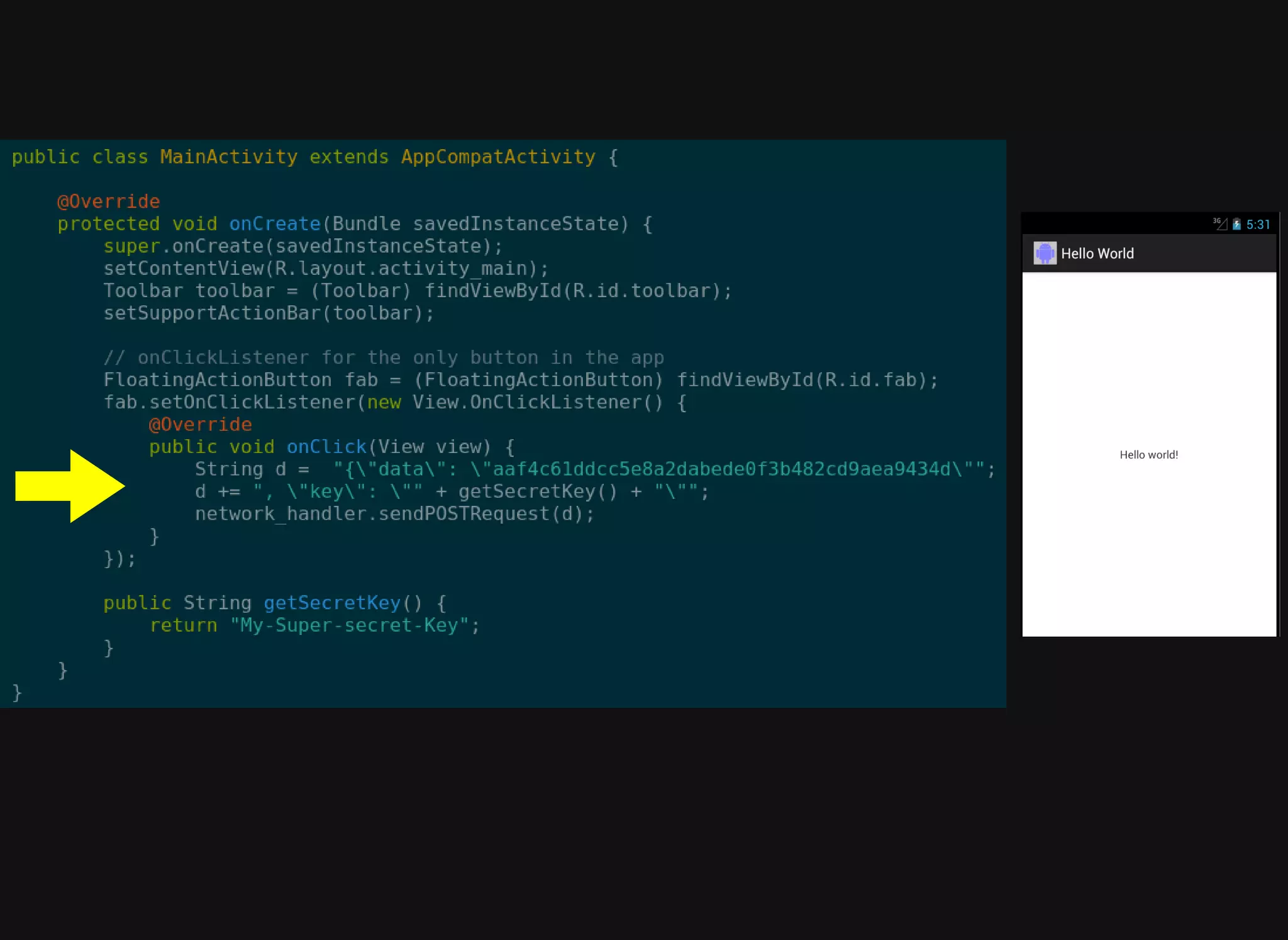
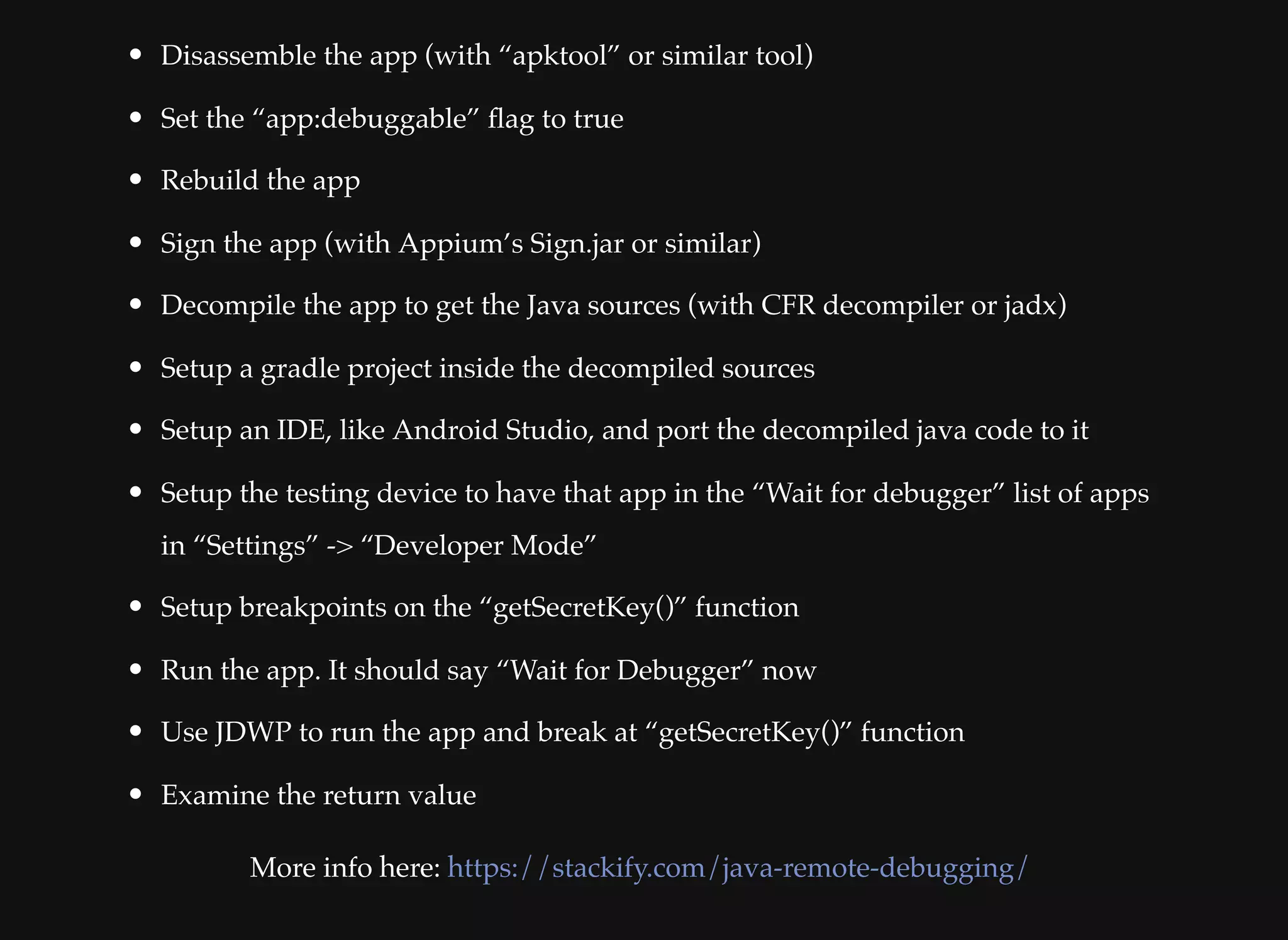
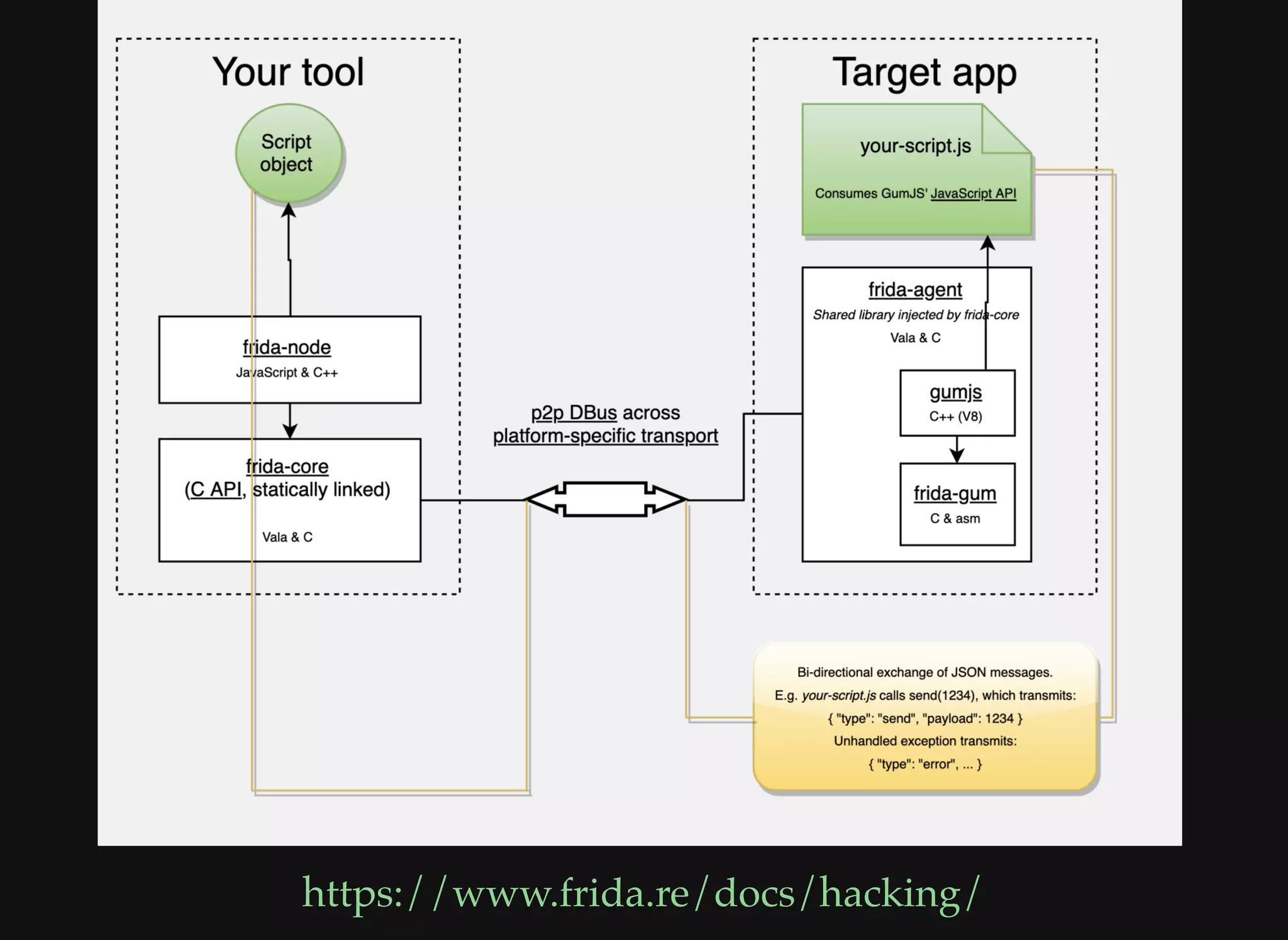
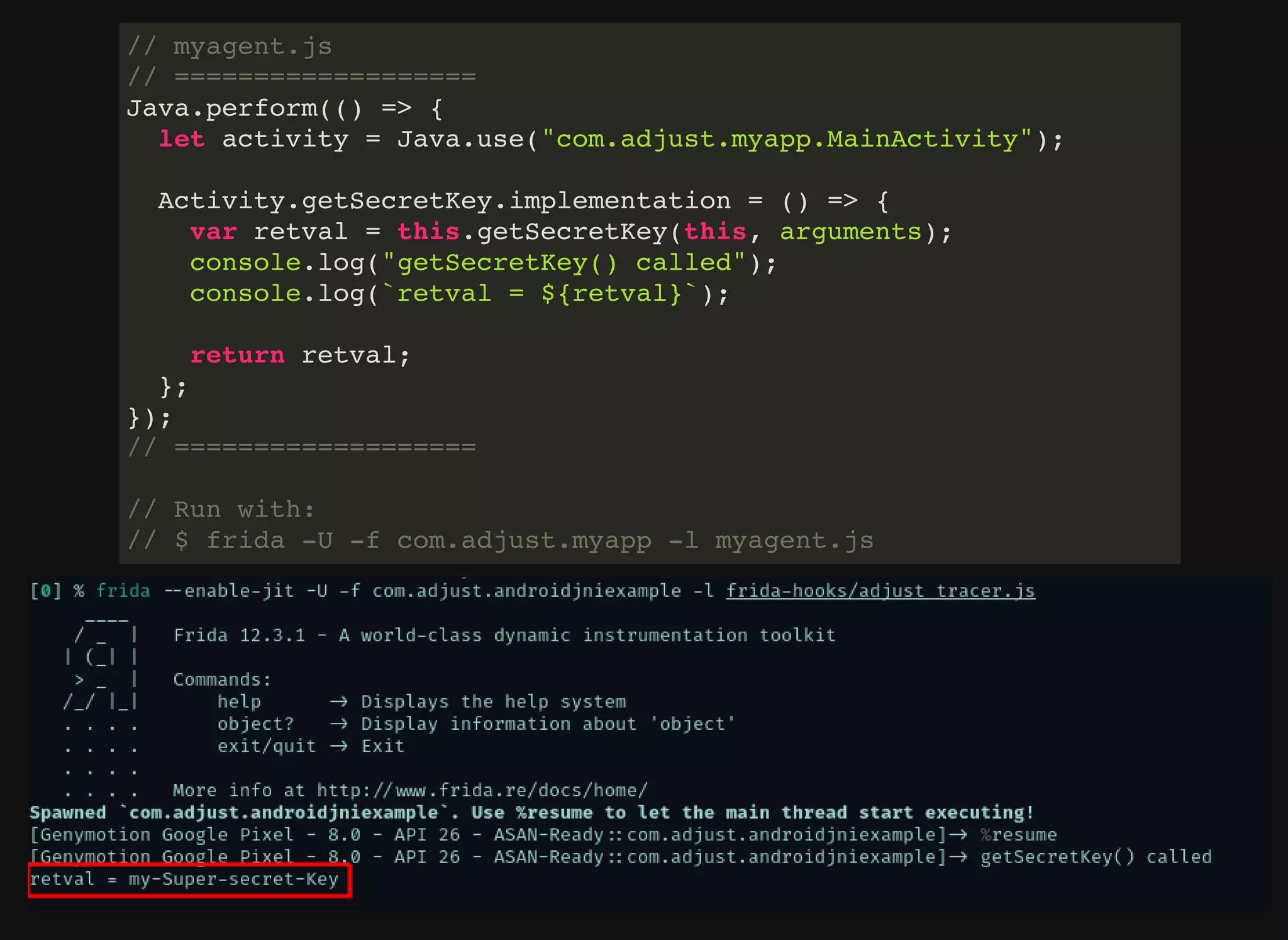
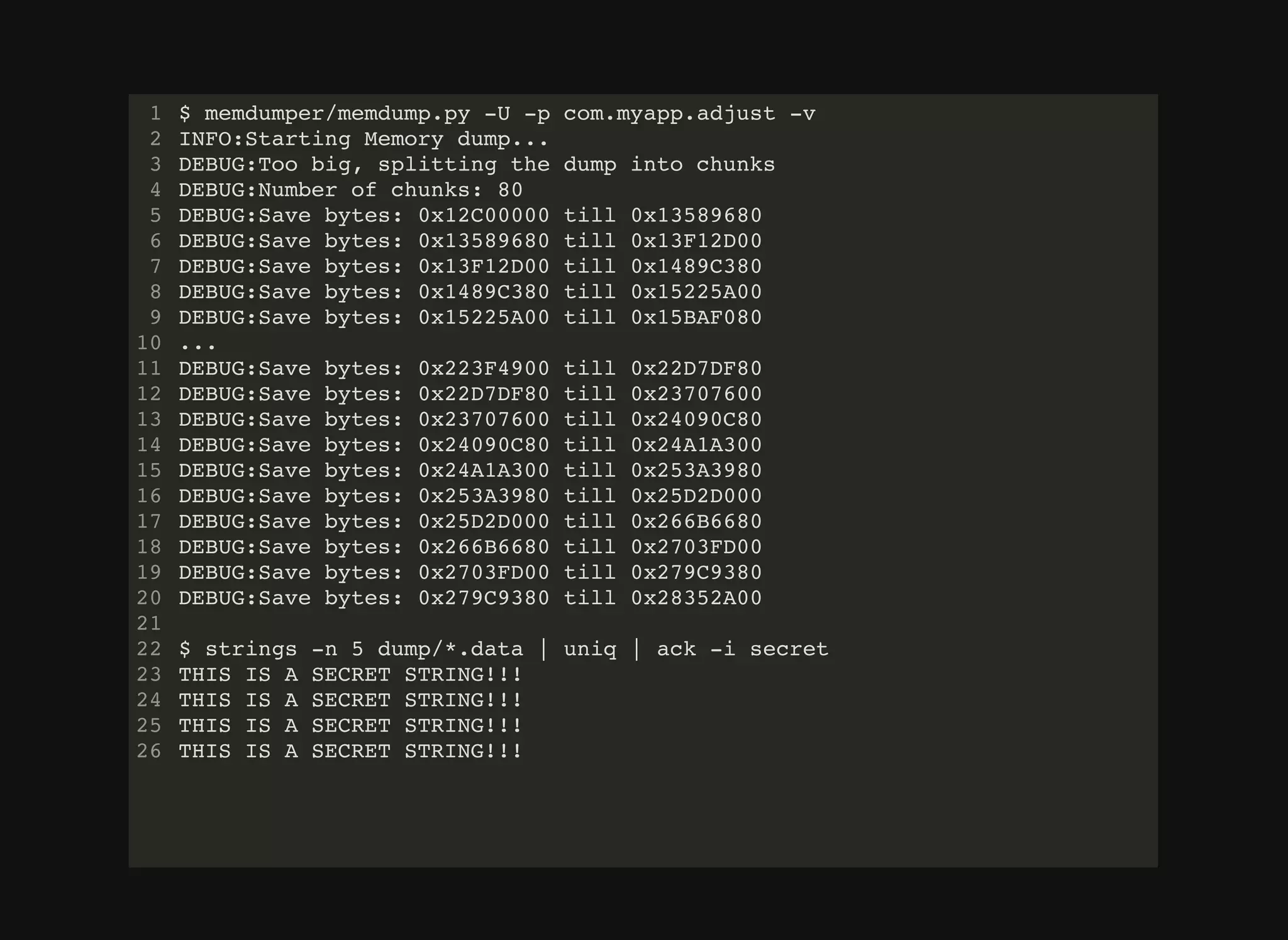
The document discusses various techniques for debugging and analyzing mobile applications, focusing on tools such as Frida, GDB, and APKTool. It highlights binary instrumentation, dynamic analysis, and the utilization of debugging functionalities to extract sensitive data like secret keys from apps. Additionally, it mentions specific use cases and offers resources for further exploration in mobile security and analysis.




![FindingsFindings
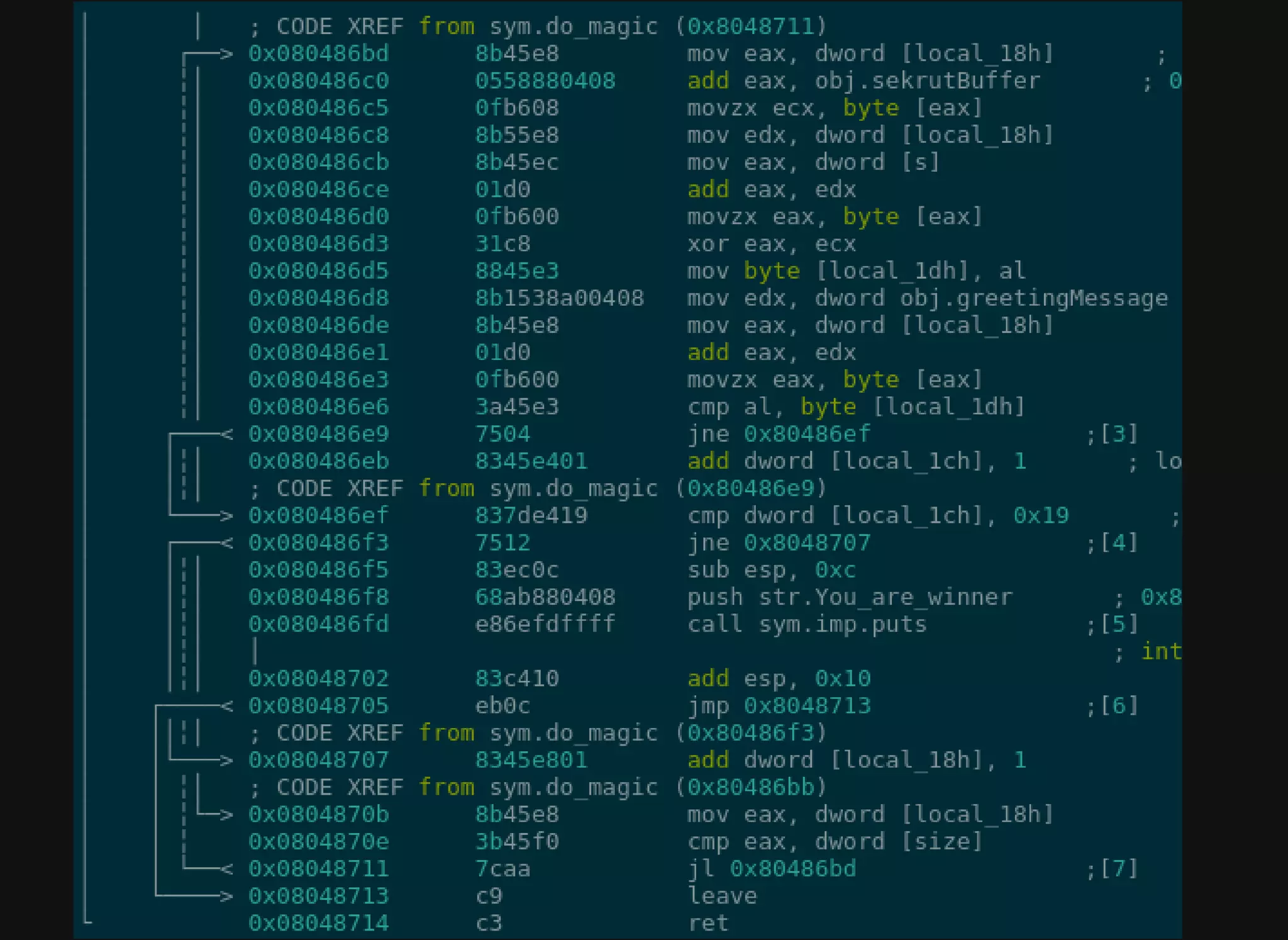
Code block takes input and puts it in [s]
At 0x080486d3, our input and obj.sekrutBuffer get XORed
together
The result has to equal obj.greetingMessage which gets
compared together in 0x080486e6
obj.sekrutBuffer holds the following byte
blob:
)x06x16O+50x1eQx1b[x14Kb]+Sx10TQCMT]](https://image.slidesharecdn.com/codeexecanalysisabdullahjosephnanosec19-191115052518/75/NanoSec-Conference-2019-Code-Execution-Analysis-in-Mobile-Apps-Abdullah-Joseph-9-2048.jpg)












![[0] % native_stalker/native_stalker.py
--process com.myapp.adjust
--library libnative-lib.so
--addr 0x00009610
--binary /path/to/my/app/libnative-lib.so
--verbose
INFO:Analyzing with R2...
INFO:Retrieving PLT section...
INFO:.plt [0x8AE0] -> [0x92D0]
INFO:Prepping Frida...
INFO:Resuming process...
INFO:Hooking library loaders...
JS: loaders(): {"0":"libnative-lib.so","1":38416,"2":35552,"3":37584}
INFO:Awaiting hook callbacks...
JS: Library [native-lib] loaded with java.lang.String.loadLibrary
[+] JS: stalk_func(): {"0":"libnative-lib.so","1":38416,"2":35552,"3":37584}
[+] JS: Library base addr: 0x8b2c1000
[+] JS: Hooking [0x8b2ca610]...
INFO:Tracing 38416@libnative-lib.so concluded with 11 calls:
0x8b80 -> sym.imp.free
0x8c40 -> fcn.00008c40
0x8b30 -> fcn.00008b30
0x8b90 -> fcn.00008b90
0x8c50 -> fcn.00008c50
0x8b40 -> sym.imp.fopen
0x8ba0 -> fcn.00008ba0
0x8bc0 -> fcn.00008bc0
0x8b70 -> sym.imp.getline
0x8c30 -> fcn.00008c30
0x8b20 -> sym.imp.__android_log_vprint
INFO:Done. You can exit the script now...
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31](https://image.slidesharecdn.com/codeexecanalysisabdullahjosephnanosec19-191115052518/75/NanoSec-Conference-2019-Code-Execution-Analysis-in-Mobile-Apps-Abdullah-Joseph-32-2048.jpg)