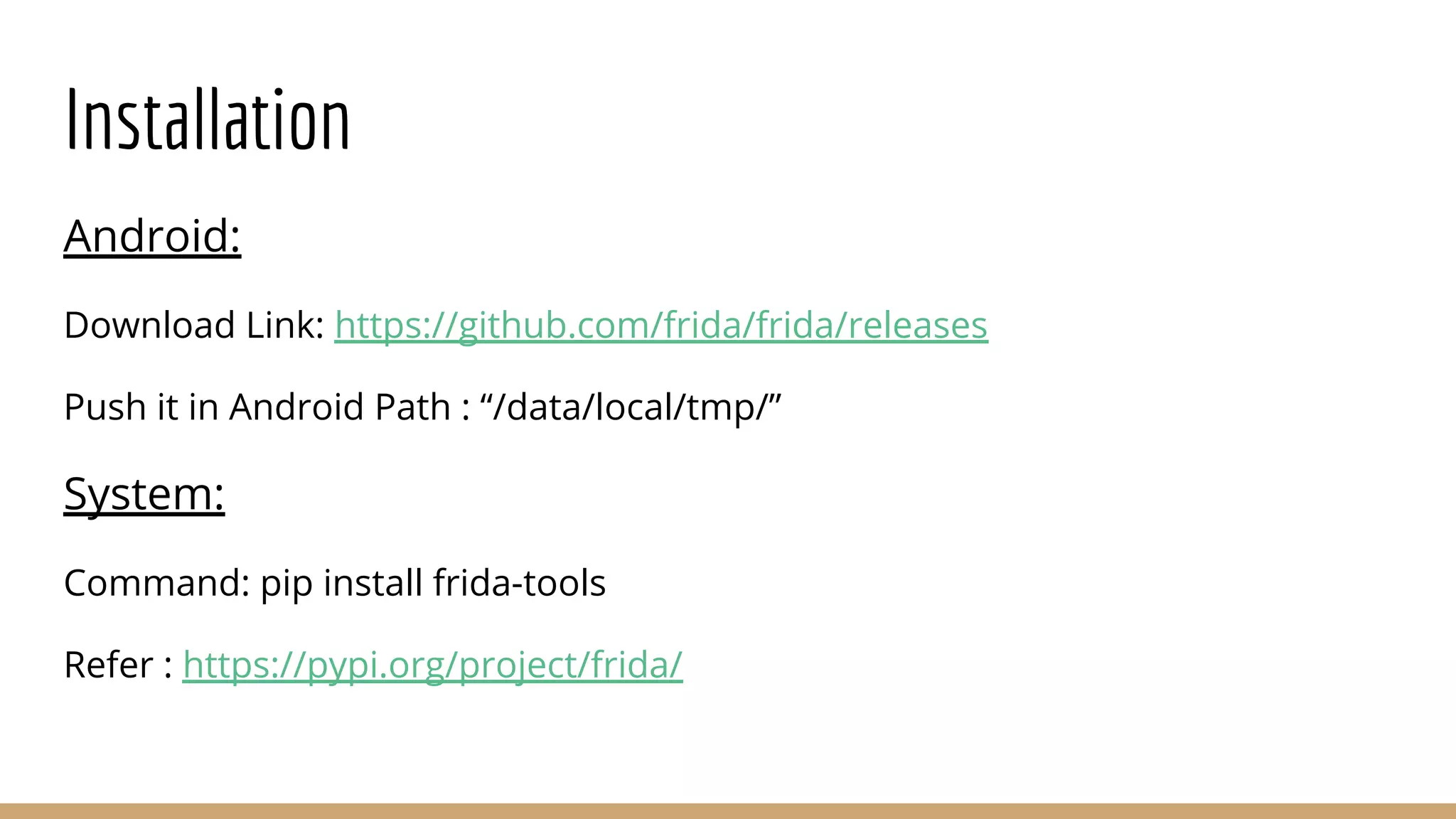
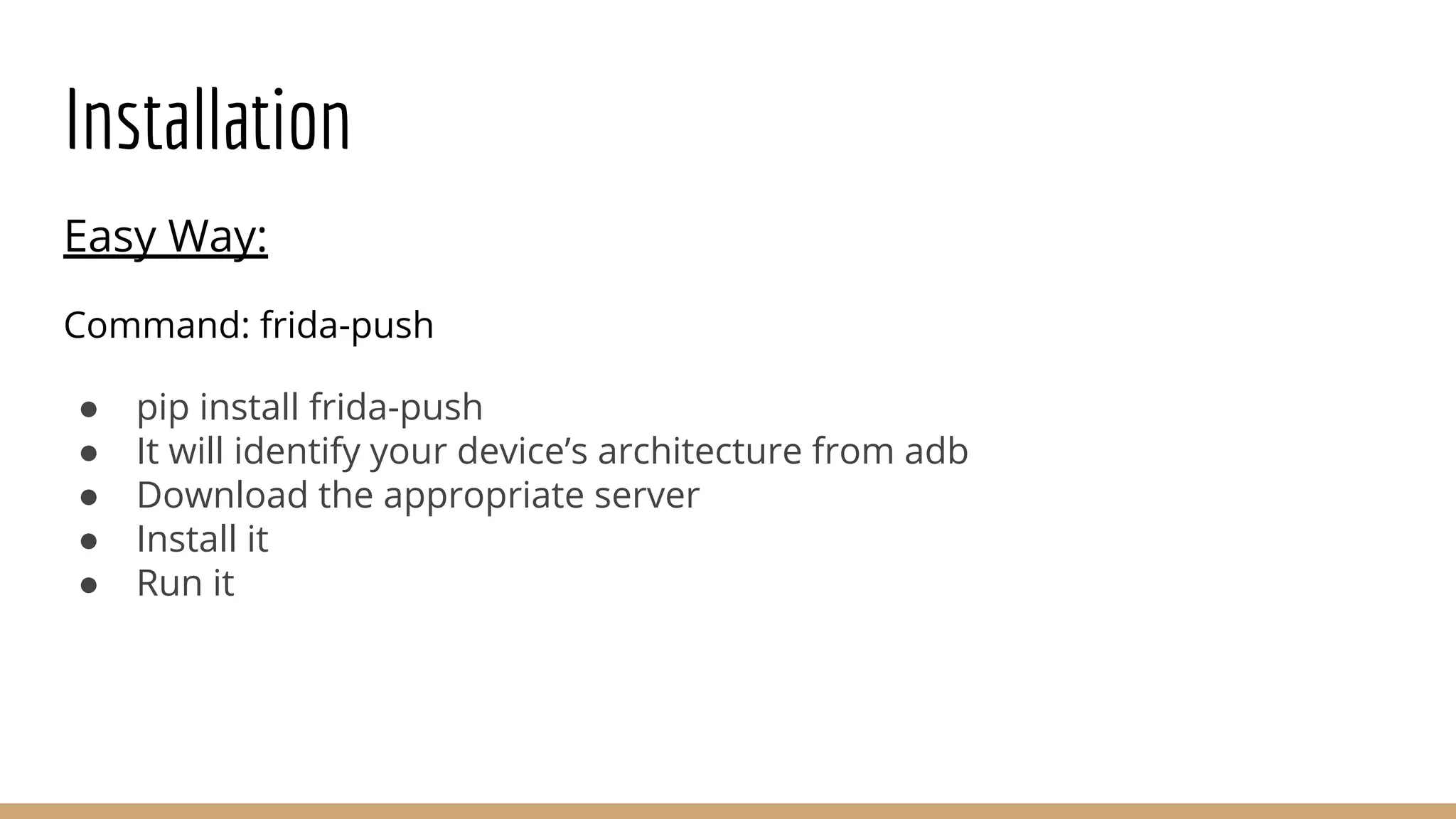
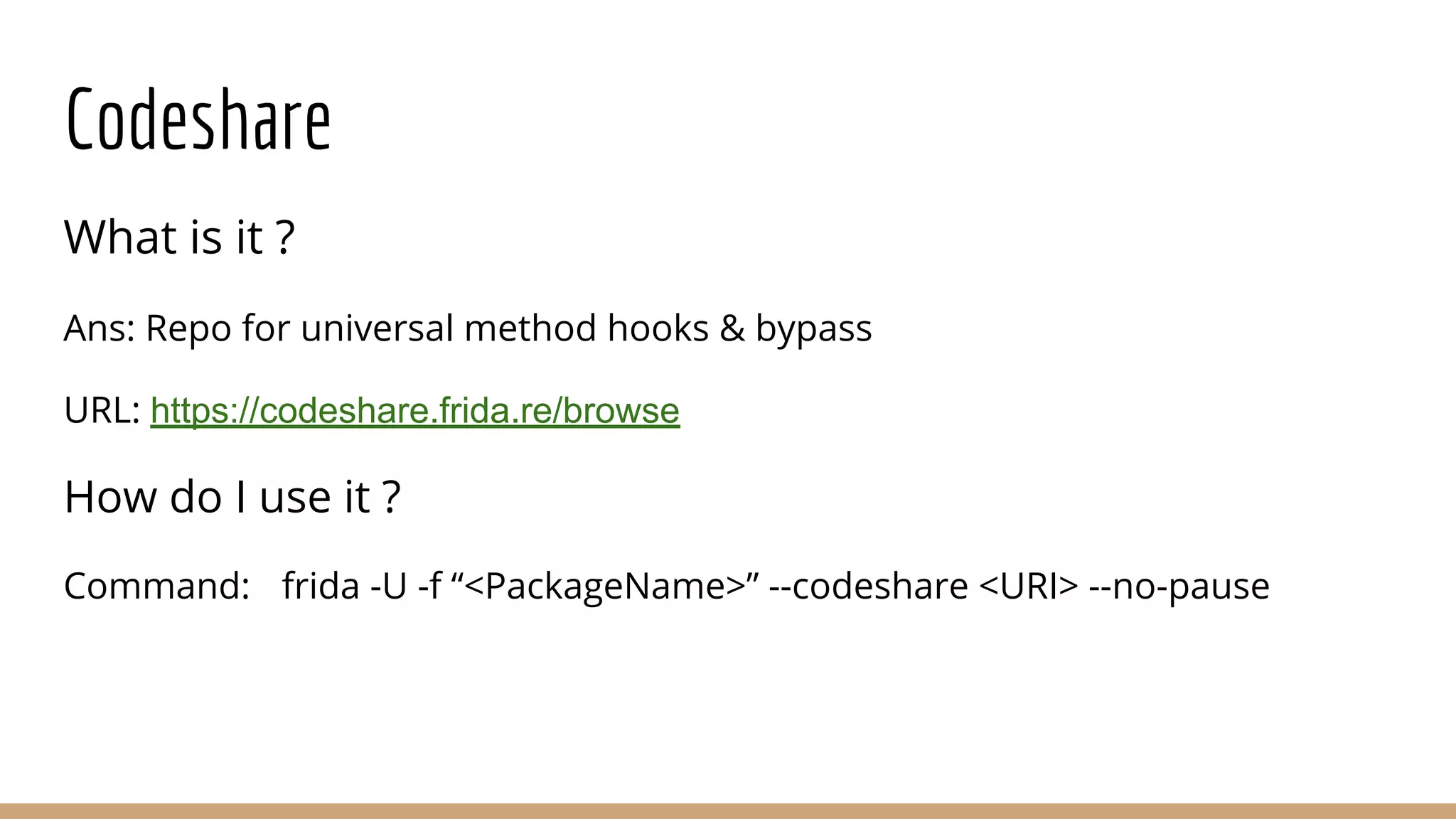
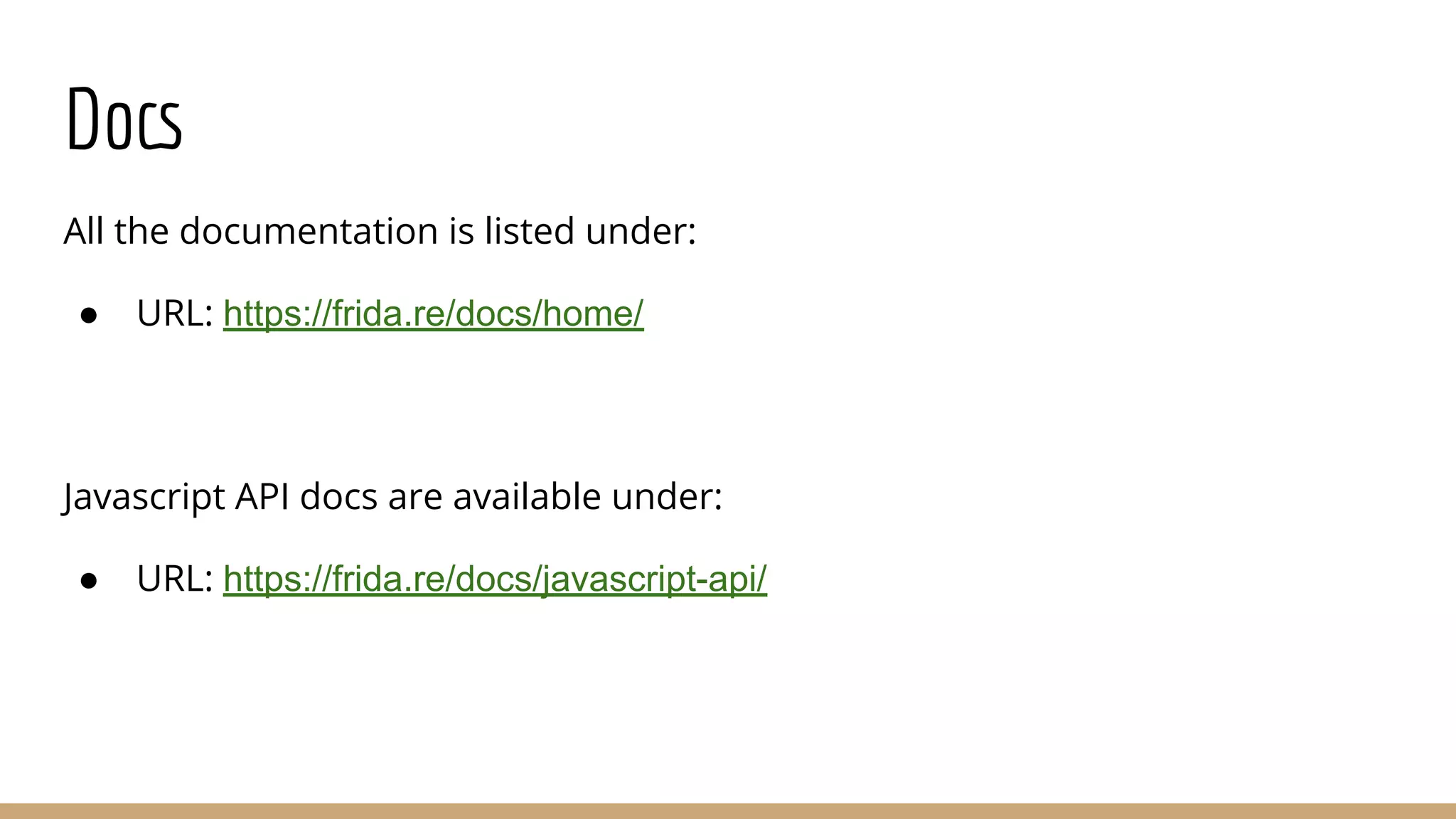
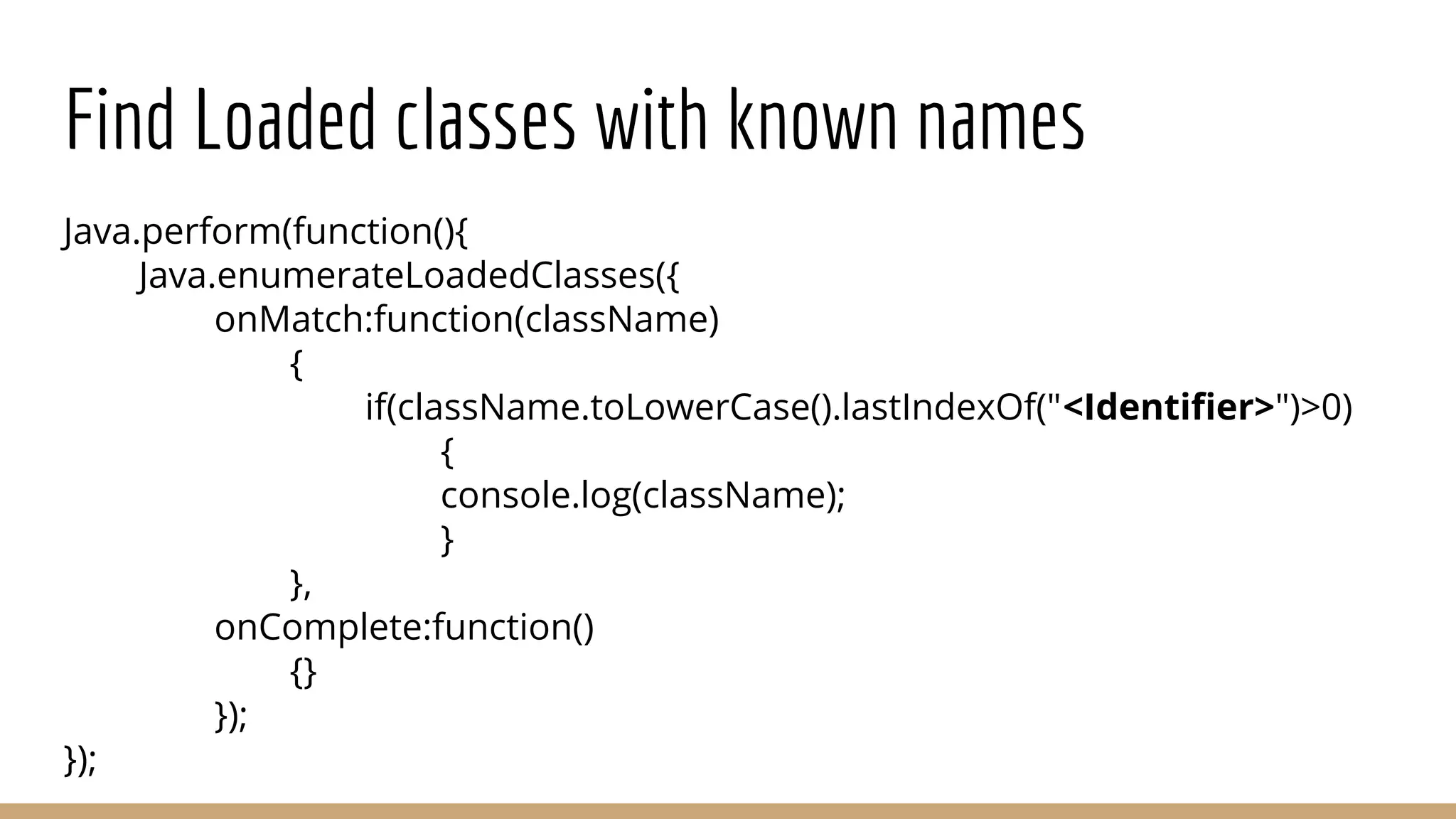
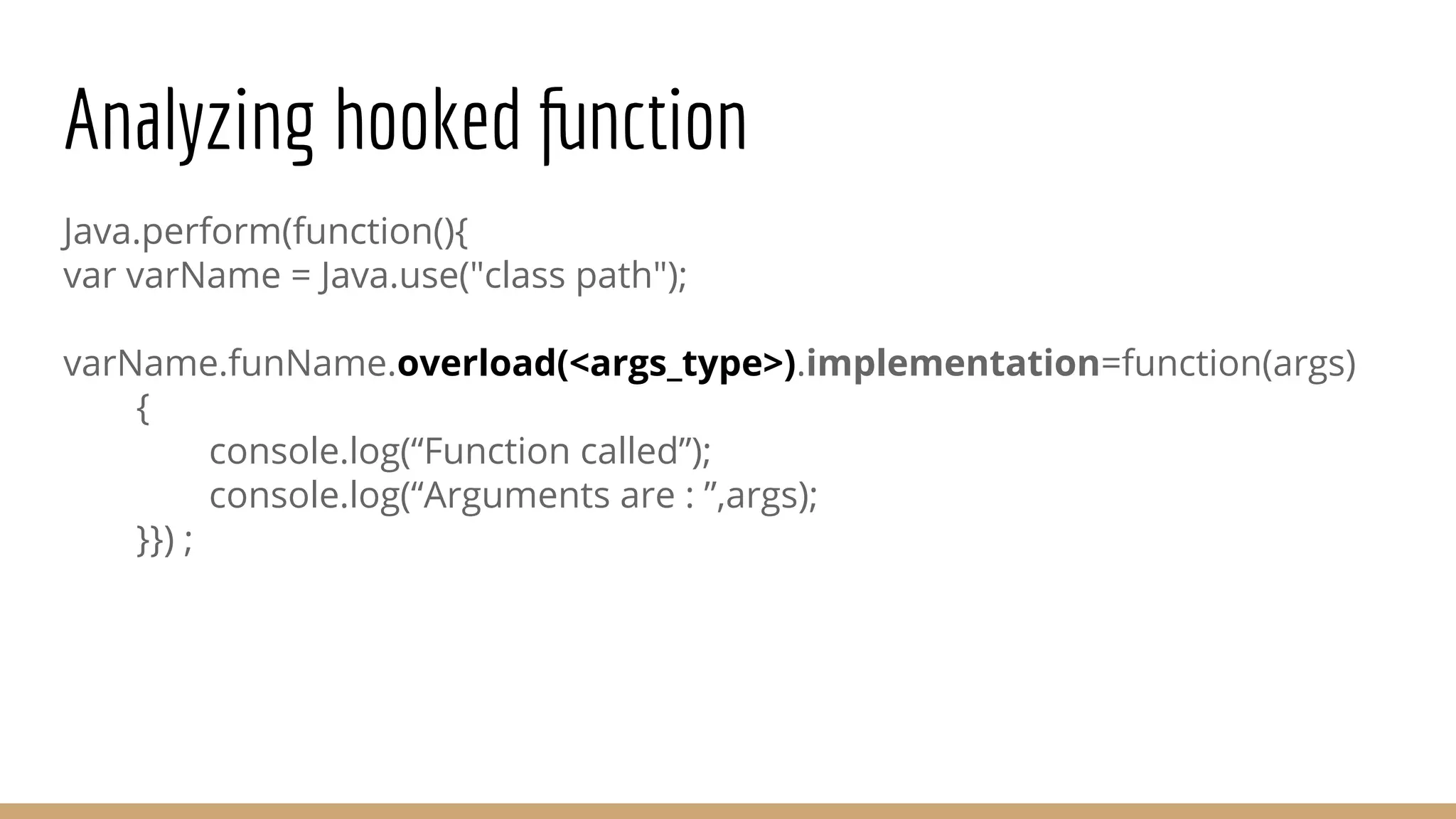
This document provides a comprehensive guide on using Frida for runtime debugging on Android, including installation steps, commands for starting and utilizing Frida for various tasks, and instructions for setting up a vulnerable environment. It also discusses methods for identifying and hooking functions within applications, with examples of scripts and code for effective usage. Additionally, it includes links to resources such as documentation and example applications to facilitate learning and application of the techniques described.