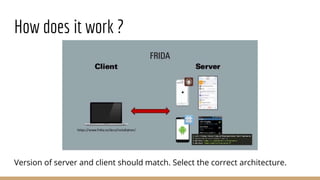
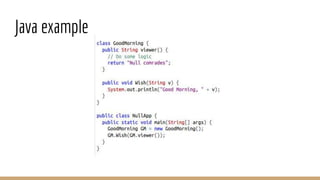
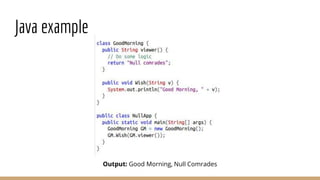
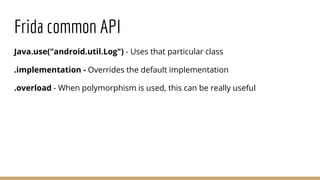
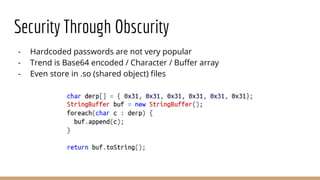
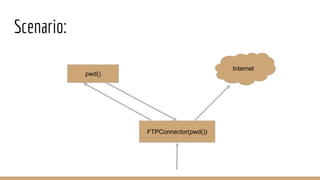
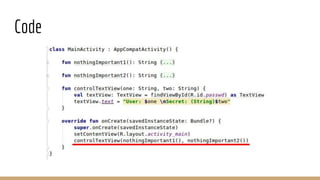
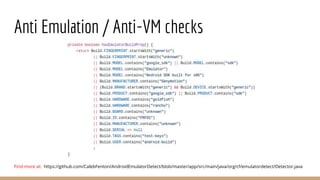
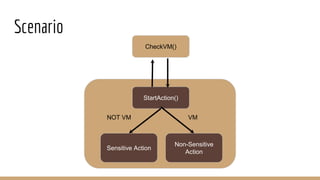
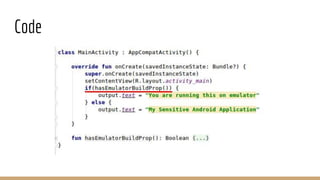
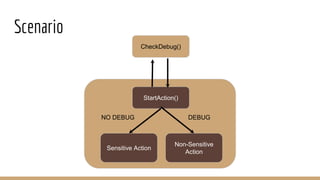
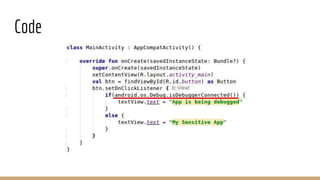
This document discusses using Frida, a dynamic instrumentation toolkit, to bypass security defenses in Android apps. It provides an introduction to Frida and how it works, describes common Android app defenses like anti-debugging and anti-emulation checks, and demonstrates how to use Frida to bypass some of these defenses through code injection and interception. The document contains code examples and promises a demo of using Frida to monitor and intercept methods in an Android app in real-time.