This document provides an outline for a lecture on software security. It introduces the lecturer, Roman Oliynykov, and covers various topics related to software vulnerabilities like buffer overflows, heap overflows, integer overflows, and format string vulnerabilities. It provides examples of vulnerable code and exploits, and recommendations for writing more secure code to avoid these vulnerabilities.





![Consequences of cyberattacks
for the society
[Norton/Symantec cybercrime report, 2013]](https://image.slidesharecdn.com/bergensoftwaresecurity-150603113550-lva1-app6892/85/Software-Security-8-320.jpg)
![Consequences of cyberattacks
for the society
[Norton/Symantec cybercrime report, 2013]](https://image.slidesharecdn.com/bergensoftwaresecurity-150603113550-lva1-app6892/85/Software-Security-9-320.jpg)
![Consequences of cyberattacks
for the society
[Norton/Symantec cybercrime report, 2013]](https://image.slidesharecdn.com/bergensoftwaresecurity-150603113550-lva1-app6892/85/Software-Security-10-320.jpg)




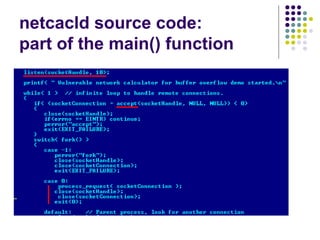


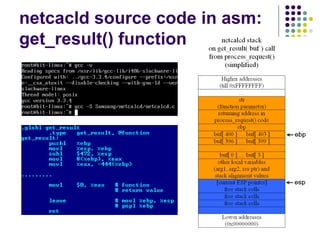
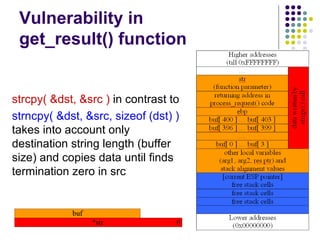
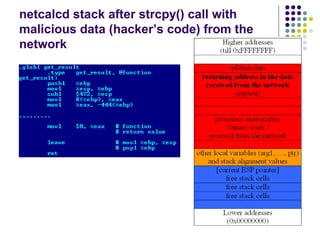
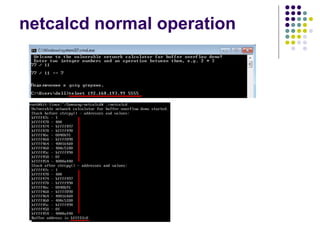
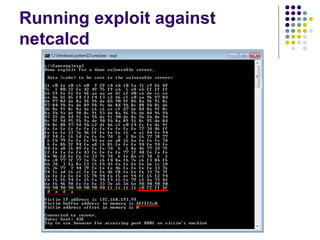


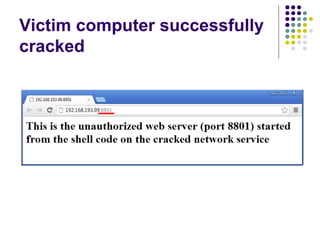
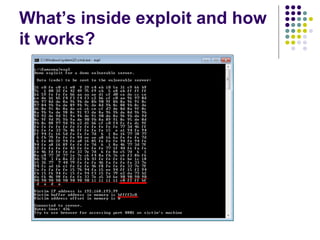
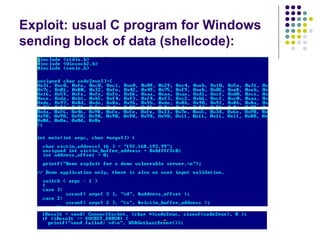

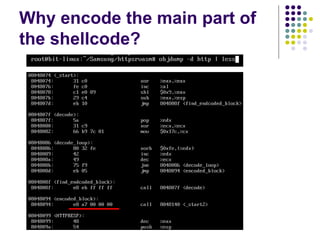



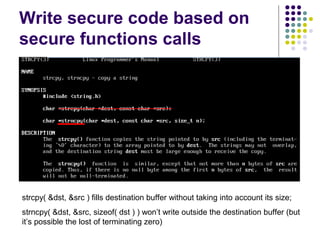

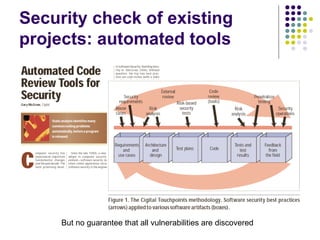







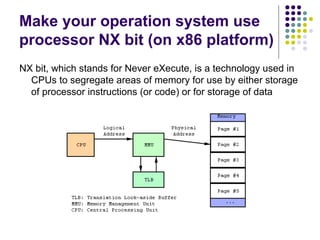
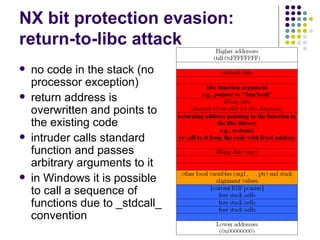







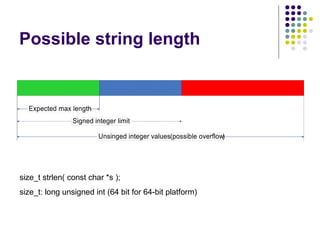



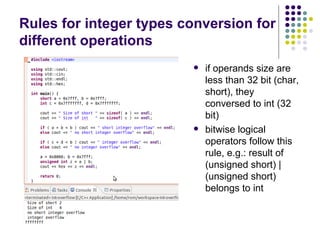
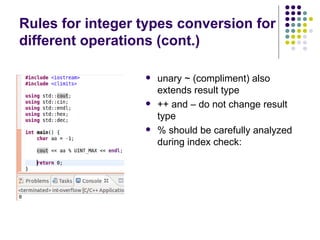
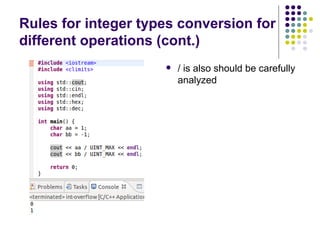







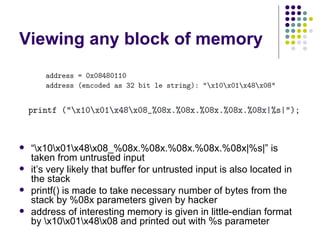

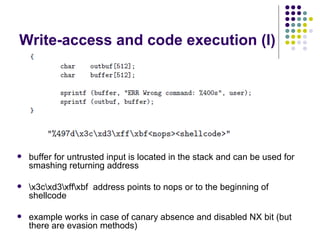

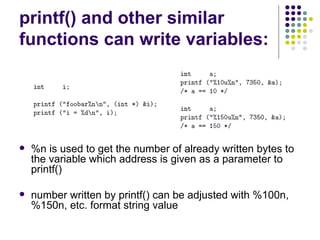
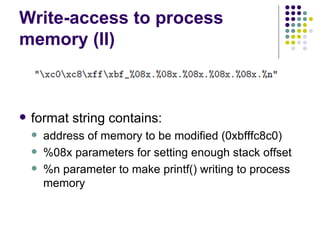
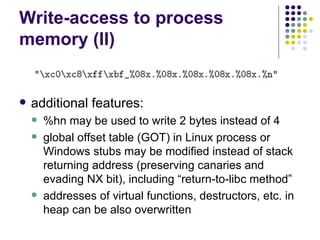
![Write-access to process memory (II):
tasks for exploiters
find format-string vulnerability
find a block of code putting parameter to the
stack
write a basic sequence for format string
find an offset in stack for taking parameters
and addresses
in case of code execution (not only memory
read/write): ASLR, canary and NX bit evasion
[beyond this attack]](https://image.slidesharecdn.com/bergensoftwaresecurity-150603113550-lva1-app6892/85/Software-Security-88-320.jpg)