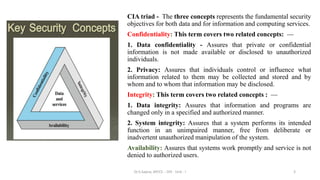
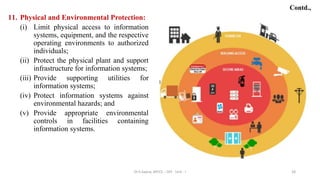
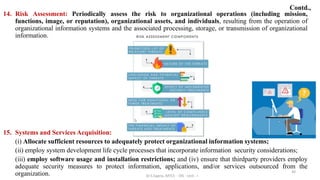
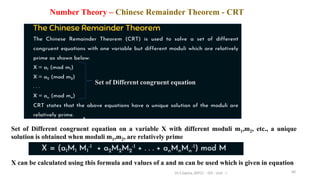
This document discusses computer security concepts and fundamentals. It defines computer security and the CIA triad of confidentiality, integrity and availability. It describes various security objectives like data confidentiality, privacy, data integrity, system integrity and availability. It also discusses additional concepts like authenticity and accountability. The document presents a model for computer security and discusses security concepts like assets, vulnerabilities, threats, attacks and countermeasures. It provides examples of different types of attacks like unauthorized disclosure, deception and disruption and how they relate to threats against confidentiality, integrity and availability.