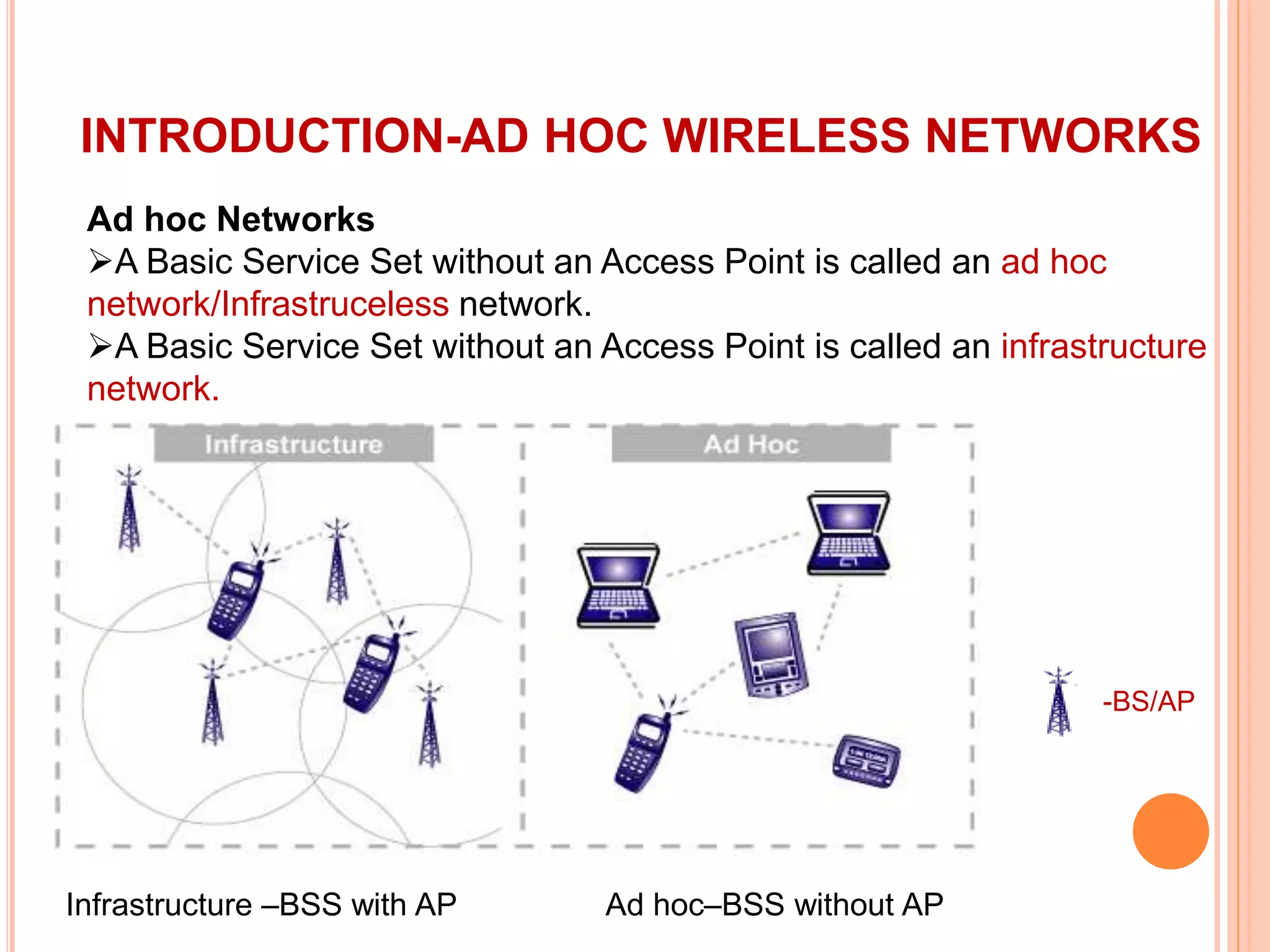
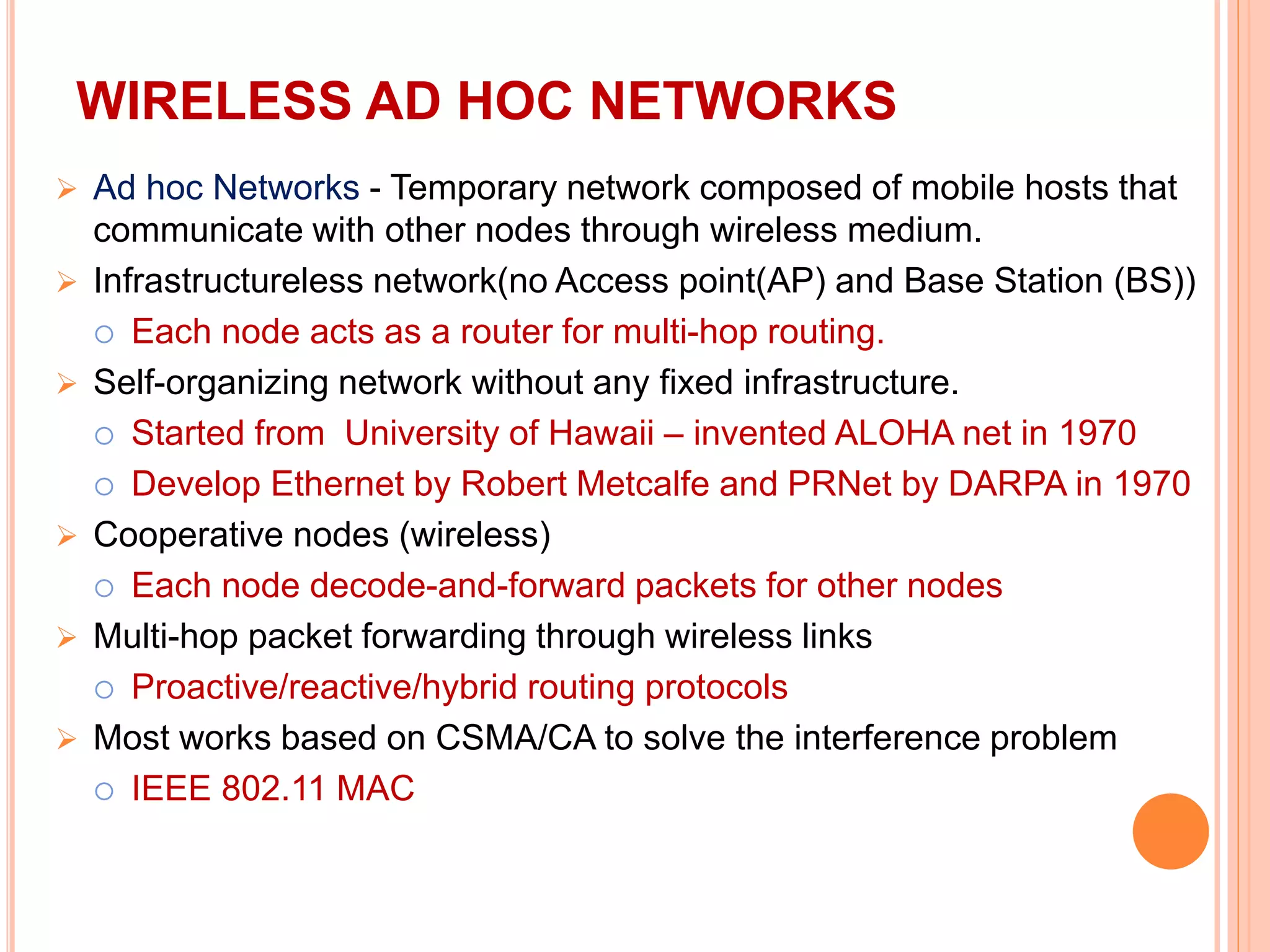
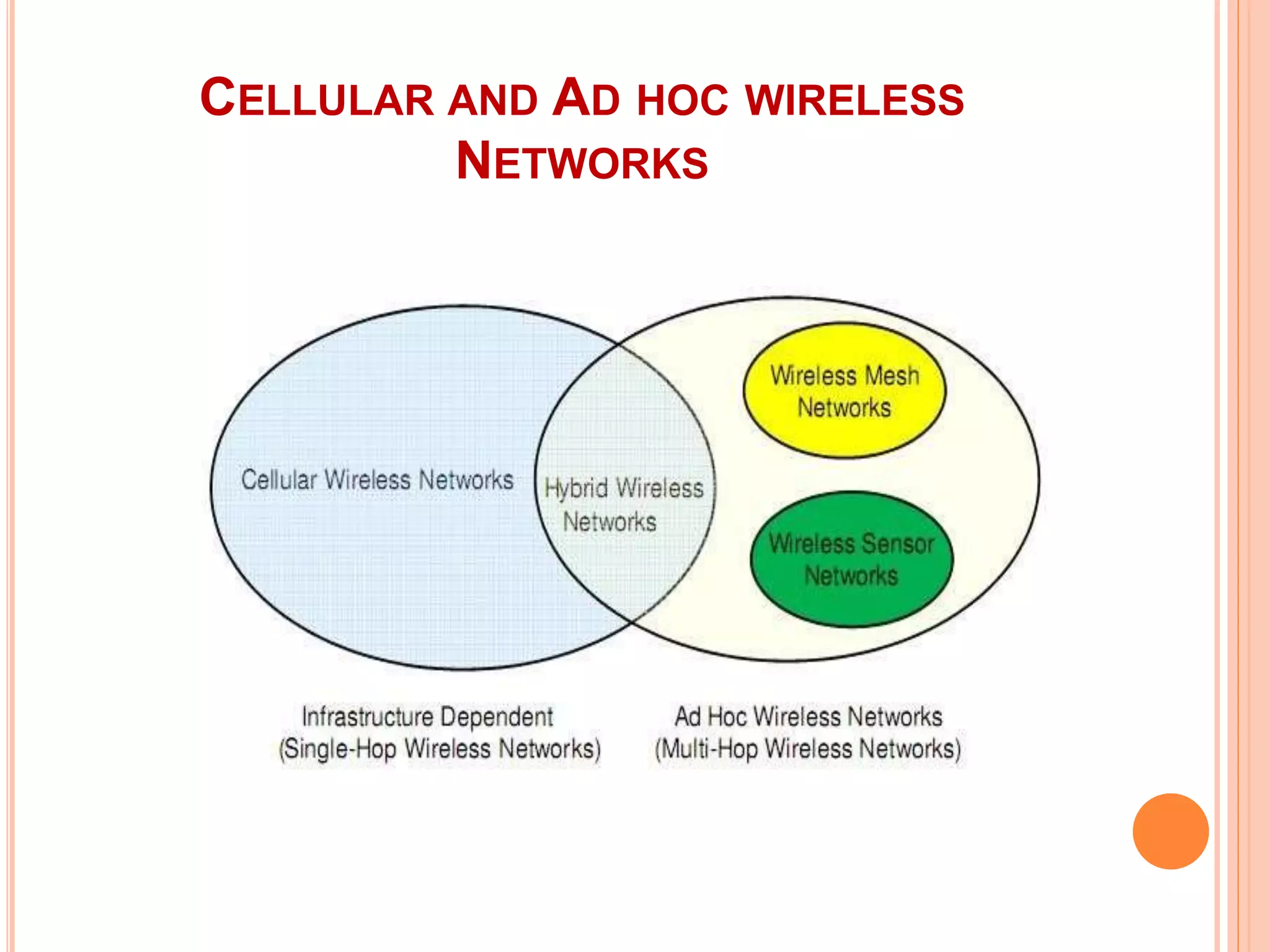
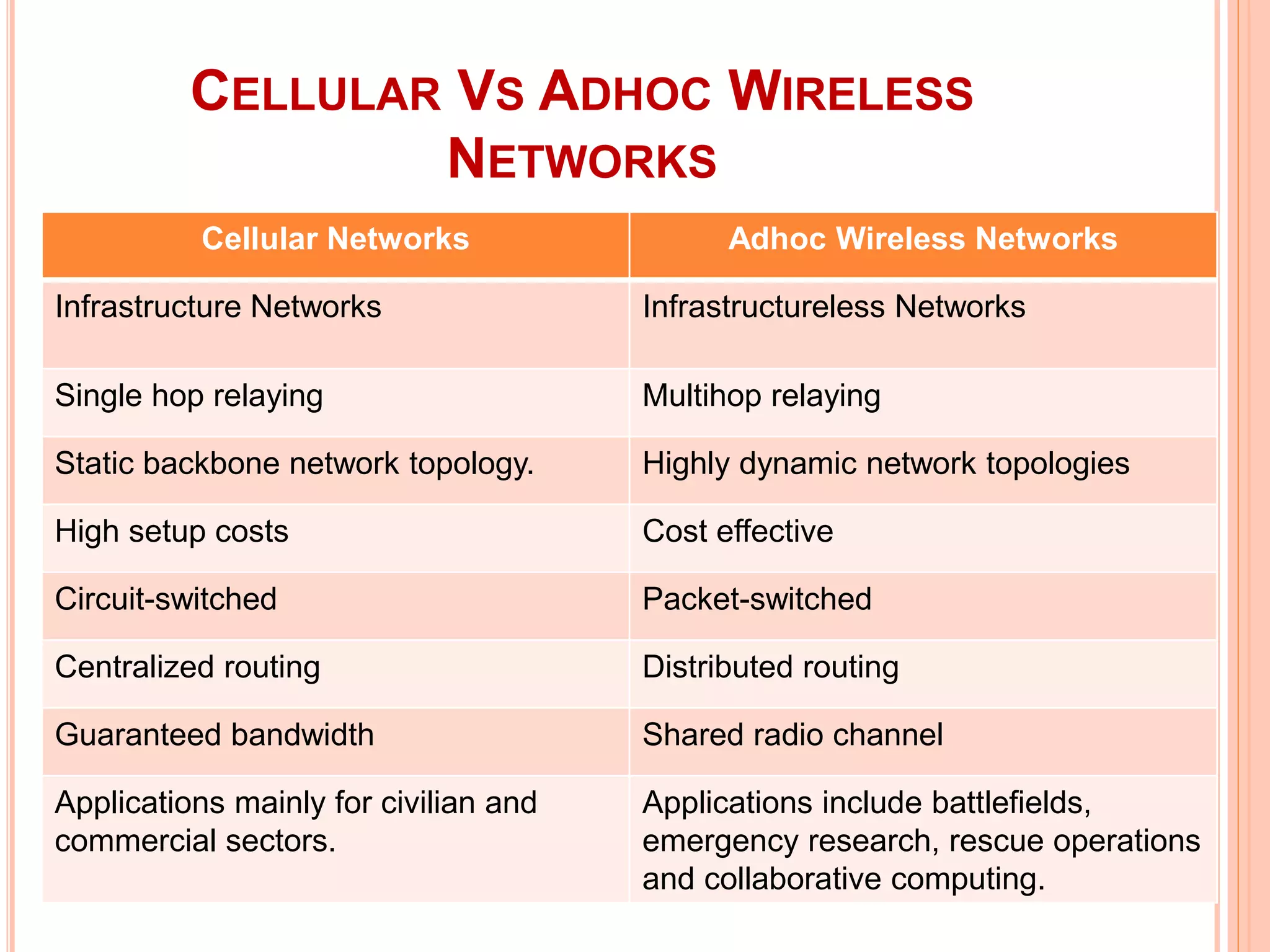
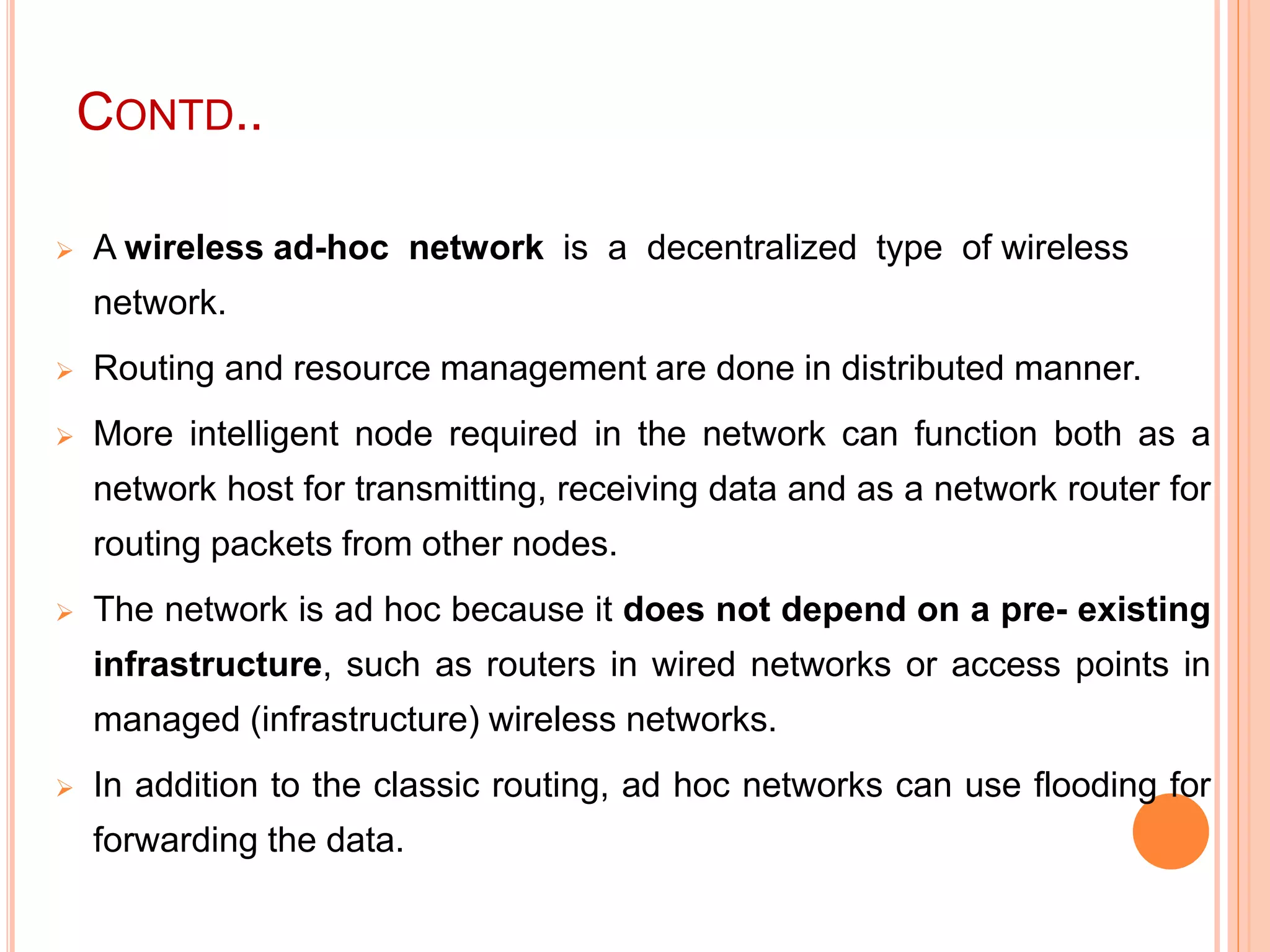
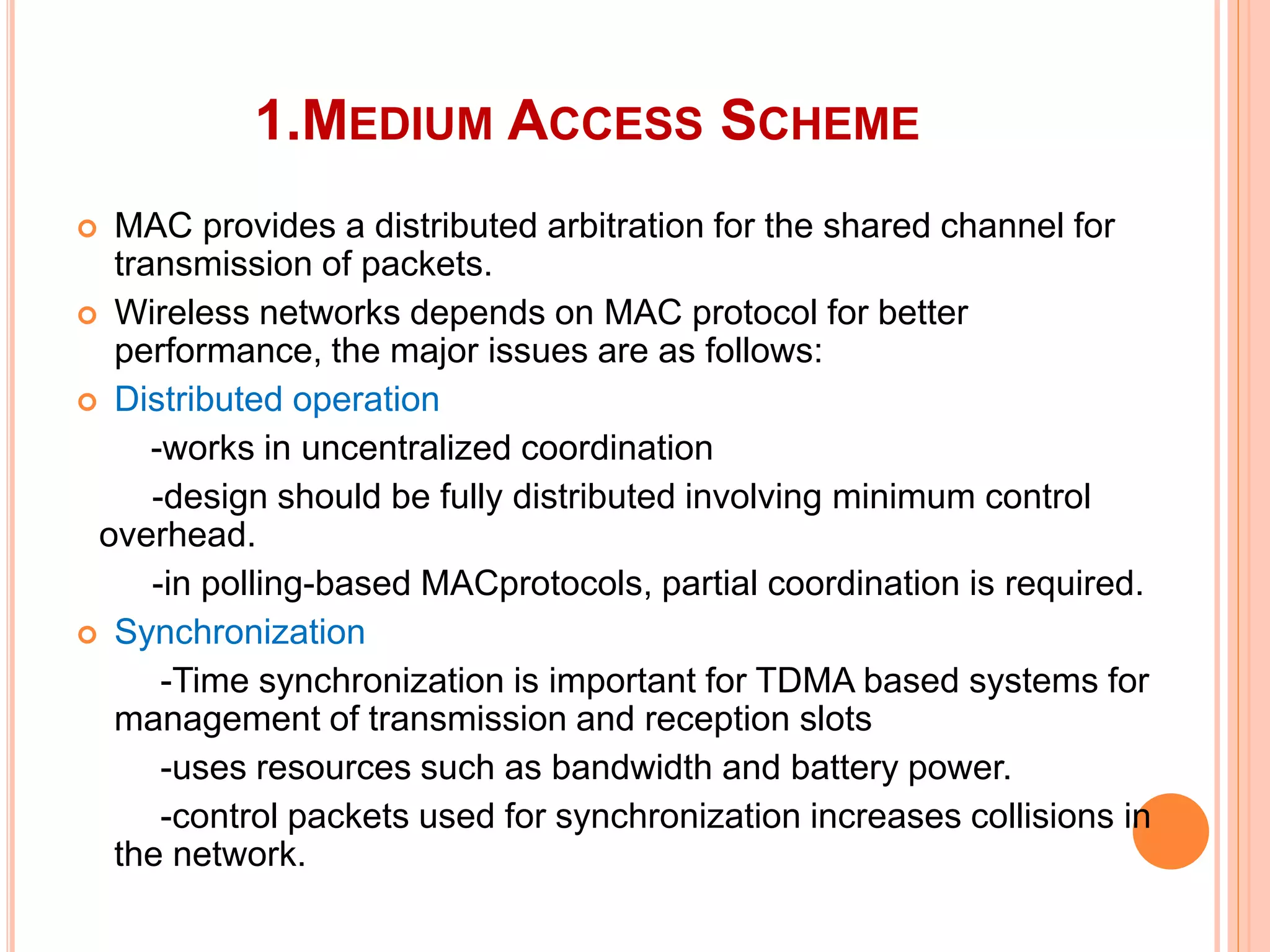
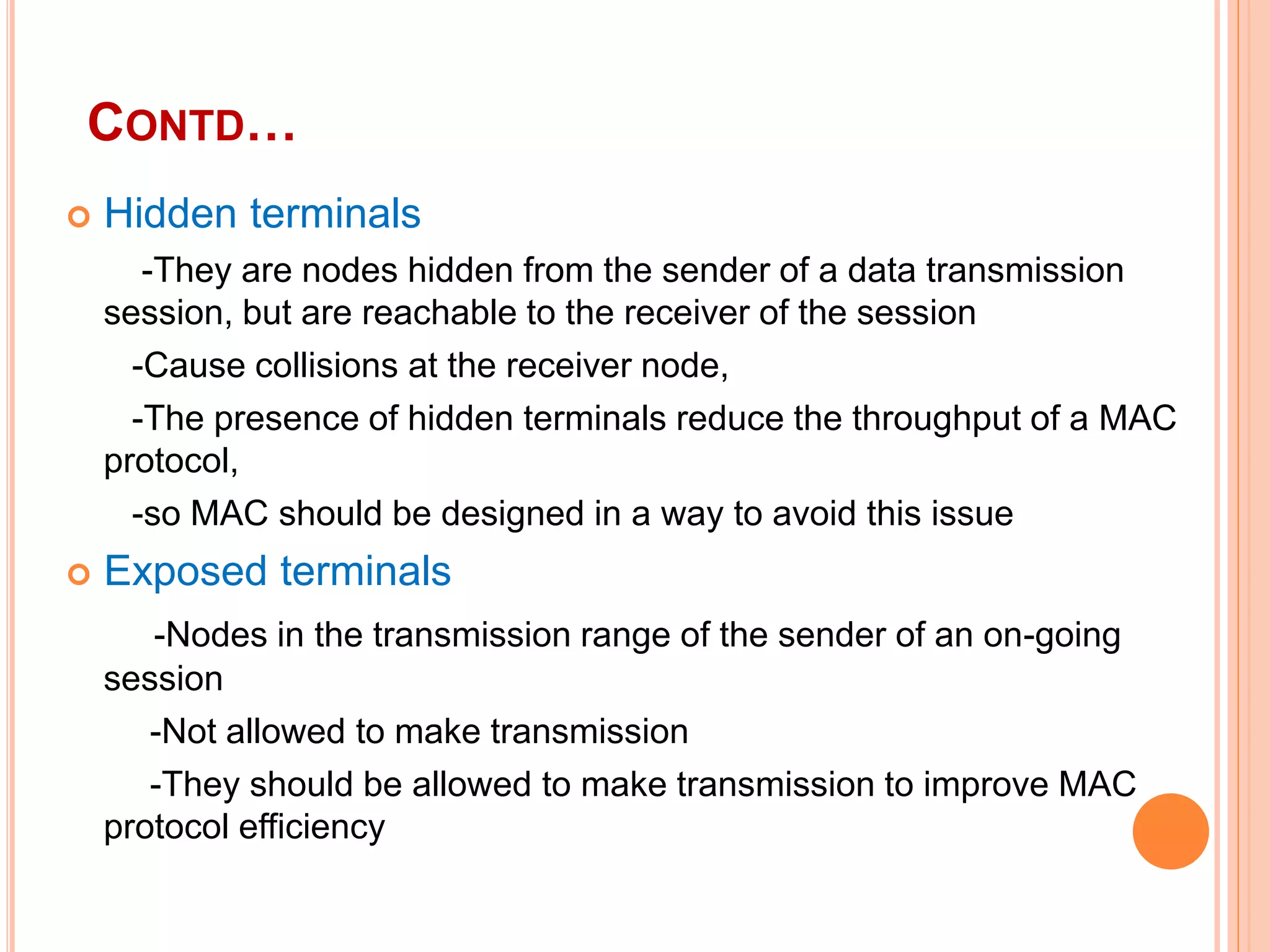
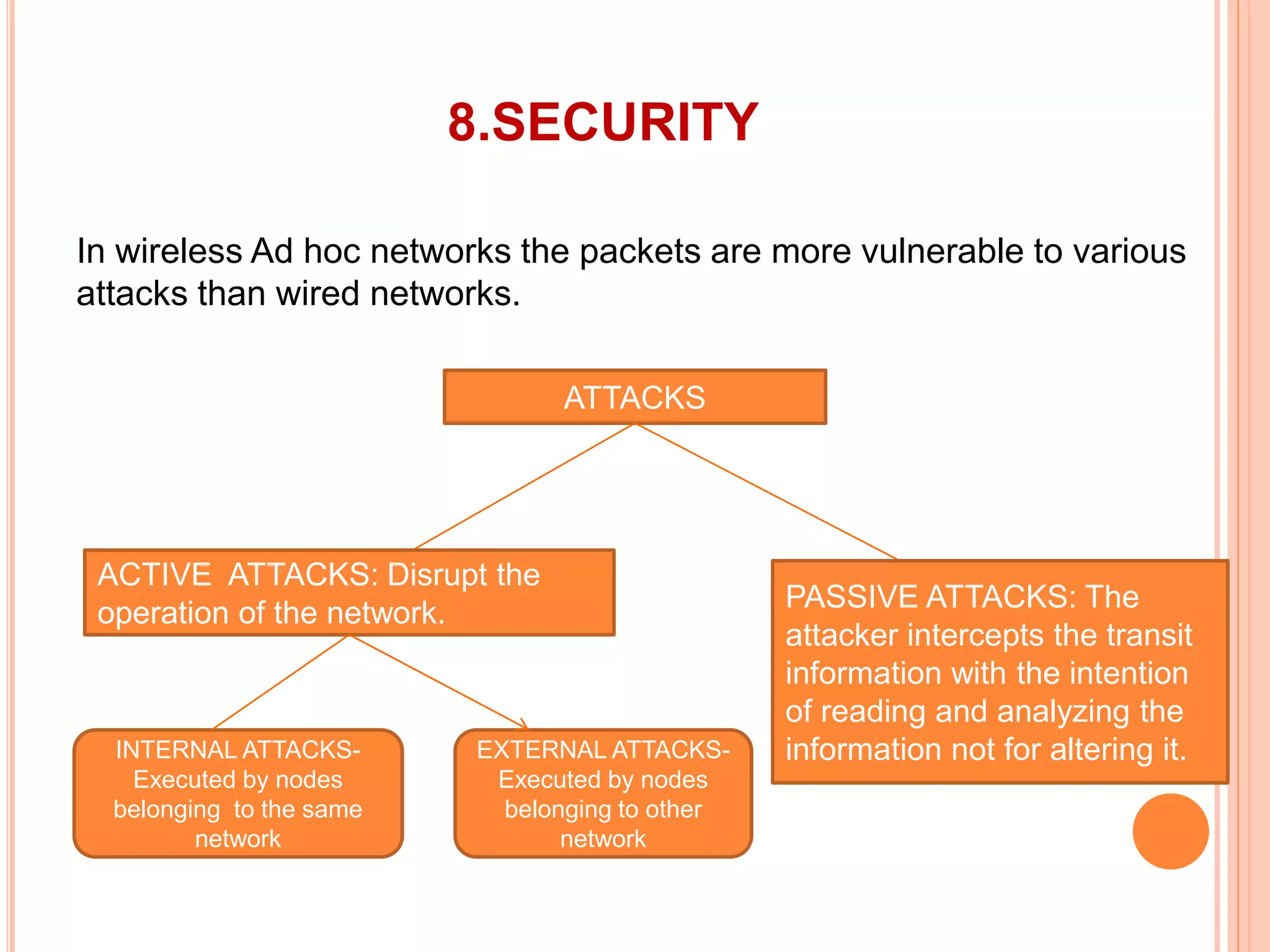
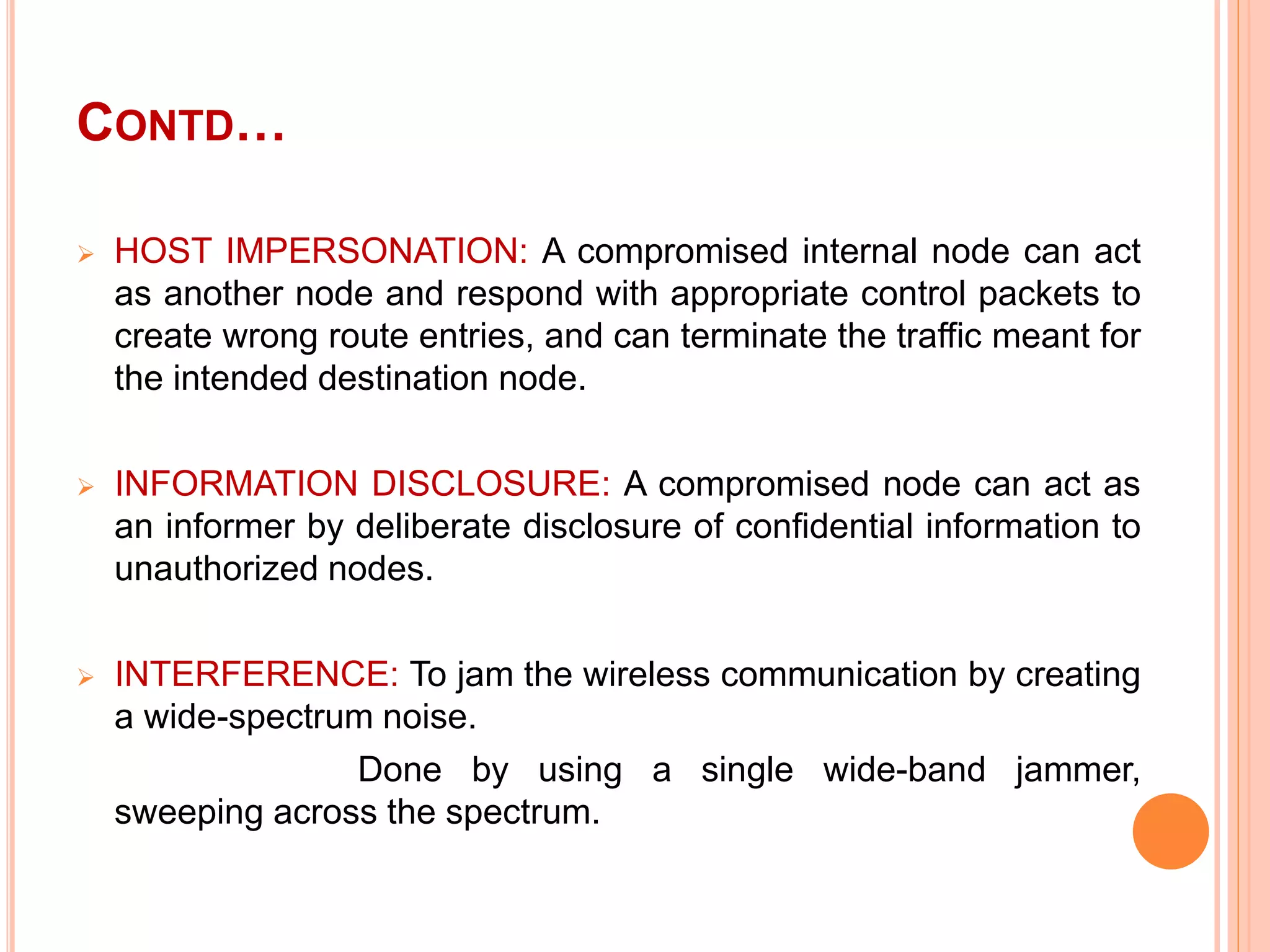
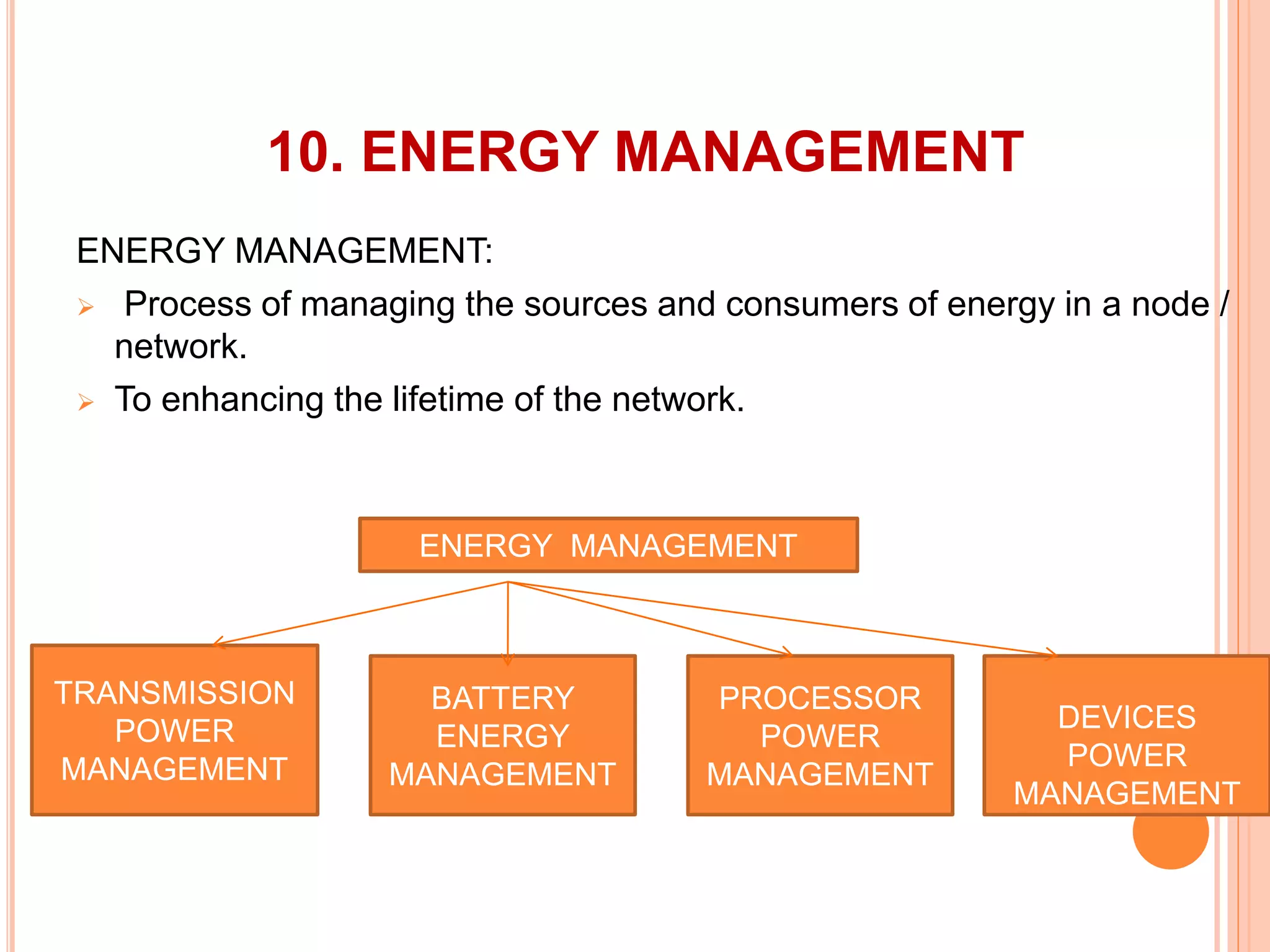
The document provides an overview of ad hoc wireless networks, detailing their characteristics, routing protocols, and various issues affecting their design and performance. It highlights the infrastructureless nature of these networks, the importance of routing and medium access control protocols, and challenges like scalability, security, and quality of service. Additionally, the document discusses the elements of ad hoc networks, including their applications, energy management, and implications of node mobility.