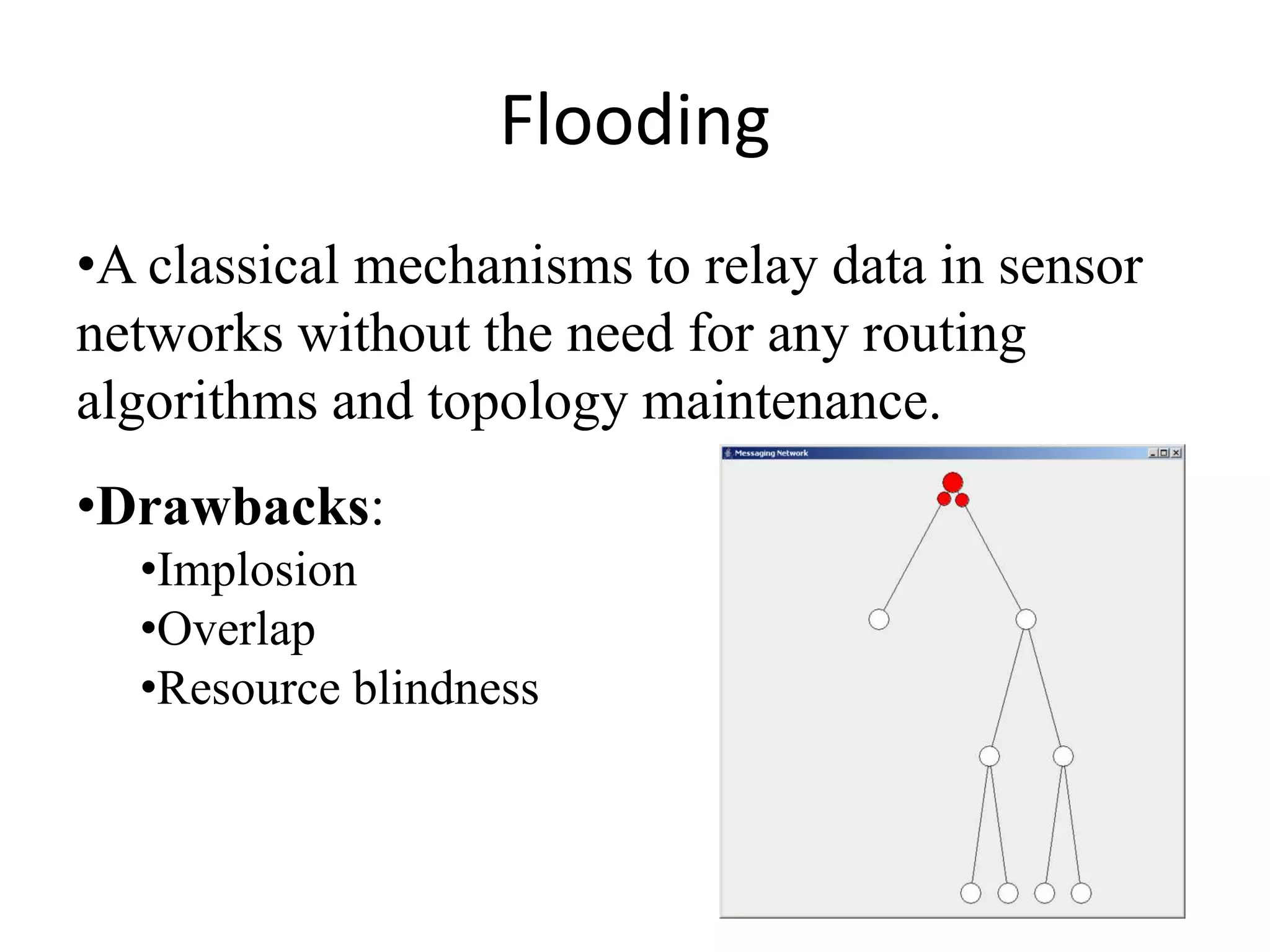
This document discusses wireless sensor networks and routing protocols for wireless sensor networks. It defines what a wireless sensor network is and its key characteristics. It then discusses objectives like understanding ad hoc network basics and various routing protocols. It covers topics like the differences between WSNs and ad hoc networks, what a network simulator is and reasons for using NS2, various routing techniques like flooding, gossiping, and hierarchical routing. It also discusses routing challenges, wireless nodes, packet transmission, applications and the future scope of WSNs.