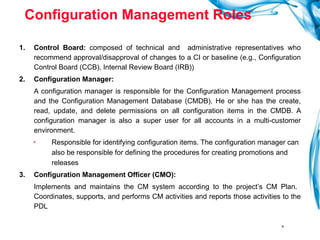
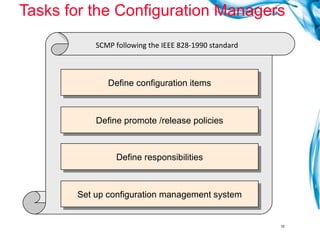
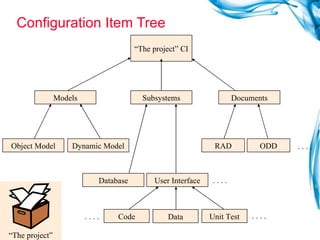
The document discusses various roles and responsibilities in software configuration management. It describes the roles of configuration control board, configuration manager, configuration item owner, configuration librarian, configuration auditor, support manager, and person in a role. It also discusses configuration management tools, selecting configuration items, configuration audits, and the configuration librarian role.