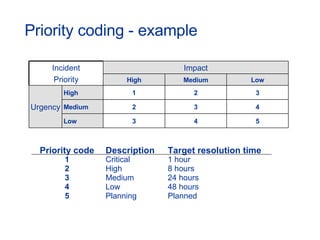
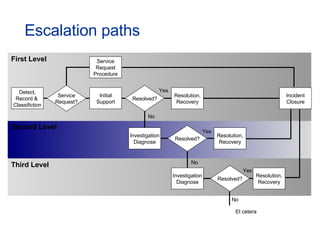
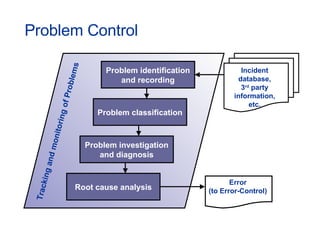
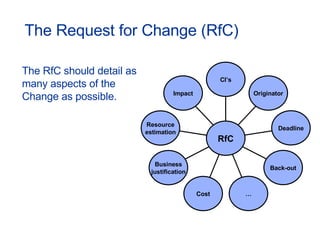
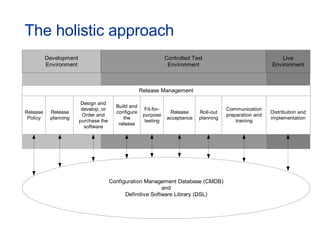
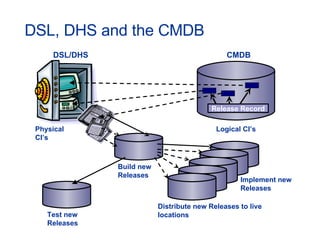
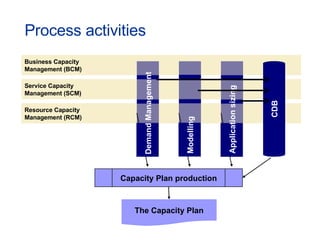
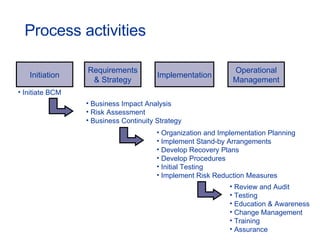
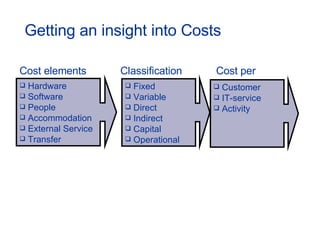
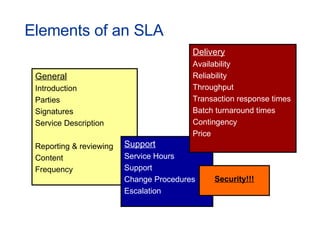
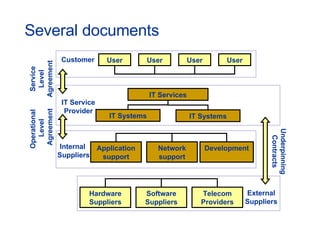
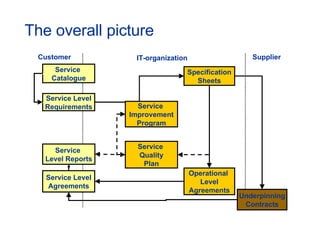
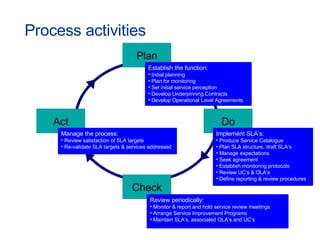
The document provides an overview of an ITIL Foundation course, including its objectives, agenda, and content. The key points are:
- The course aims to increase understanding of IT service management processes and concepts based on ITIL best practices.
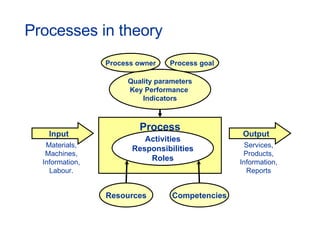
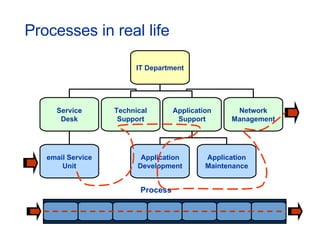
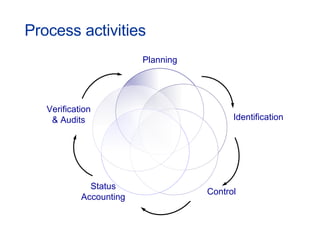
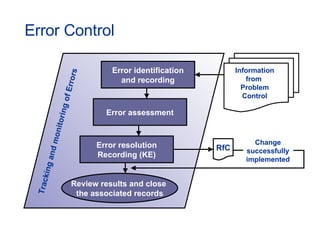
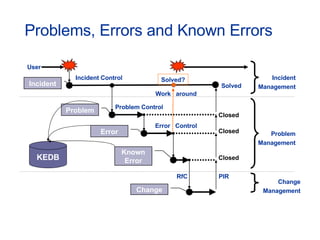
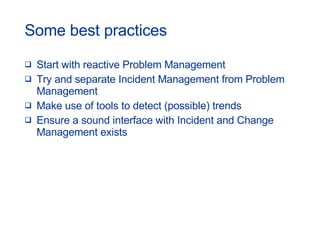
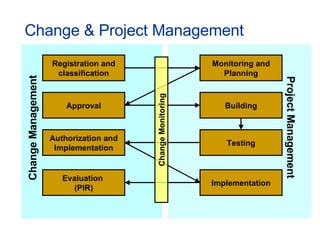
- Topics covered include service desk, incident management, problem management, change management, and other ITIL processes.
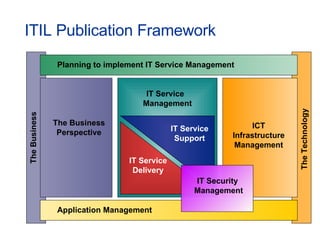
- ITIL is a collection of best practices for IT service management and has become the de facto international standard.