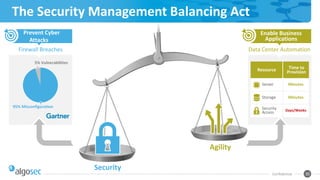
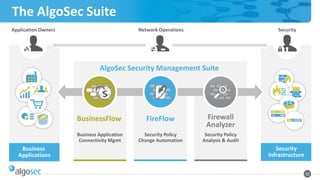
The document discusses the importance of network segmentation for enhancing security against potential attacks, highlighting expert insights from Mark Wolfgang of Shorebreak Security. It outlines various methods of segmentation, common mistakes organizations make, and the steps needed to effectively implement segmentation in a business context. The need for a comprehensive understanding of assets, personnel, and their access requirements is emphasized as crucial for reducing risks and improving network security.