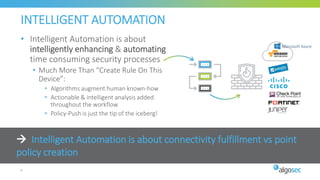
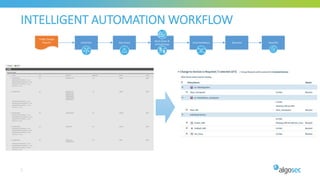
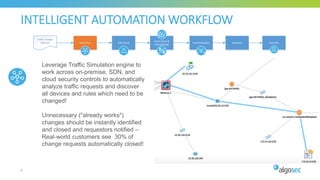
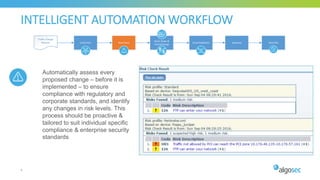
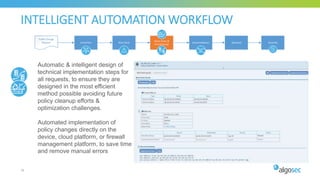
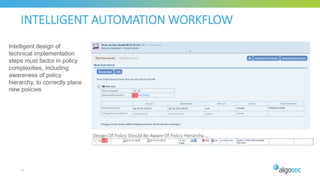
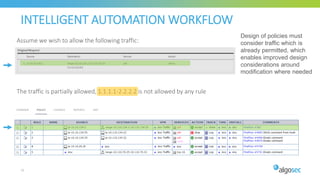
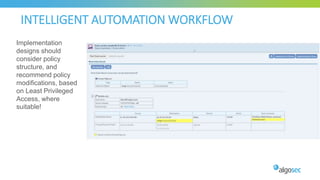
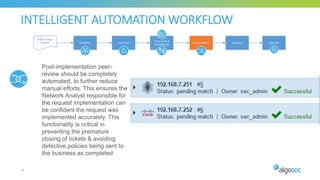
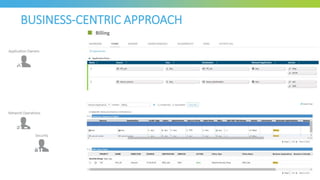
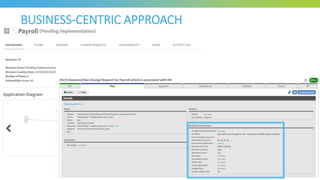
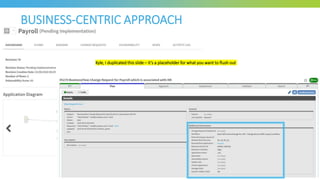
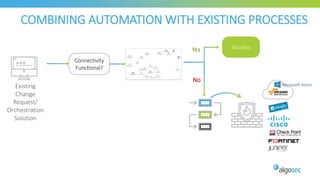
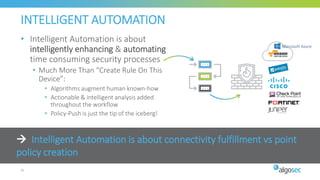
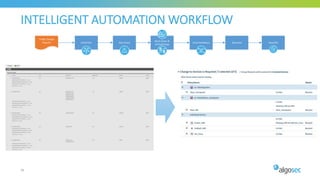
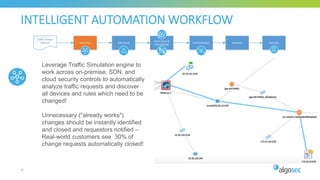
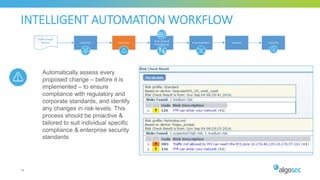
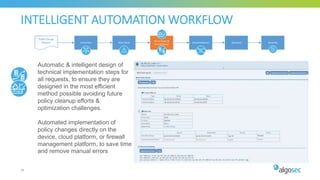
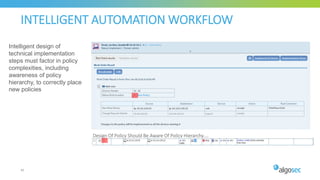
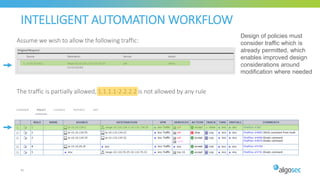
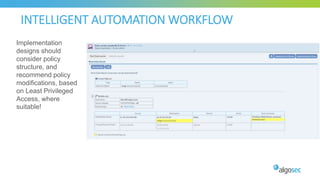
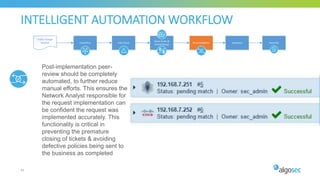
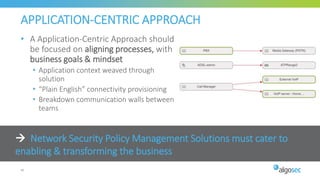
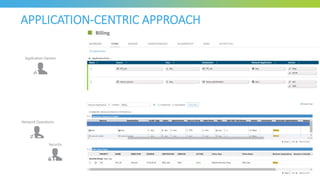
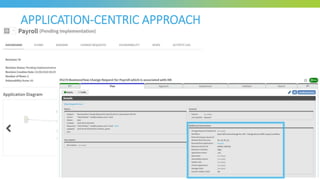
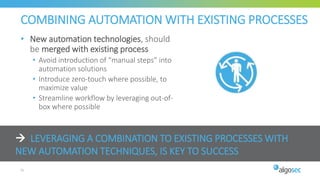
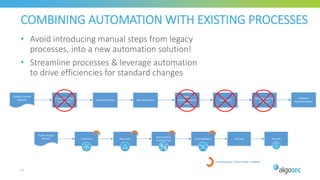
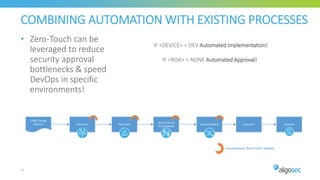
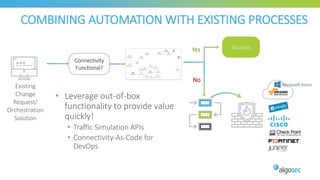
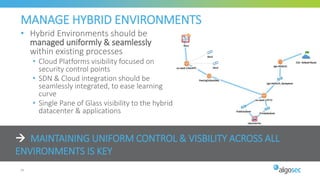
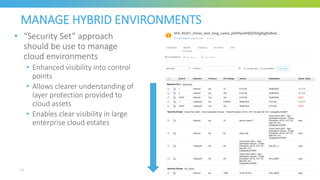
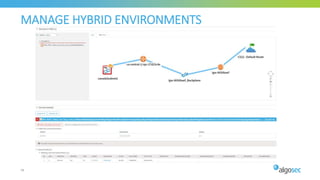
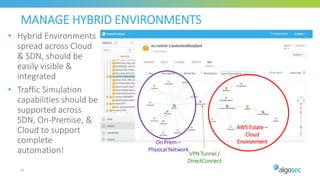
The document discusses key considerations for selecting a network security policy management solution. It emphasizes the importance of intelligent automation throughout the workflow to streamline processes. An application-centric approach is also highlighted to better align security with business needs. When combining new automation technologies with existing processes, organizations should look to optimize workflows by reducing manual steps and introducing zero-touch automation where possible. Effective solutions also provide uniform management and visibility across hybrid environments involving cloud, SDN and on-premises infrastructure.