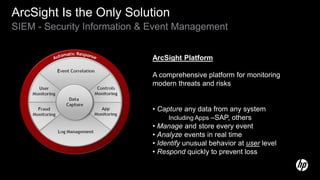
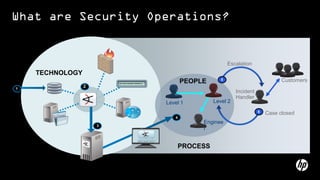
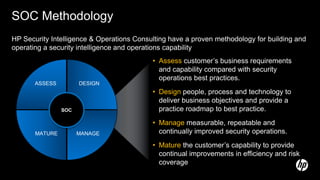
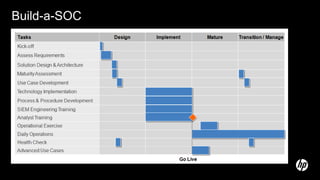
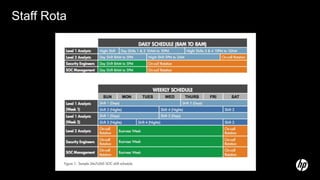
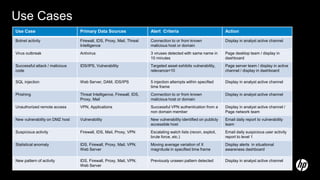
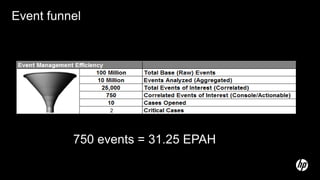
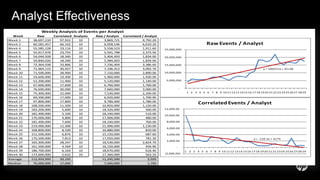
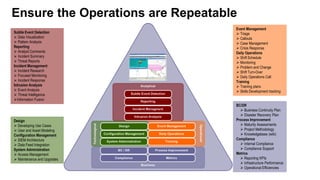
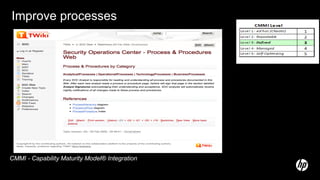
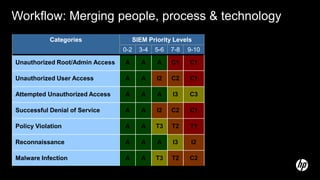
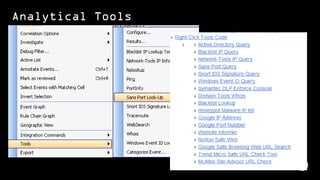
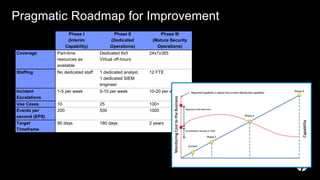
The document discusses building a security operations center (SOC) and provides information on why an organization would build a SOC, how to establish the necessary skills and processes, and technology solutions like HP ArcSight that can be used. It describes how HP consultants have experience building SOCs for major companies and can help customers establish an effective SOC to monitor for security events, ensure compliance, and protect the organization. It provides details on how to structure a SOC, including defining roles and processes, implementing a security information and event management (SIEM) system, and establishing performance metrics to improve over time.