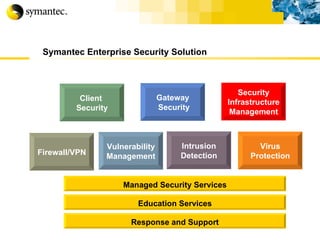
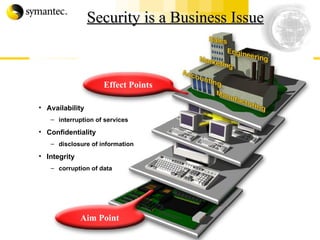
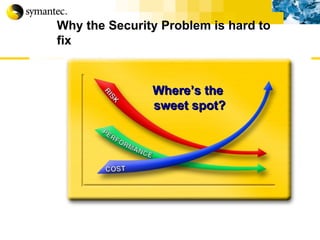
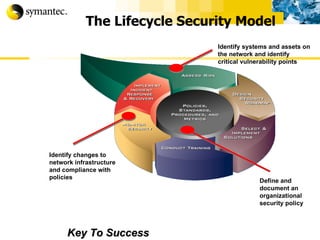
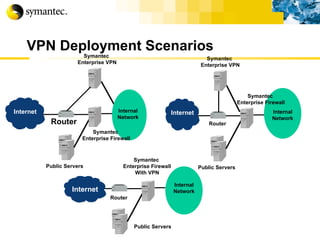
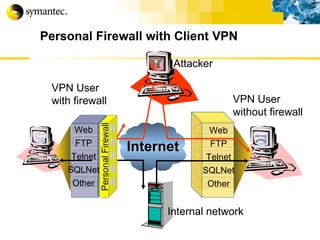
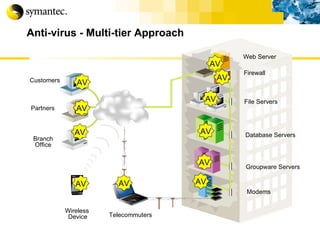
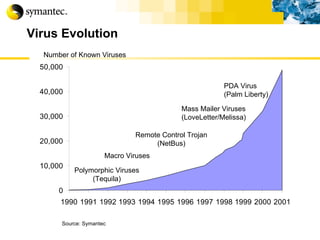
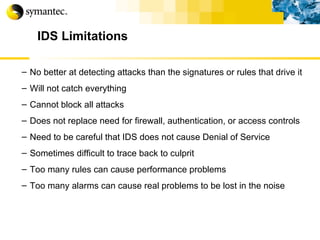
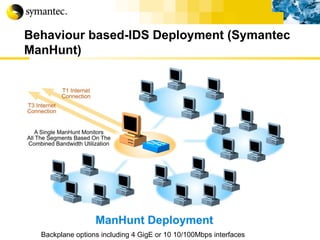
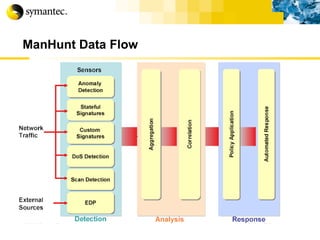
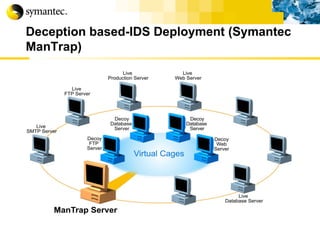
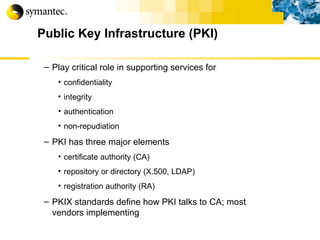
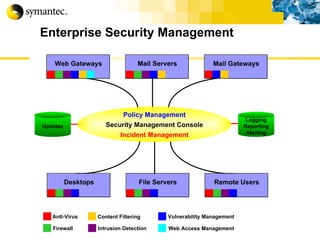
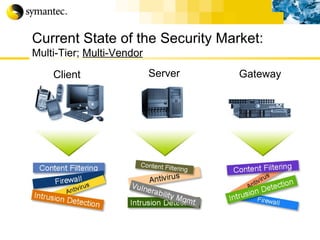
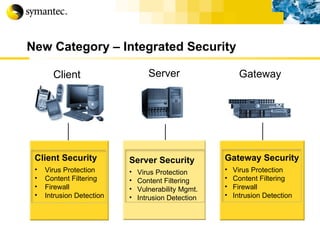
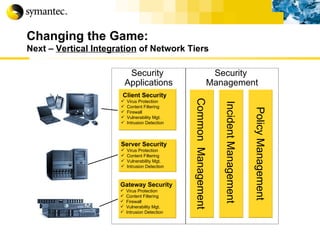
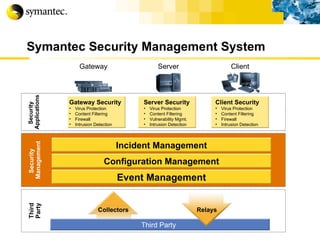
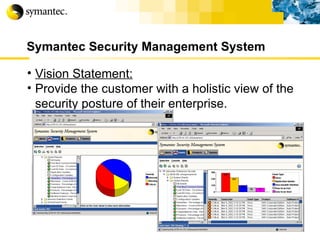
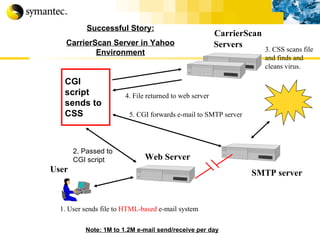
This document summarizes Symantec's enterprise security solutions, including vulnerability management, firewalls, intrusion detection, virus protection, and managed security services. It discusses why security is important for businesses, common security threats, and how Symantec's layered approach addresses these threats through technologies like firewalls, VPNs, antivirus software, and vulnerability scanning.








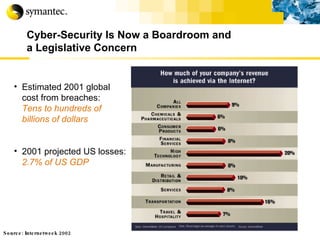
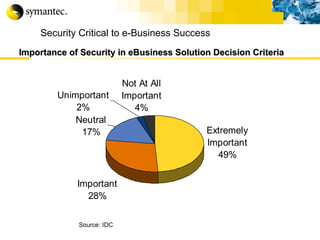
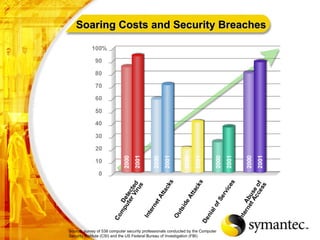

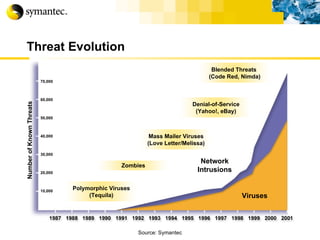
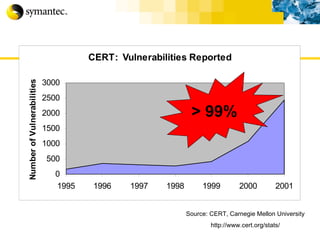
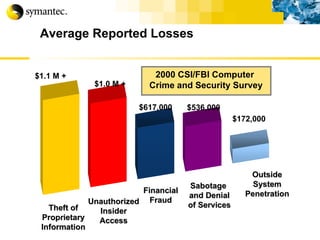


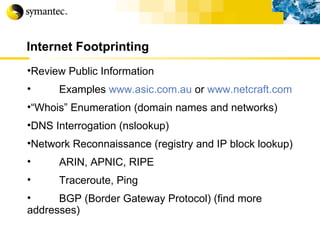





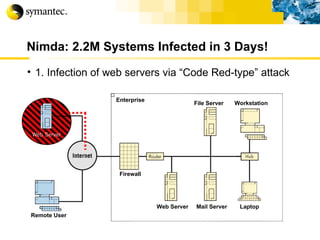
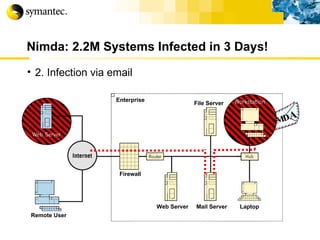
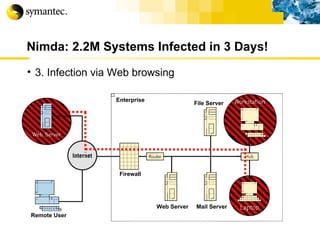
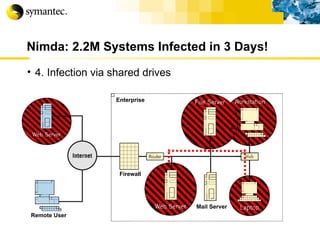
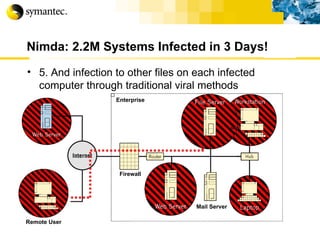
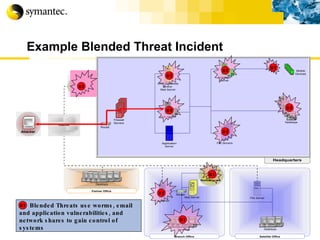

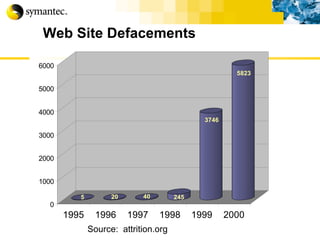
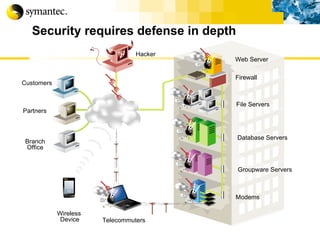


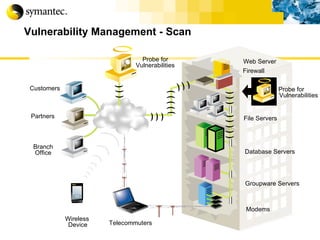


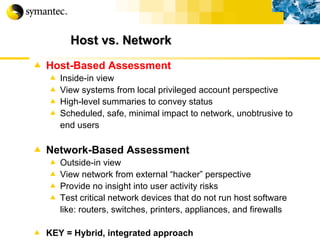
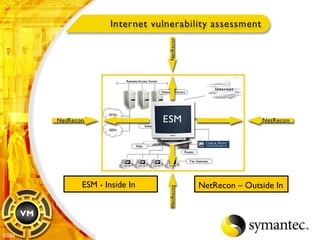

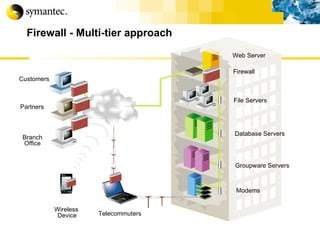

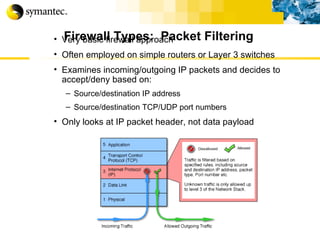
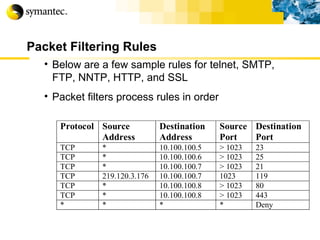

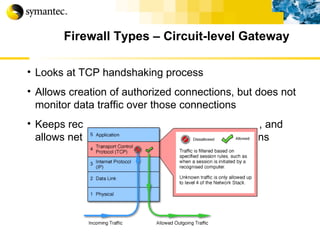
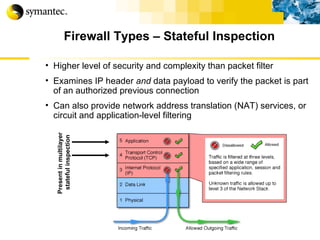

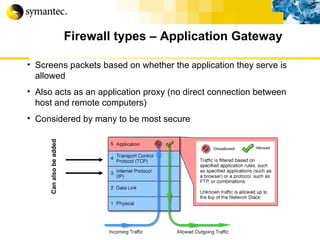
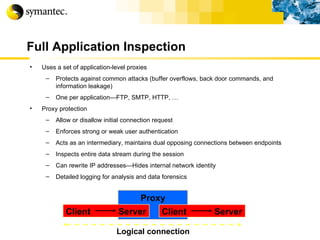

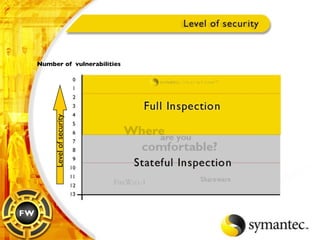

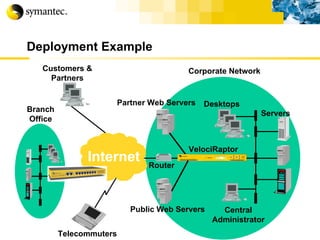
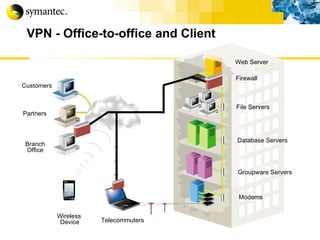
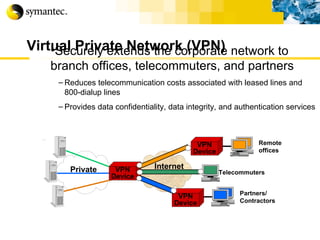




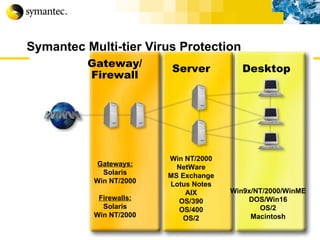
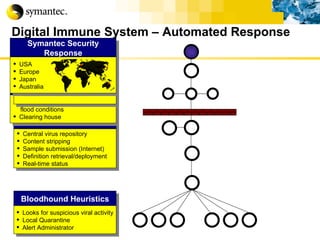












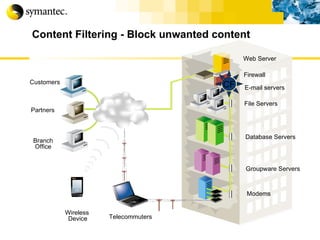
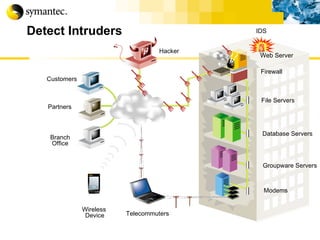


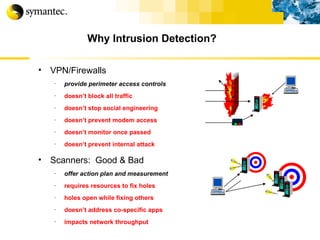
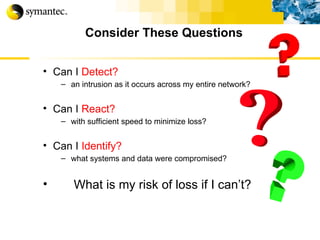


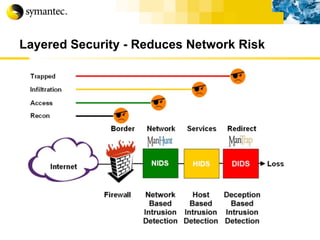
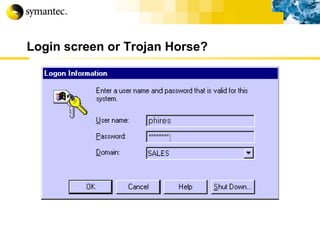


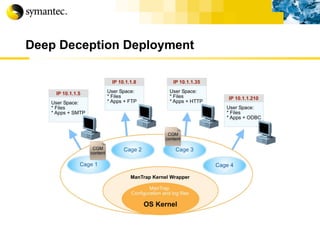
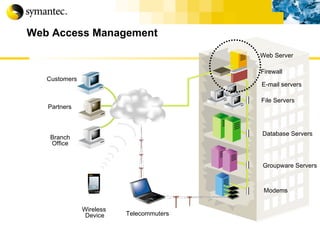
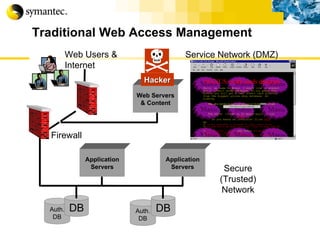
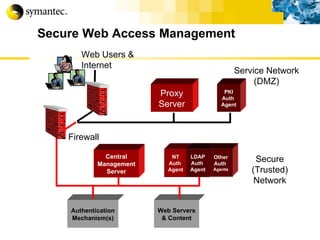





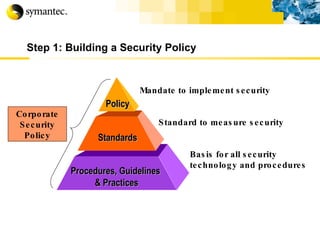
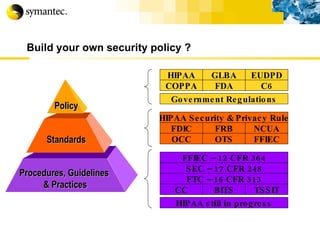
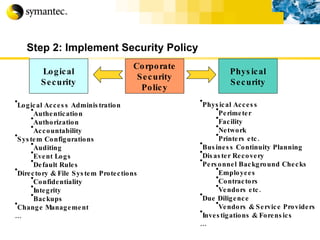
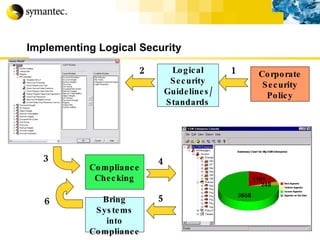
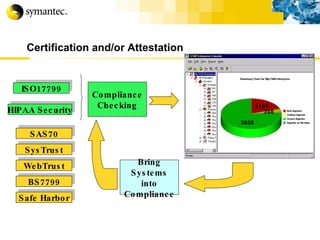

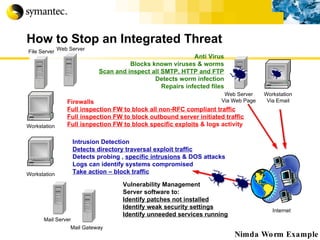
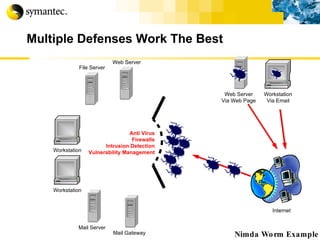
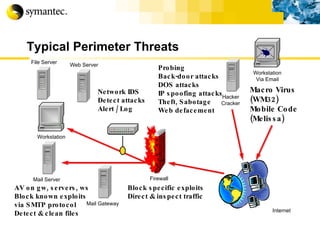





![Thank you Somyos Udomnilobon [email_address] (662)627-9051](https://image.slidesharecdn.com/internet-thailand-total-security-perimeters-1233409563878093-1/85/Event-Internet-Thailand-Total-Security-Perimeters-154-320.jpg)
