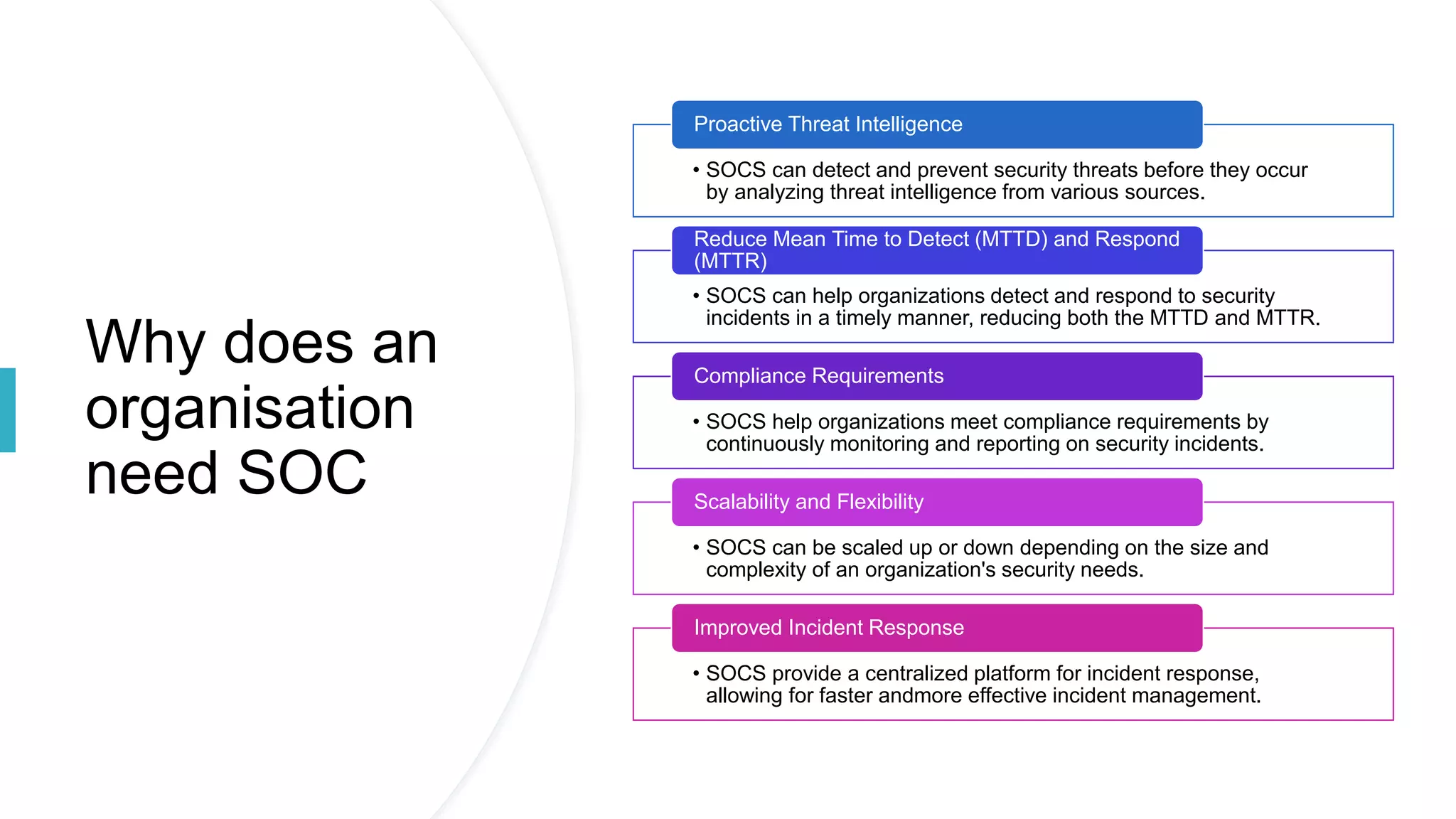
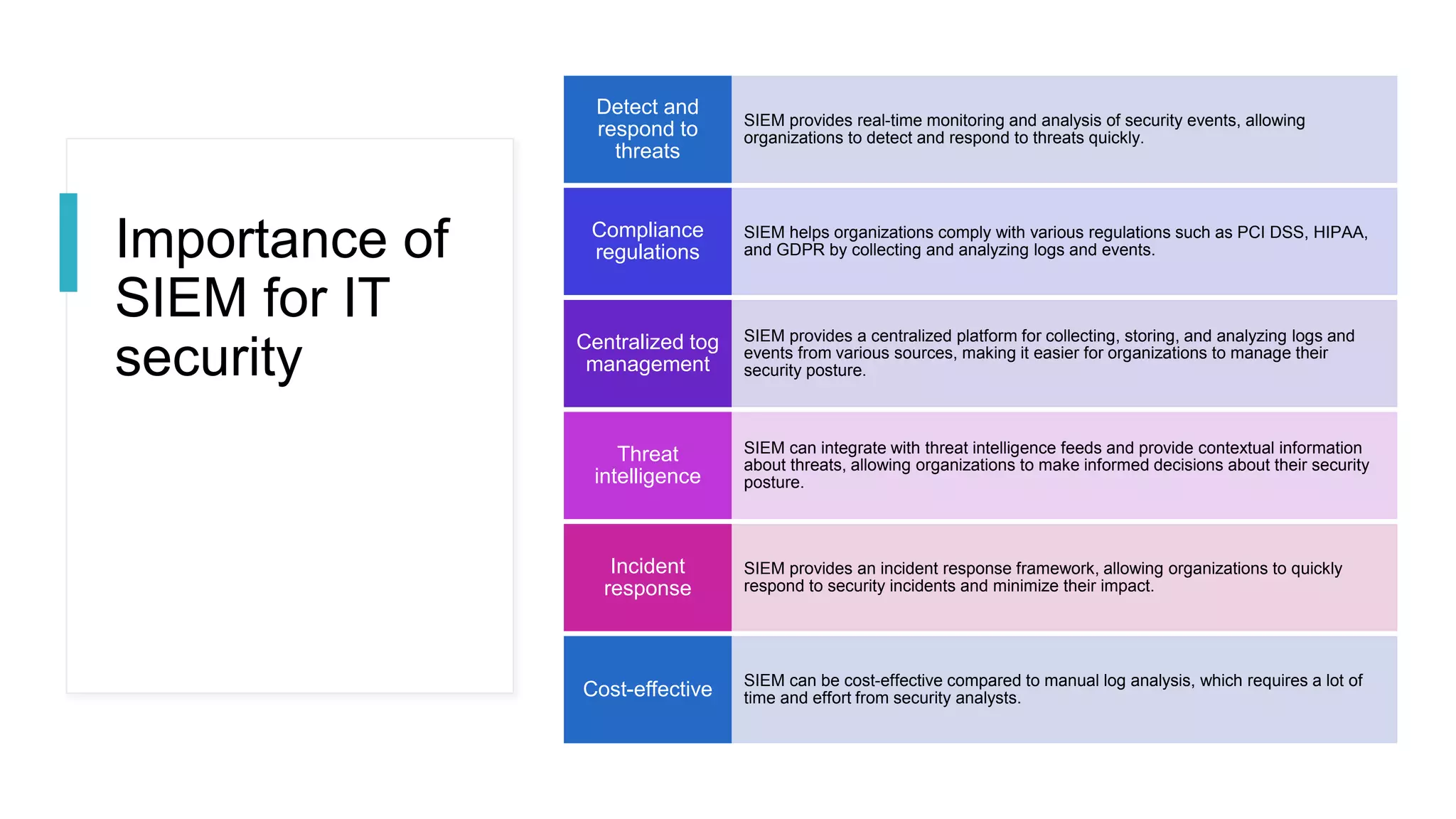
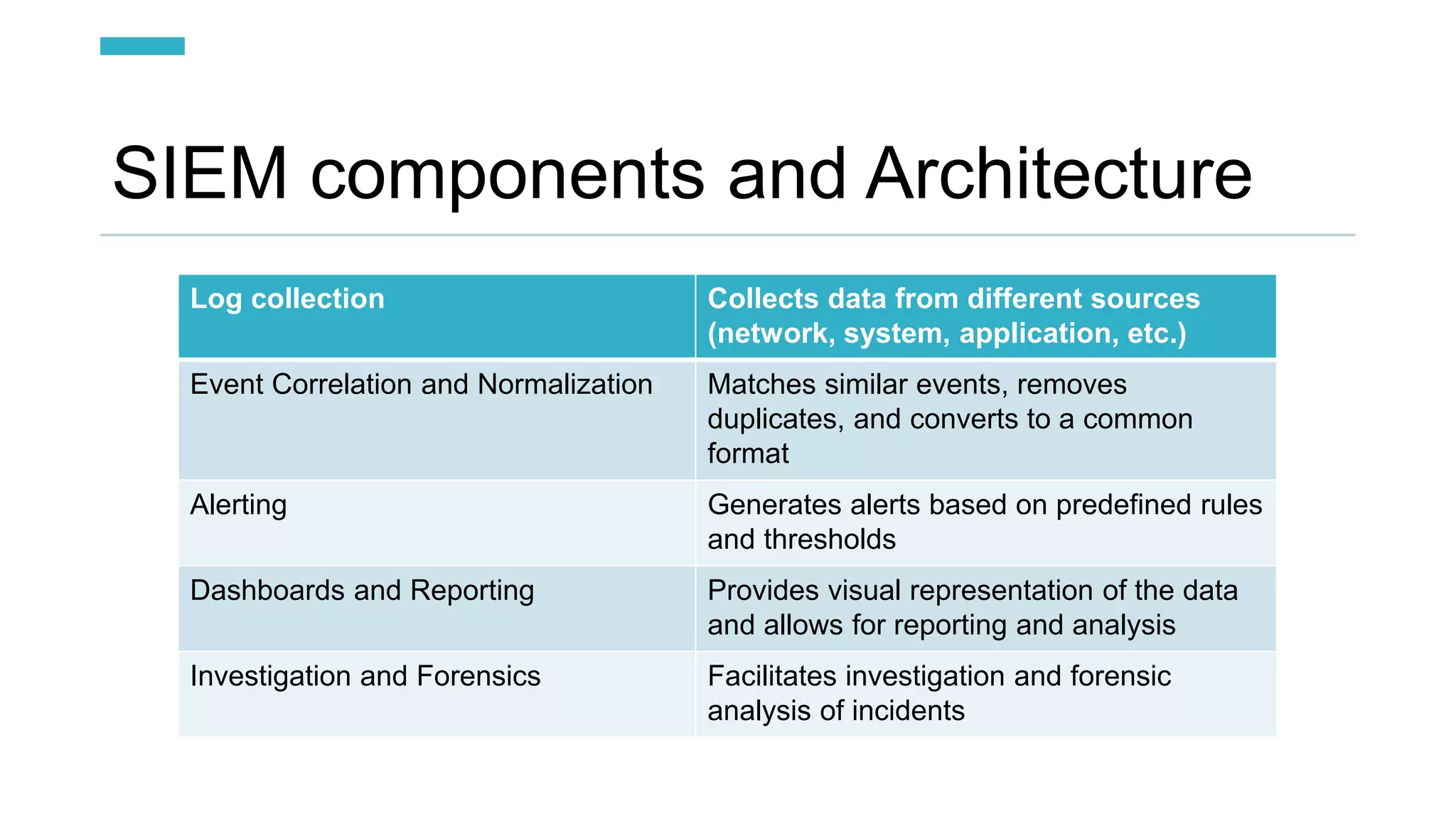
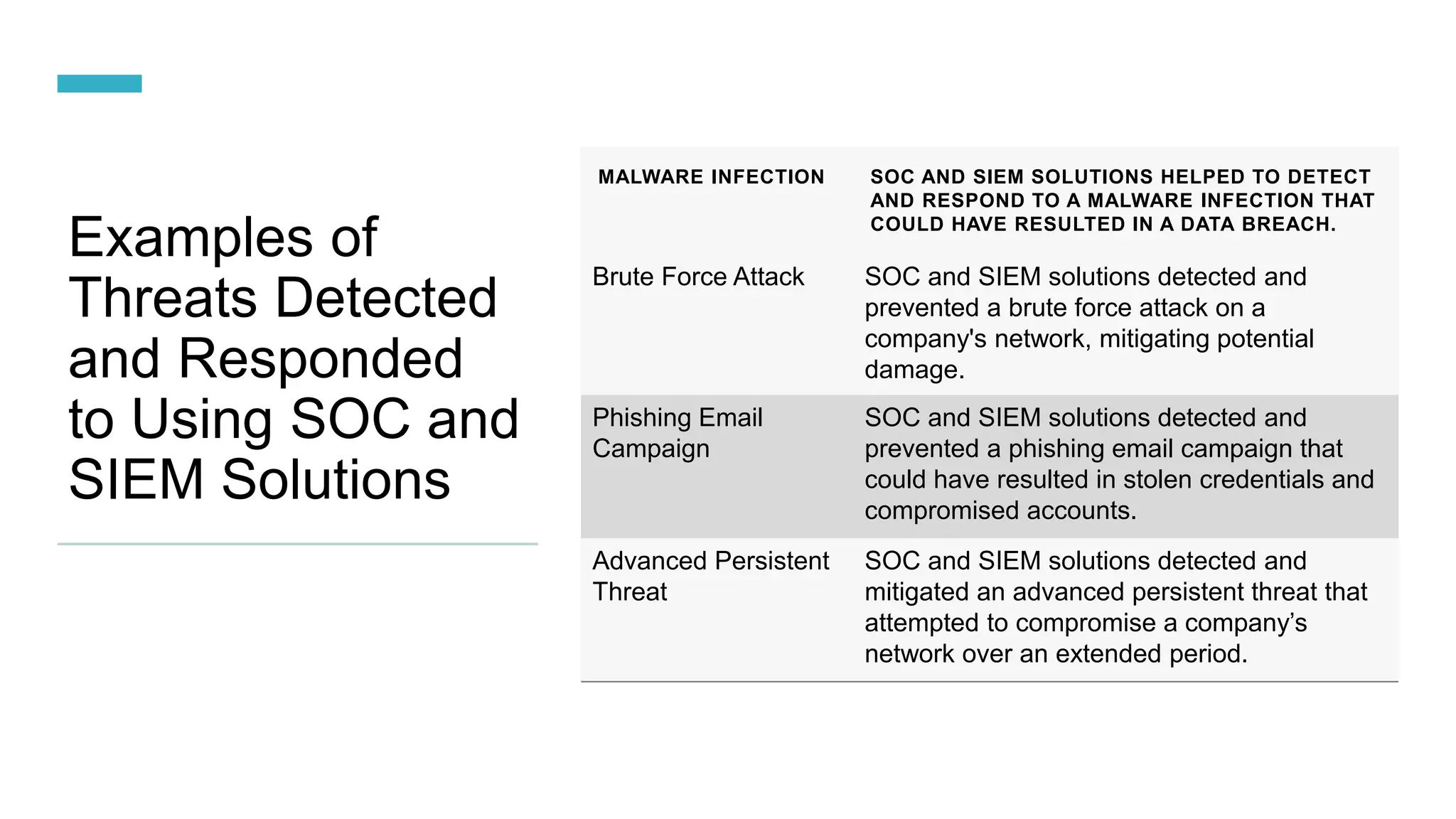
SOC and SIEM systems can help organizations detect and respond to security incidents and threats in a timely manner. A SOC acts as a security operations center to monitor, analyze, and respond to cybersecurity incidents. SIEM provides real-time analysis of security alerts and events to help identify potential threats. Implementing SOC and SIEM solutions can improve an organization's security posture through early threat detection, compliance with regulations, and reduced breach impact.