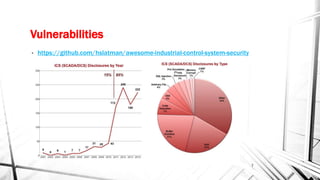
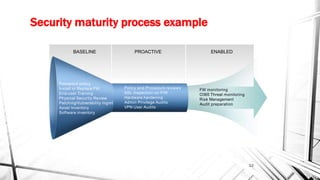
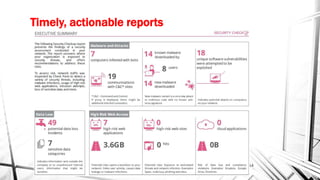
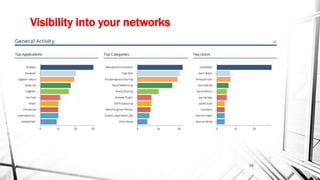
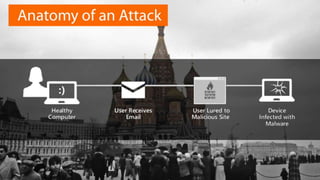
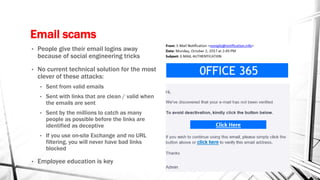
The document discusses the evolving landscape of cyber security, particularly for industrial control systems, highlighting a shift from individual crime to large-scale cyber attacks with minimal repercussions. It emphasizes the importance of continuous risk-based planning, user education, and tailored security solutions rather than a one-size-fits-all approach. The key takeaway is the necessity for organizations to prioritize security maturity and comprehensive incident response strategies to mitigate the diverse and changing threats in cyber security.