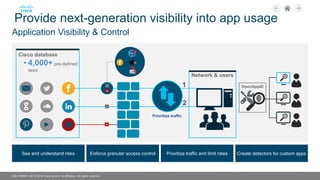
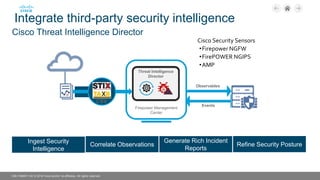
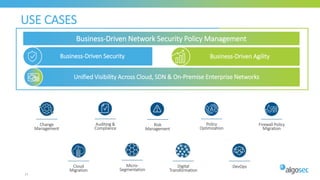
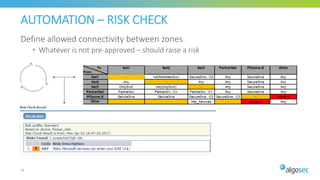
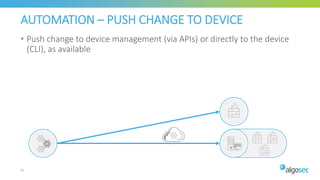
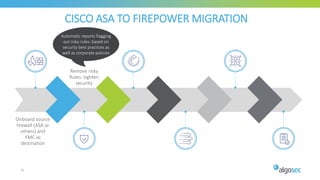
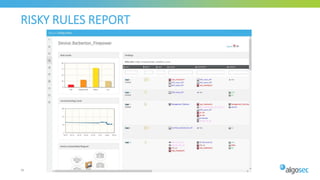
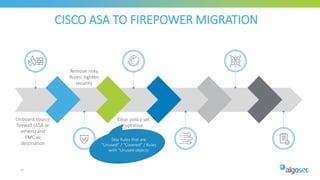
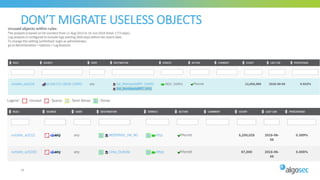
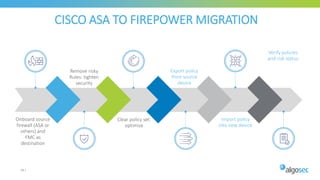
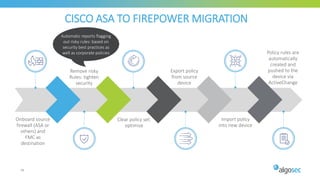
The document discusses Cisco's next-generation firewall (NGFW) and its integration with AlgoSec's security policy automation. It outlines Cisco's integrated security portfolio including the Firepower NGFW. It then discusses how AlgoSec provides automation for balancing security and business agility through responsible automation of risk analysis, compliance, policy optimization, and change management. Key capabilities covered include automating the migration of policies from Cisco ASA to Firepower NGFWs.