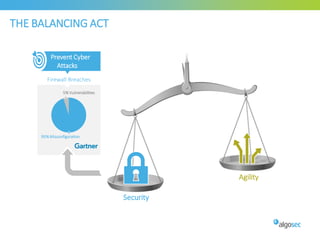
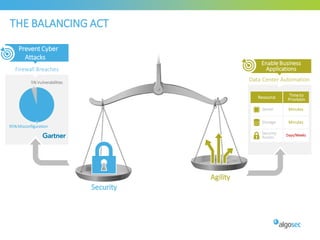
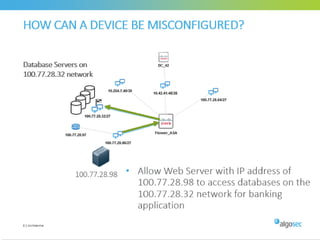
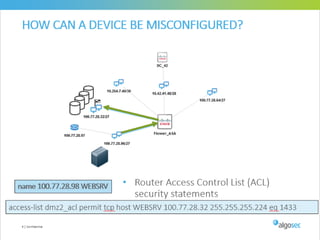
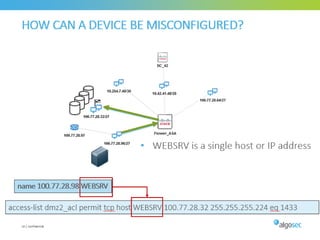
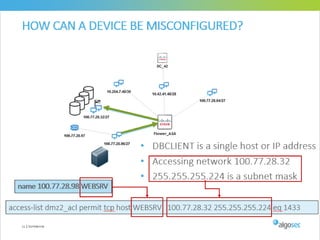
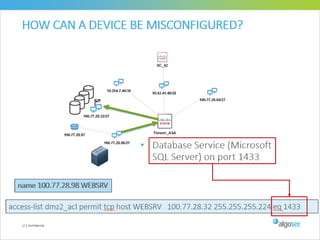
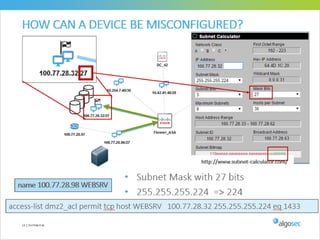
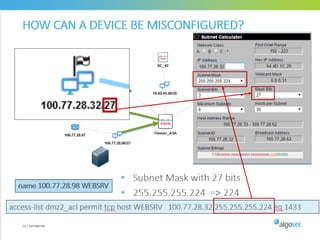
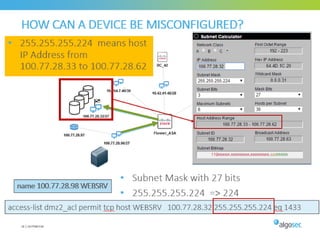
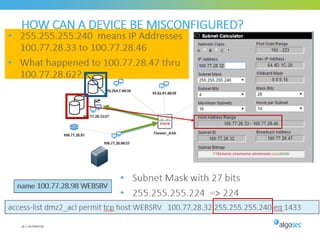
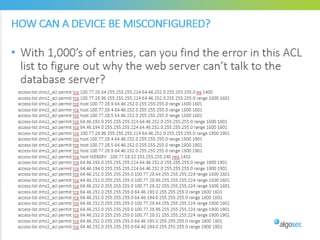
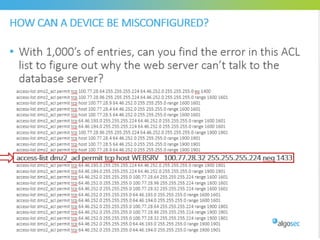
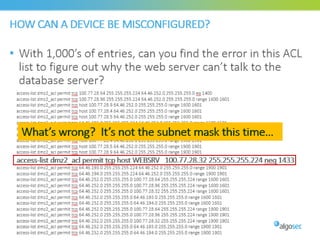
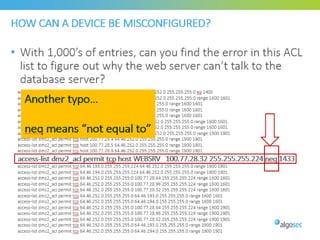
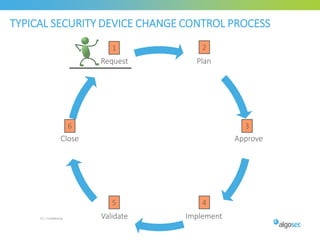
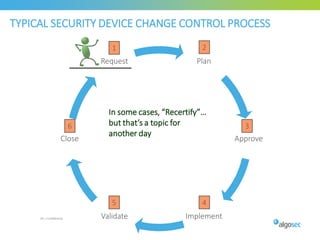
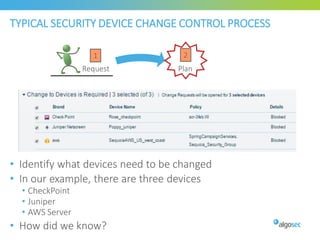
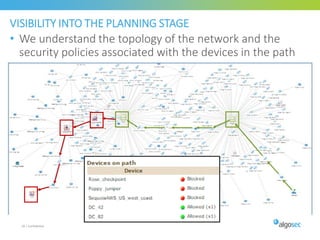
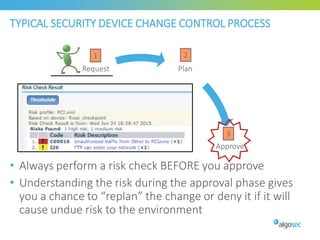
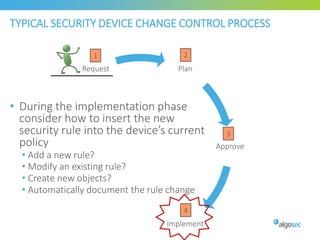
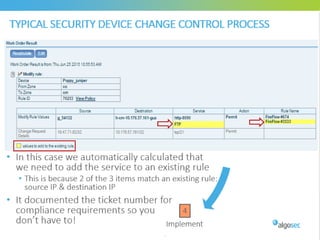
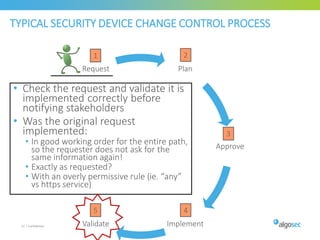
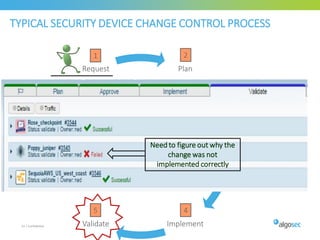
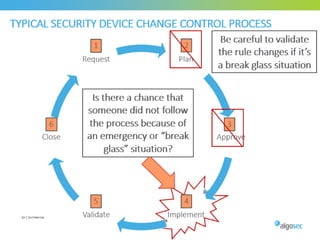
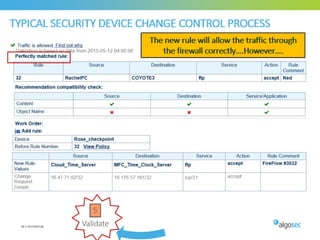
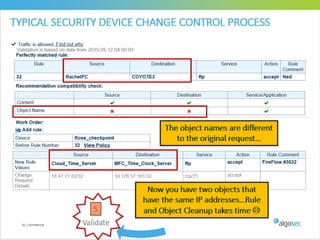
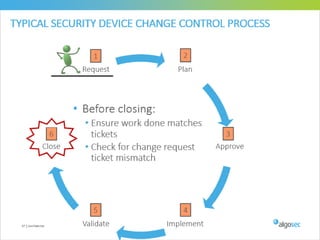
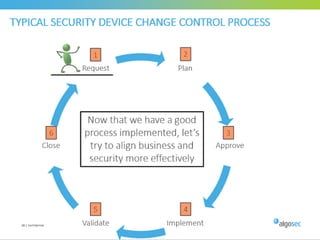
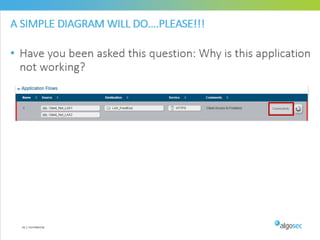
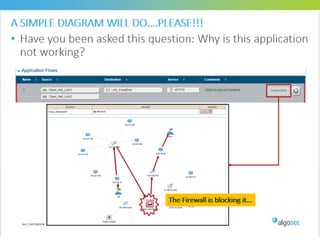
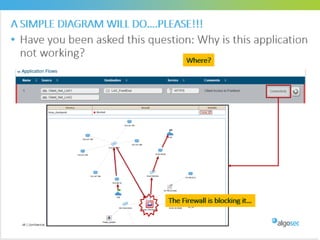
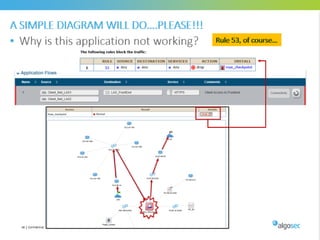
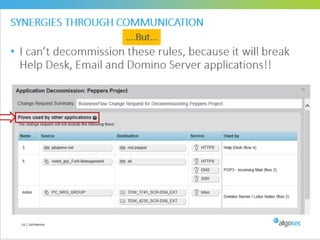
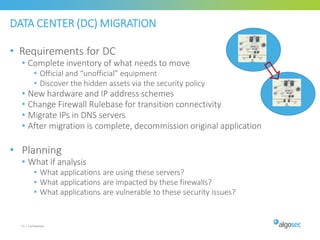
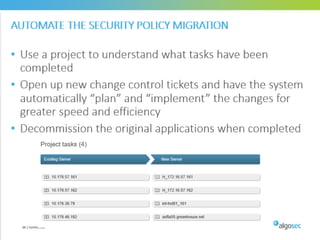
Misconfigured network devices can lead to outages and security breaches, emphasizing the need for effective change control processes and better communication between IT and business sectors. Automation and validation are recommended to reduce human errors, while the security change management process must improve to meet rapid business demands. The document outlines strategies for addressing these issues, particularly during data center migrations.