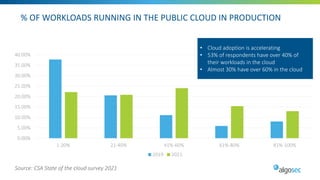
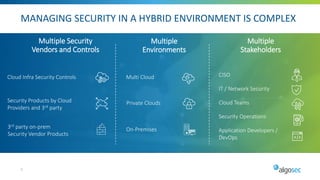
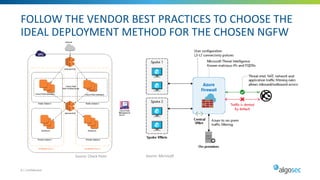
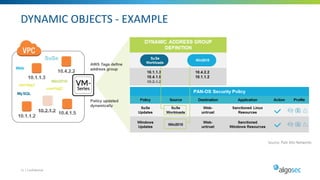
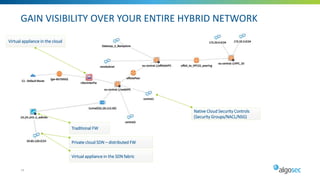
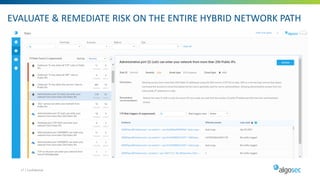
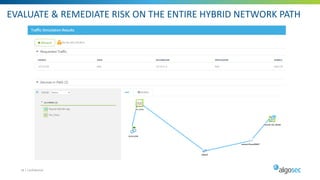
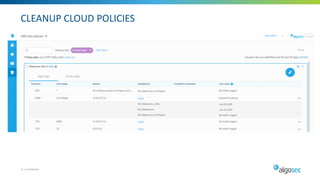
Managing security in hybrid cloud environments is complex due to multiple security vendors, controls, stakeholders, and environments spanning on-premises, private clouds, and public clouds. The document outlines six best practices for tighter hybrid cloud security: 1) use next-generation firewalls in the cloud, 2) use dynamic objects to configure firewalls, 3) gain visibility over the entire hybrid network, 4) evaluate and remediate risk across the hybrid network path, 5) cleanup cloud security policies, and 6) maintain infrastructure-as-code security as part of the cloud change pipeline. Adopting these practices can help organizations securely manage networks spanning multiple cloud and on-premises components.