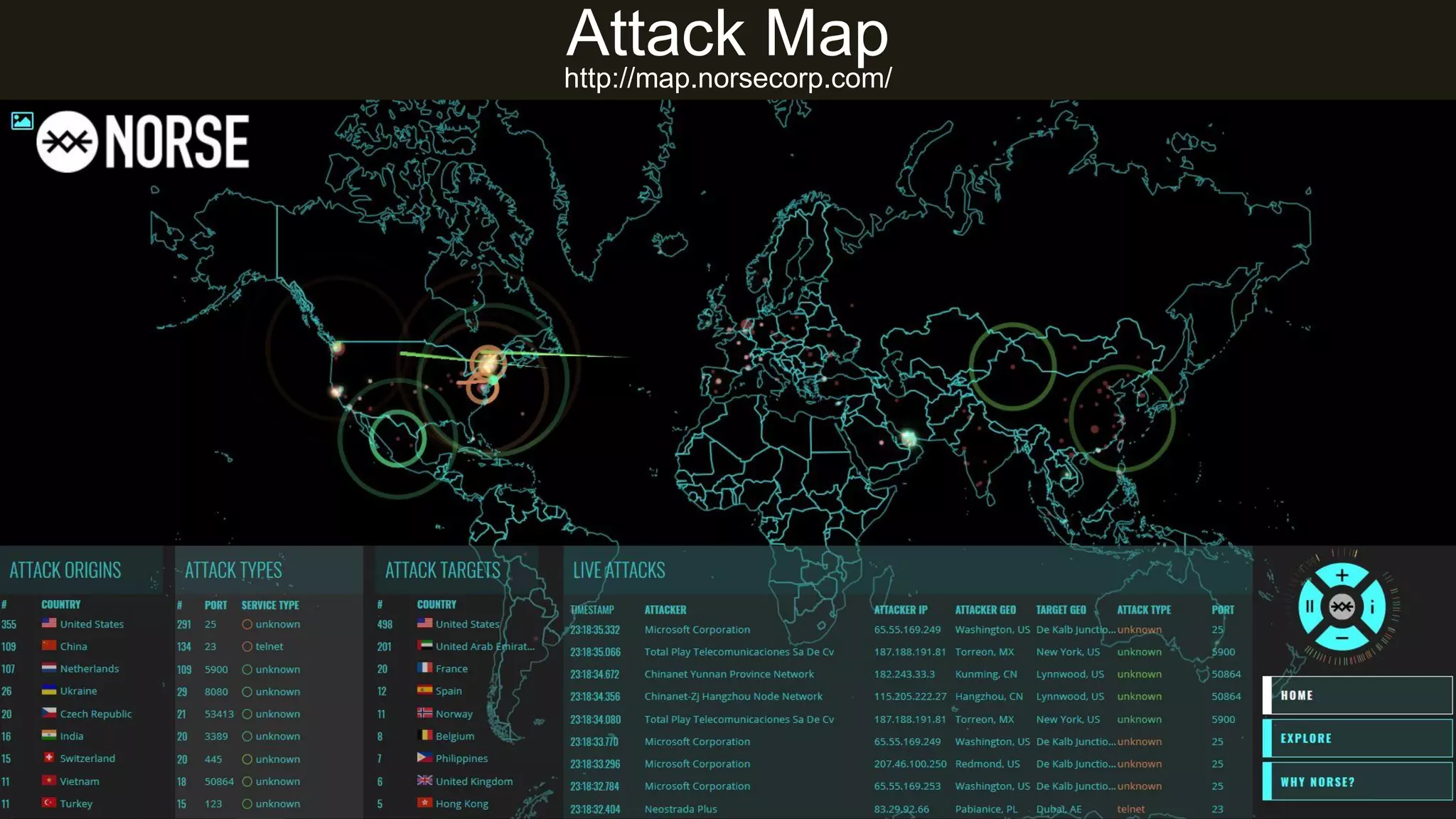
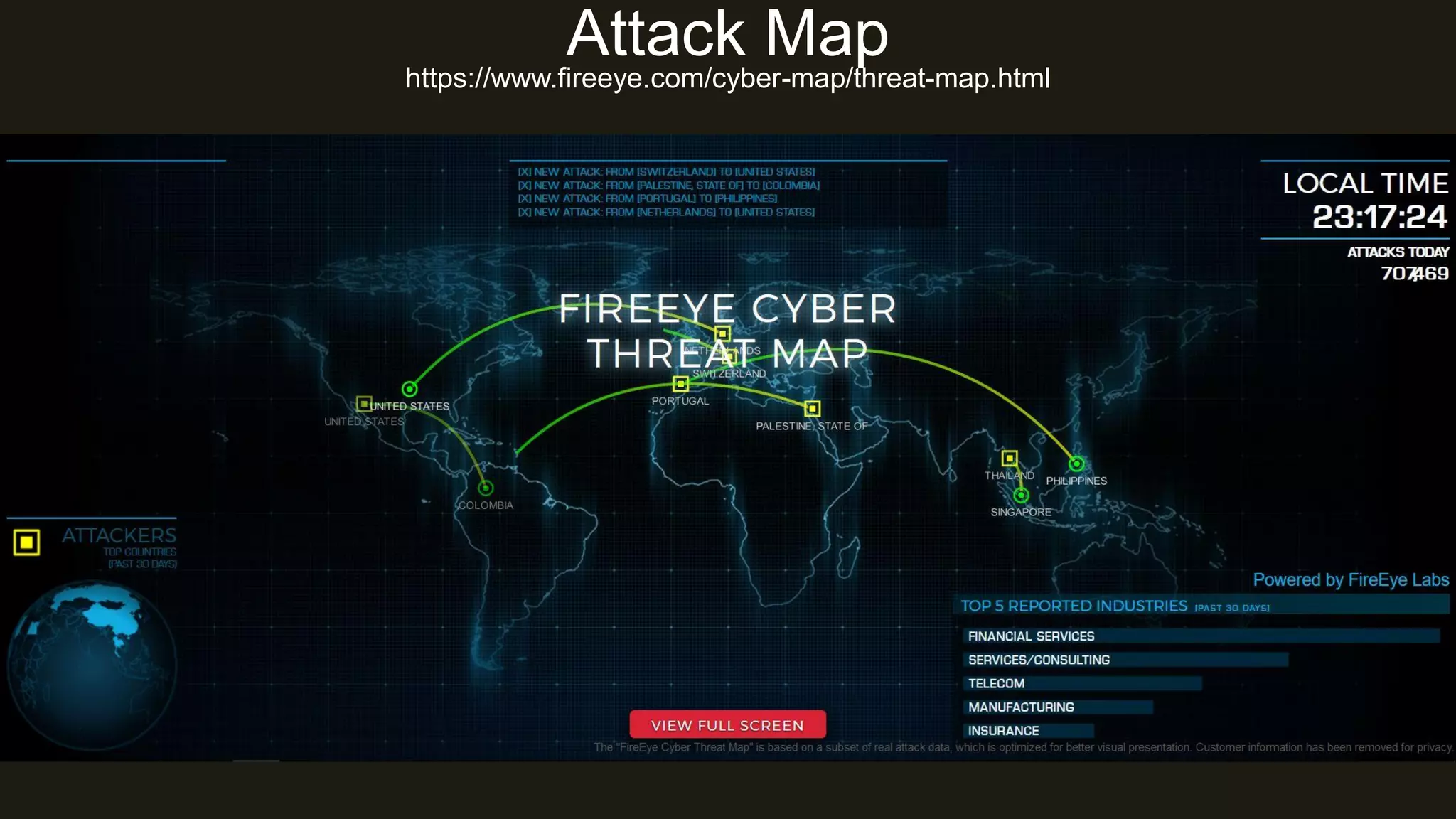
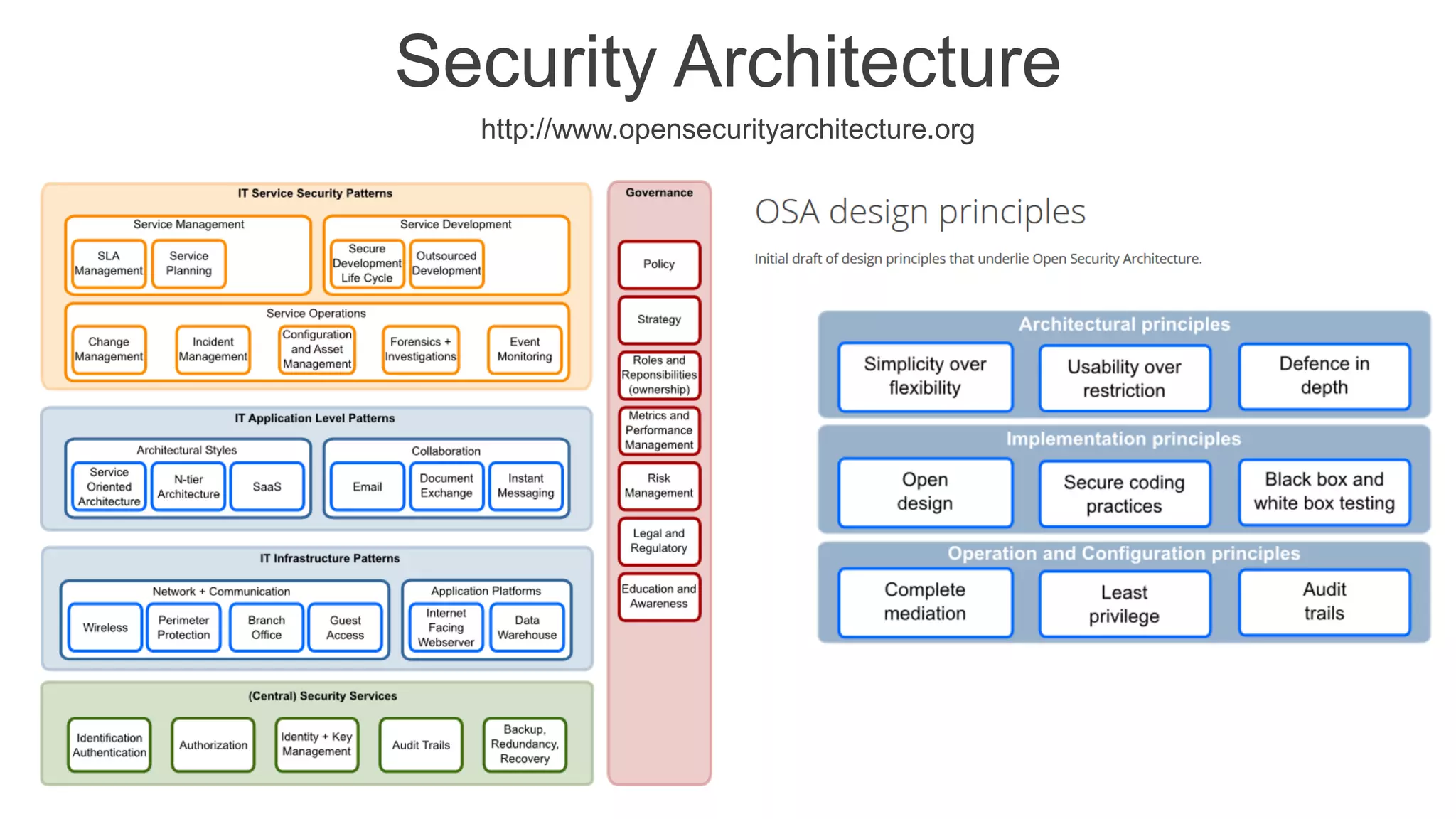
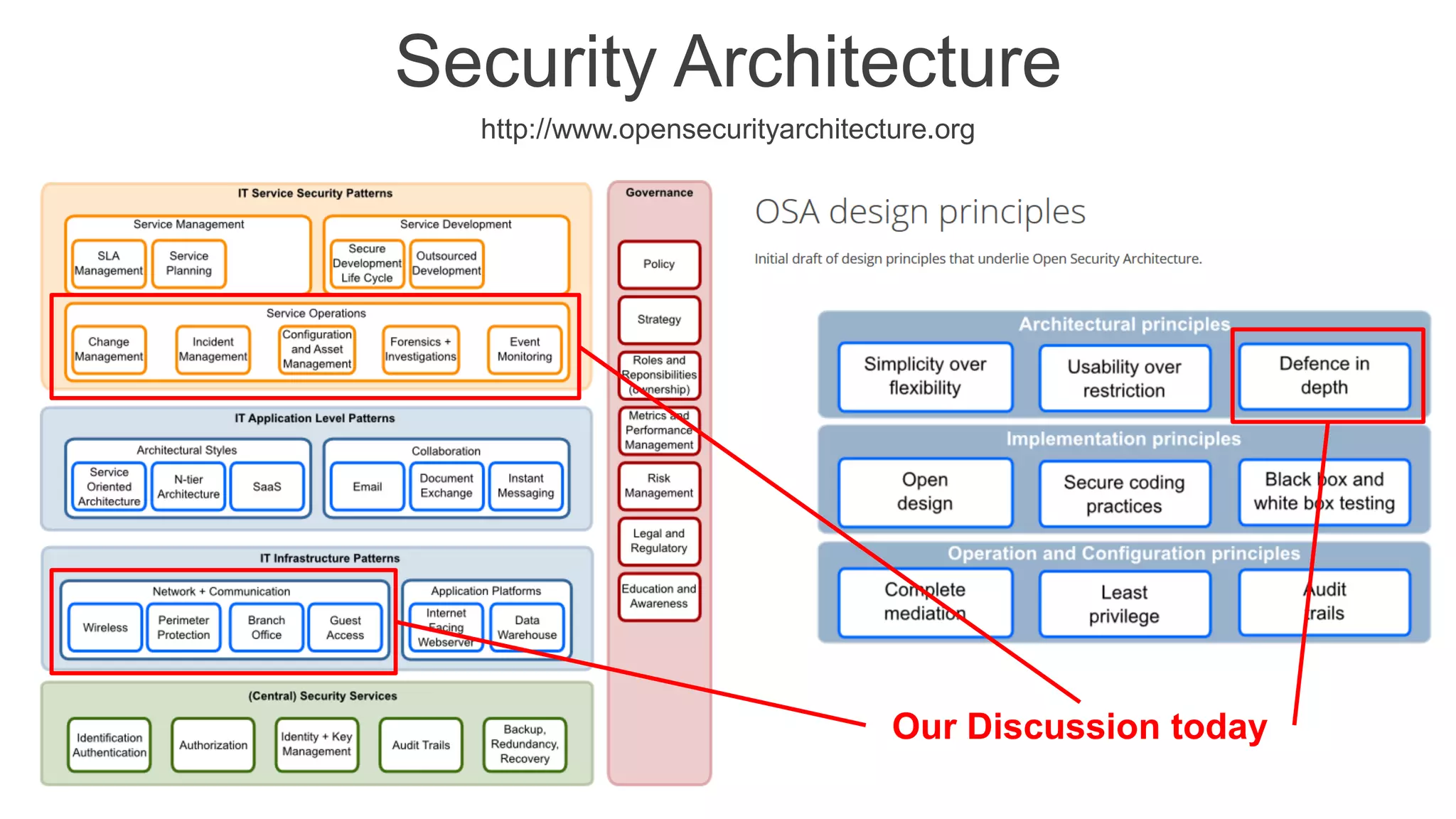
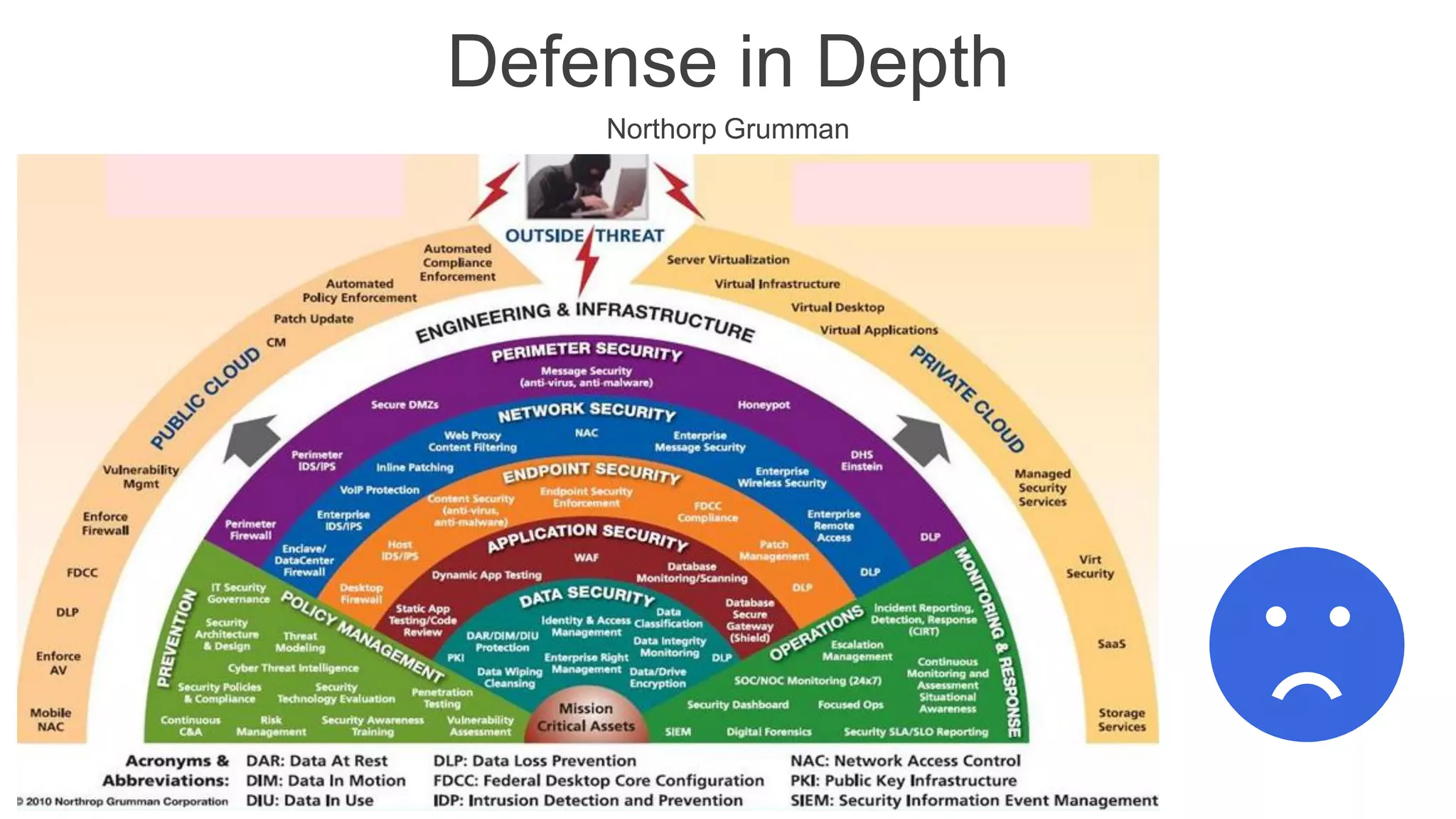
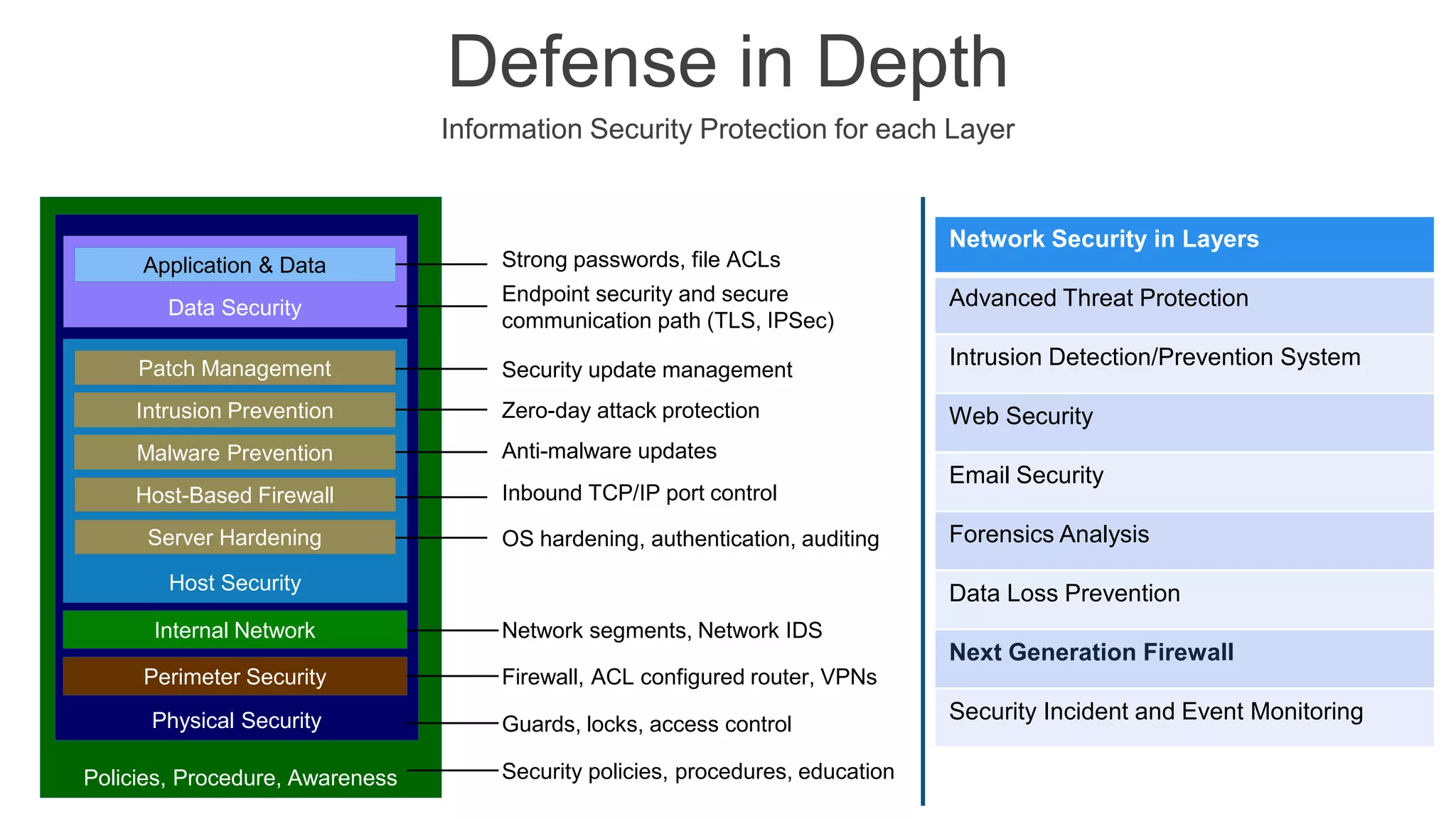
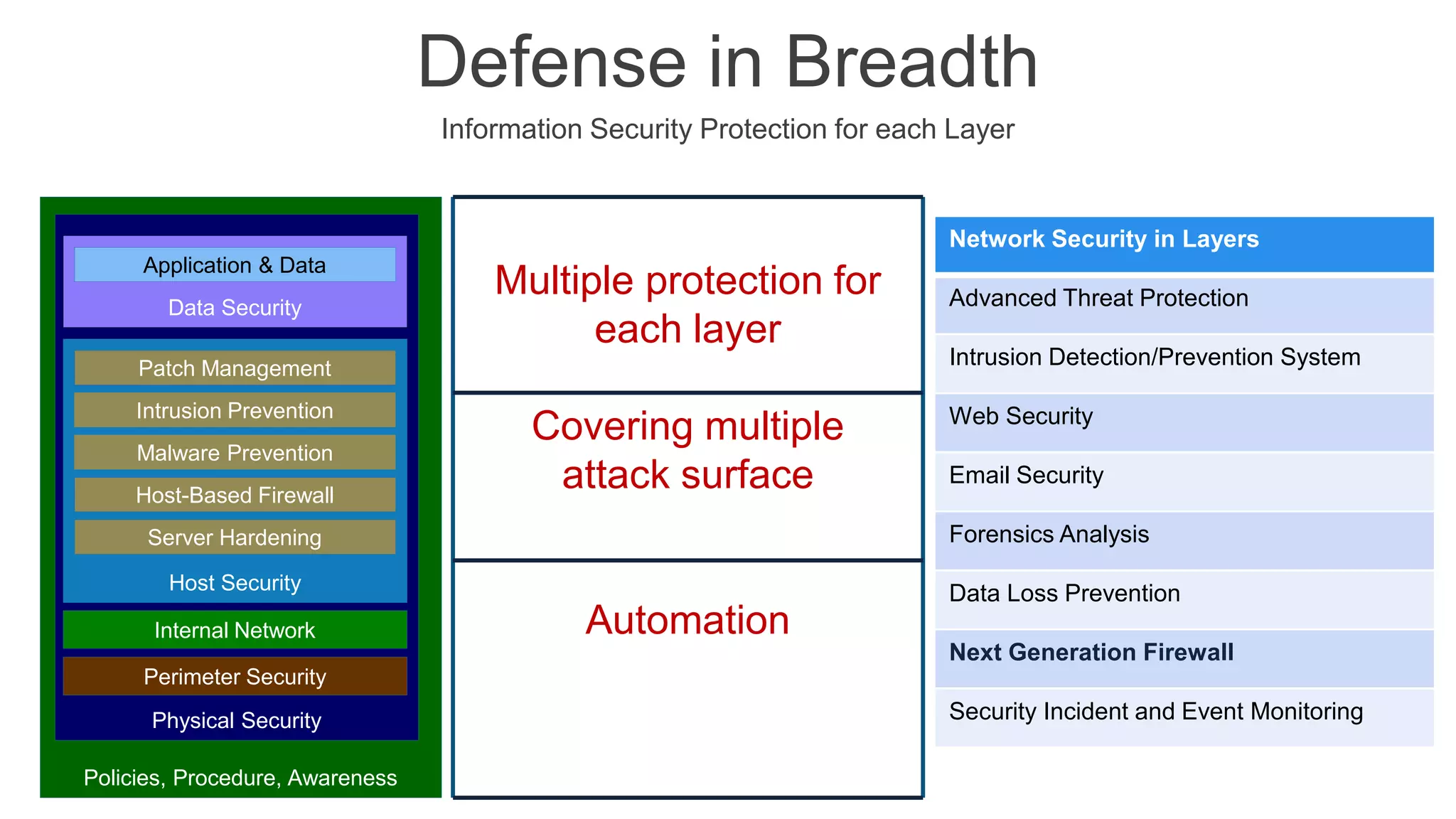
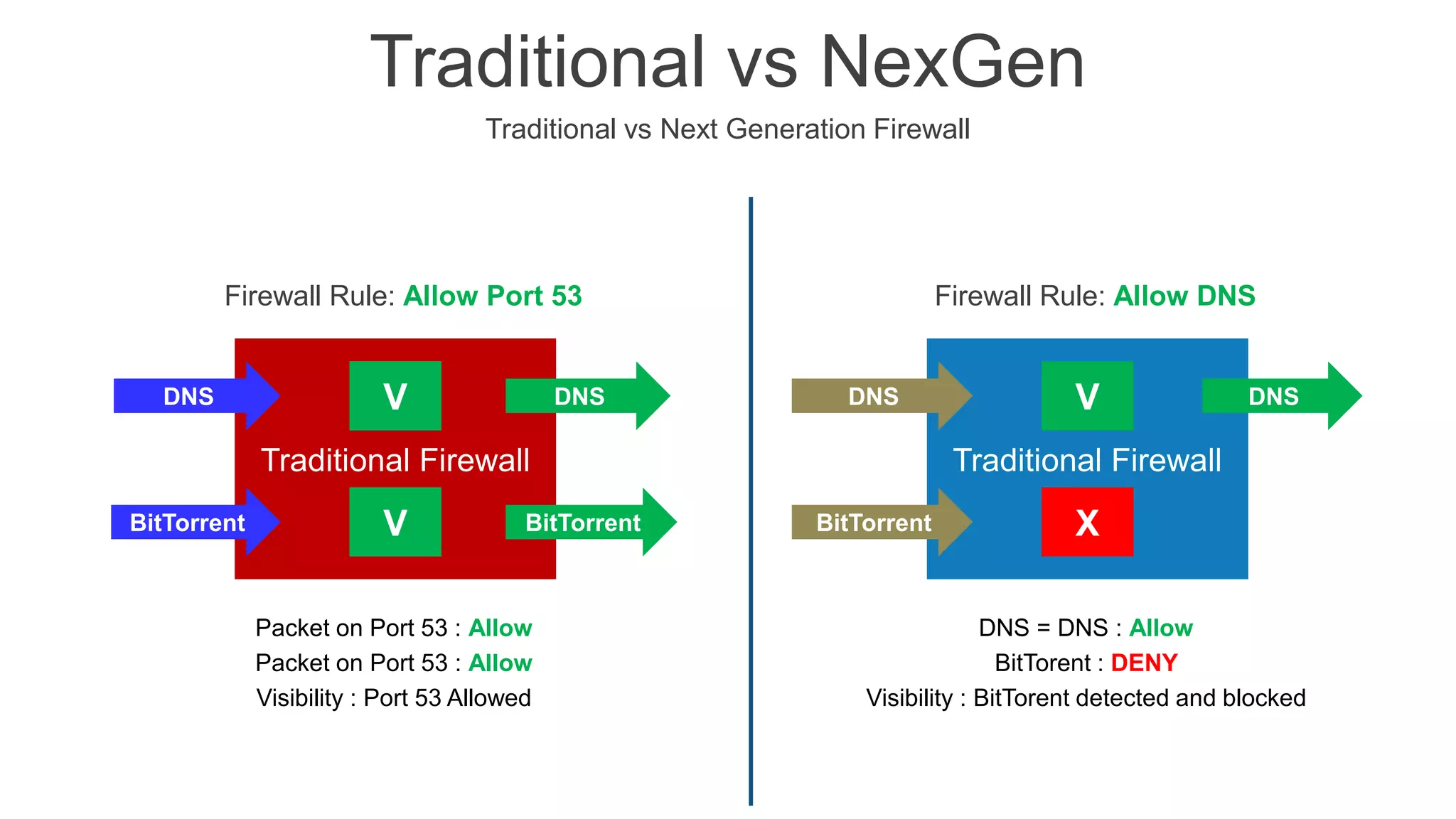
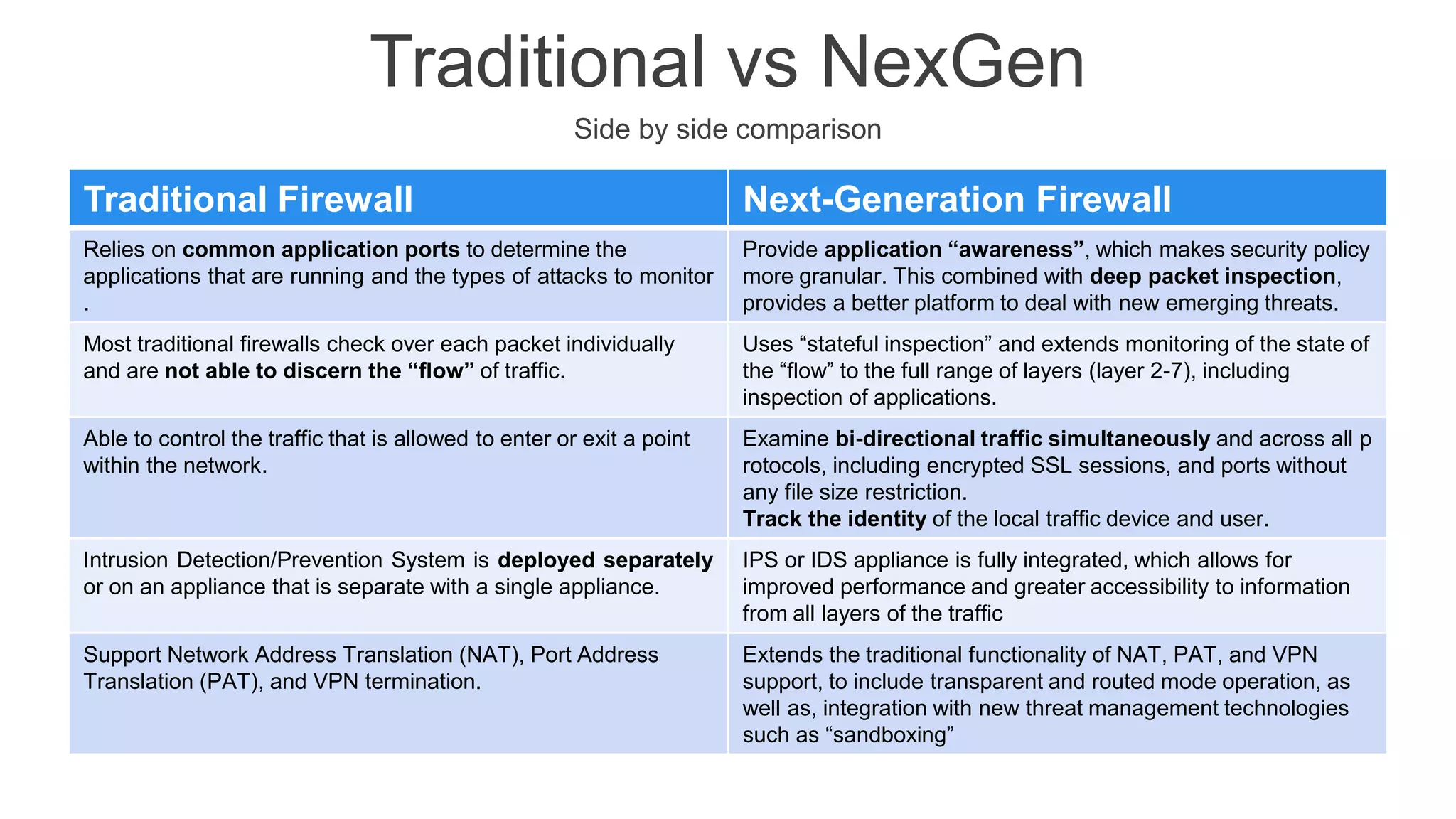
The document presents insights into network security and defense mechanisms, focusing on layered information security and new technologies like next-generation firewalls. It outlines various significant cyber attacks and their impacts, such as WannaCry and the Macon campaign hack, while detailing multi-layered security strategies and the evolving nature of network security threats. The speaker, Eryk Budi Pratama, emphasizes the importance of comprehensive defense strategies that incorporate application awareness and advanced threat protection.