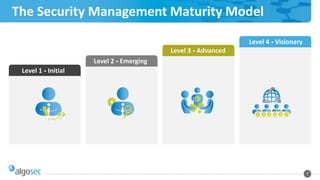
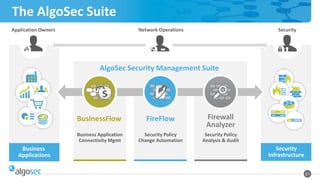
This document discusses a security policy management maturity model with four levels - initial, emerging, advanced, and visionary. It provides recommendations for organizations at each level to improve their security policy management processes and tools. Level 1 focuses on basic documentation and risk analysis. Level 2 introduces some automation but change management is still manual. Level 3 has more automated processes but documentation and communication could be improved. The ideal level 4 provides fast, efficient security for applications through alignment of security, operations, and application teams. The document promotes the AlgoSec Security Management Suite as a tool to help organizations progress through the maturity levels.