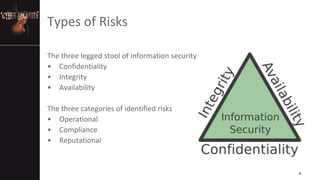
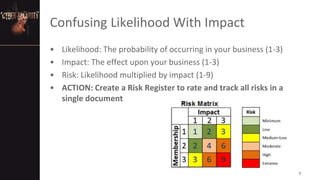
The document outlines key challenges in information security, emphasizing the importance of asset management, risk assessment, and the need for comprehensive policies. It discusses common vulnerabilities, the role of human error, and the necessity for ongoing training and awareness. Additionally, it highlights overlooked threats such as disgruntled employees and outdated software, urging organizations to adopt proactive measures to enhance their cybersecurity posture.