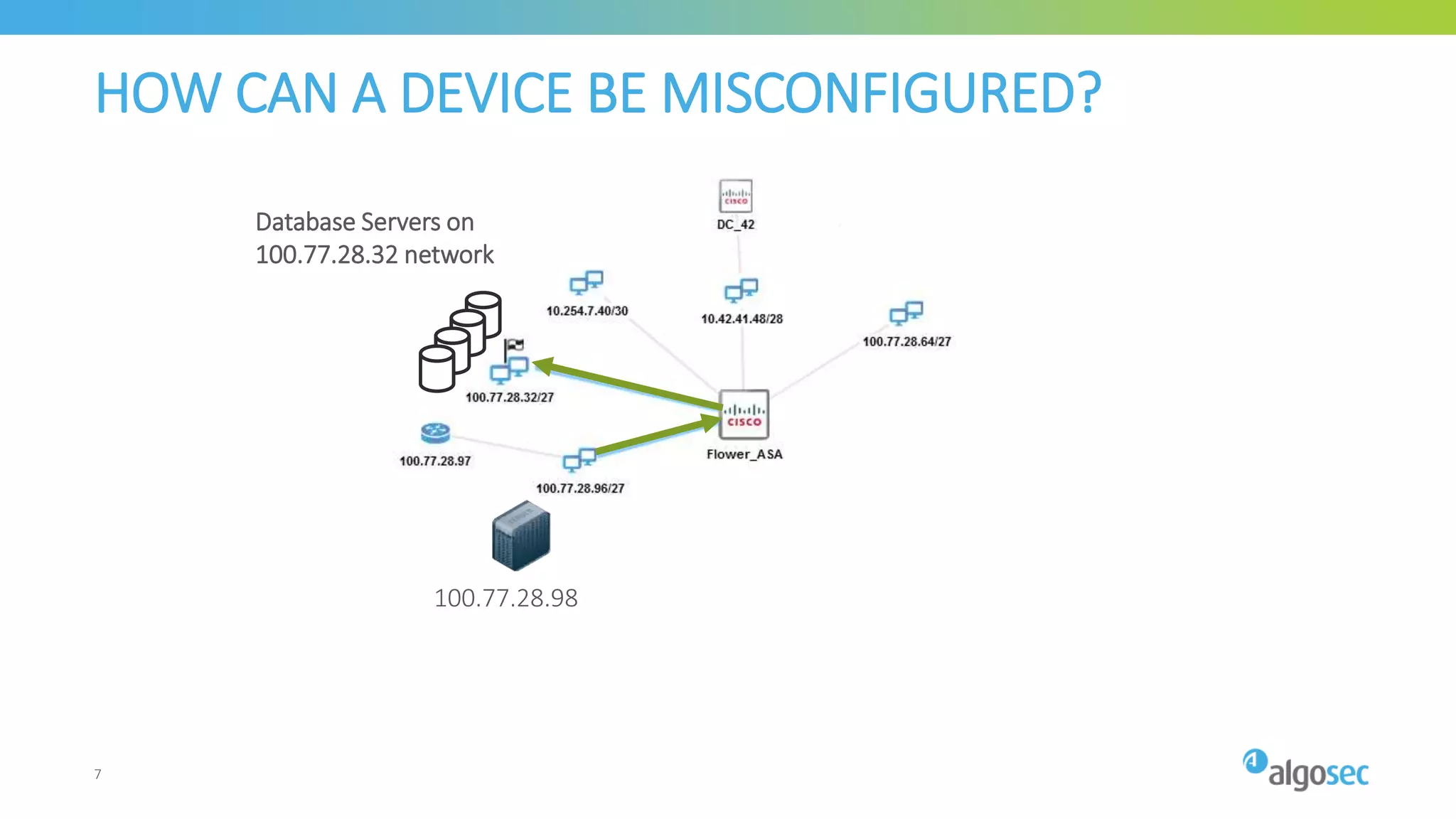
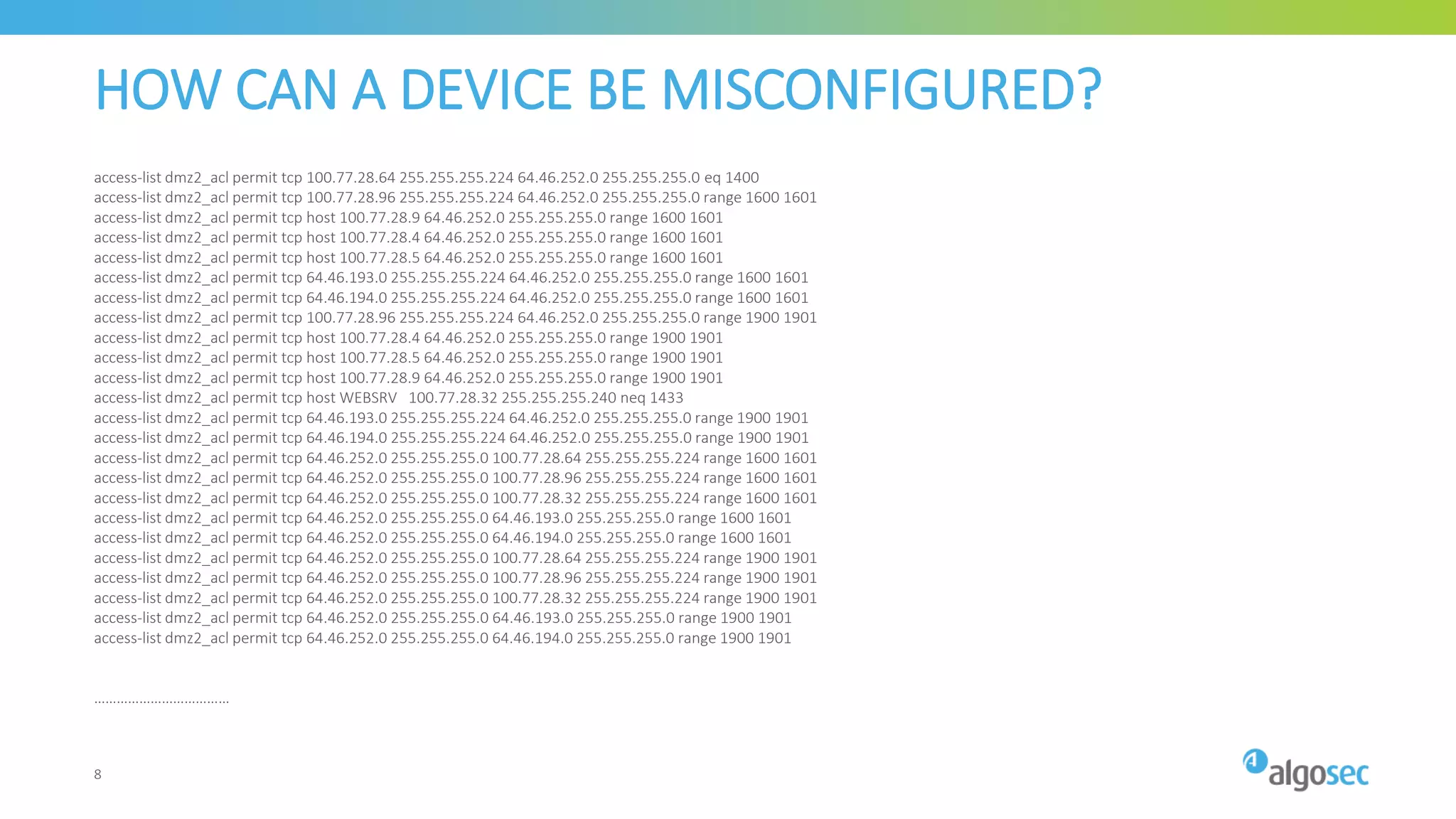
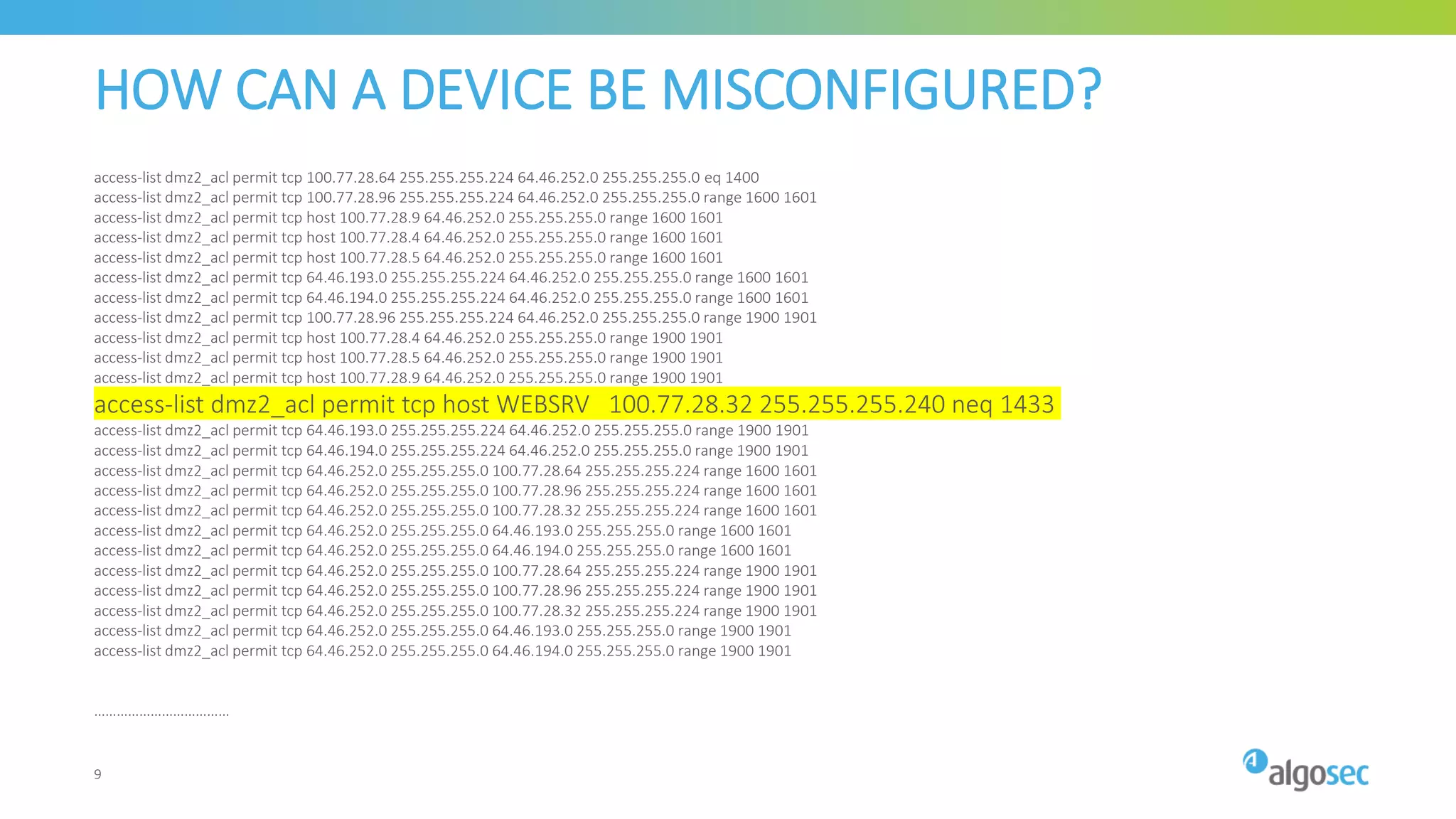
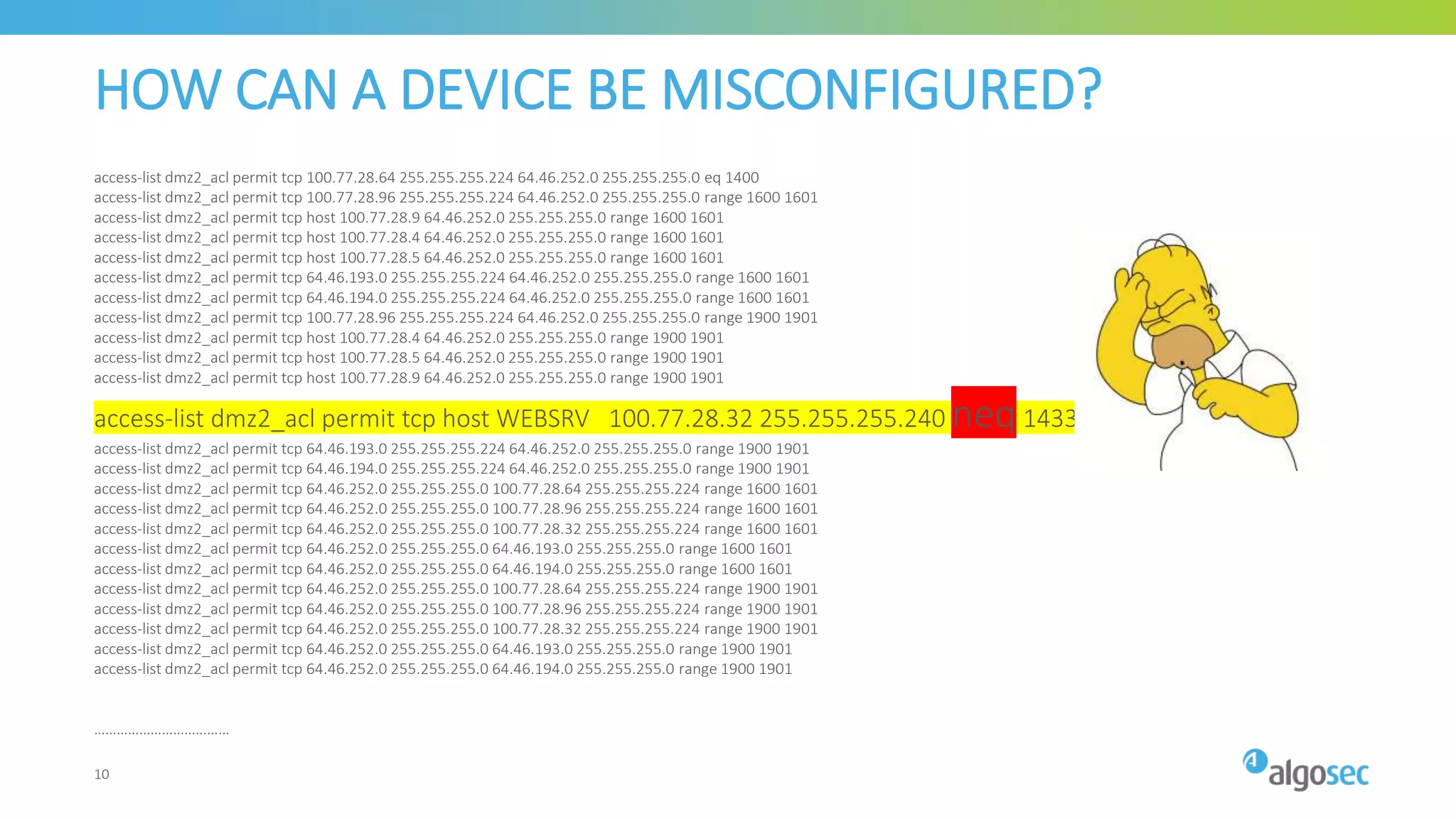
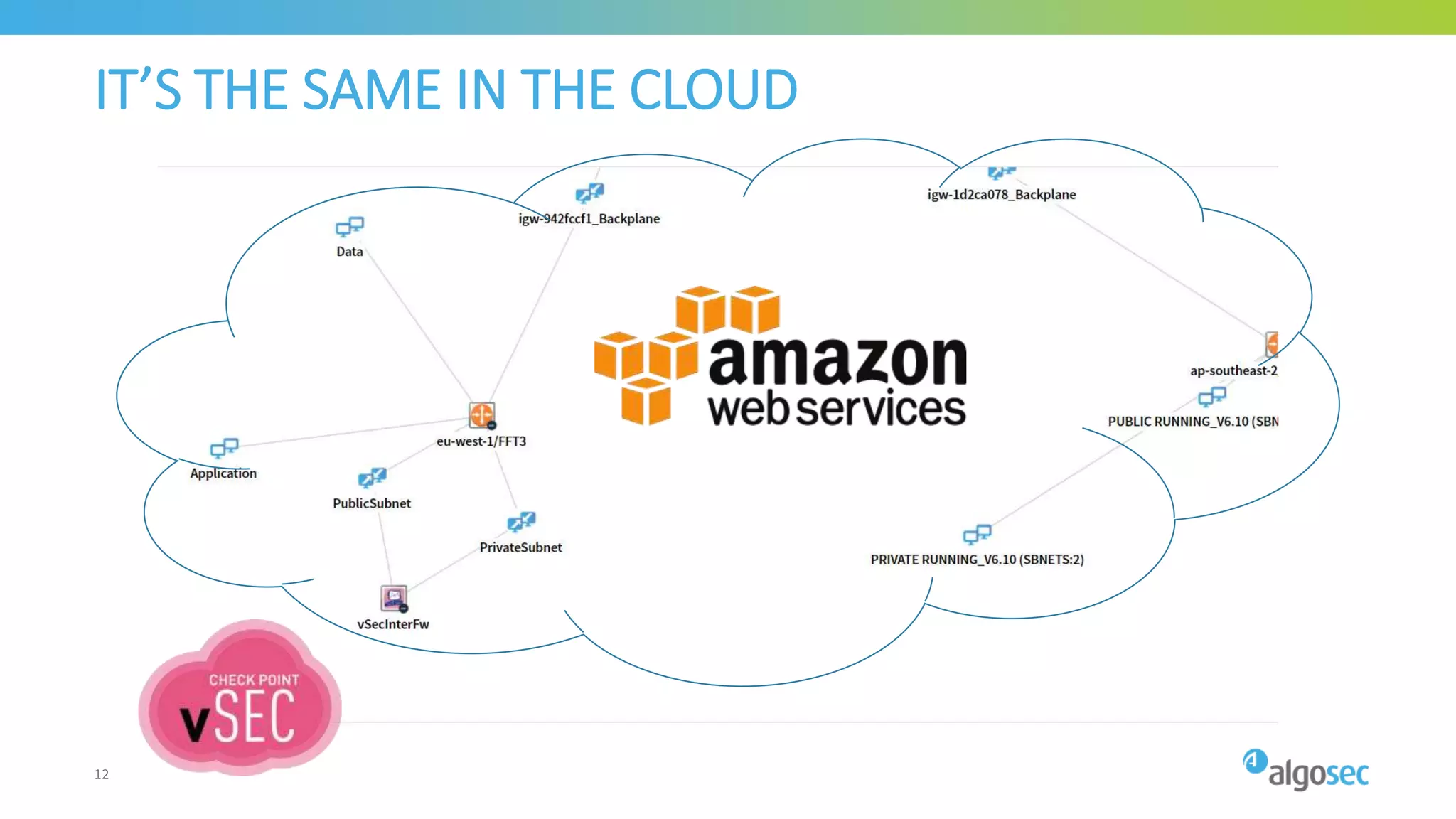
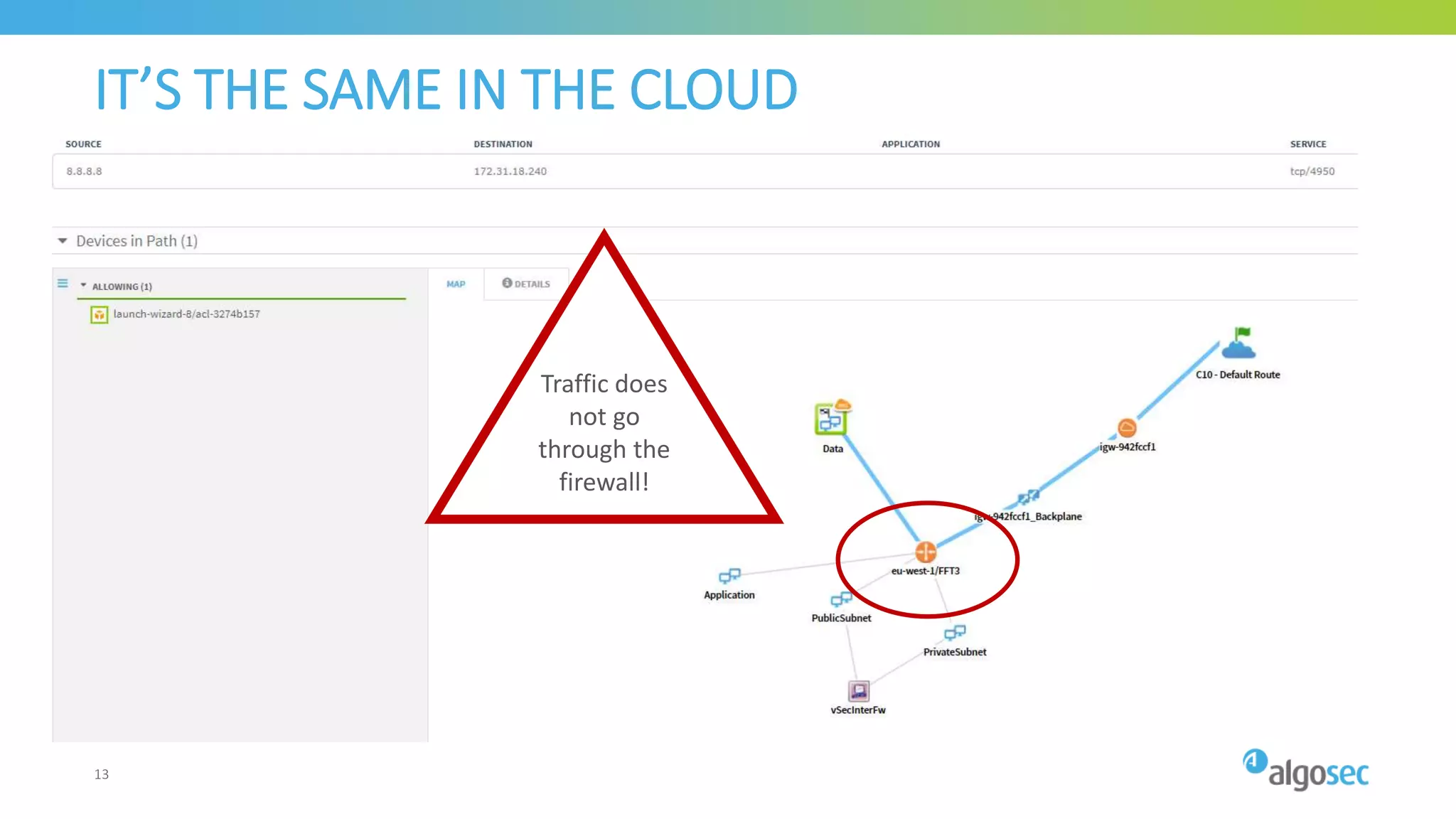
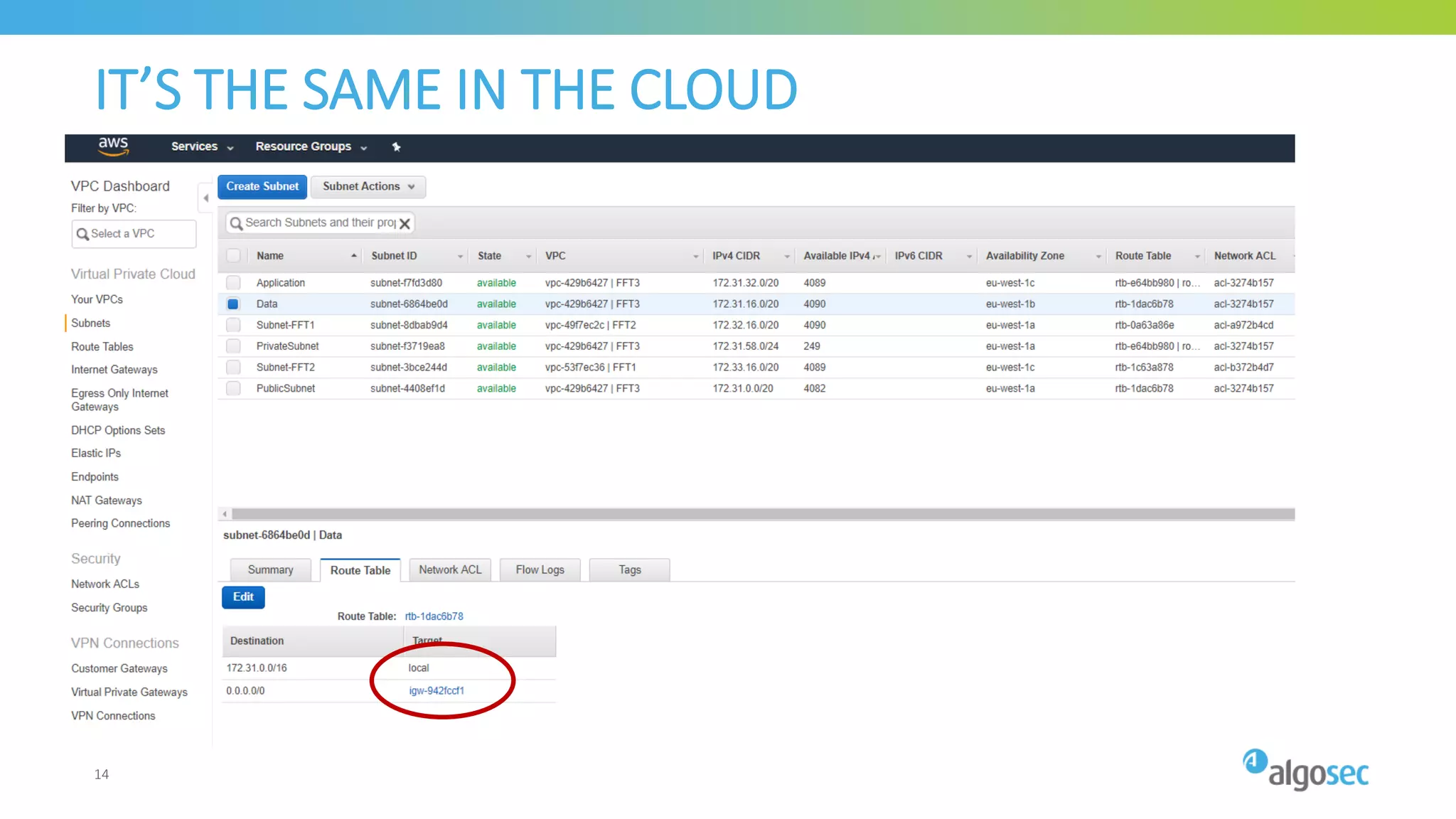
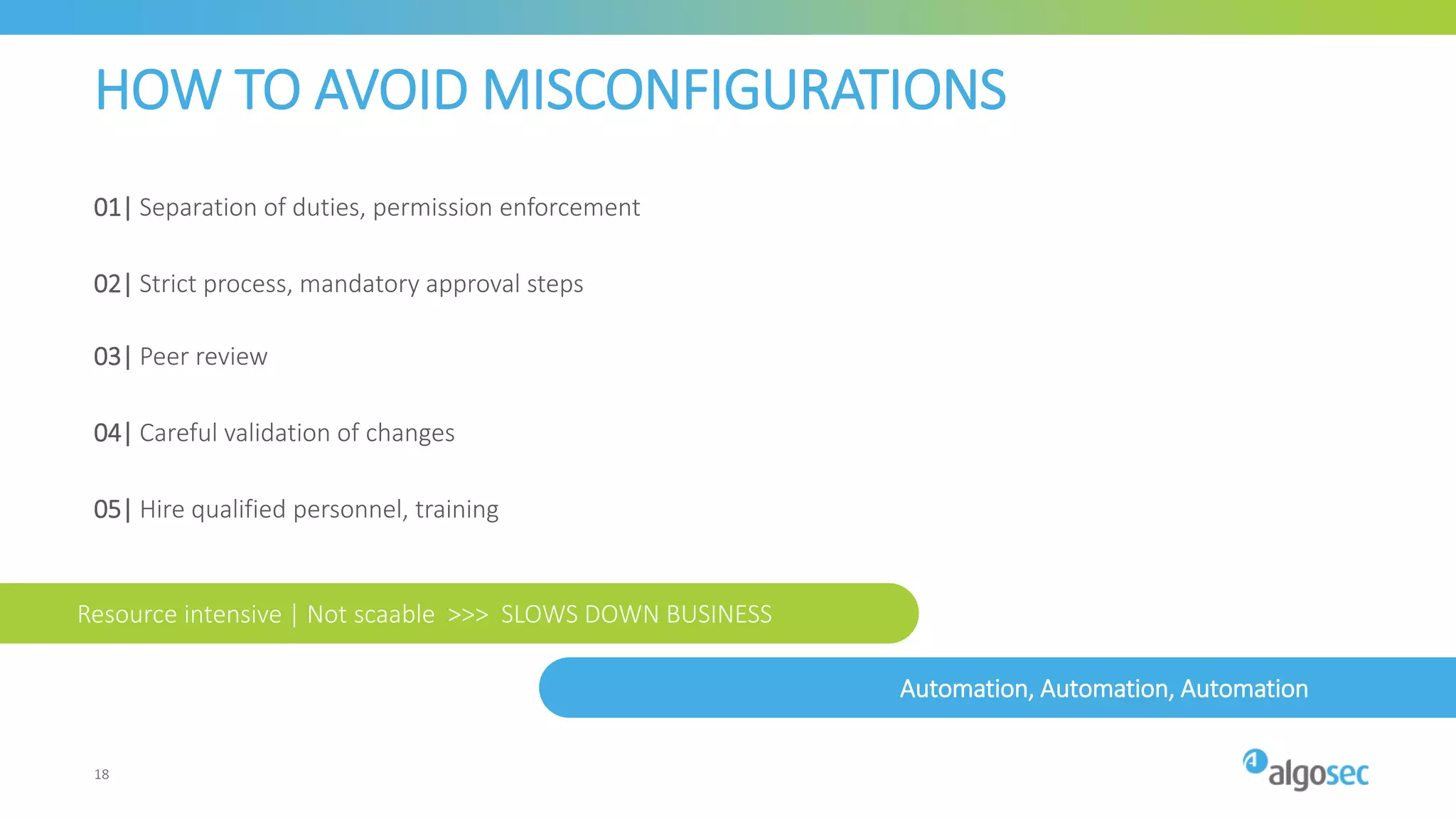
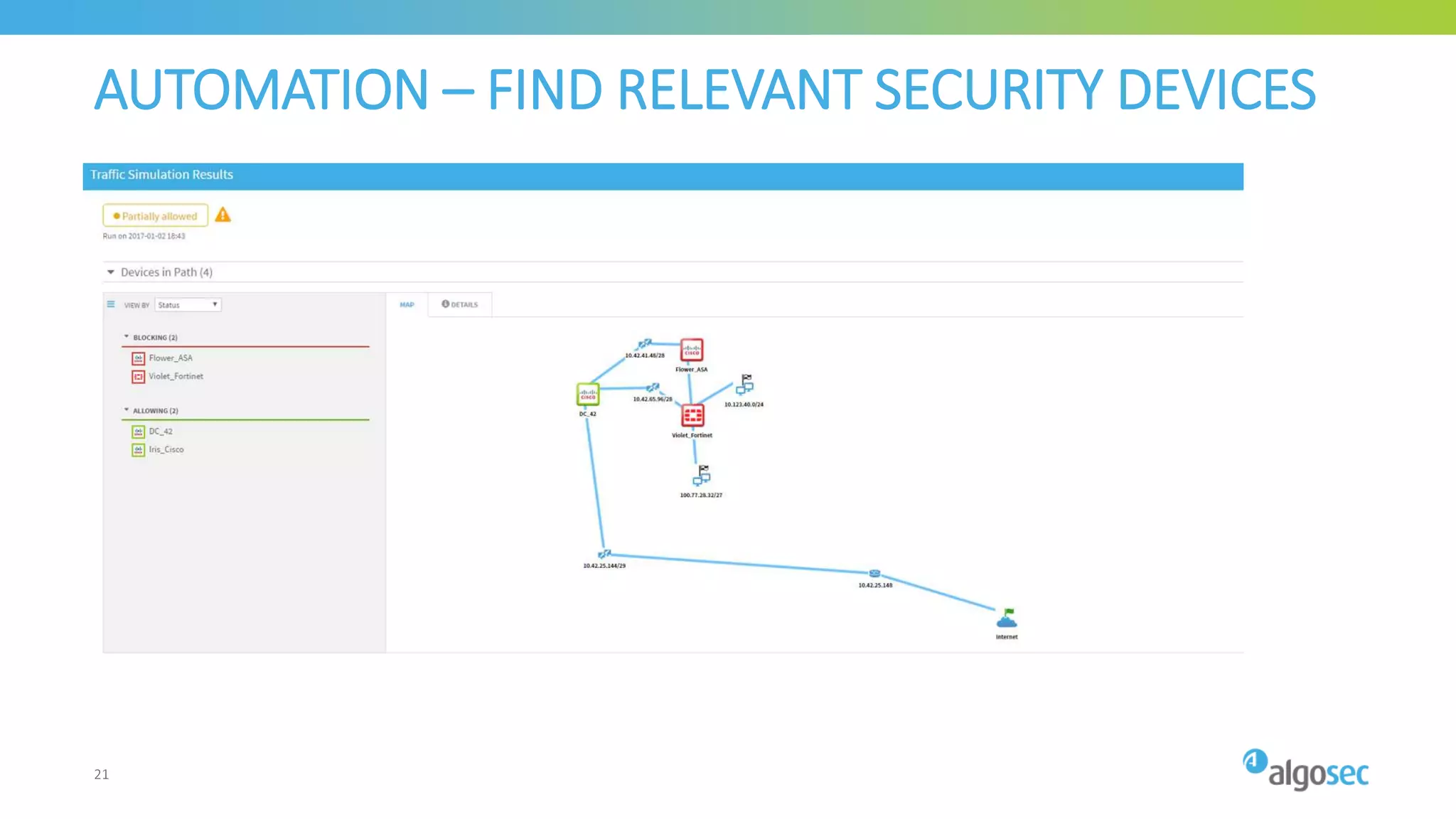
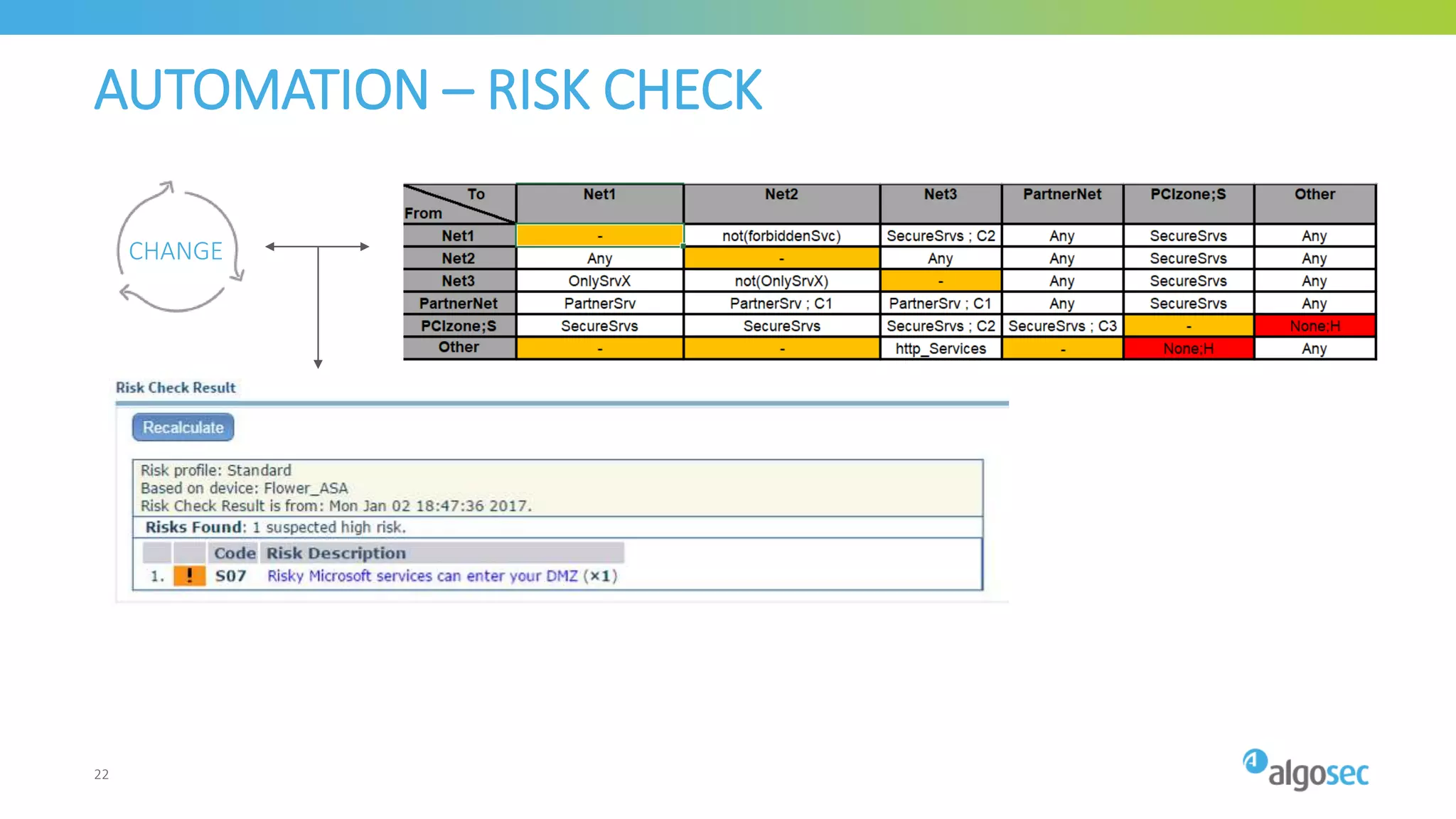
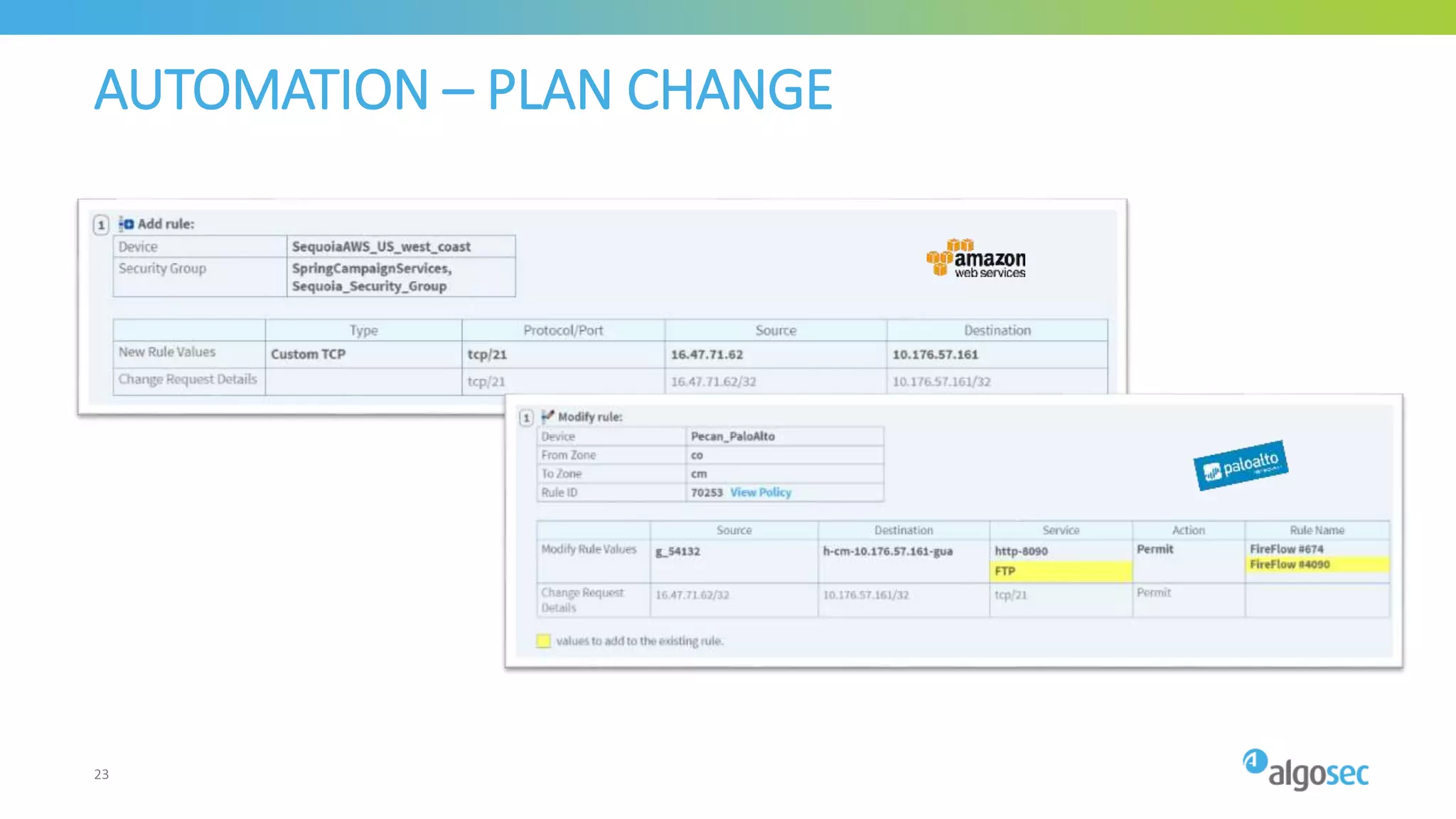
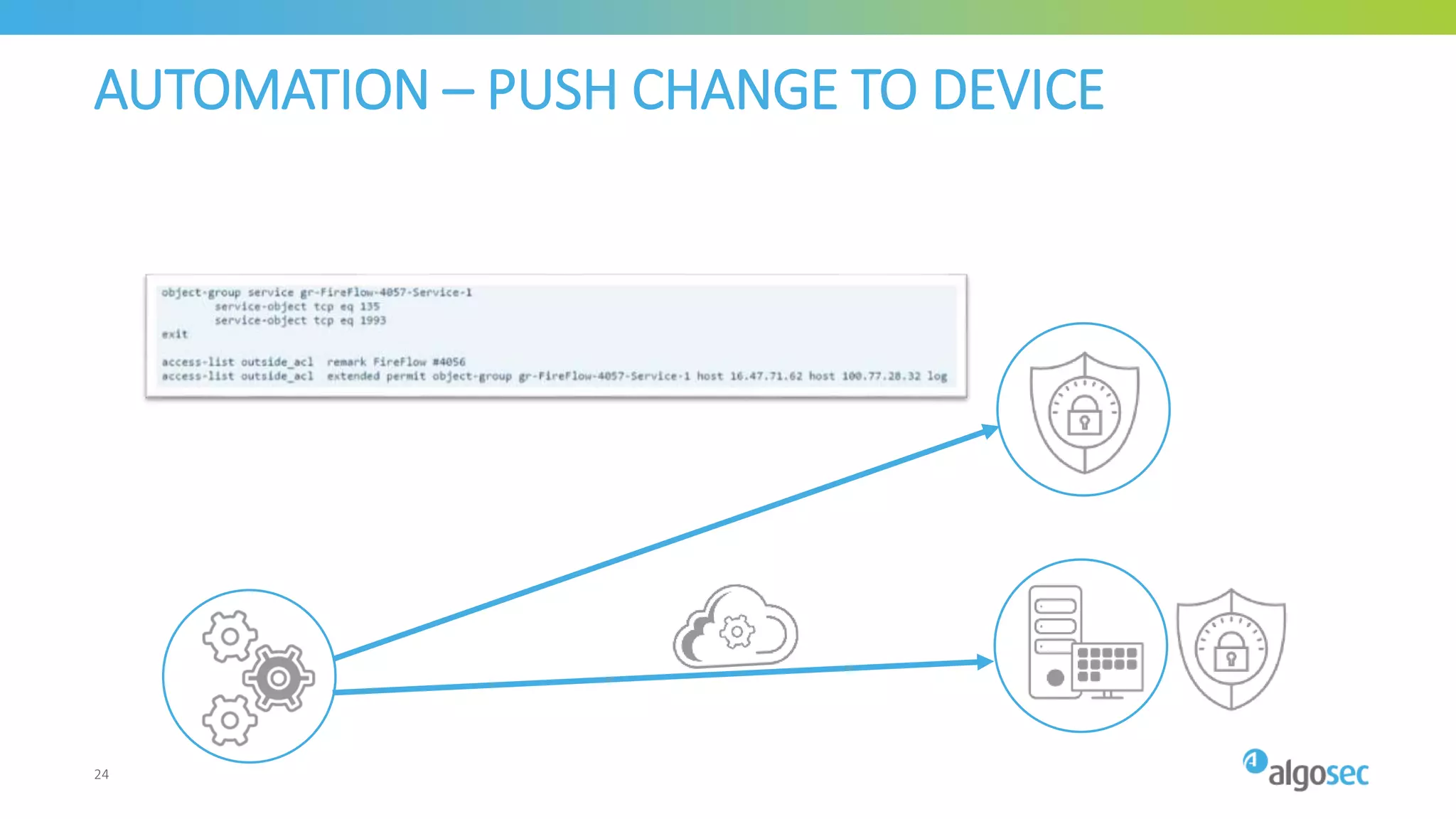
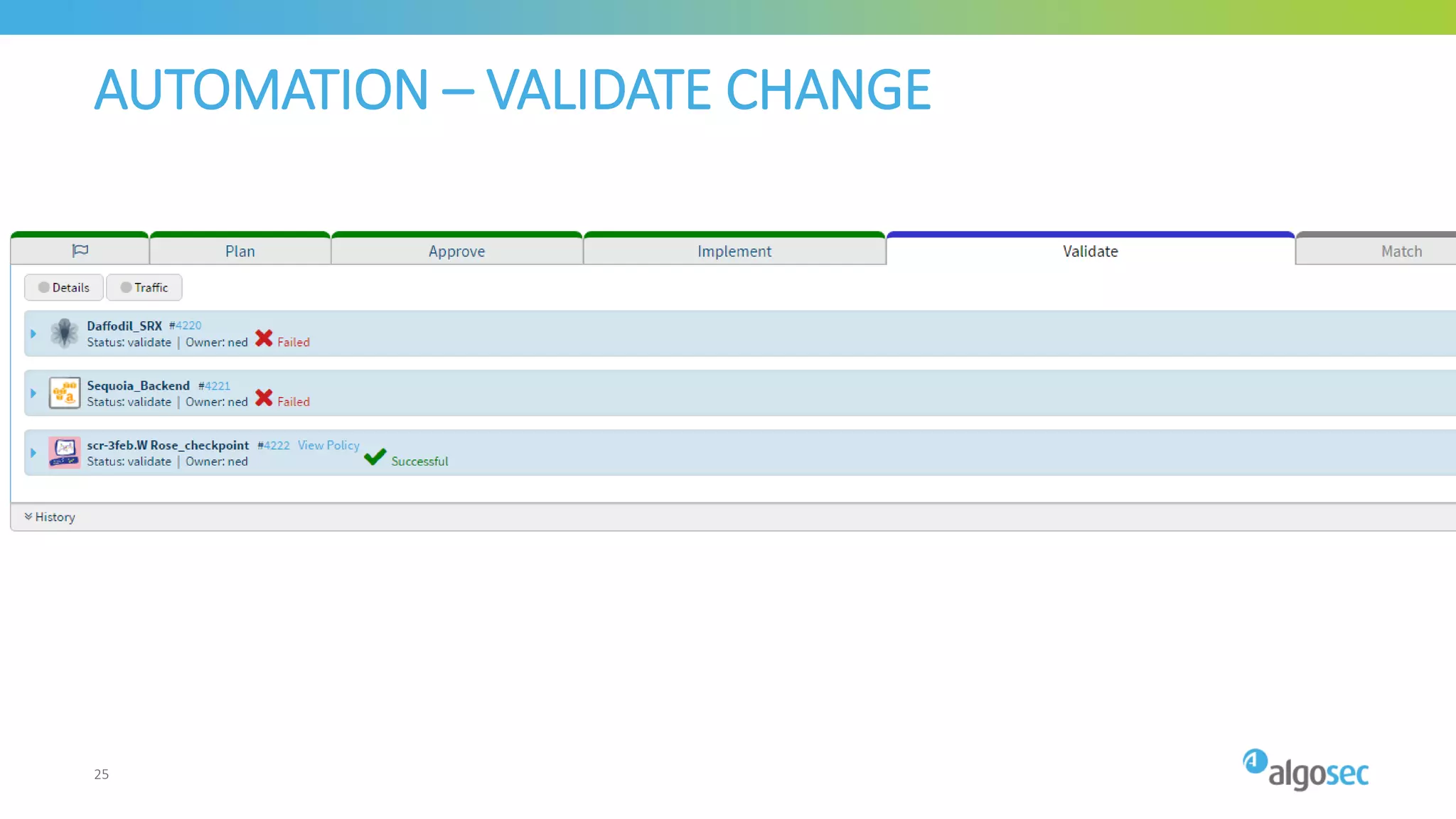
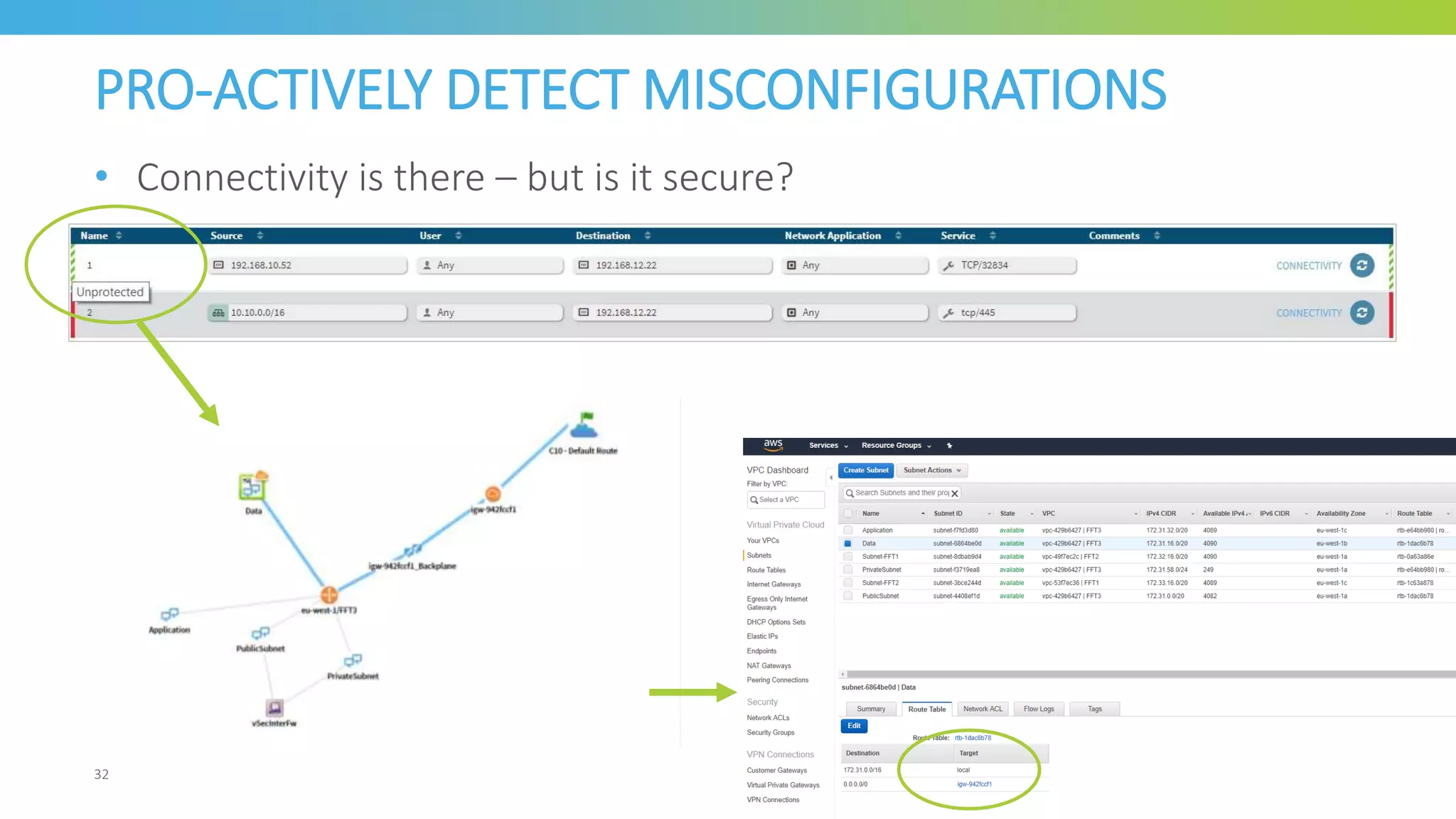
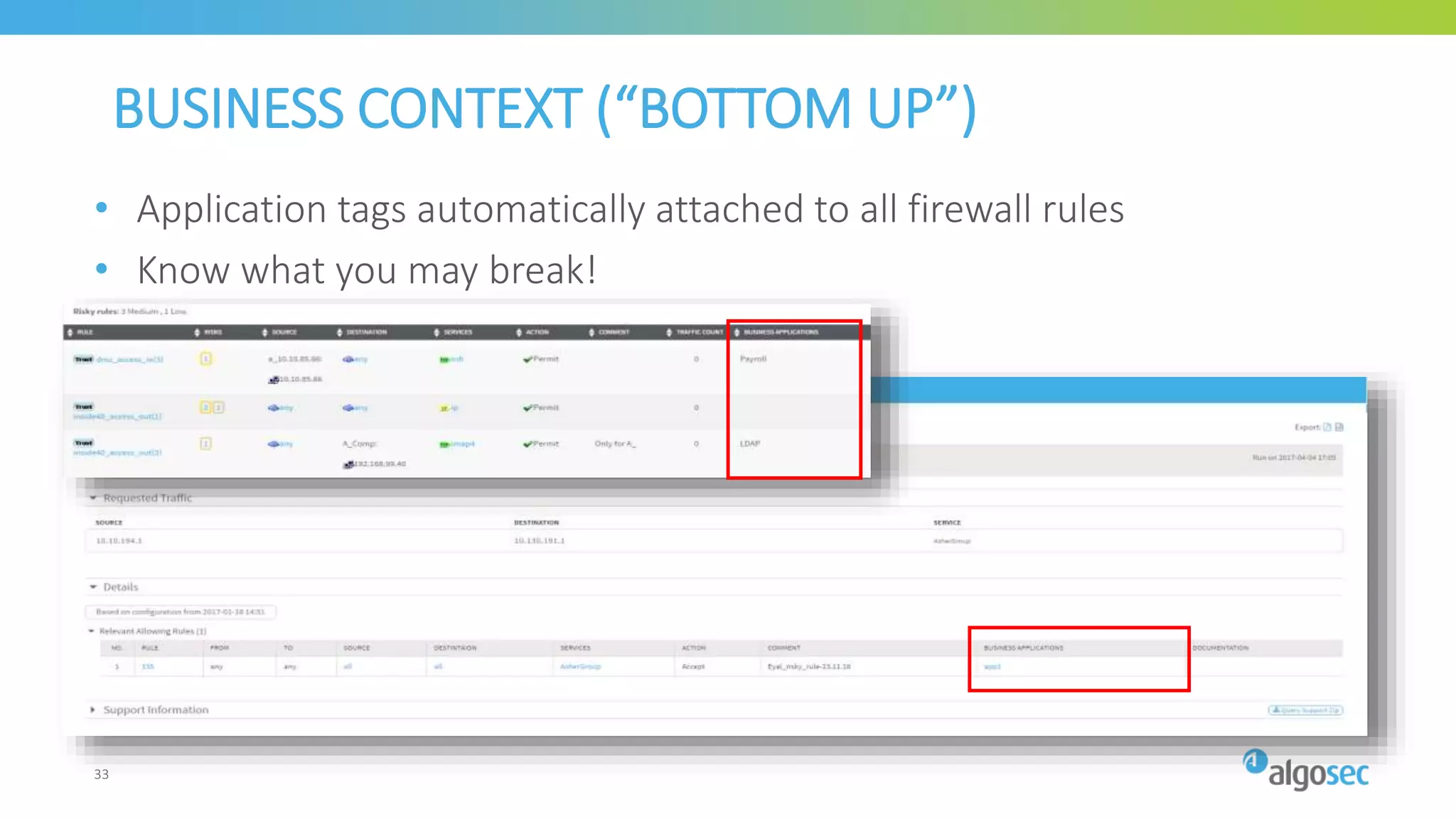
The document outlines the risks associated with network misconfigurations and highlights the importance of avoidance through automation and rigorous processes. It emphasizes common mistakes that can lead to vulnerabilities and operational downtime, underscoring the significance of trained personnel and strict change validation. Additionally, it presents examples showcasing the potential impacts of misconfigurations on business continuity and security.