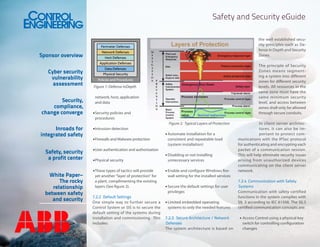
This document discusses the importance of conducting a cyber security vulnerability assessment. It recommends beginning by selecting a security standard to guide the assessment. A key step is taking an inventory of all cyber assets, how they are connected and configured. This information should be documented and updated regularly. The document provides tips for involving staff, reviewing documentation, analyzing network and wireless traffic, and physically verifying connections. The goal is to identify vulnerabilities before a hacker could exploit them.