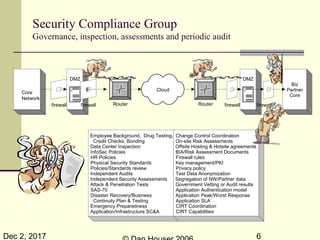
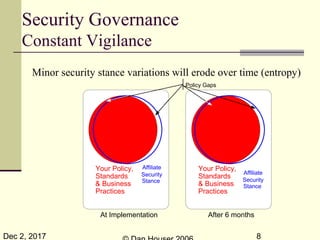
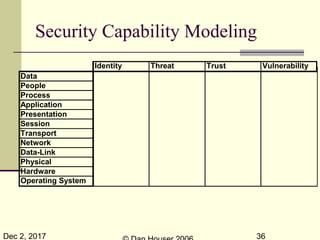
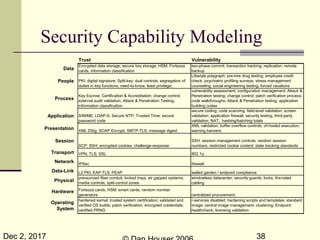
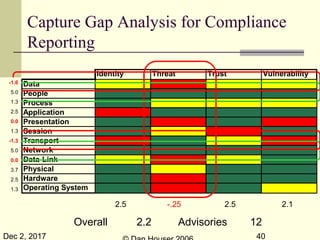
The document discusses the complexities of security capability modeling in the context of changing business dynamics and increasing risks from third-party integrations. It outlines various laws and regulations impacting information security, the evolving model of security compliance, and the observations of the risks and challenges specific to third-party assessments. Additionally, it suggests the necessity for rapid risk assessments that can keep pace with business developments and outlines several preventive measures and controls against various types of security threats.