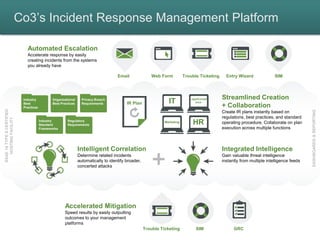
The document introduces speakers Bill Campbell and Ted Julian, both with extensive backgrounds in the security and compliance industry. It outlines key themes for a presentation aimed at newly appointed Chief Information Security Officers, including understanding their context, changes they will face, and strategies for effective onboarding. Co3 Systems is highlighted for its incident response management platform, emphasizing automated escalation and collaborative incident response planning.