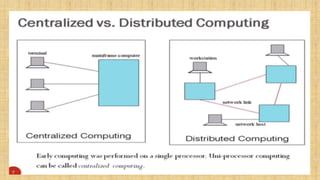
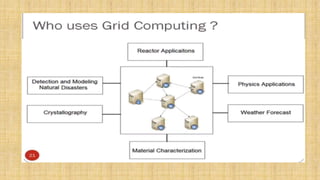
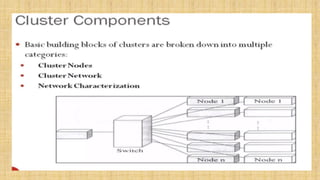
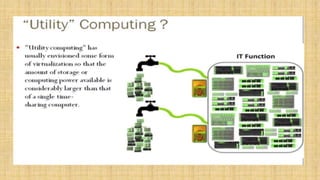
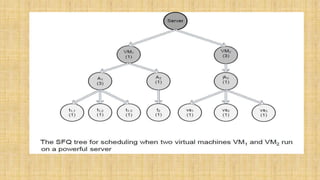
The document discusses cloud resource management and cloud computing architecture. It covers the following key points in 3 sentences:
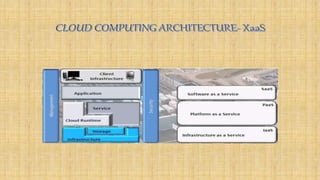
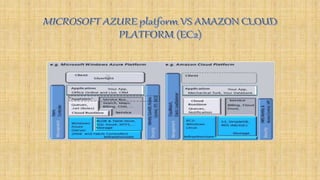
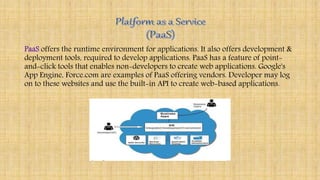
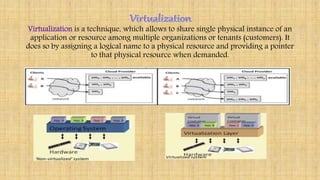
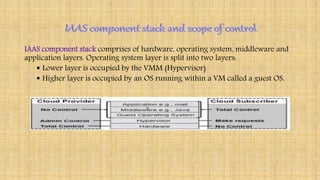
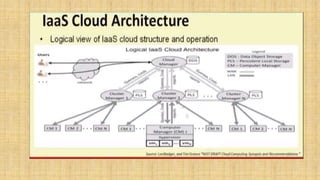
Cloud architecture can be broadly divided into the front end, which consists of interfaces and applications for accessing cloud platforms, and the back end, which comprises resources for providing cloud services like storage, virtual machines, and security mechanisms. Common cloud service models include infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). Virtualization techniques allow for the sharing of physical resources among multiple organizations by assigning logical names to physical resources and providing pointers to access them.