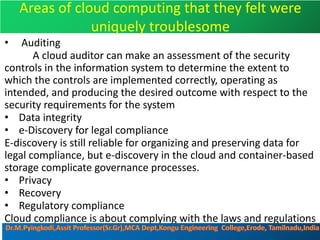
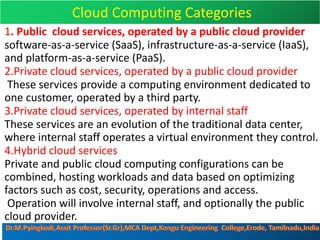
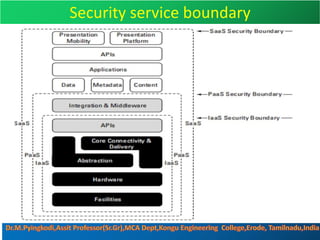
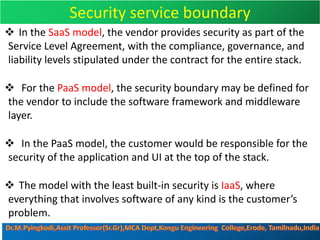
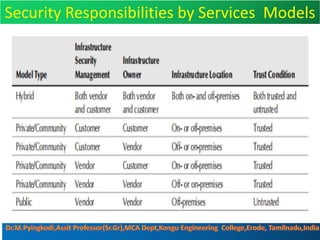
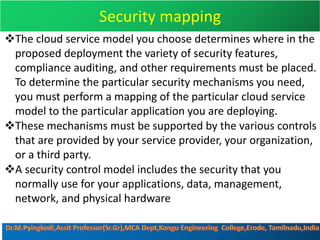
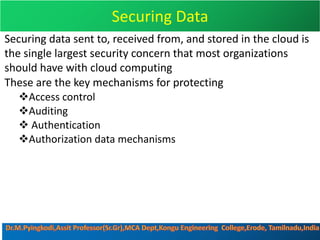
Cloud security consists of policies, controls, procedures and technologies that work together to protect cloud systems, data and infrastructure. It secures cloud environments against external and internal threats through authentication, traffic filtering and configuring security based on business needs. Key challenges include attacks moving faster than protections can be implemented and ensuring security audits and adoption of new technologies do not introduce risks. Responsibilities are divided between the customer and provider based on the cloud service model used.