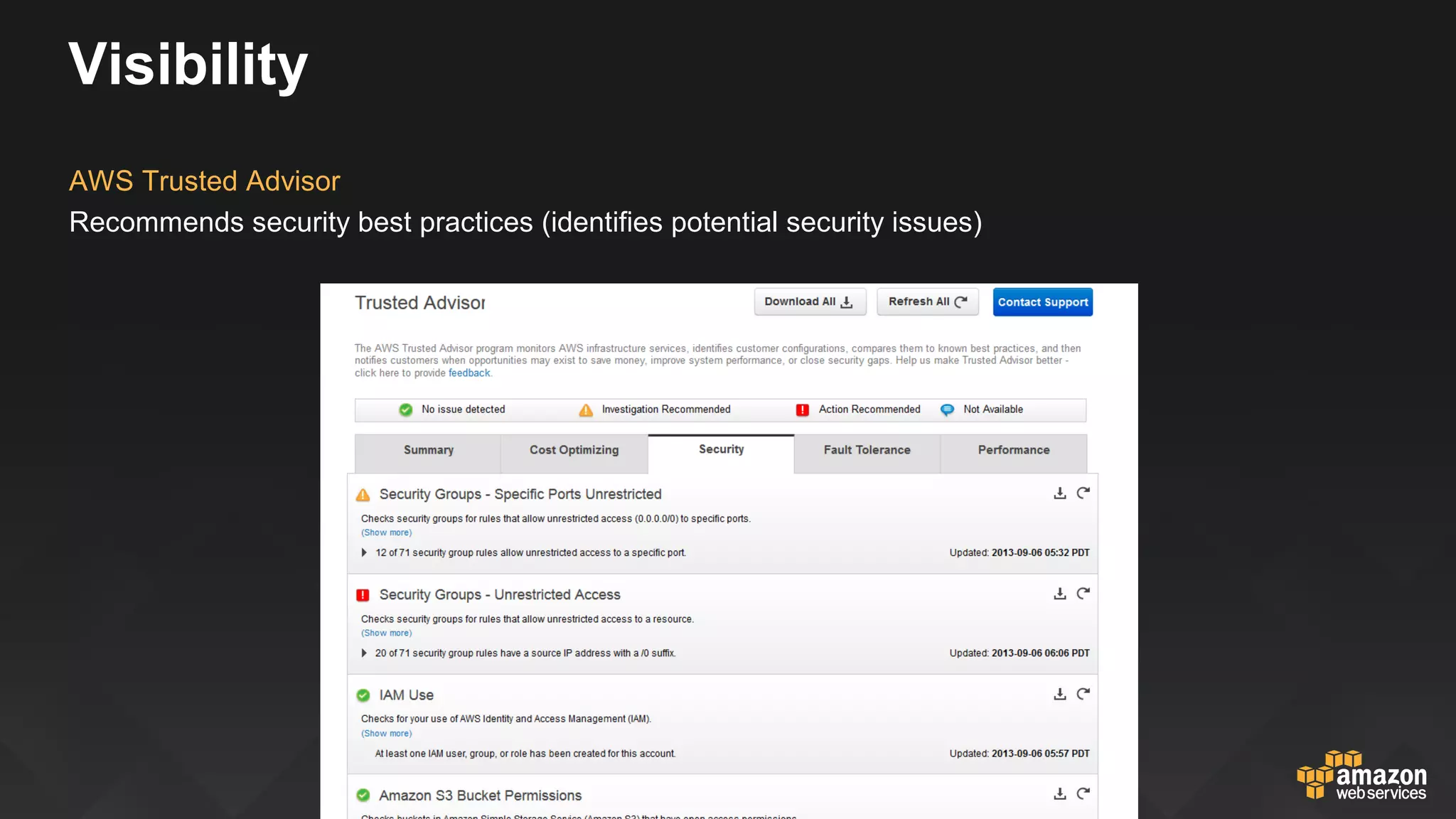
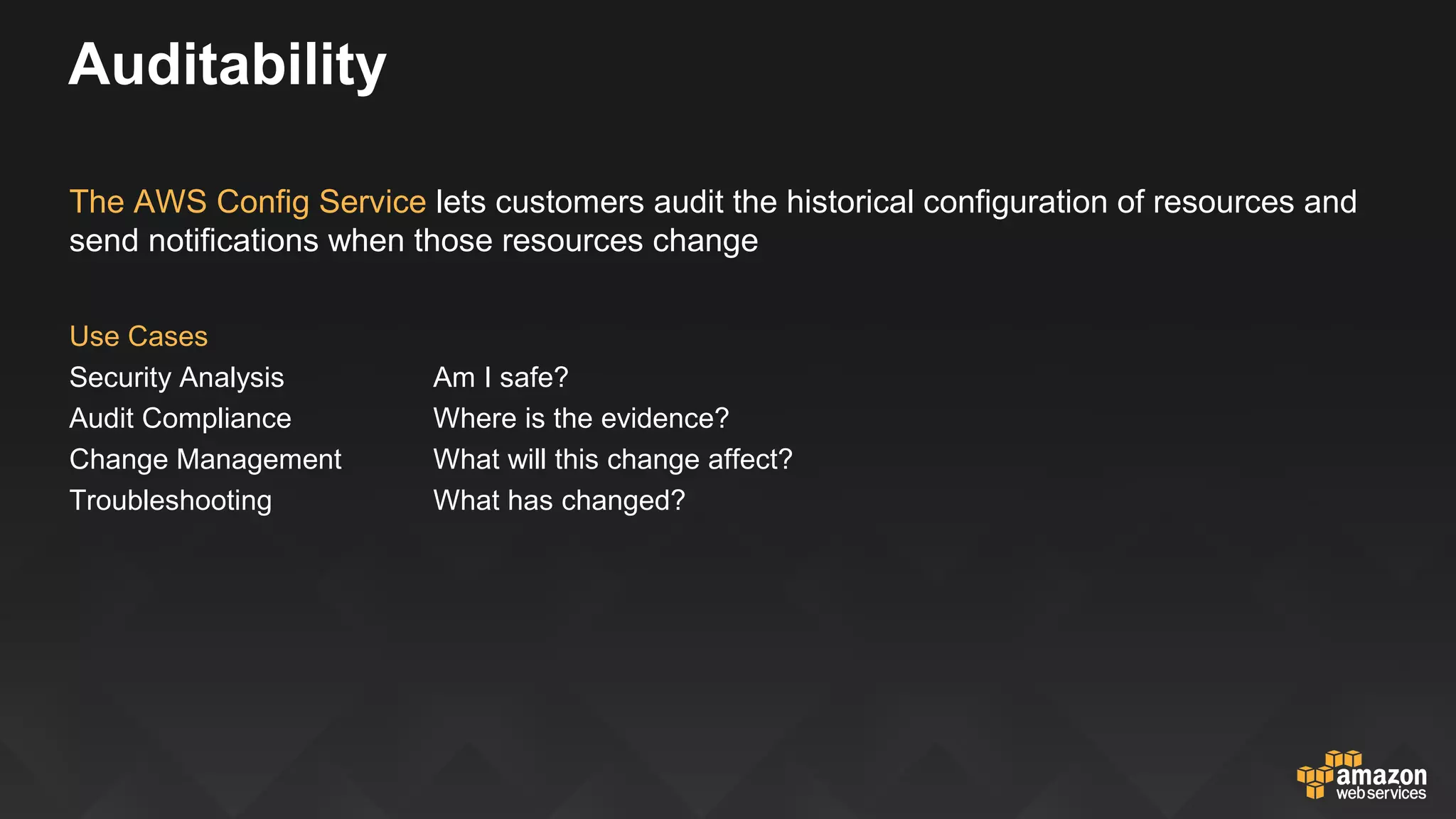
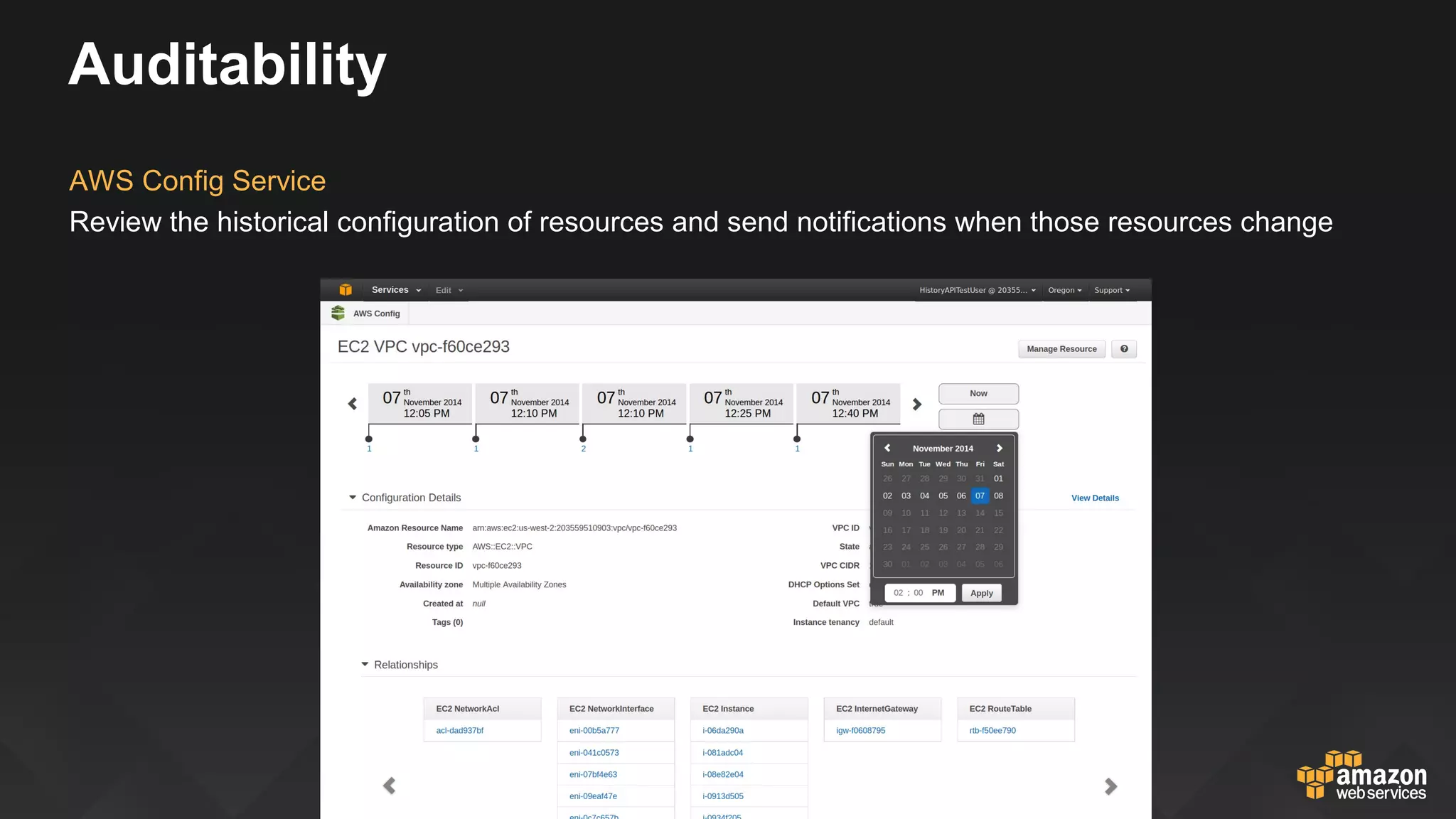
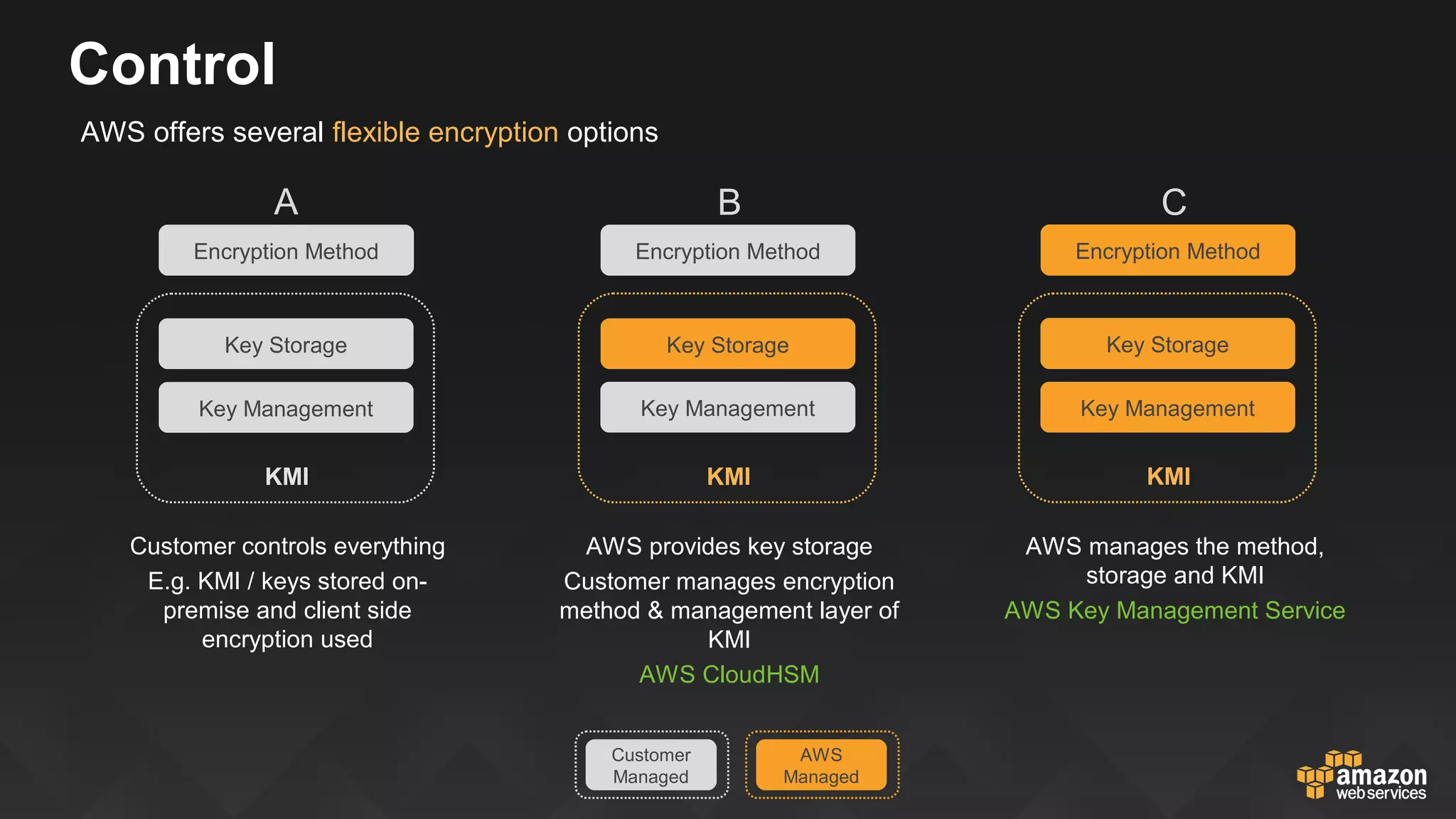
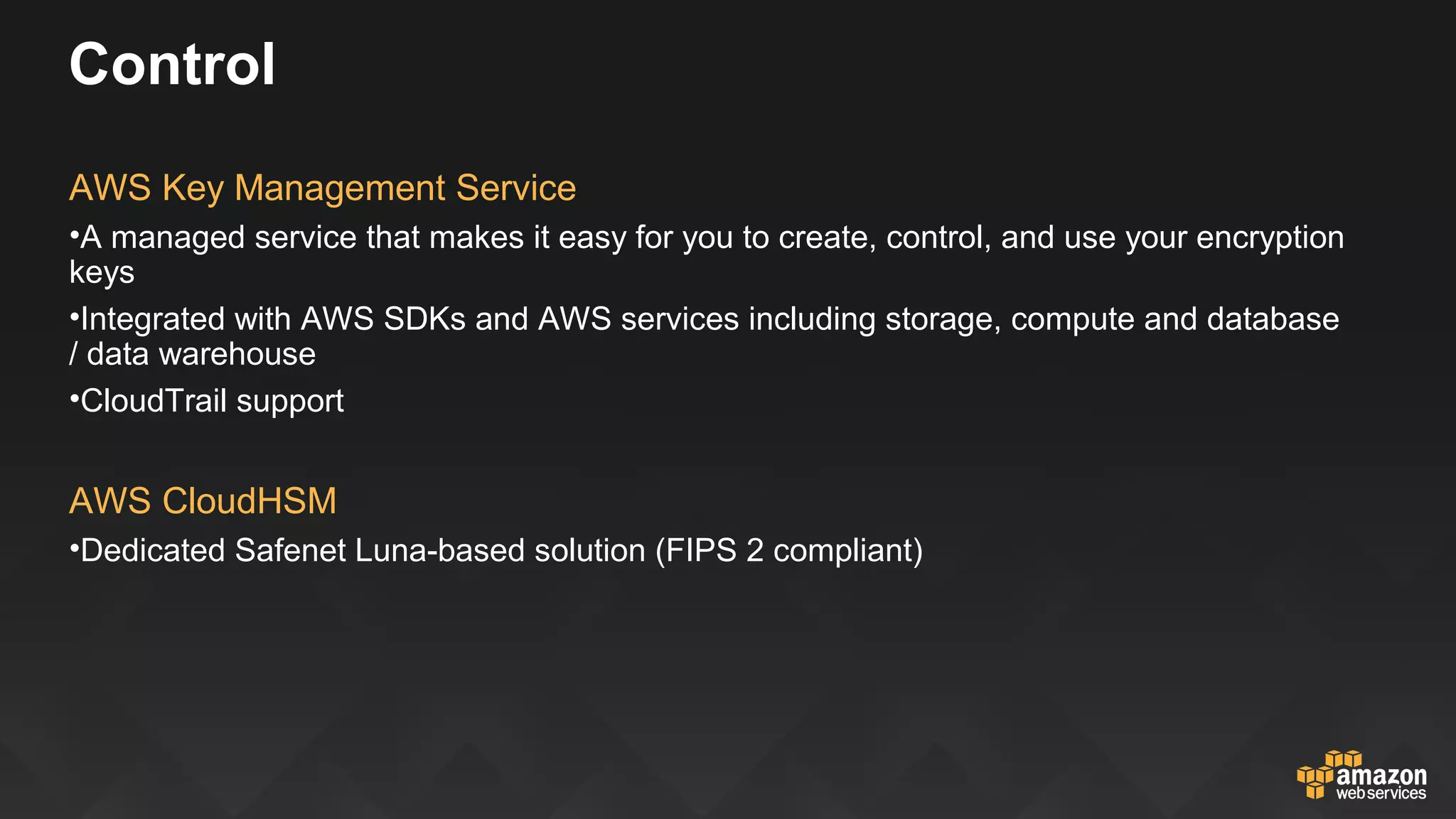
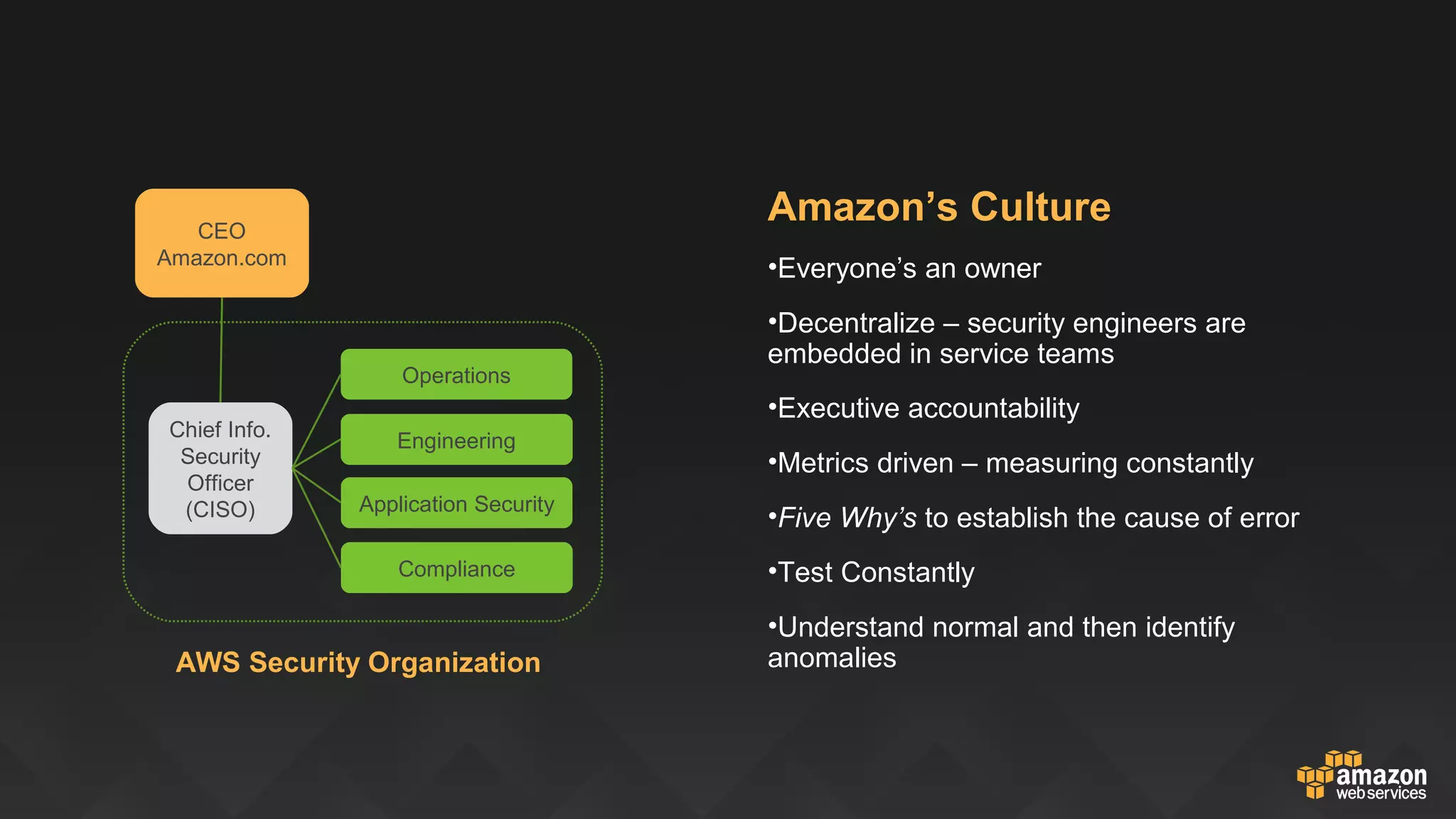
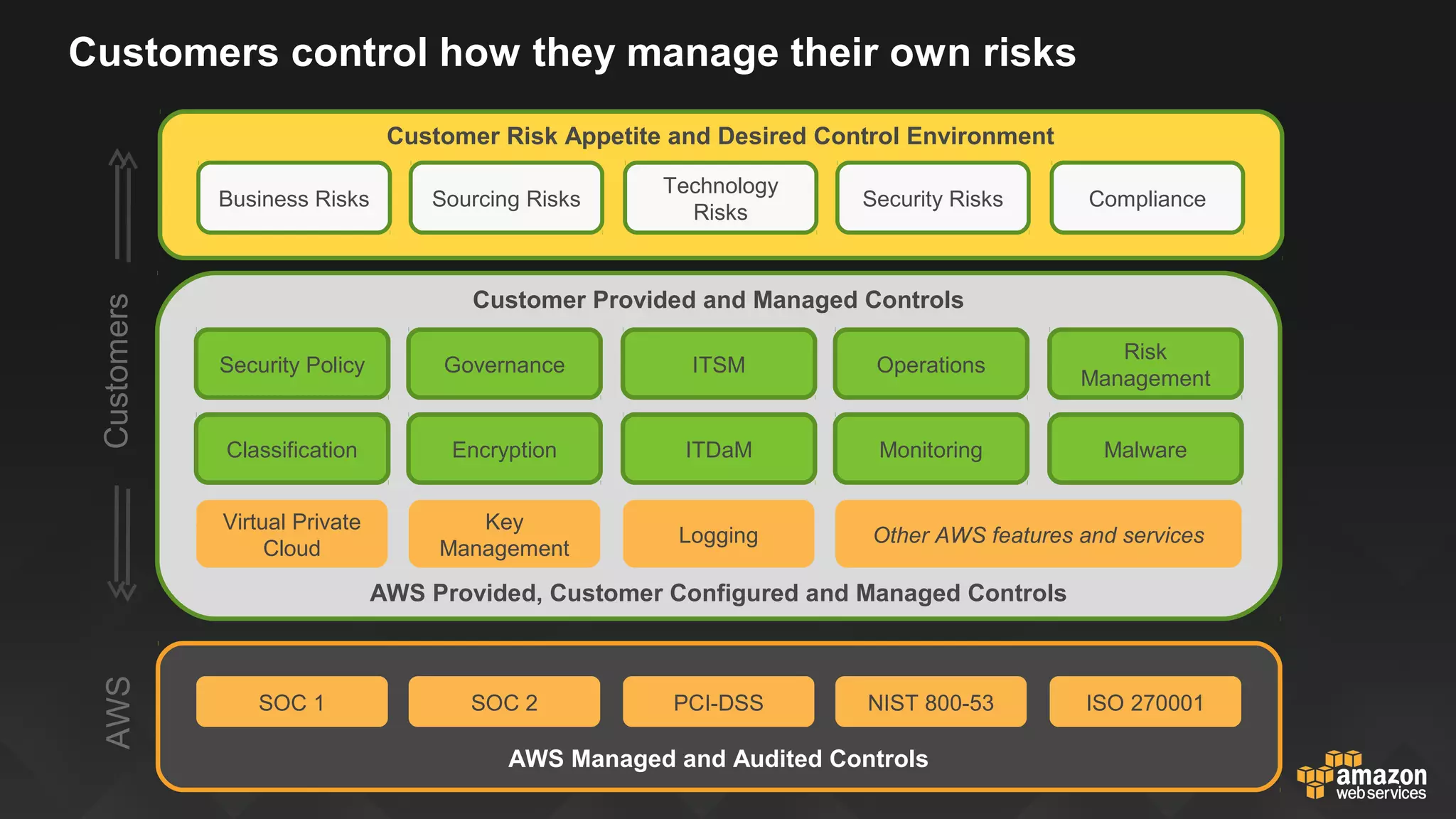
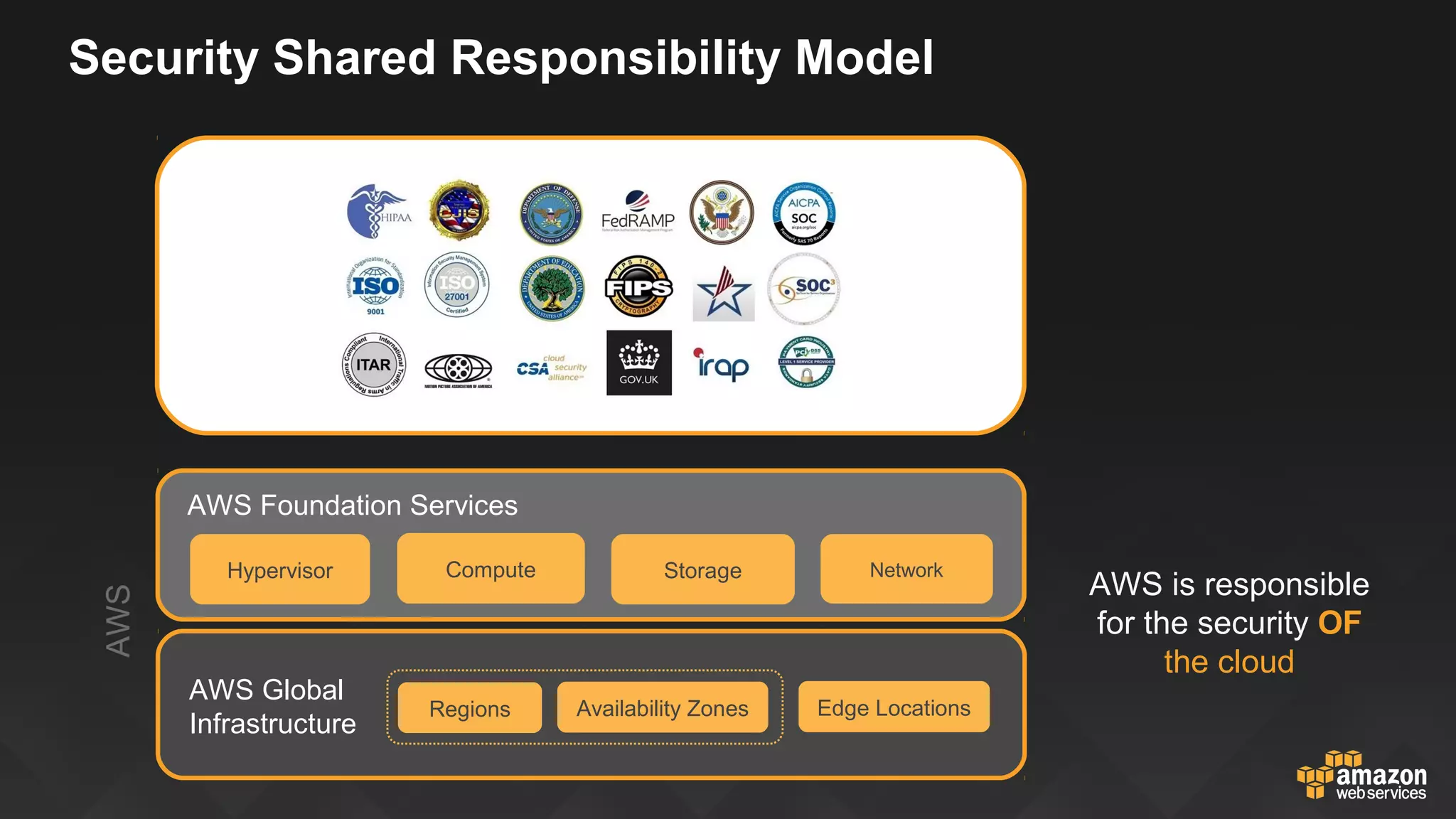
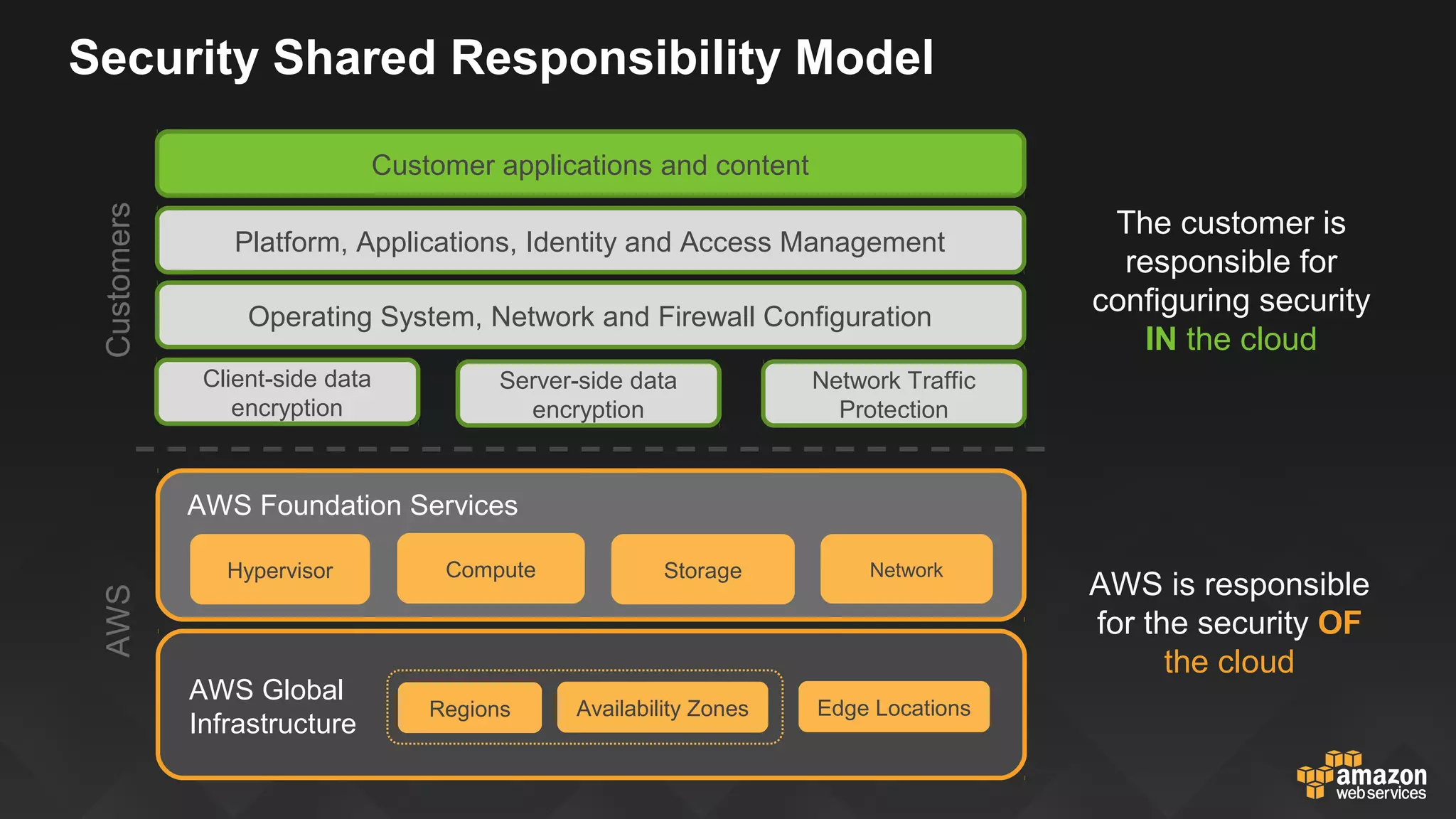
This document discusses governance, risk, and compliance considerations for using AWS cloud services. It outlines AWS assurance programs that provide regular third-party security evaluations. It also describes the shared responsibility model where AWS is responsible for security of the cloud and customers are responsible for security in the cloud. The document provides examples of how AWS services like CloudTrail, Config, and Key Management Service provide visibility, auditability, and control to help customers meet their security and compliance needs.





![“Based on our experience, I believe that we can be even more
secure in the AWS cloud than in our own data centers.”
Tom Soderstrom, CTO, NASA JPL
Nearly 60% of organizations agreed that CSPs [cloud service
providers] provide better security than their own IT organizations.
Source: IDC 2013 U.S. Cloud Security Survey
doc #242836, September 2013](https://image.slidesharecdn.com/2015summit-hk-cloud-riskcompliance-karimh-v1-150927033158-lva1-app6891/75/Cloud-Security-Risk-and-Compliance-on-AWS-12-2048.jpg)