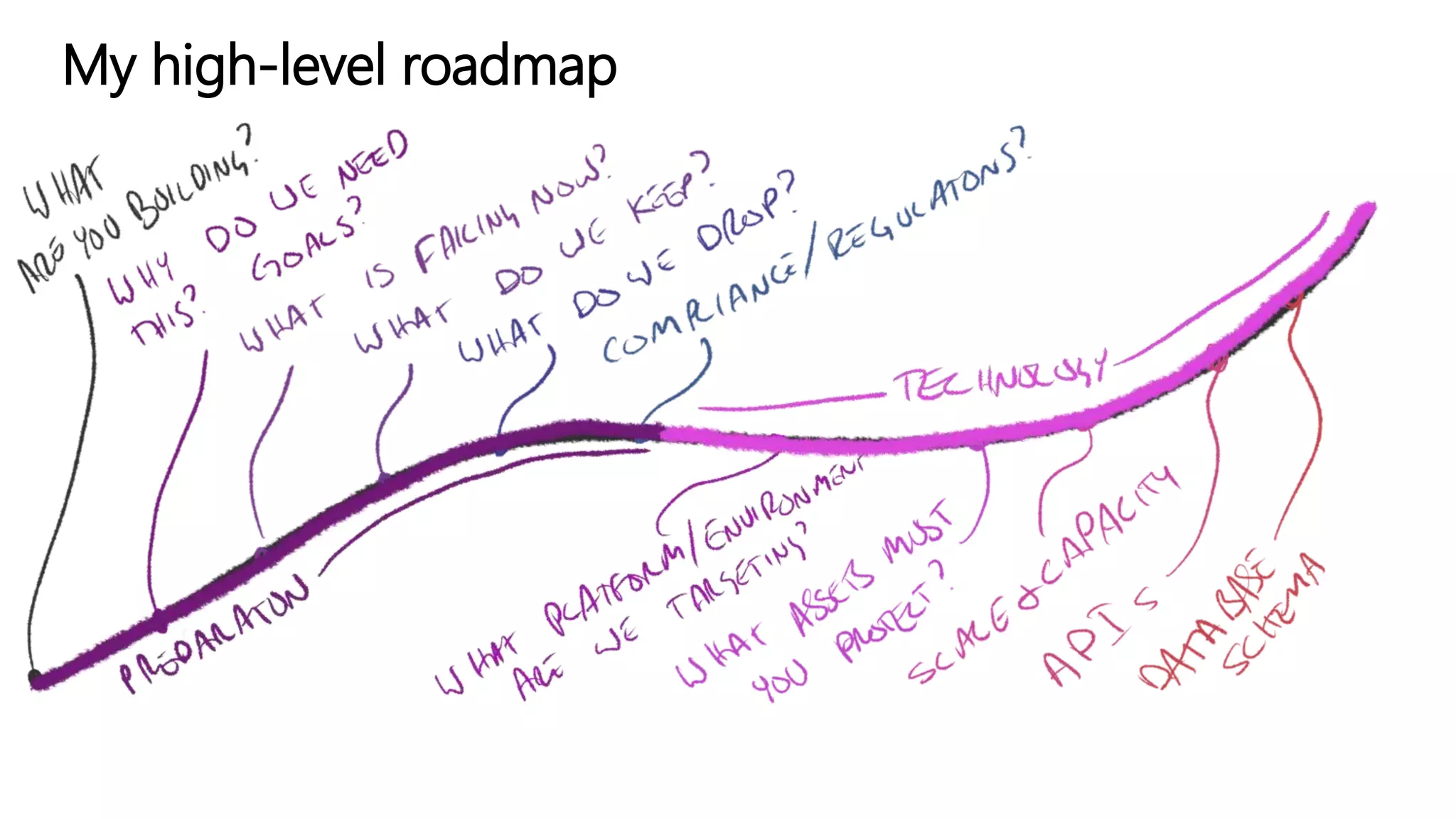
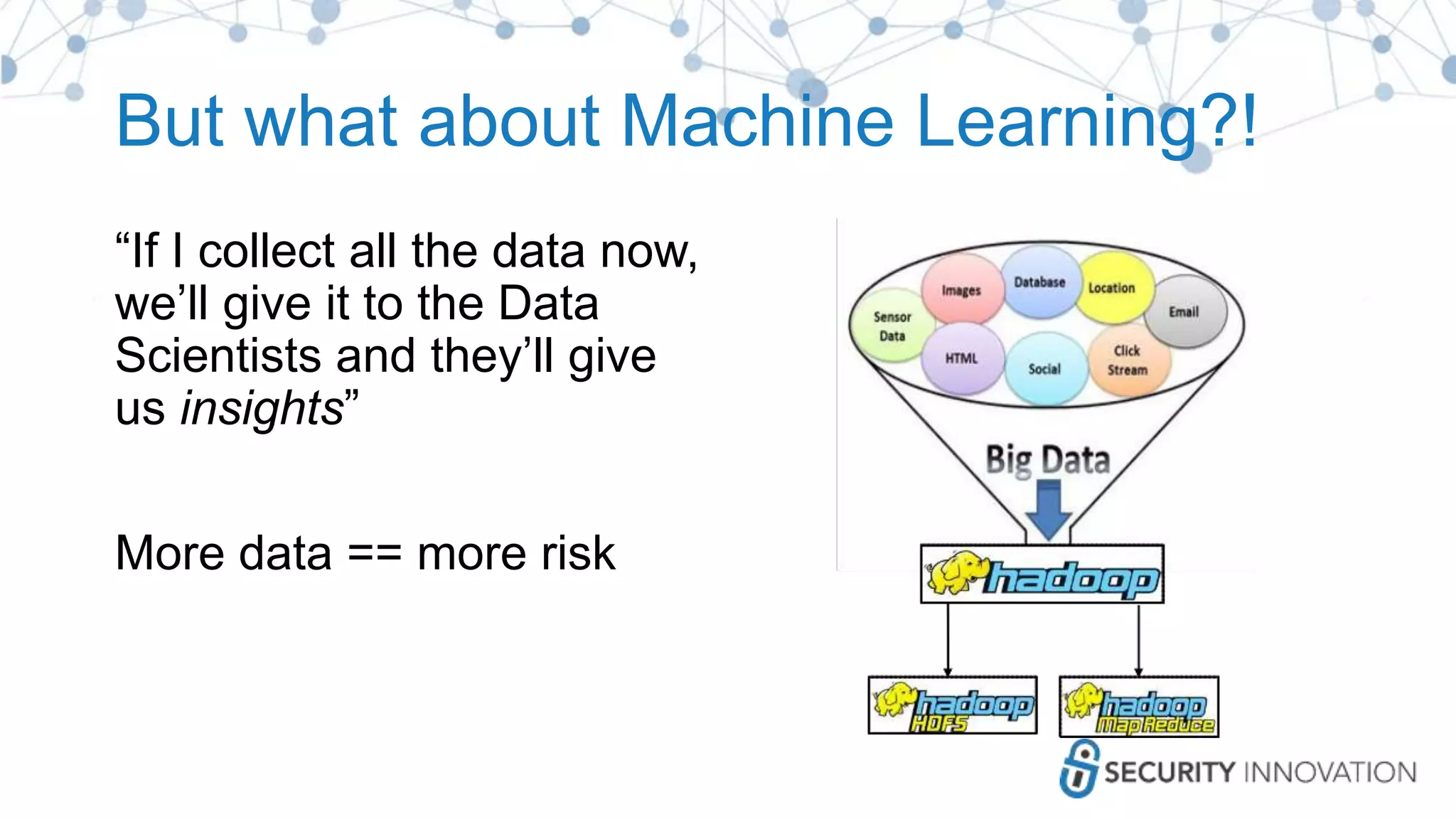
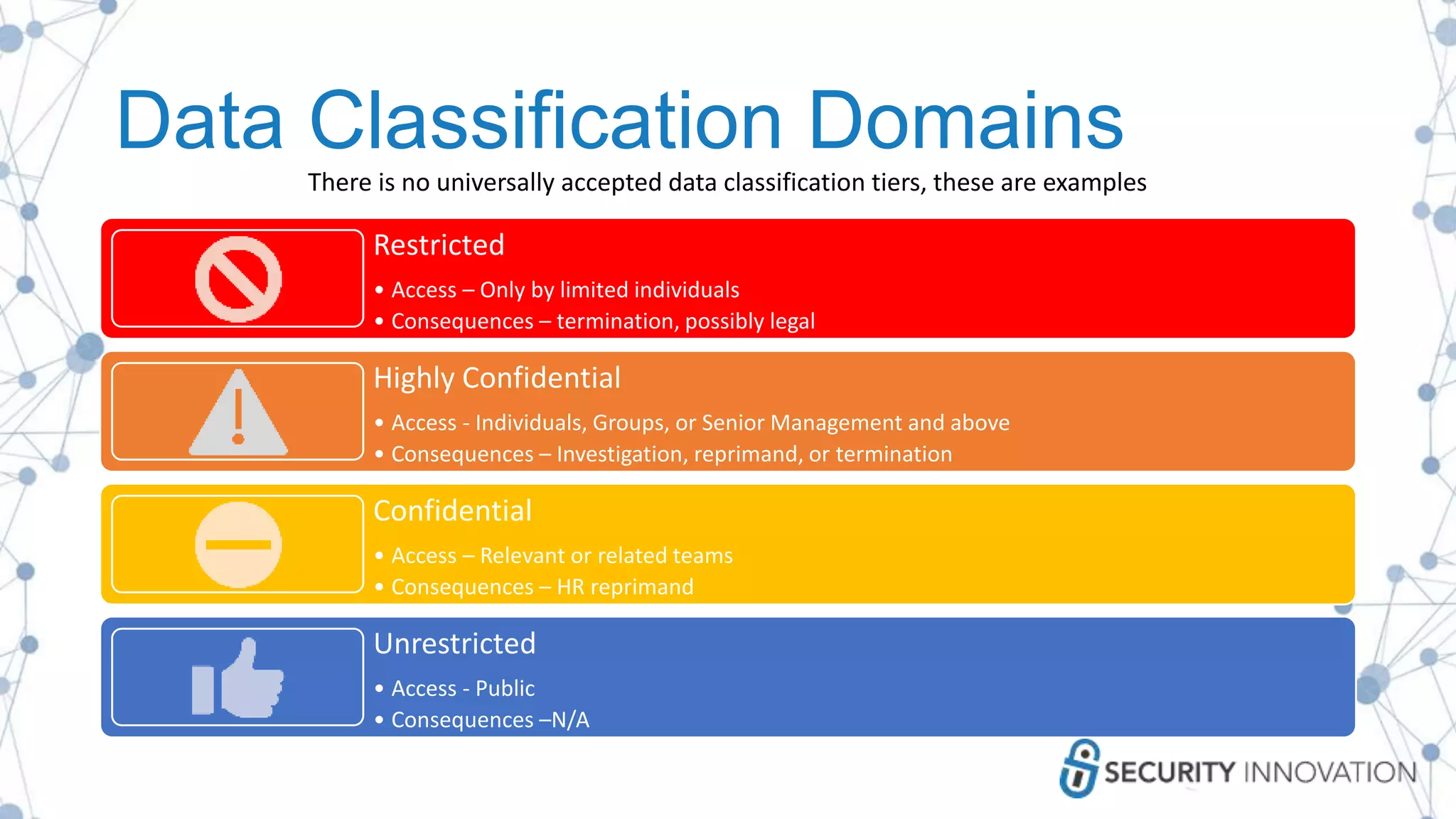
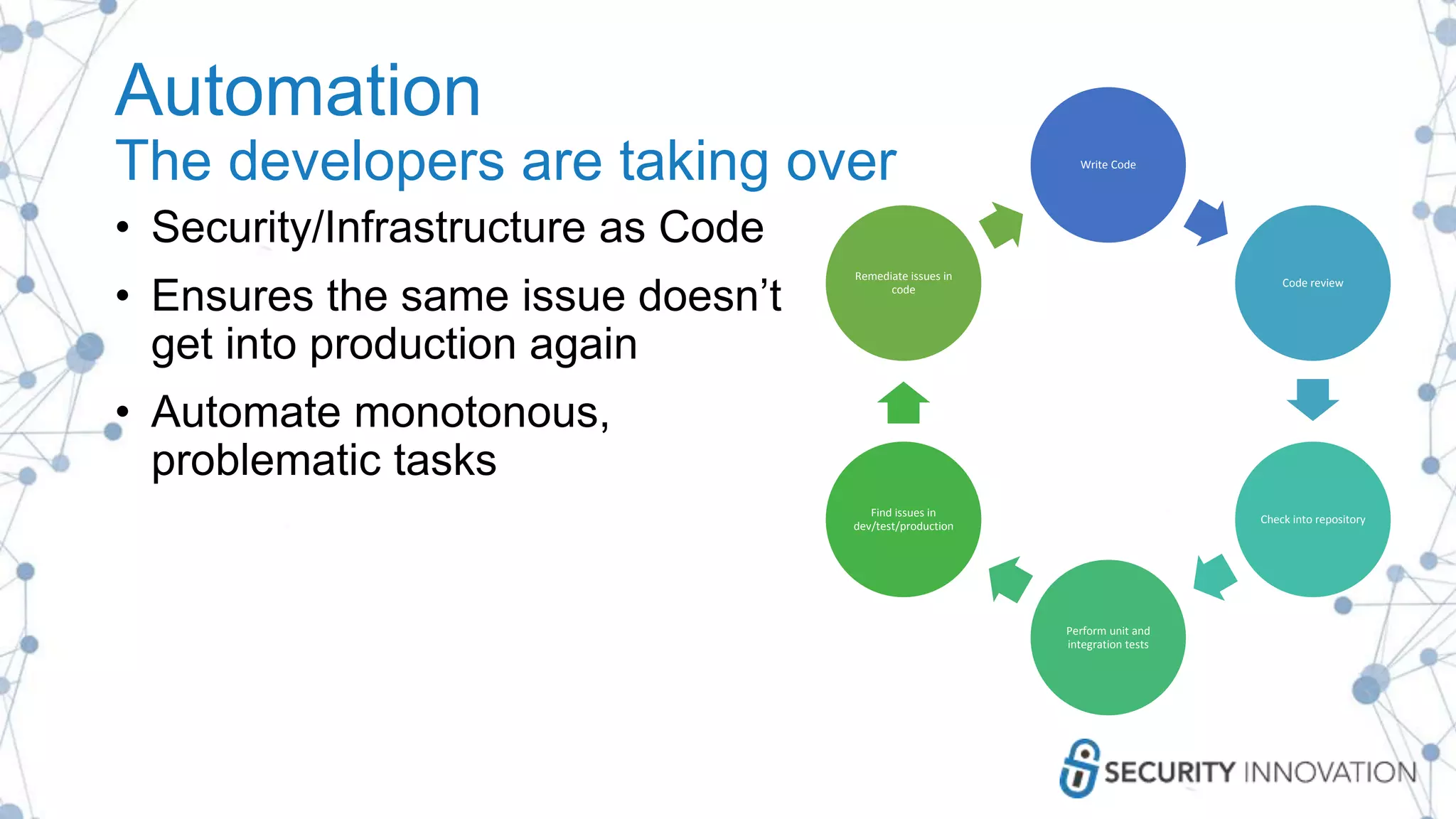
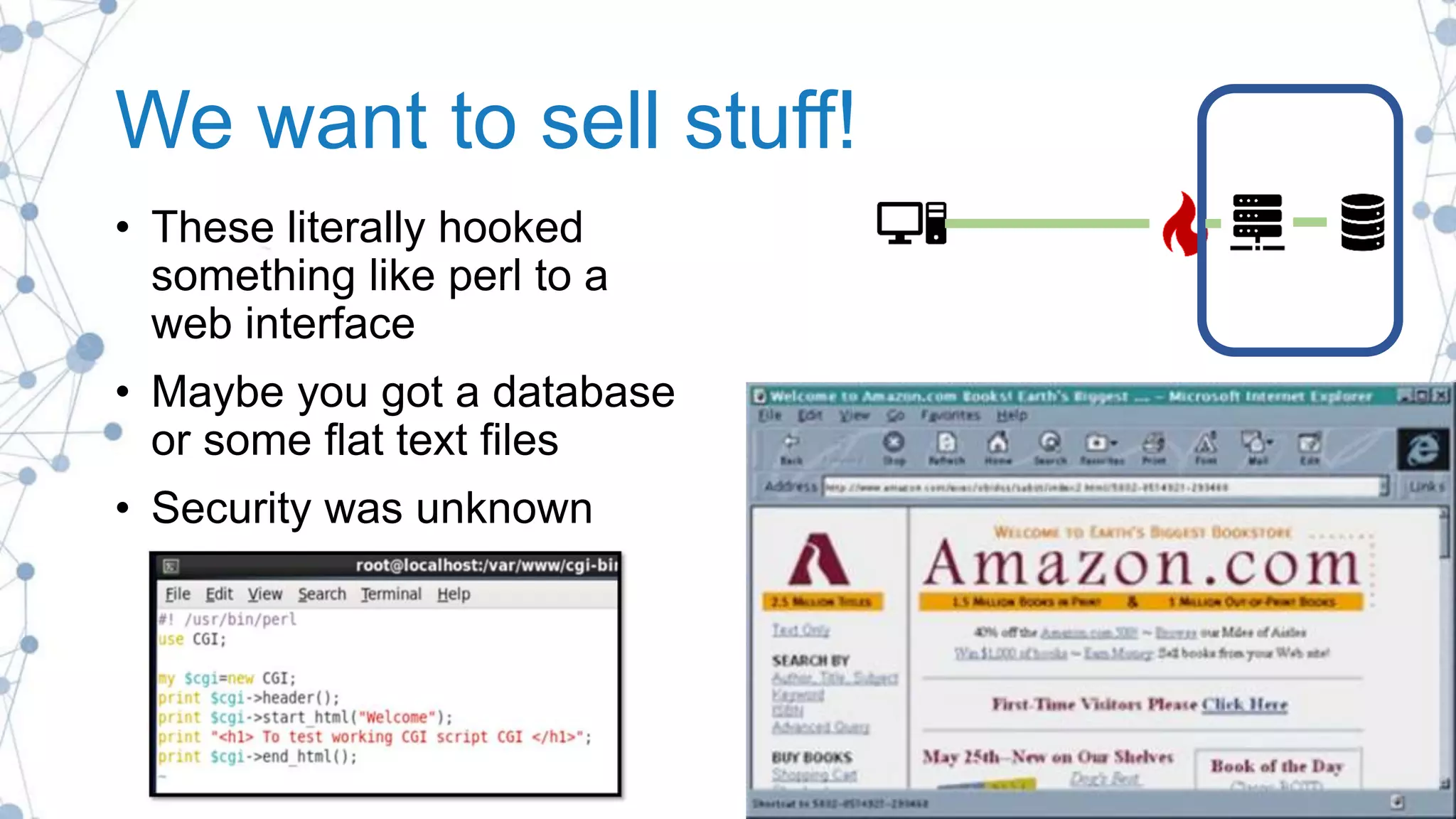
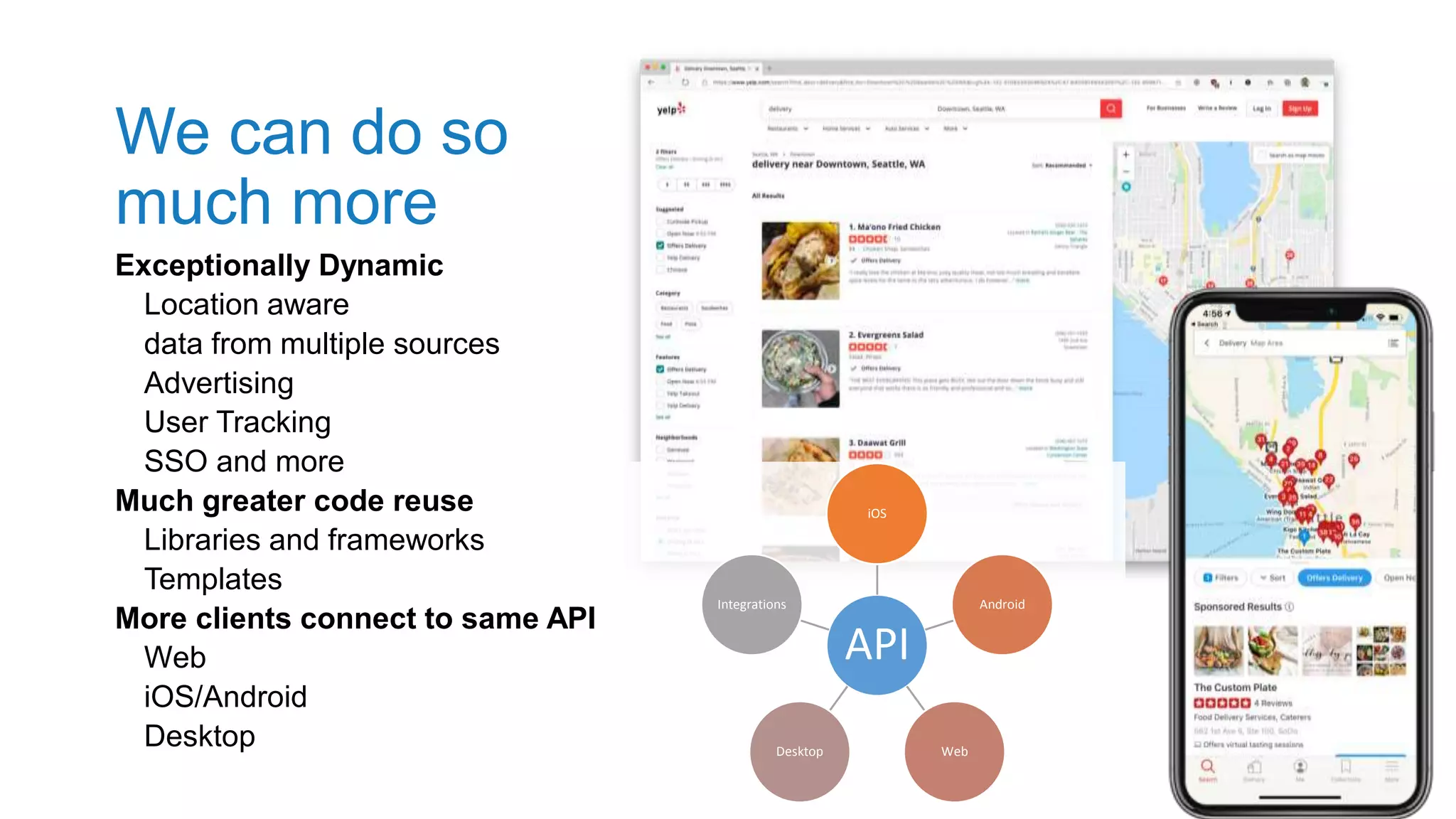
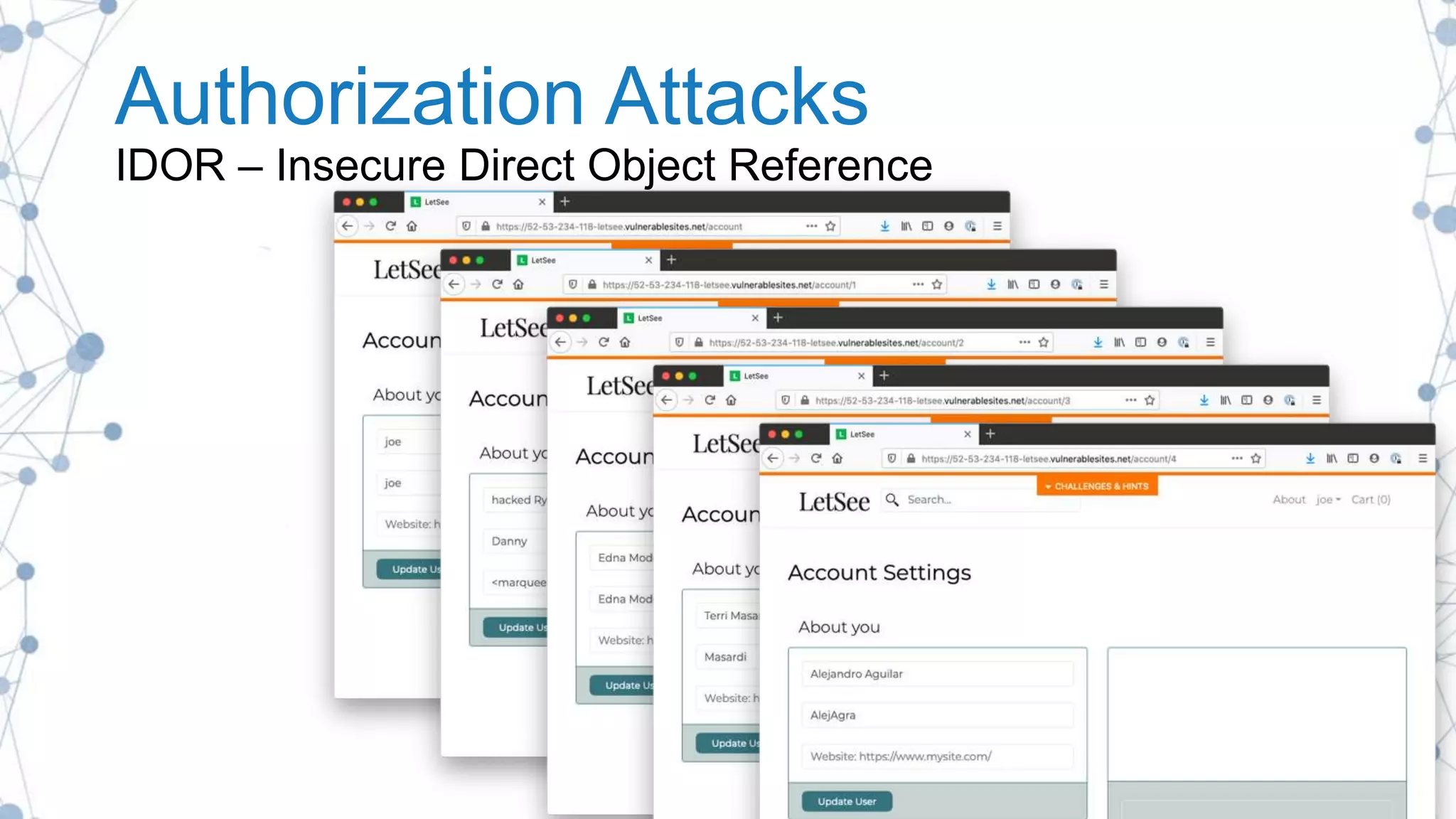
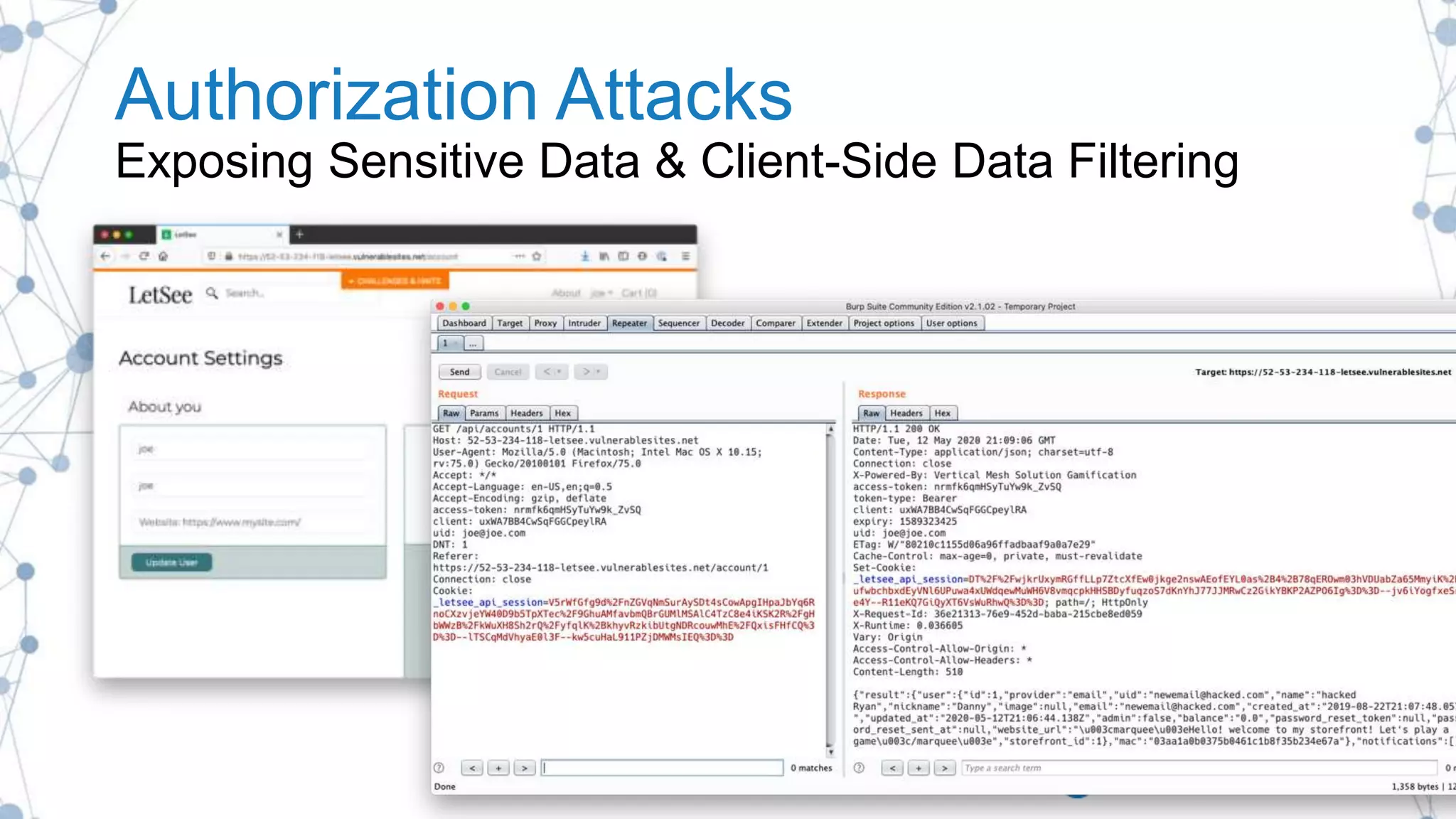
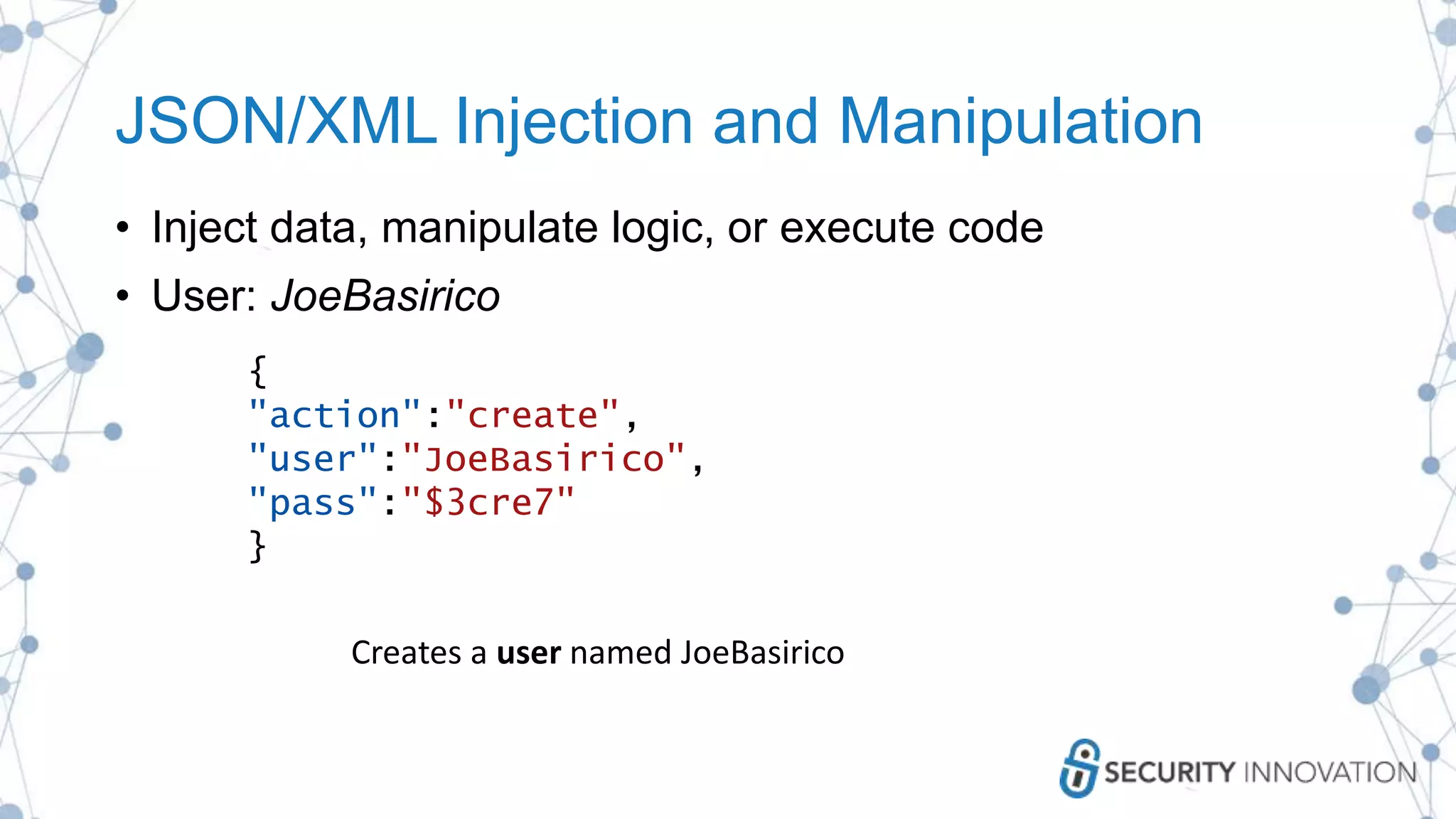
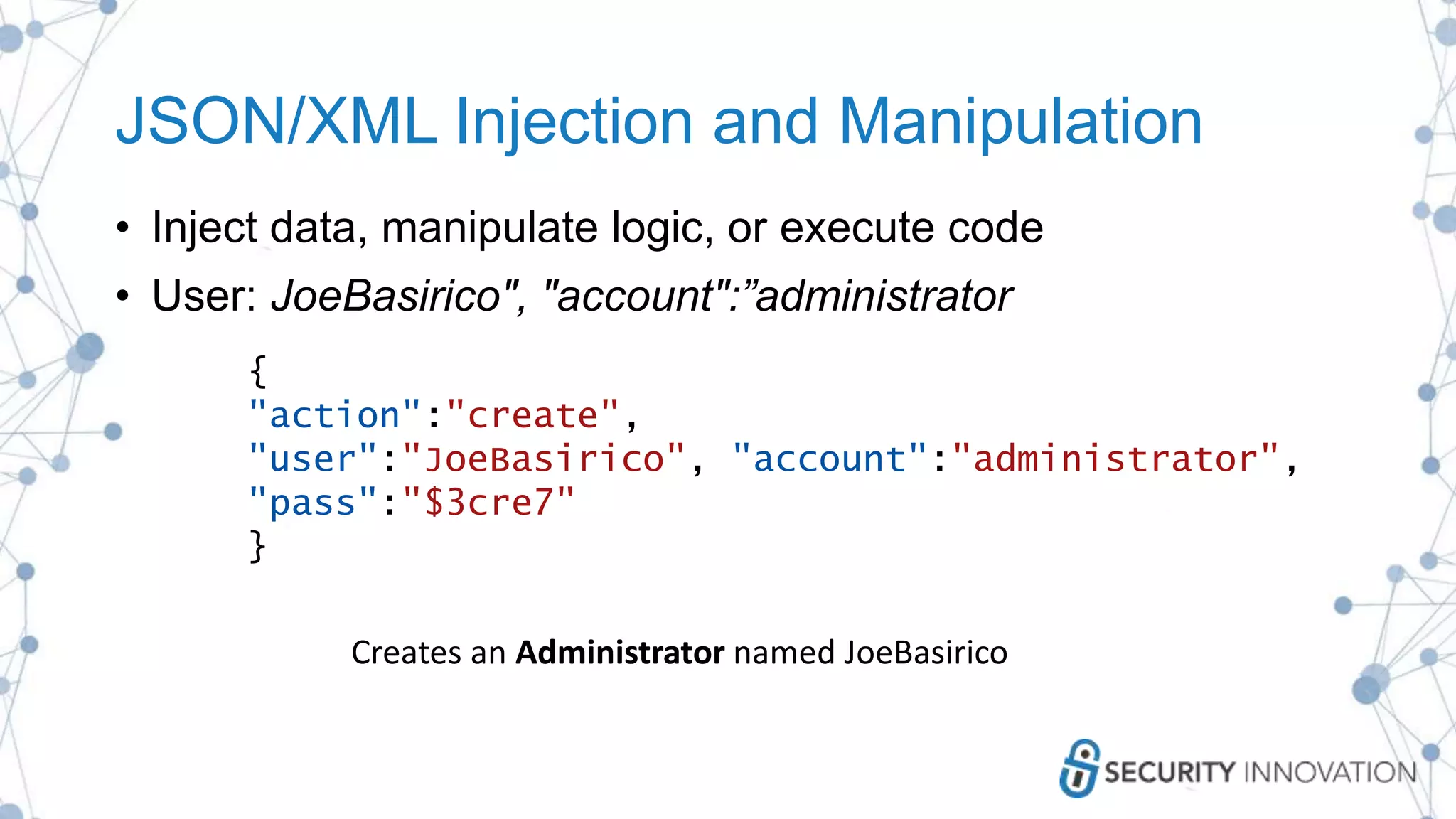
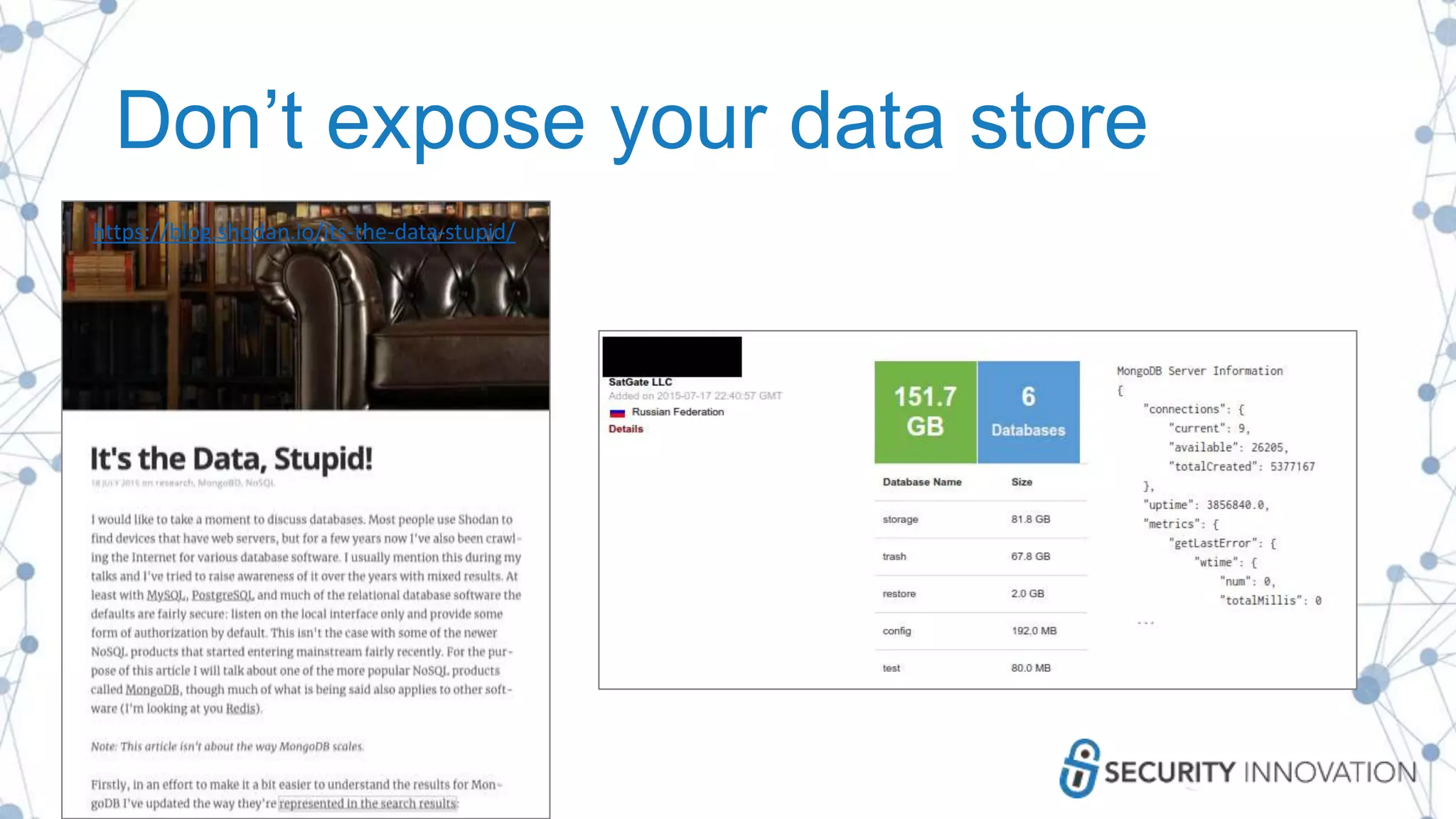
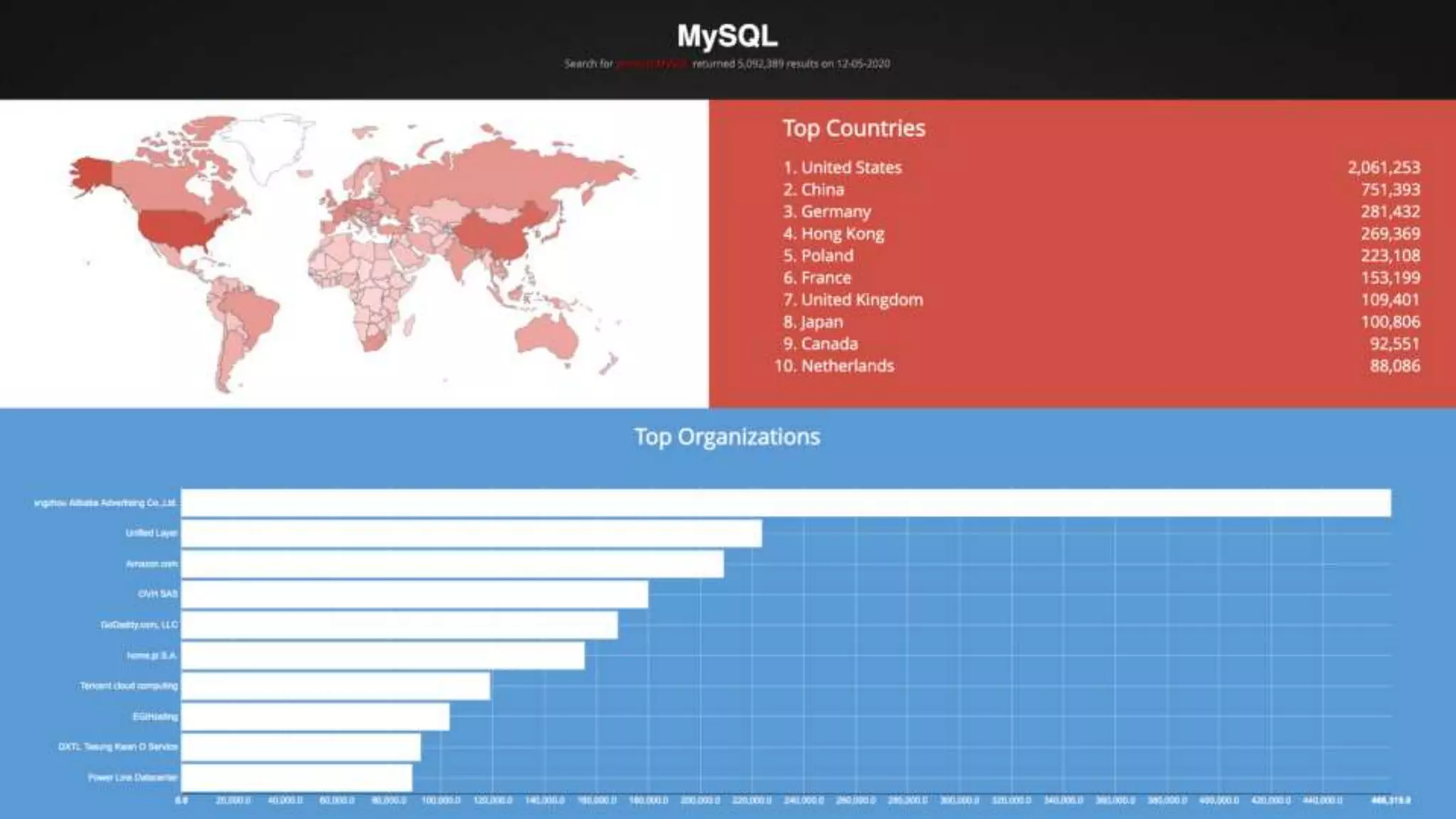
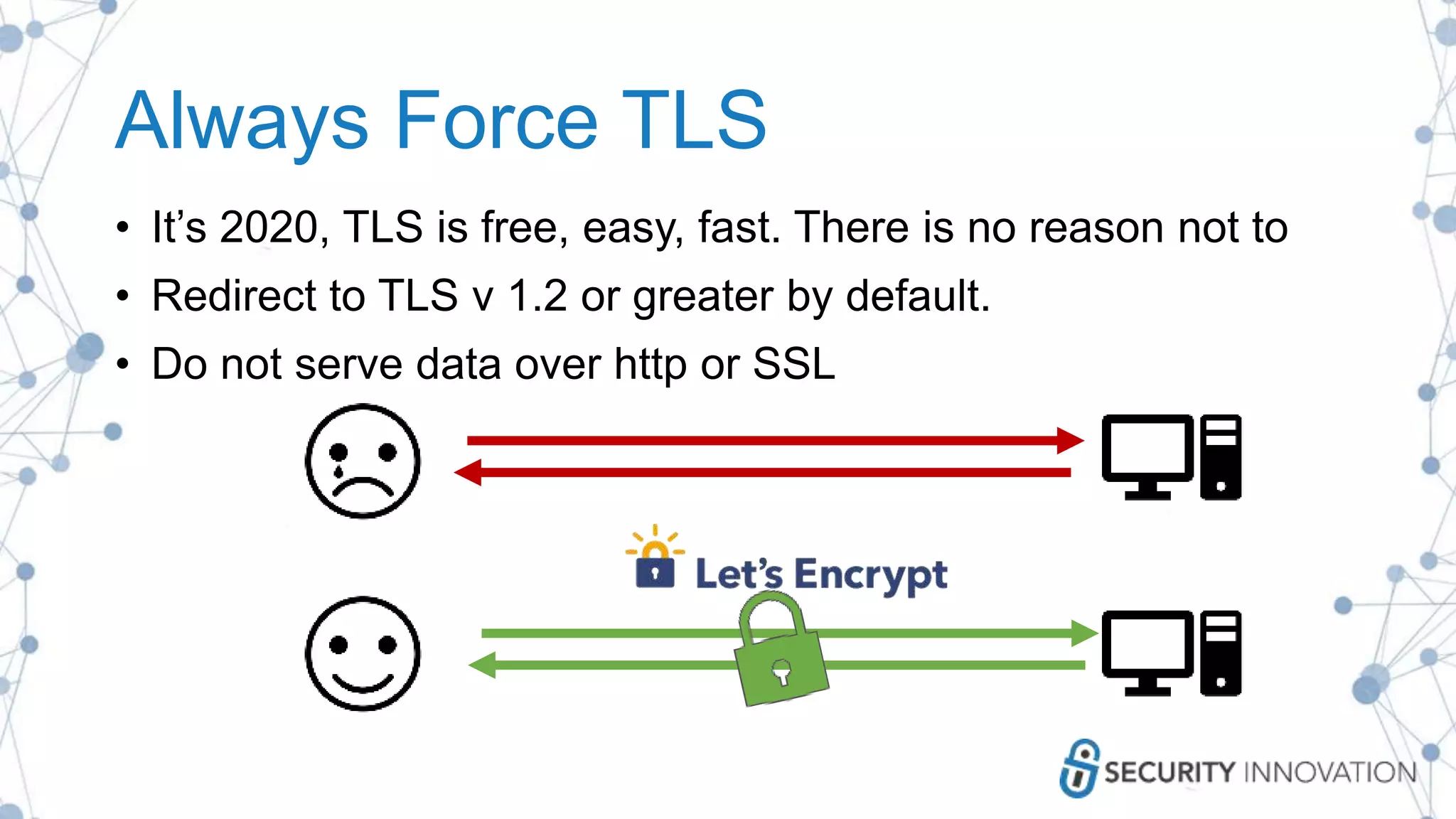
The document outlines best practices for enhancing software security and minimizing data breaches through a structured approach to privacy, data classification, and secure coding. It emphasizes the need for organizations to adopt strong goals for data collection, utilize automation, and provide developers with the necessary tools and training to prevent security vulnerabilities. The document also highlights the importance of making security an integral part of the development process rather than an afterthought.