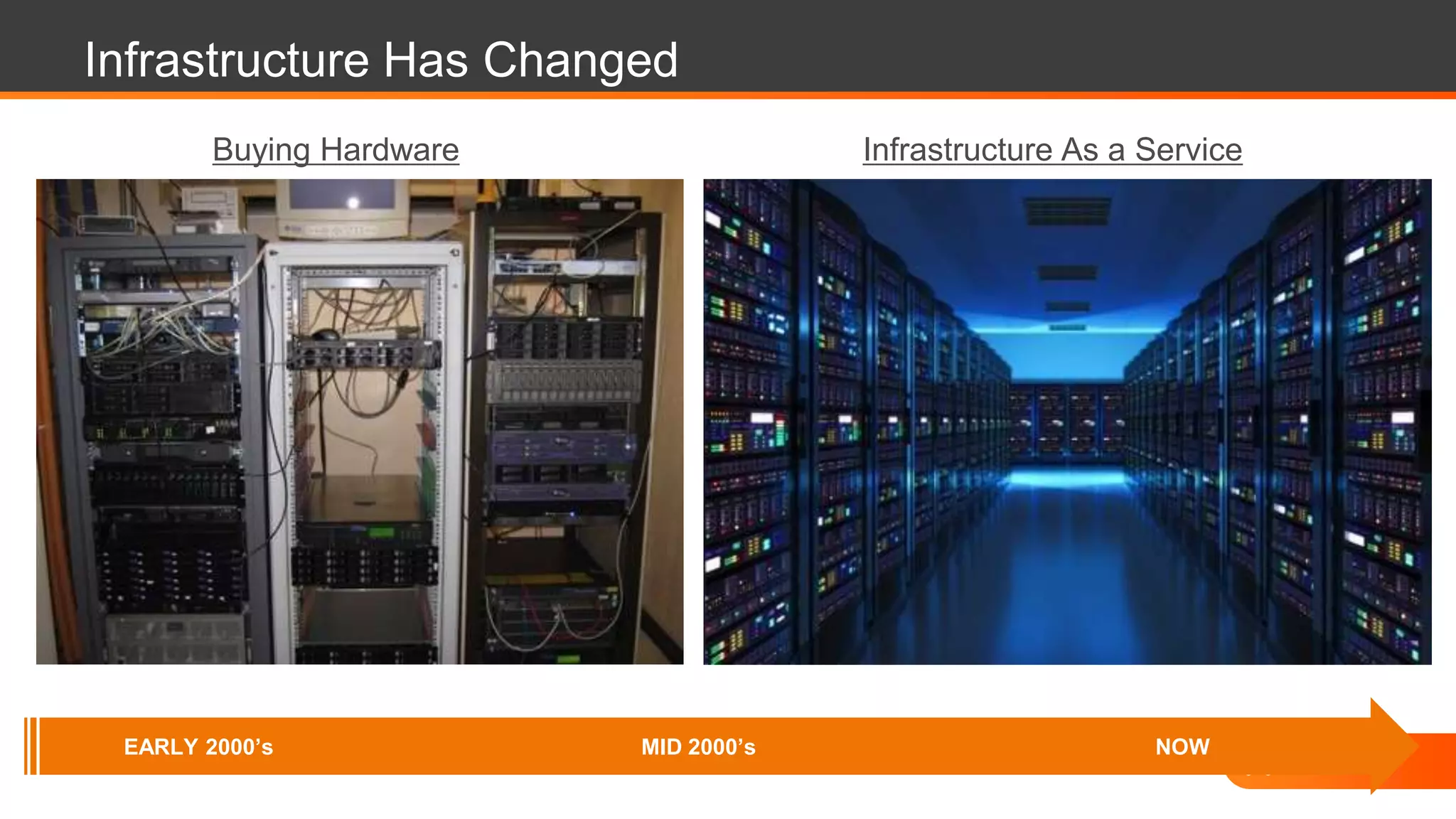
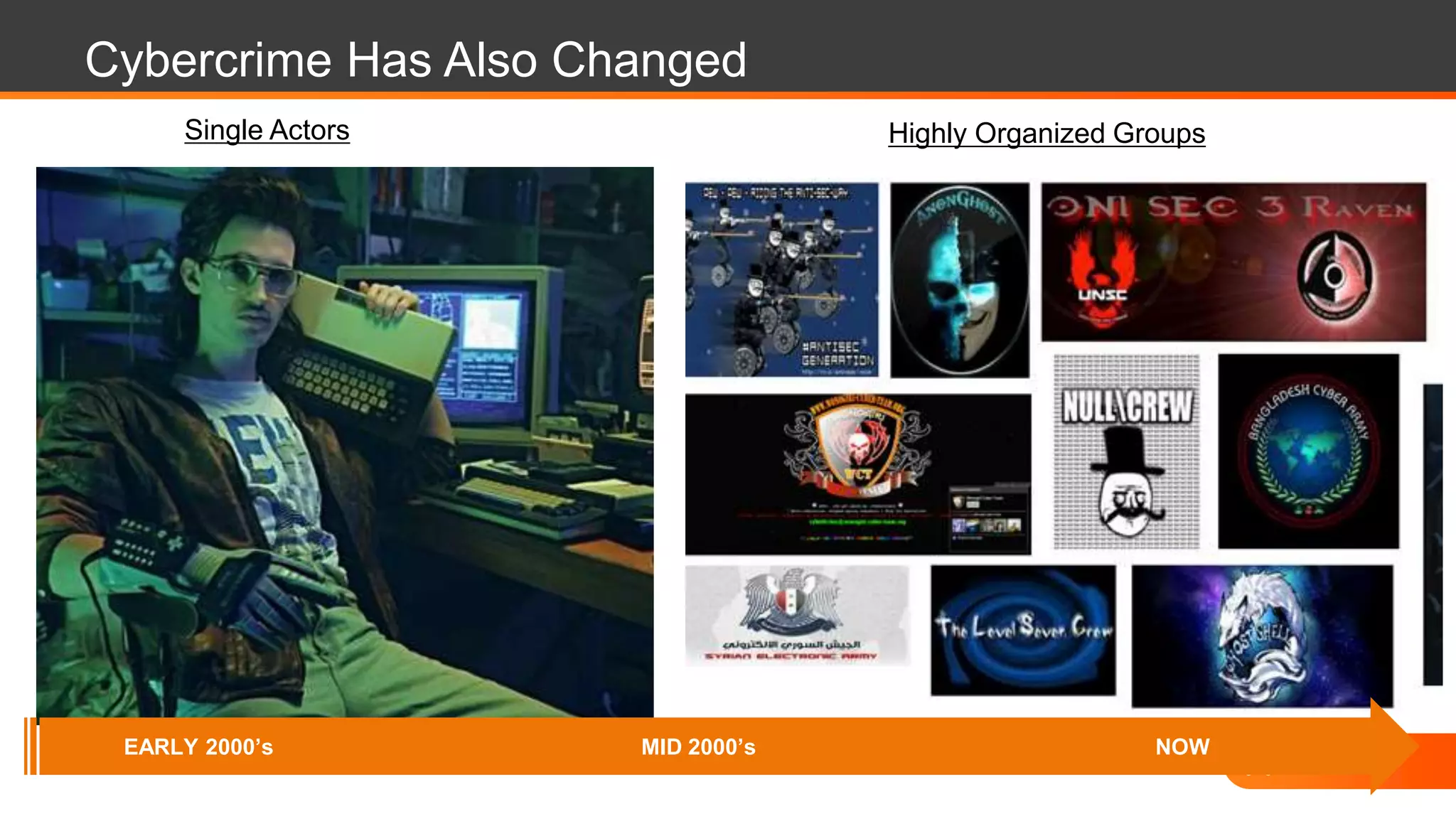
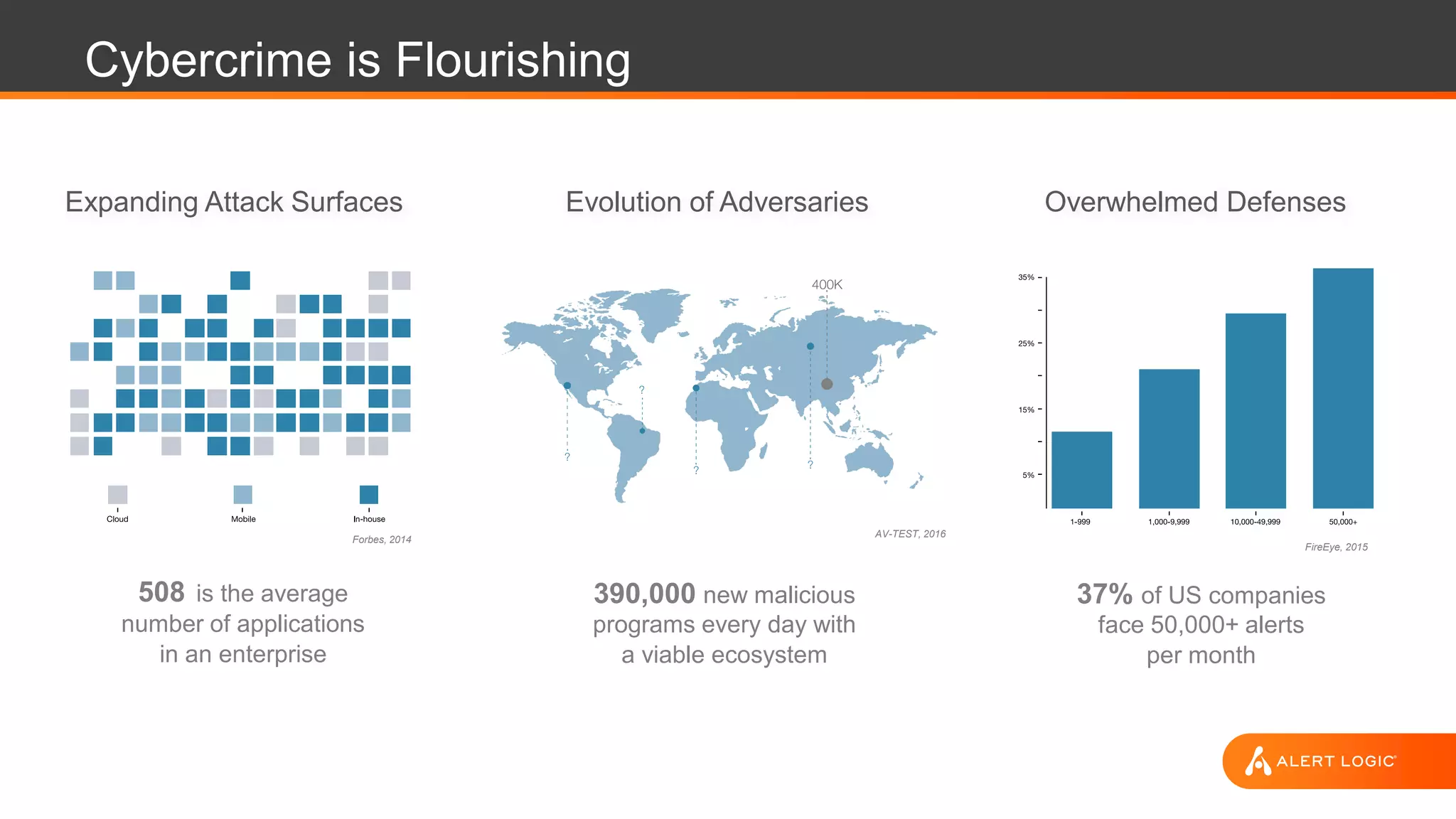
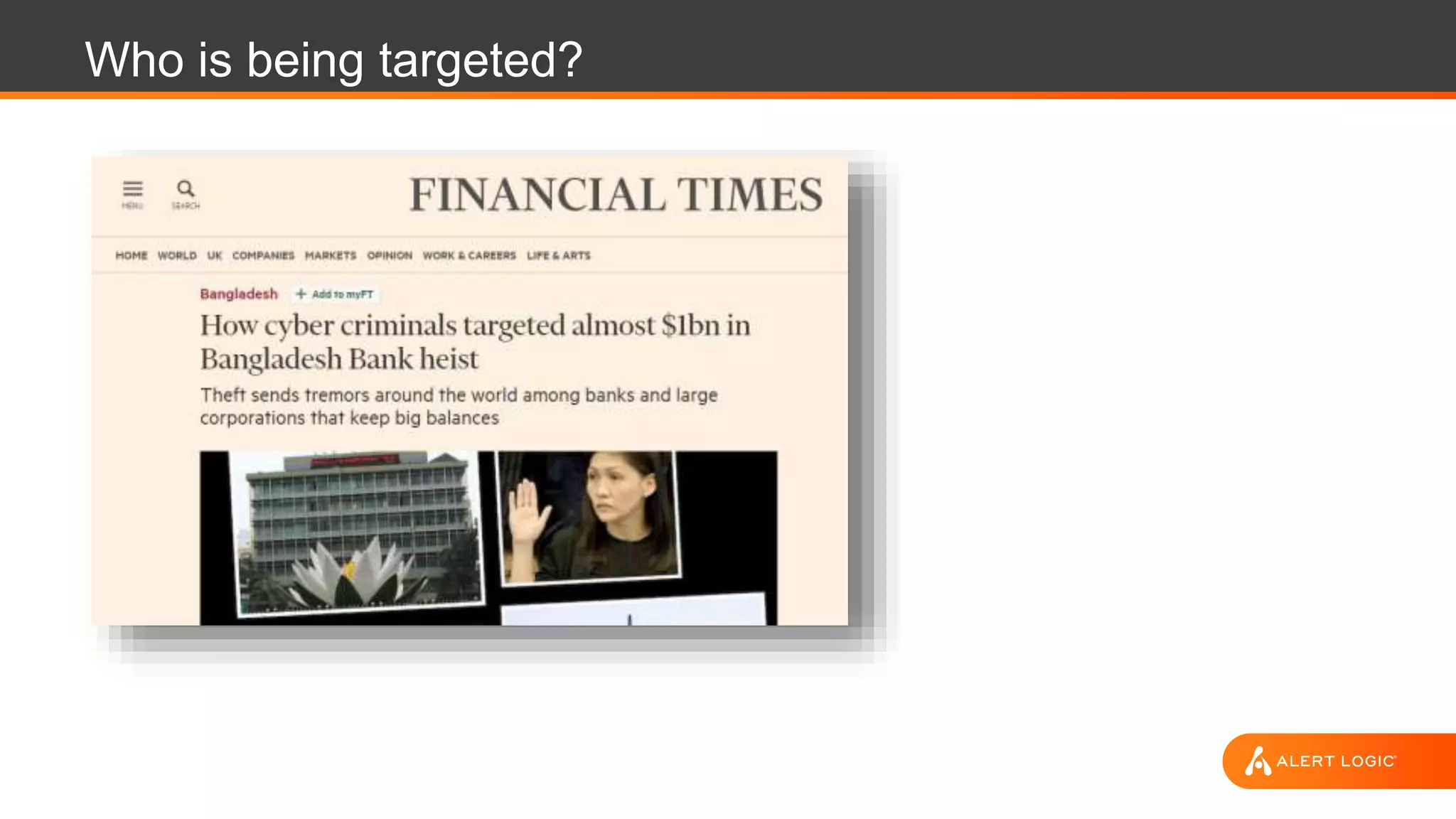
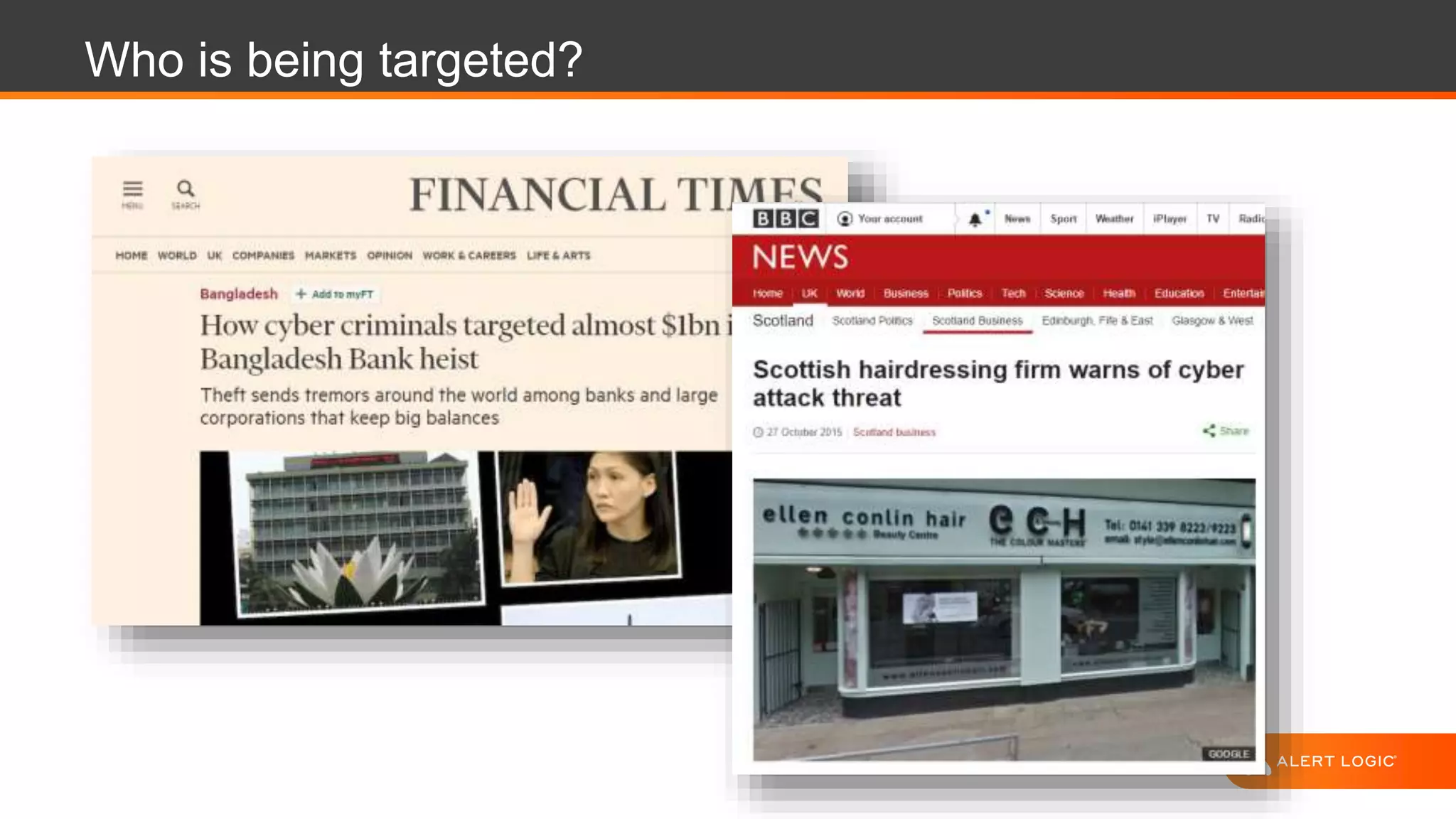
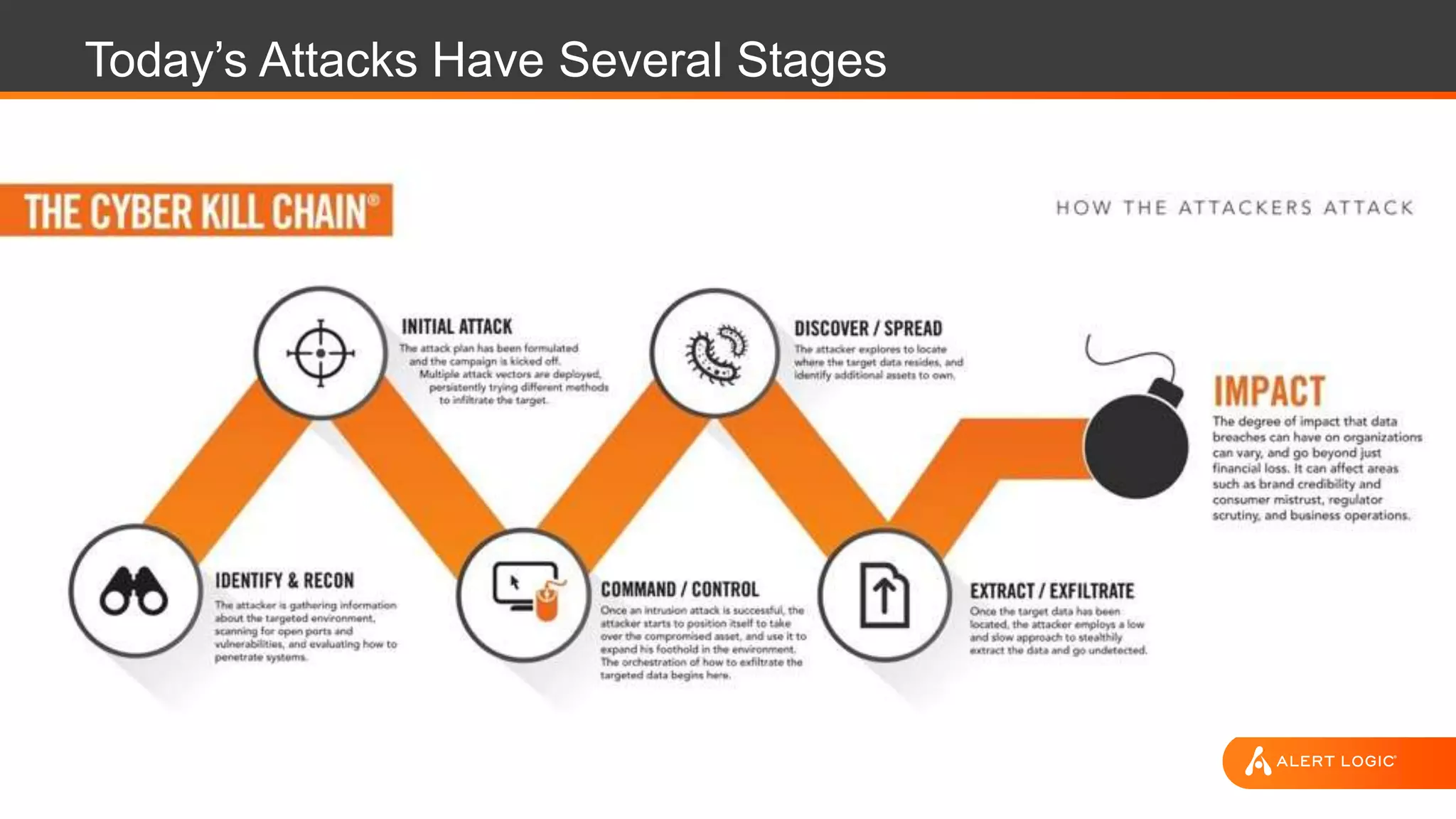
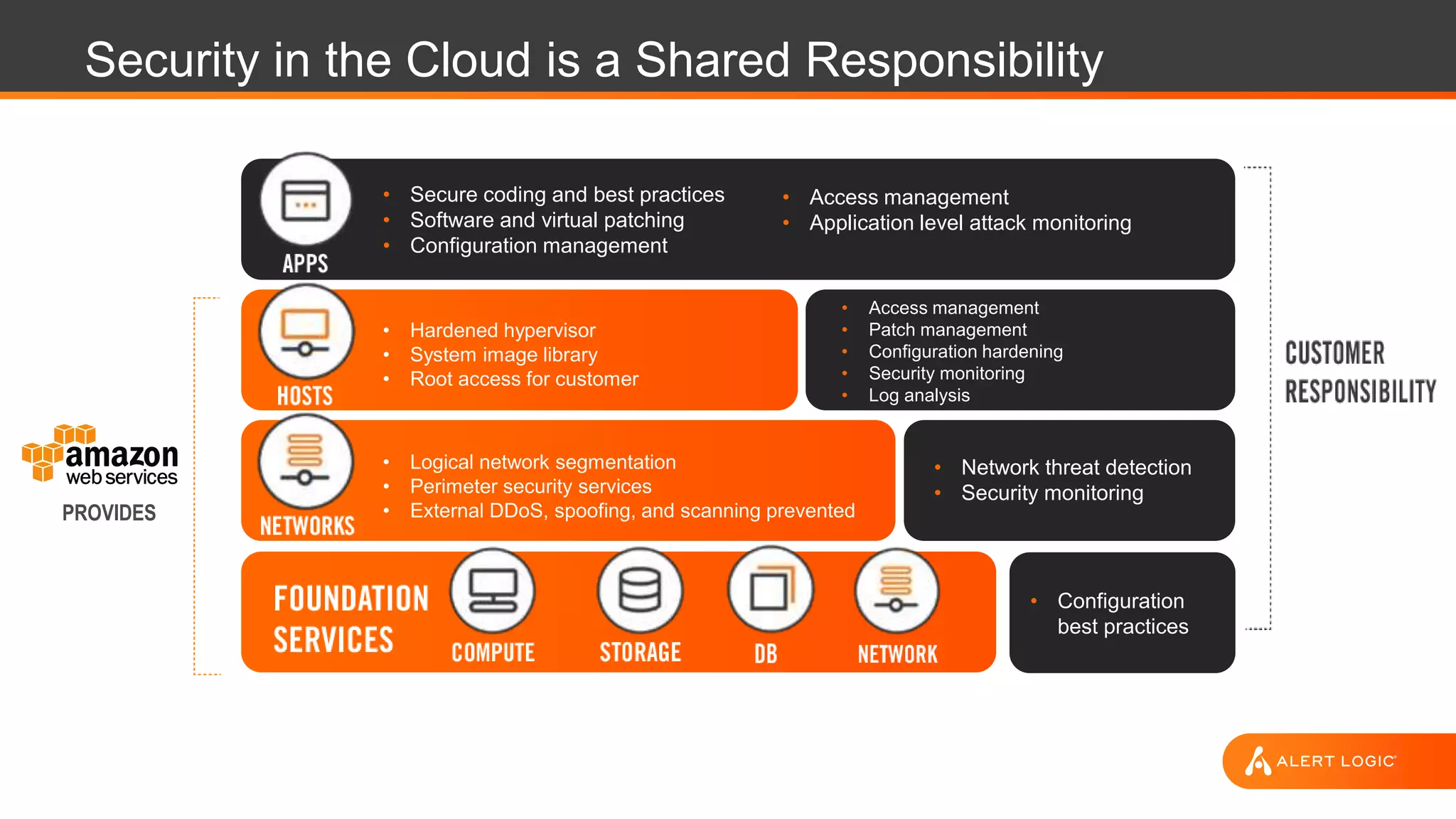
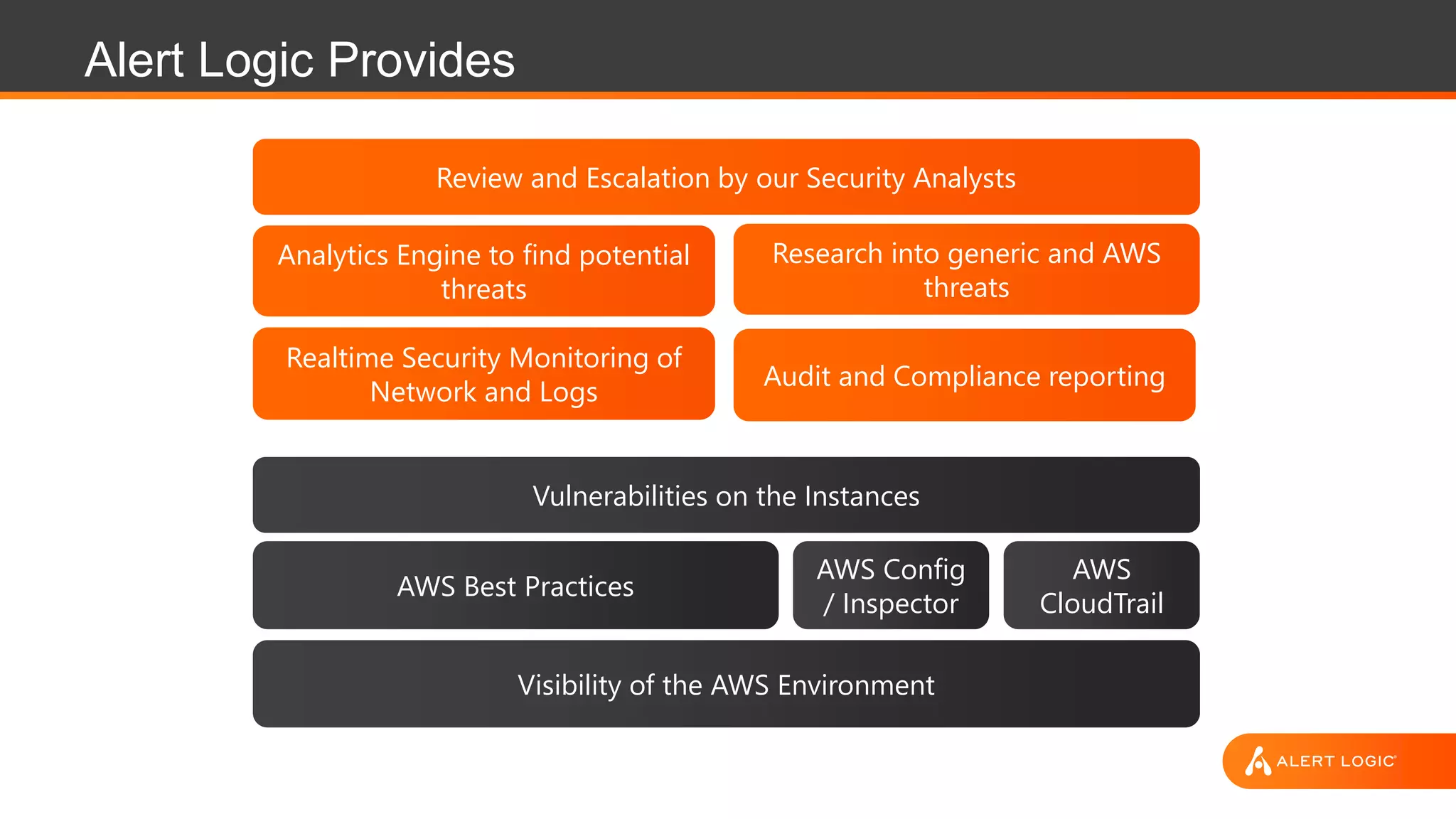
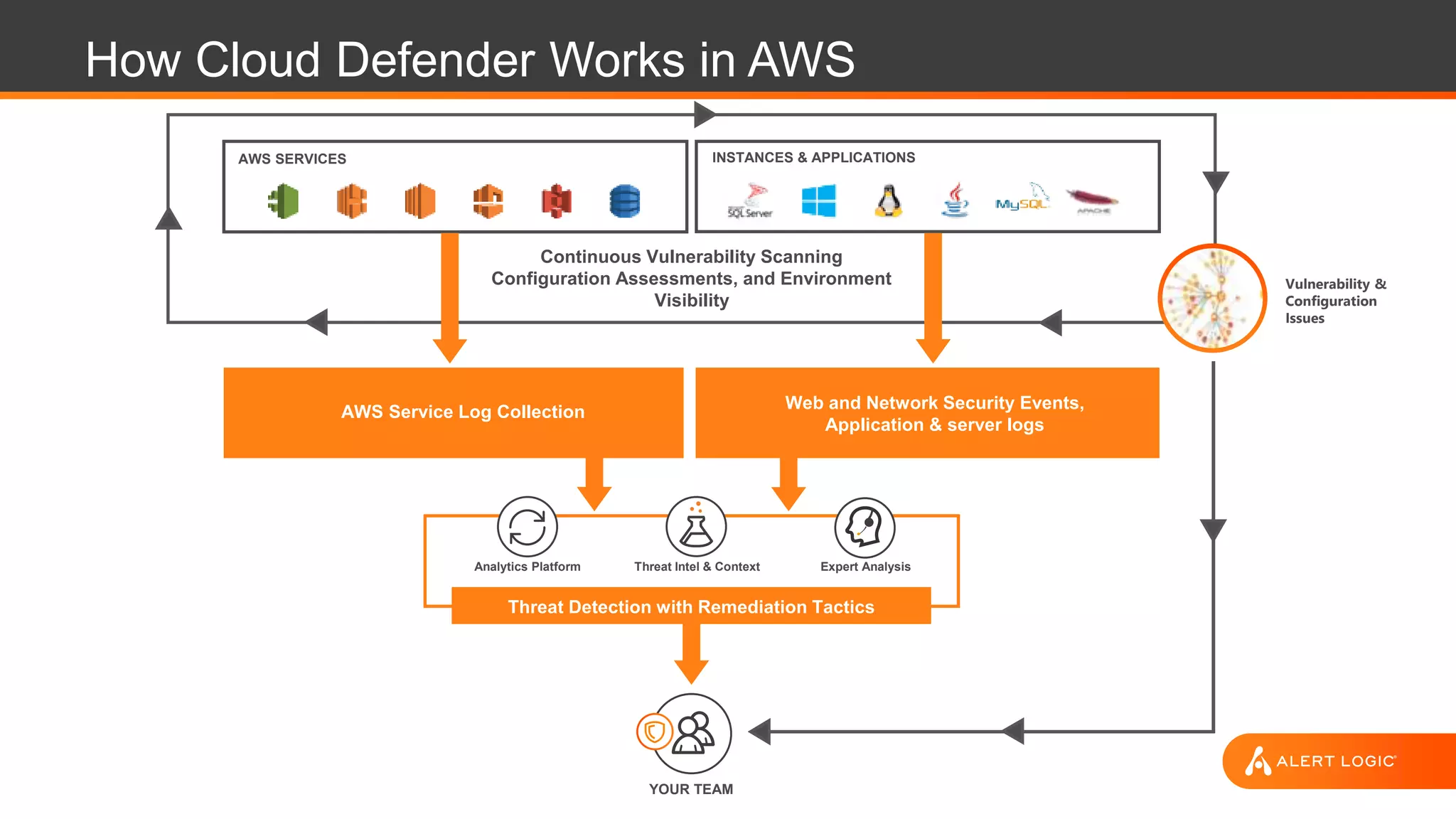
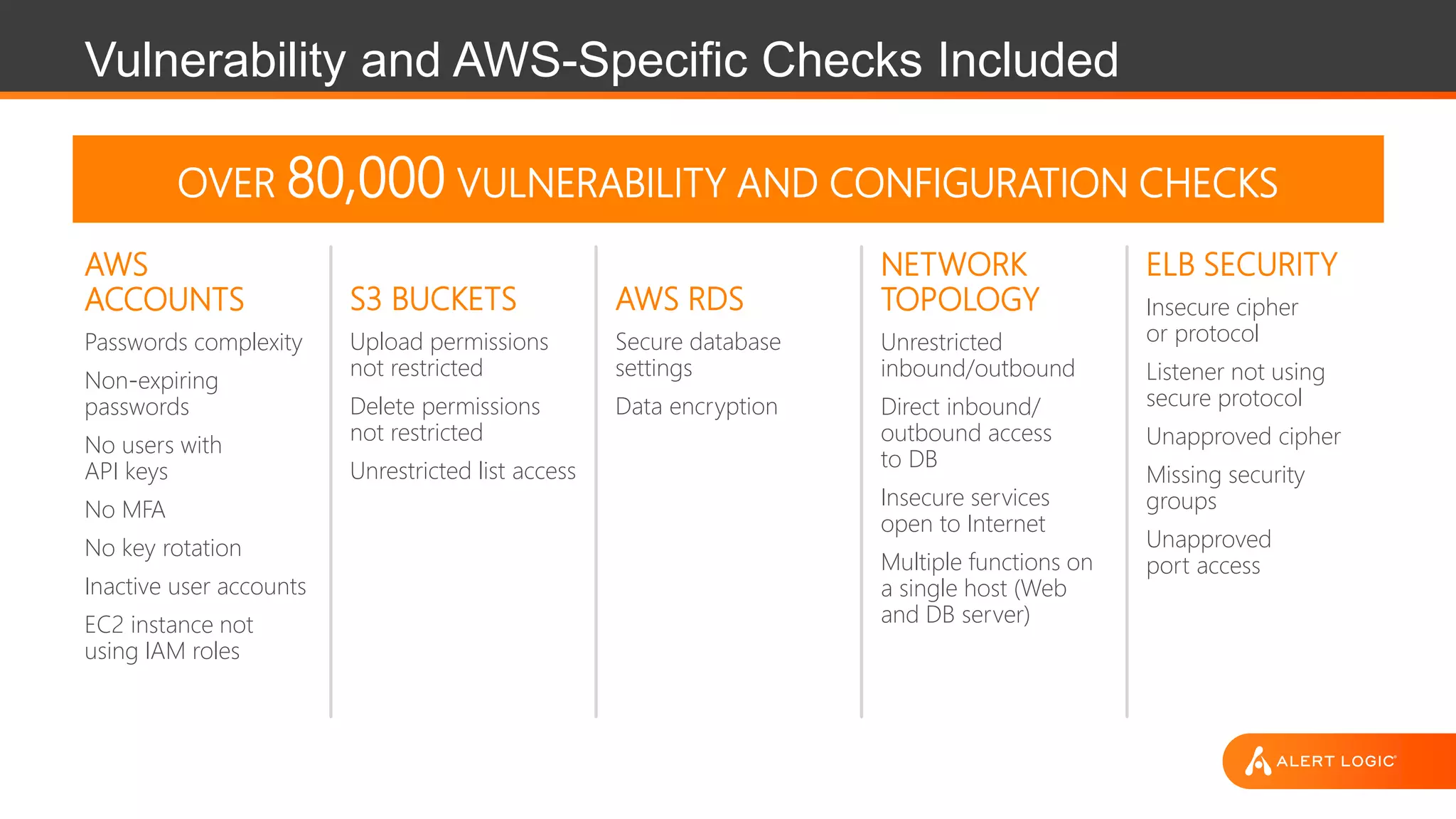
The document discusses the evolution of cybersecurity challenges in the cloud, emphasizing the shift from single actors to organized groups behind cybercrime and the increased alert volume faced by companies. It highlights the importance of shared responsibility in cloud security and the necessity of applying the same security practices as on-premises, while also detailing tools and services offered by Alert Logic for effective cloud defense. Overall, it presents a call to adapt security approaches to meet the complexities of modern enterprises leveraging cloud technology.