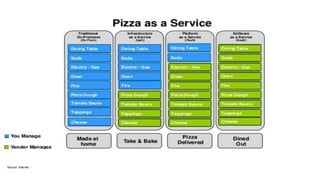
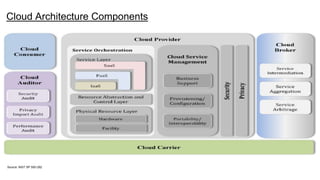
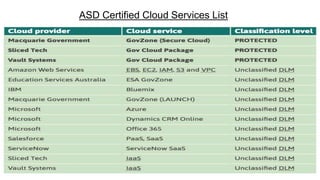
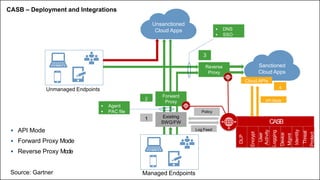
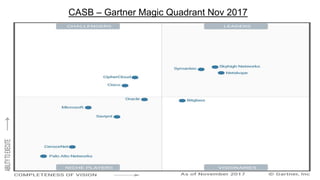
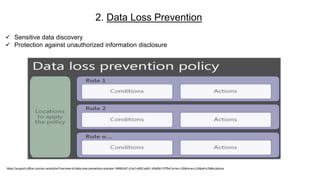
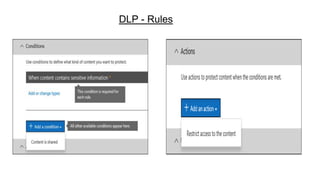
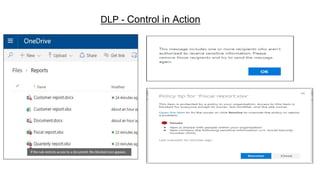
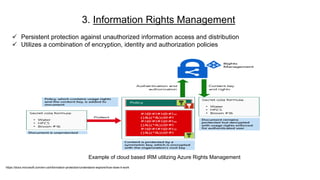
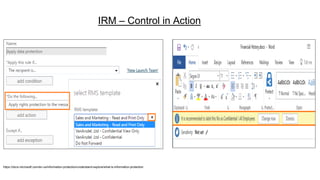
This document provides an overview of practical cloud security advice. It discusses security risks in cloud computing like unauthorized data exposure and loss of availability. It recommends technical controls like CASB for access monitoring, DLP for data protection, and IRM for persistent data protection. The document also stresses the importance of identity and access management, encryption, and secure configurations.