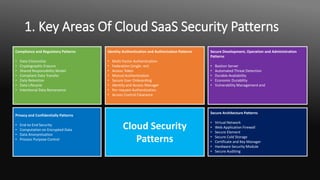
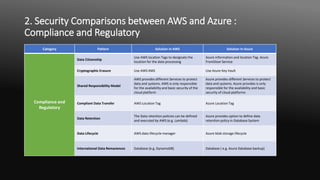
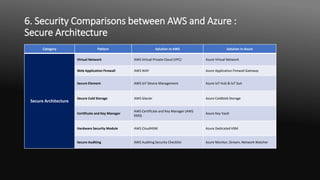
The document compares security patterns and solutions between Amazon Web Services (AWS) and Microsoft Azure for cloud computing. It discusses six key areas of comparison: 1) compliance and regulatory, 2) identity authentication and authorization, 3) secure development, operation and administration, 4) privacy and confidentiality, 5) secure architecture, and 6) provides examples of specific security solutions offered by each cloud provider for different security patterns within each area.