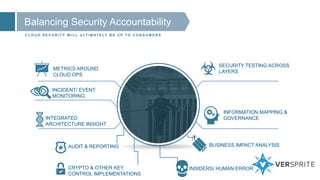
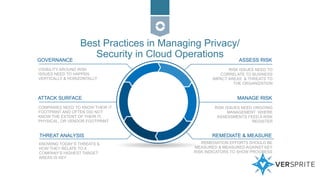
This document discusses strategies for securing cloud operations and mitigating vulnerabilities. It covers topics like holding cloud service providers (CSPs) accountable by examining their people, processes, and technologies; balancing security accountability between CSPs and customers; privacy considerations for data in the cloud; top threats to cloud security like injection flaws and poor access controls; and mitigating risk through contract negotiation with CSPs. Examples are provided around liability limitations, insurance requirements, compliance audits, security obligations, and restrictions on subcontracting for cloud services.