This paper proposes a multilayer perceptron guided encryption system for secure data exchange in wireless communication, addressing key distribution challenges and man-in-the-middle attacks. The method ensures both sender and receiver generate identical session keys through synchronized weight vectors, enabling effective encryption and decryption of plaintext. The technique demonstrates comparable performance to existing classical methods under various test conditions.
![International Journal of Mobile Network Communications & Telematics ( IJMNCT) Vol. 4, No.4,August 2014
SECURED TRANSMISSION THROUGH MULTI LAYER
PERCEPTRON IN WIRELESS COMMUNICATION
(STMLP)
Arindam Sarkar1 and J. K. Mandal2
1Department of Computer Science & Engineering, University of Kalyani, W.B, India
2Department of Computer Science & Engineering, University of Kalyani, W.B, India
ABSTRACT
In this paper, a multilayer perceptron guided encryption/decryption (STMLP) in wireless communication
has been proposed for exchange of data/information. Multilayer perceptron transmitting systems at both
ends generate an identical output bit and the network are trained based on the output which is used to
synchronize the network at both ends and thus forms a secret-key at end of synchronizations of the
networks. Weights or hidden units of the hidden layer help to form a secret session key. The plain text is
encrypted through chaining , cascaded xoring of multilayer perceptron generated session key. If size of the
final block of plain text is less than the size of the key then this block is kept unaltered. Receiver will use
identical multilayer perceptron generated session key for performing deciphering process for getting the
plain text. Parametric tests have been done and results are compared in terms of Chi-Square test, response
time in transmission with some existing classical techniques, which shows comparable results for the
proposed technique. Variation numbers of input vectors and hidden layers will increase the confusion
/diffusion of the schemeand hence increase the security. As a result variable energy based techniques may
be achieved which may be applicable devices/interface of the heterogeneous sizes of the network/device.
KEYWORDS
Multilayer Perceptron, Session Key, Wireless Communication.
1. INTRODUCTION
In recent times wide ranges of techniques are developed to protect data and information from
eavesdroppers [1, 2, 3, 4, 5, 6, 7, 8, 9]. Algorithms have their virtue and shortcomings. For
Example in DES, AES algorithms [1] the cipher block length is nonflexible. In NSKTE [4],
NWSKE [5], AGKNE [6], ANNRPMS [7] and ANNRBLC [8] technique uses two neural
network one for sender and another for receiver having one hidden layer for producing
synchronized weight vector for key generation. Attacker can get an idea about sender and
receiver’s neural machine as session architecture of neural machine is static. In NNSKECC
algorithm [9] any intermediate blocks throughout its cycle taken as the encrypted block and this
number of iterations acts as secret key. Here, if n number of iterations are needed for cycle
formation and if intermediate block is chosen as an encrypted block after n/2th iteration then
exactly same number of iterations i.e. n/2 are needed for decode the block which makes easier
the attackers life. This paper proposed a multilayer perceptron guided encryption technique in
wireless communication to overcome the problem.
The organization of this paper is as follows. Section 2 of the paper deals with the problem domain
and methodology. Proposed Multilayer Perceptron based key generation has been discussed in
DOI : 10.5121/ijmnct.2014.4401 1](https://image.slidesharecdn.com/securedtransmissionthroughmultilayerperceptroninwirelesscommunicationstmlp-140910050619-phpapp01/75/Secured-transmission-through-multi-layer-perceptron-in-wireless-communication-stmlp-1-2048.jpg)
![International Journal of Mobile Network Communications & Telematics ( IJMNCT) Vol. 4, No.4,August 2014
section 3. Triangularization encryption technique is given in section 4. Triangularization
decryption has been presented in section 5. Section 6 presents energy computation technique.
Complexity analysis of the technique is given in section 7. Experimental results are described in
section 8. Analysis of the results presented in section 9. Analysis regarding various aspects of the
technique has been presented in section 10. Conclusions and future scope are drawn in section 11
and that of references at end.
2
2. PROBLEM DOMAIN AND METHODOLOGY
In security based communication the main problem is distribution of key between sender and
receiver. As, during exchange of key over public channel intruders can intercept the key as a
middleman. The problem has been addressed and a technique has been proposed addressing the
issue. These are presented in section 2.1 and 2.2 respectively.
2.1. Man-In-The-Middle Attack
Intruders intercepting in the middle between sender and receiver try to capture all the information
transmitting from both. Diffie-Hellman key exchange technique [1] suffers from this type of
problems. Intruders can act as sender/ receiver simultaneously and try to steal secret session key
at the time of exchanging key via public channel.
2.2. Methodology
Well known problem of man in the middle attack has been addressed in STMLP where secret
session key is not exchanged over public insecure channel. At end of synchronization both
parties’ generates identical weight vectors and activated hidden layer outputs for both the parties
become identical. This identical output of hidden layer for both parties are used as one time secret
session key for secured data exchange.
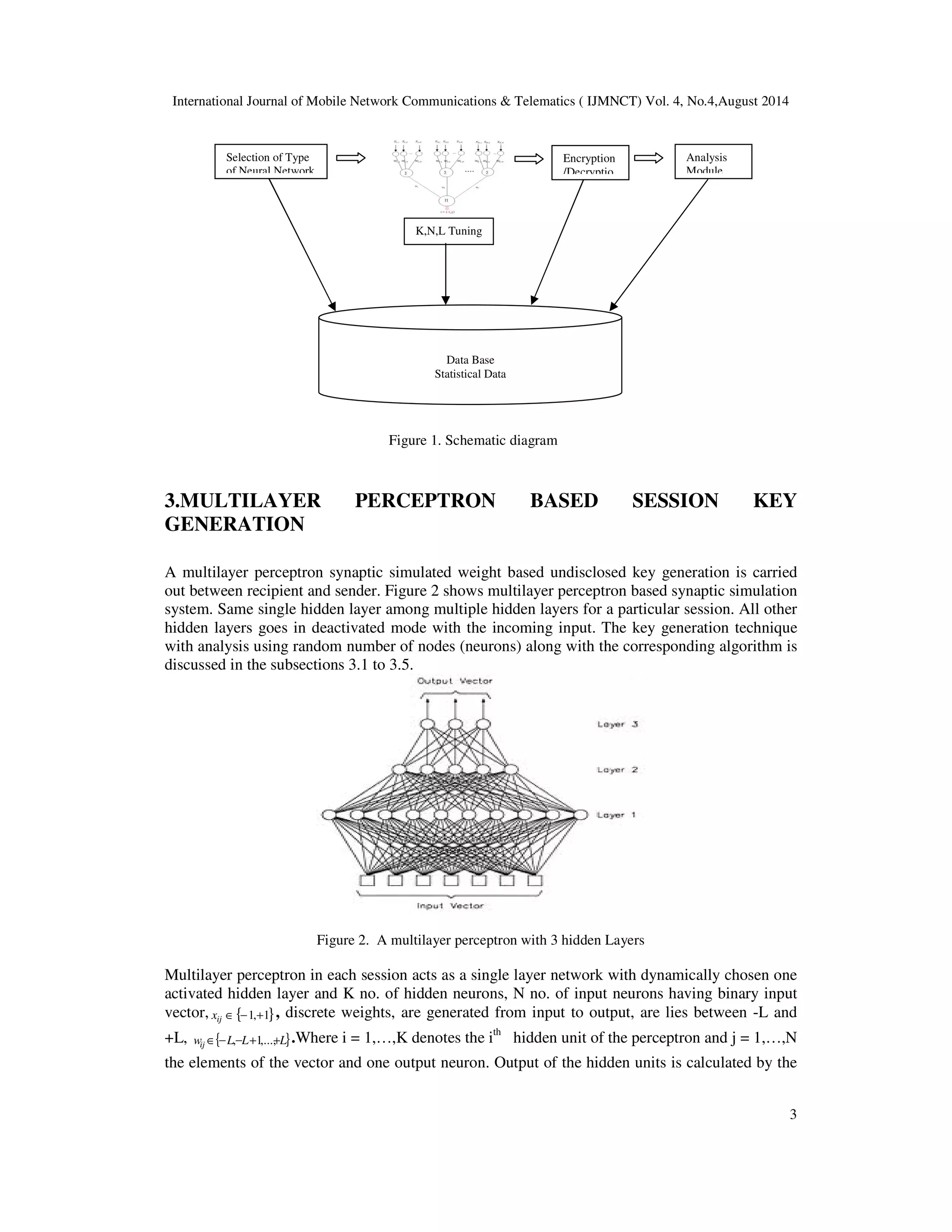
The basic idea here is to design such a program with effective GUI which helps people to
understand the underlying calculations. In this case this would be the Tree Parity Machine and the
various encryption and decryption techniques. First we need to figure out what are main functions
of our system. Since we are going to work on various Neural network structures we need a menu
to choose from. Again after that, two different Neural network need mutual synchronization and
associated statistical data like type of network and total time required to synchronize mutually.
Then at the end we need a menu to choose various encryption and decryption techniques and
statistical modules to compute probable power consumption by the network. So we need various
menus / forms to cater our need of various functions within their scope. So the schematic view
looks like the figure 1.](https://image.slidesharecdn.com/securedtransmissionthroughmultilayerperceptroninwirelesscommunicationstmlp-140910050619-phpapp01/75/Secured-transmission-through-multi-layer-perceptron-in-wireless-communication-stmlp-2-2048.jpg)

![International Journal of Mobile Network Communications Telematics ( IJMNCT) Vol. 4, No.4,August 2014
5
i j i w g w f x i j , , , , , = + s t t +
Hebbian learning
anti-Hebbian learning
Random walk learning
3.2 Multilayer Perceptron Learning
At the beginning of the synchronization process multilayer perceptron of A and B start with
uncorrelated weight vectors A B
i w / . For each time step K, public input vectors are generated
randomly and the corresponding output bits t
A/Bare calculated. Afterwards A and B communicate
their output bits to each other. If they disagree, t
A
t
B, the weights are not changed. Otherwise
learning rules suitable for synchronization is applied. In the case of the Hebbian learning rule [10]
both neural networks learn from each other.
( ( ) ( )) A B
i j i j i wi j g w x = + tQst Qt t +
, , , (8)
The learning rules used for synchronizing multilayer perceptron share a common structure. That
is why they can be described by a single (eq. 4)
( ( A B
) ) i j
(9)
with a function ( A B )
i f s ,t ,t , which can take the values -1, 0, or +1. In the case of bidirectional
interaction it is given by
s
( ) ( ) ( )
, , =Q Q −
s
1
s t t st t t A B A A B
i f
(10)
The common part ( A ) ( A B ) Qst Qt t of ( A B )
i f s ,t ,t controls, when the weight vector of a hidden
unit is adjusted. Because it is responsible for the occurrence of attractive and repulsive steps [6].
3.3 Weight Distribution within Multilayer Perceptron
In case of the Hebbian rule (eq. 8), A's and B's multilayer perceptron learn their own output.
Therefore the direction in which the weight i j w , moves is determined by the product i i j x , s . As
the output i s is a function of all input values, i j x , and i s are correlated random variables. Thus
the probabilities to observe i i j x , s = +1 or i i j x , s = -1 are not equal, but depend on the value of the
corresponding weight i j w , [11, 13, 14, 15, 16].
1
w
( )
P s x erf (11)](https://image.slidesharecdn.com/securedtransmissionthroughmultilayerperceptroninwirelesscommunicationstmlp-140910050619-phpapp01/75/Secured-transmission-through-multi-layer-perceptron-in-wireless-communication-stmlp-5-2048.jpg)

![International Journal of Mobile Network Communications Telematics ( IJMNCT) Vol. 4, No.4,August 2014
distribution of the weights for t ® ¥ is calculated for the transition probabilities. This leads to
[11].
6
( )
−
( )
Õ=](https://image.slidesharecdn.com/securedtransmissionthroughmultilayerperceptroninwirelesscommunicationstmlp-140910050619-phpapp01/75/Secured-transmission-through-multi-layer-perceptron-in-wireless-communication-stmlp-9-2048.jpg)