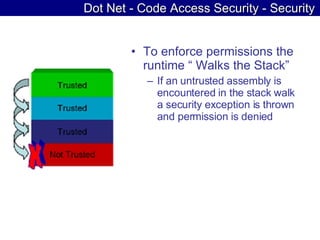
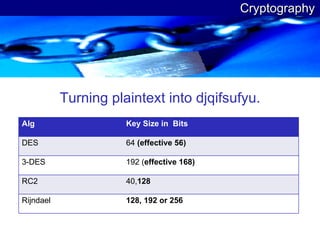
The document discusses various threats to .NET web applications and guidelines for securing .NET web applications. It covers topics like input validation, authentication, authorization, code access security, session security, auditing, and cryptography. Recommendations are given around validating all user input, using SSL, enforcing strong passwords, limiting privileges, and encrypting sensitive data.