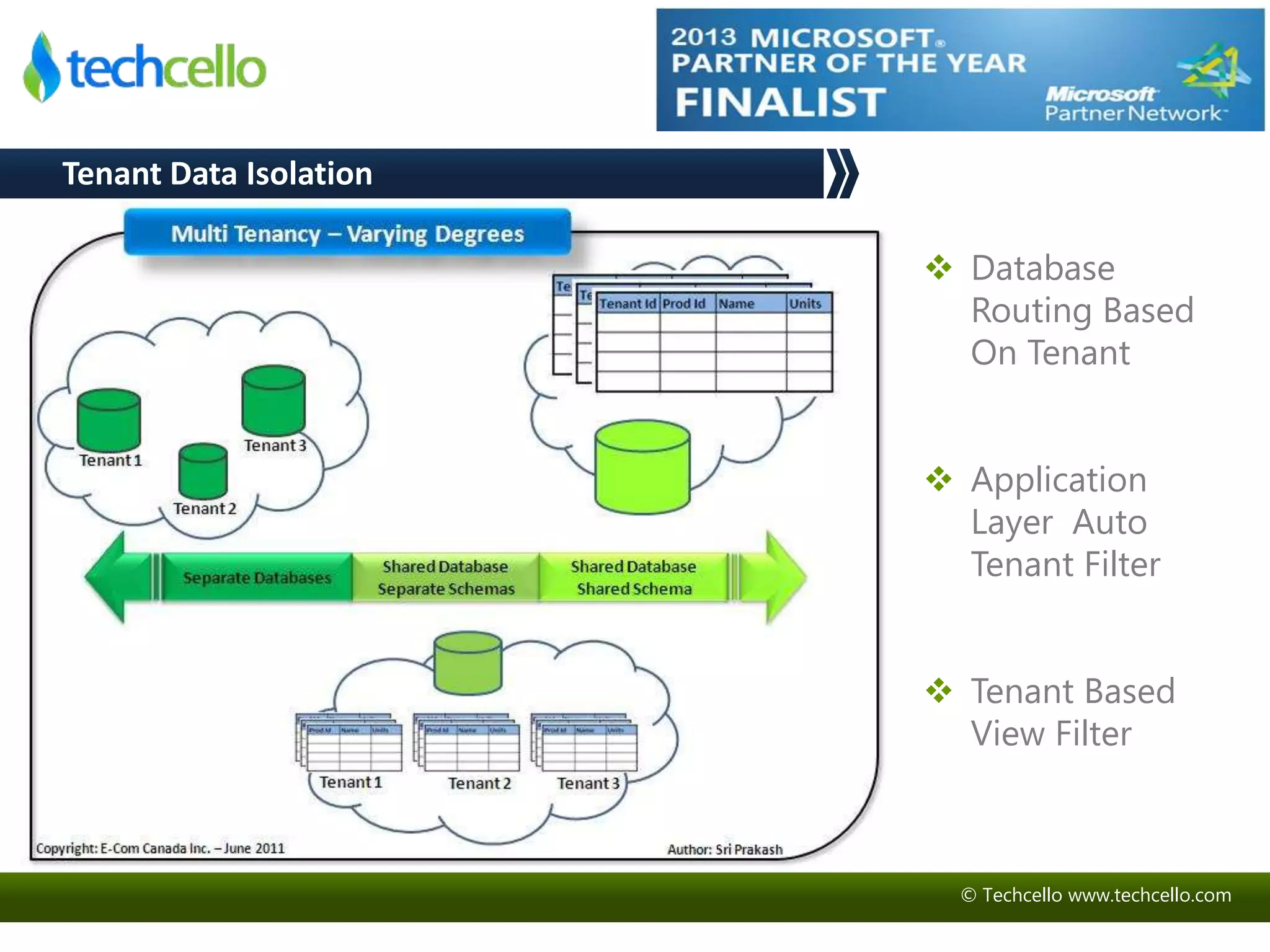
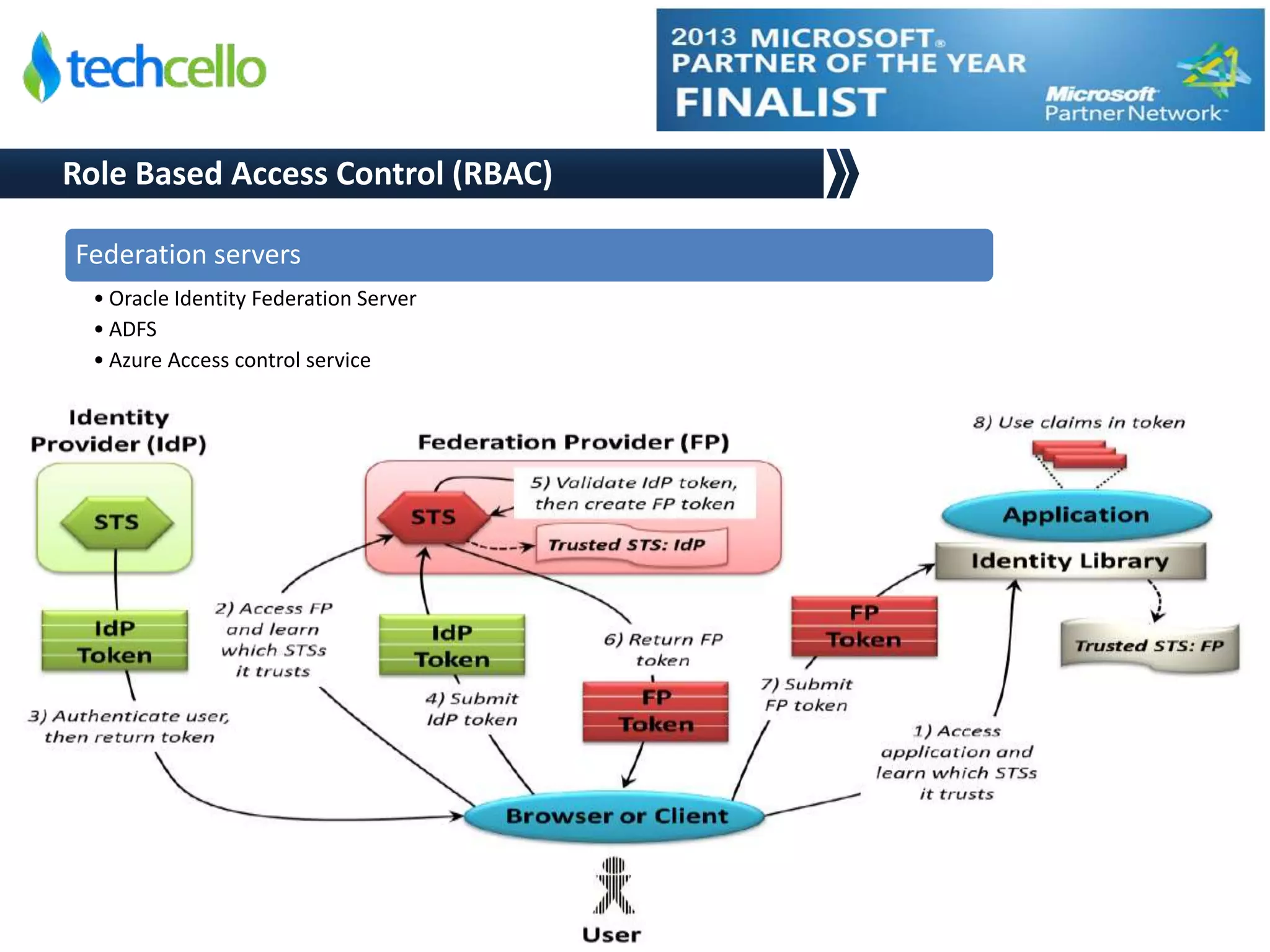
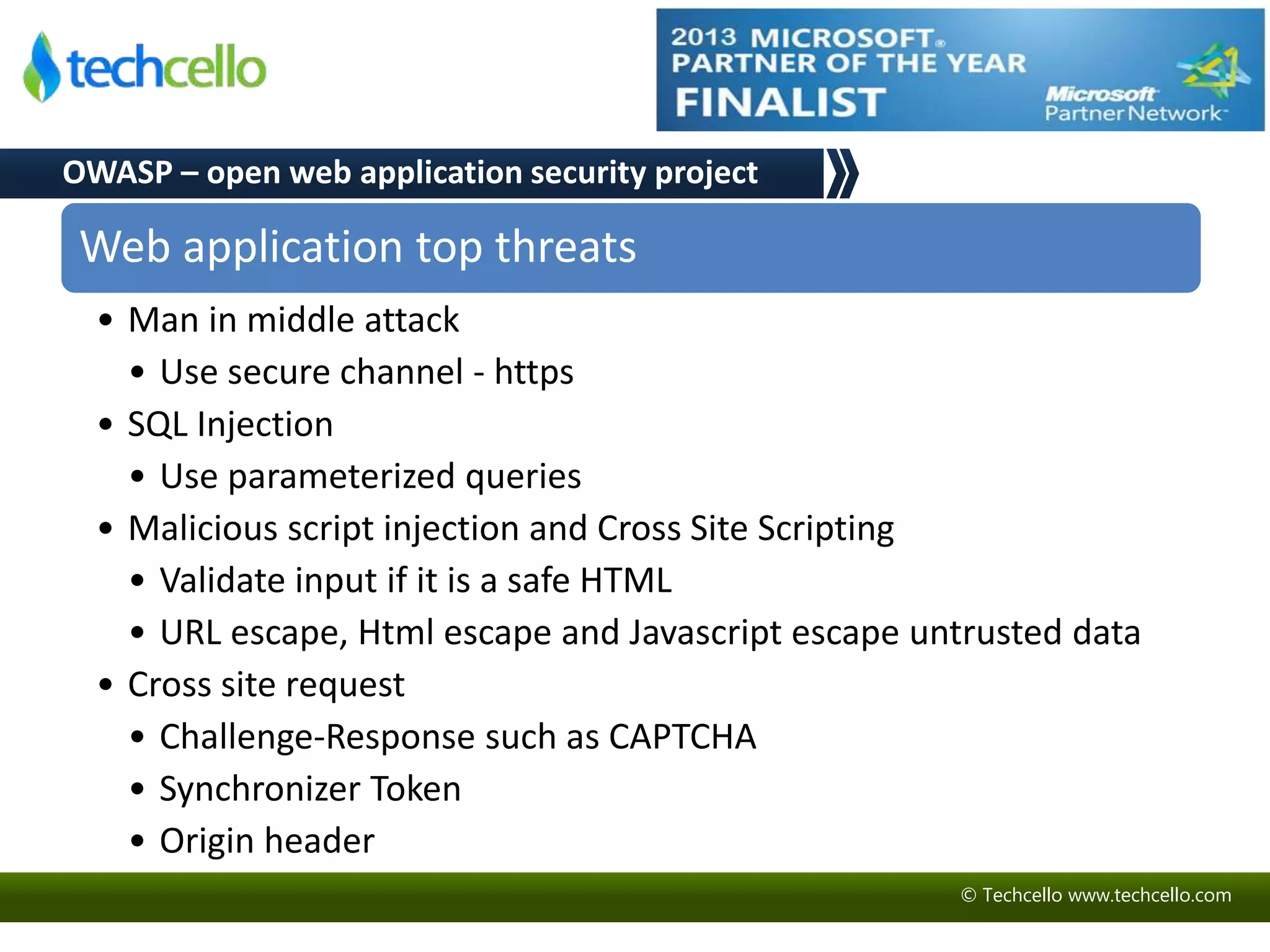
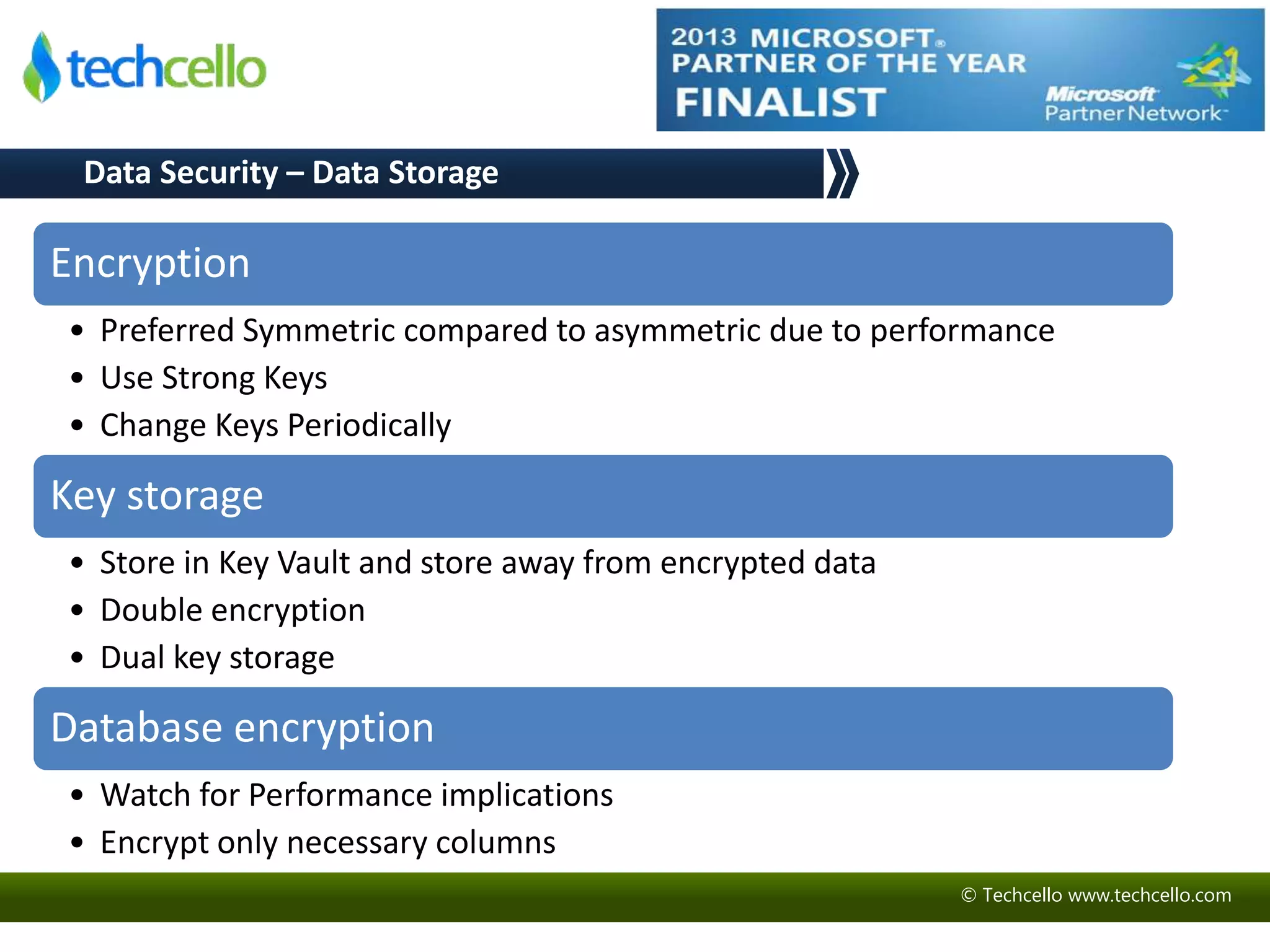
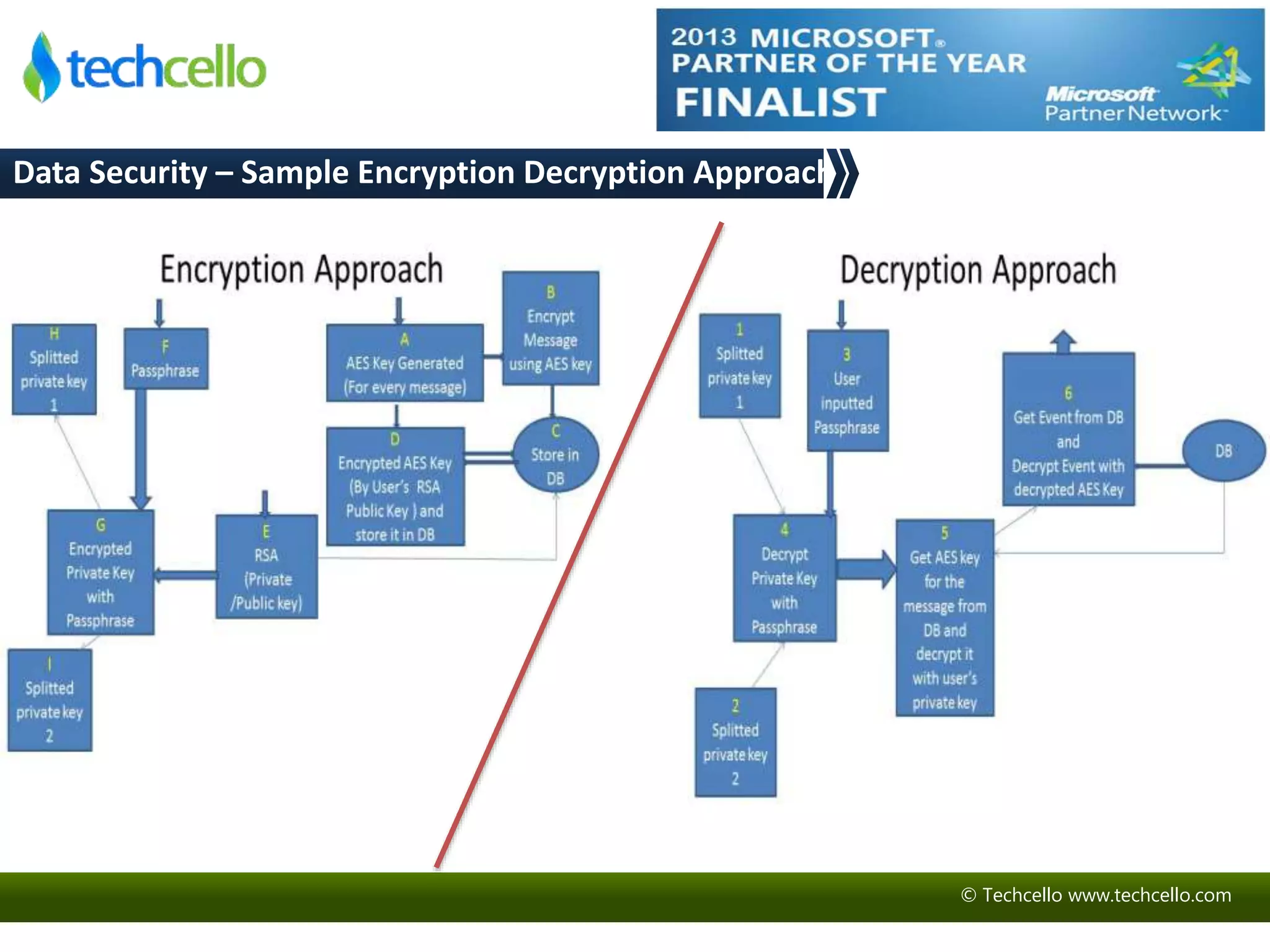
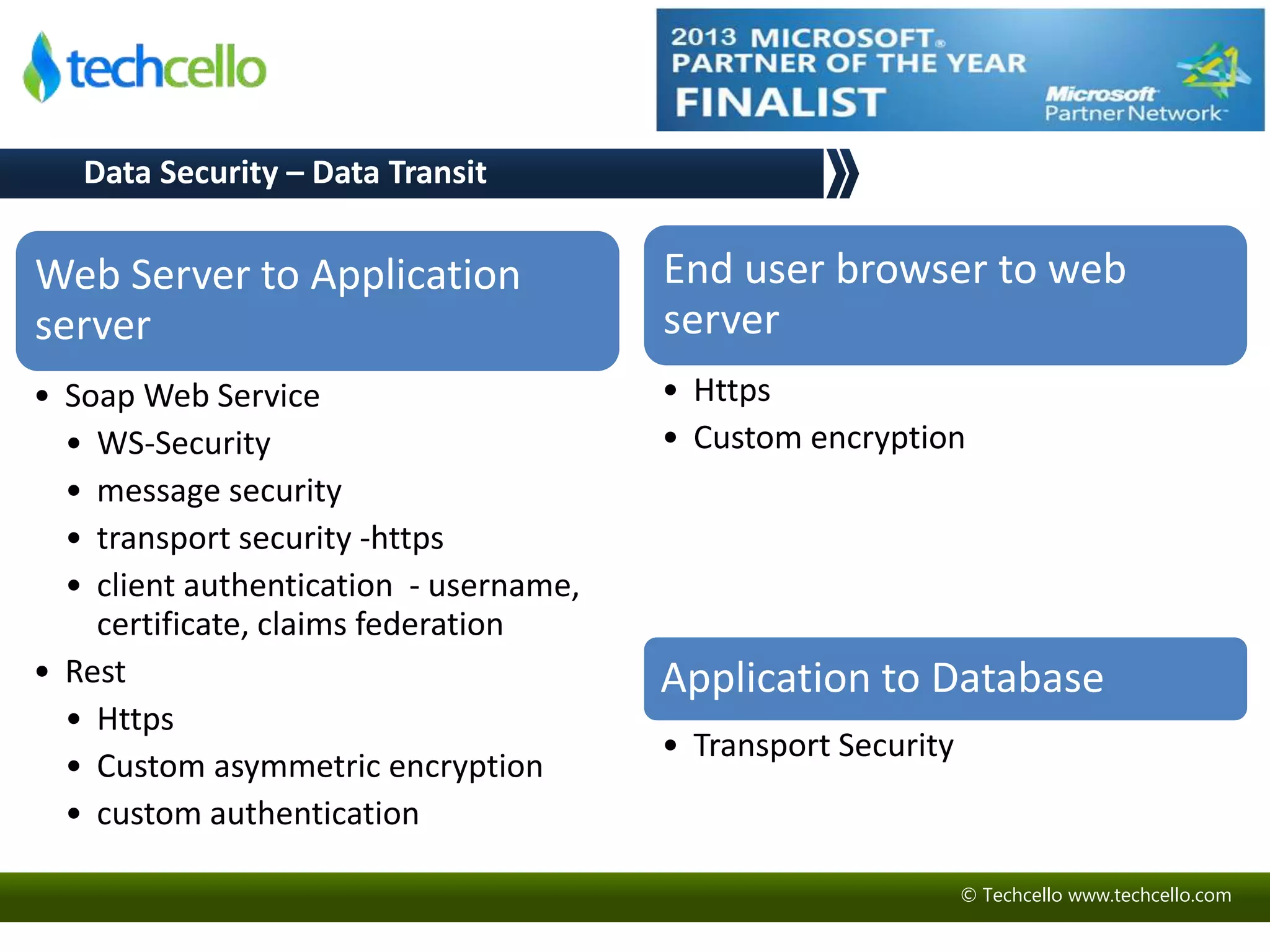
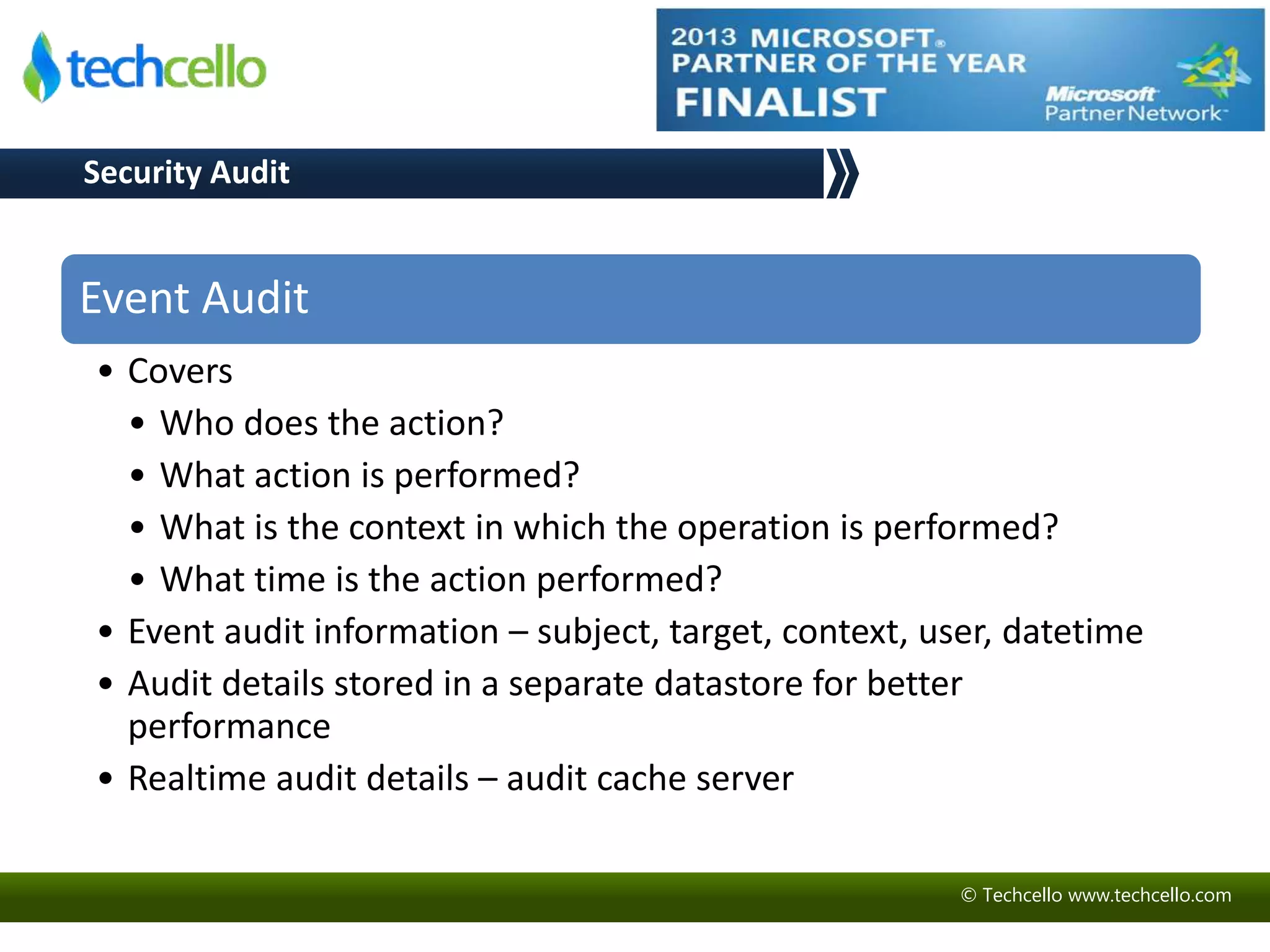
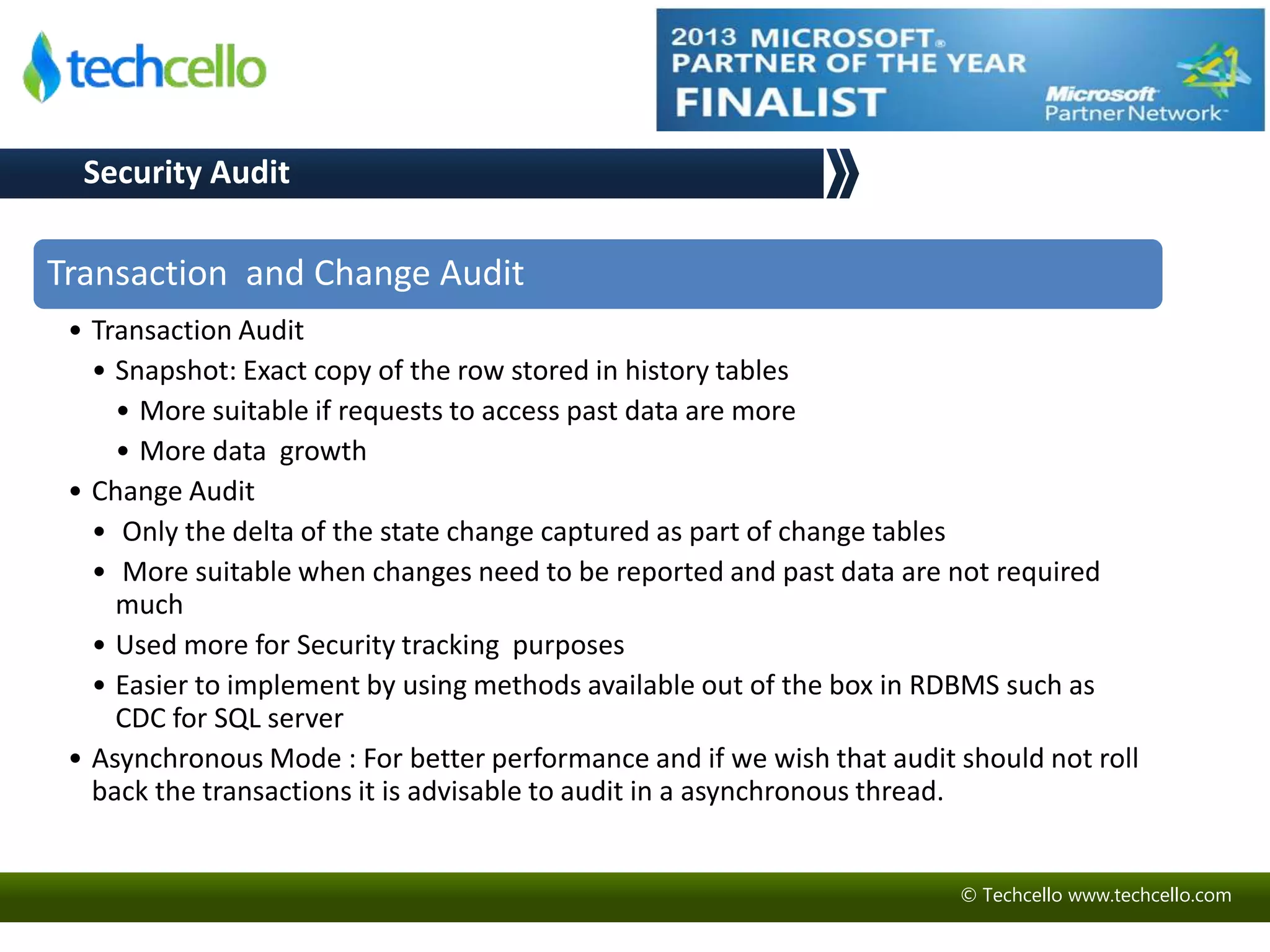
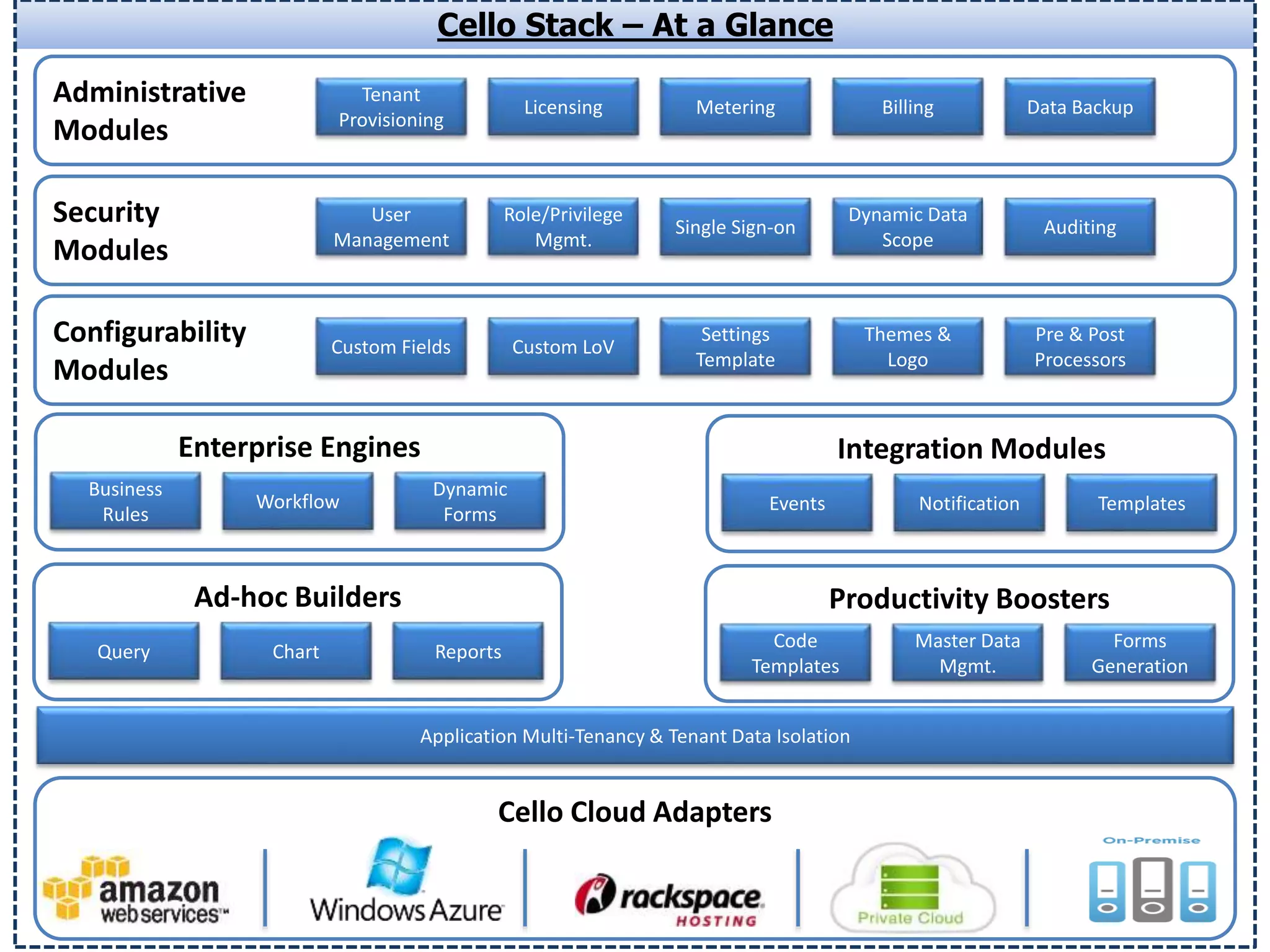
This document discusses building secure multi-tenant applications on .NET for cloud environments. It covers topics like tenant data isolation, role-based access control, securing data transmission and storage, addressing common web application vulnerabilities, and implementing security auditing. The speakers are introduced and their backgrounds are provided. Contact details and additional resources are listed at the end.