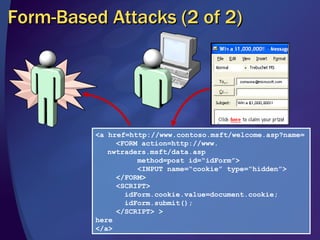
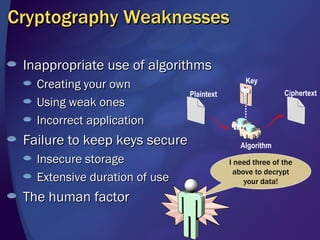
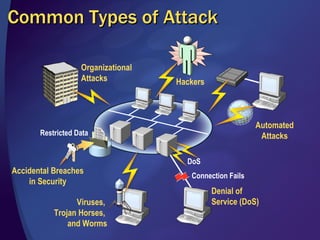
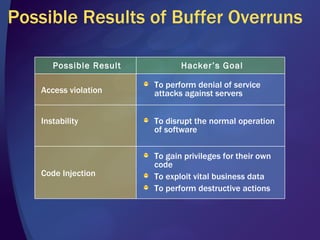
The document discusses various methods for writing secure code, including defending against memory issues like buffer overflows, arithmetic errors, cross-site scripting, SQL injection, canonicalization issues, cryptography weaknesses, Unicode issues, and denial of service attacks. It provides examples of these vulnerabilities and recommendations for mitigating each risk, such as input validation, output encoding, access control, key management practices, and using secure coding standards.









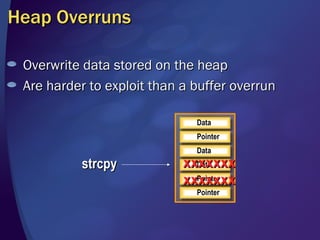
![Stack-Based Buffer Overrun Example Top of Stack char[4] int Return address void UnSafe (const char* uncheckedData) { int anotherLocalVariable; strcpy (localVariable, uncheckedData); } char localVariable[4];](https://image.slidesharecdn.com/writing-secure-code-threat-defense-13384/85/Writing-Secure-Code-Threat-Defense-12-320.jpg)