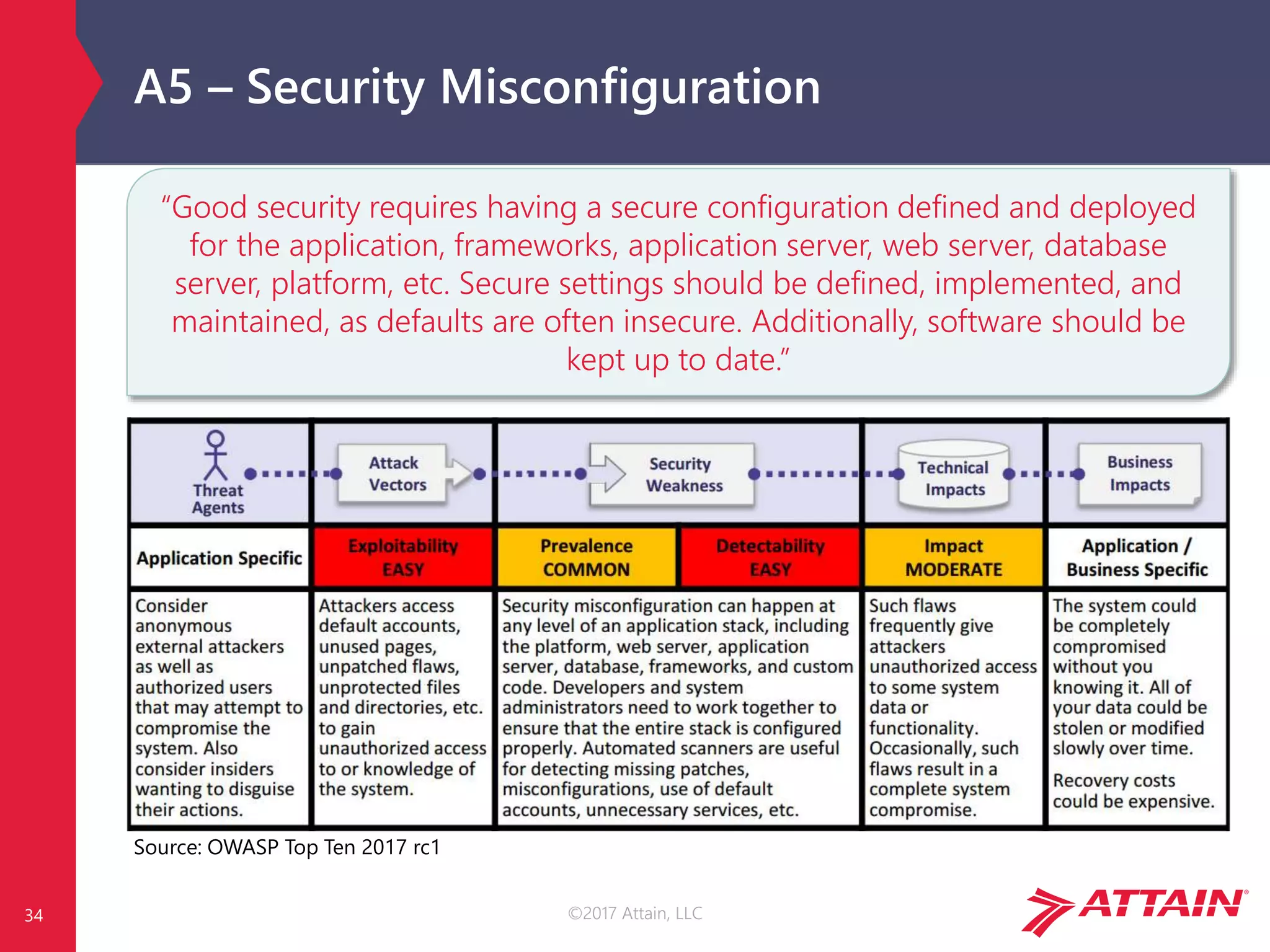
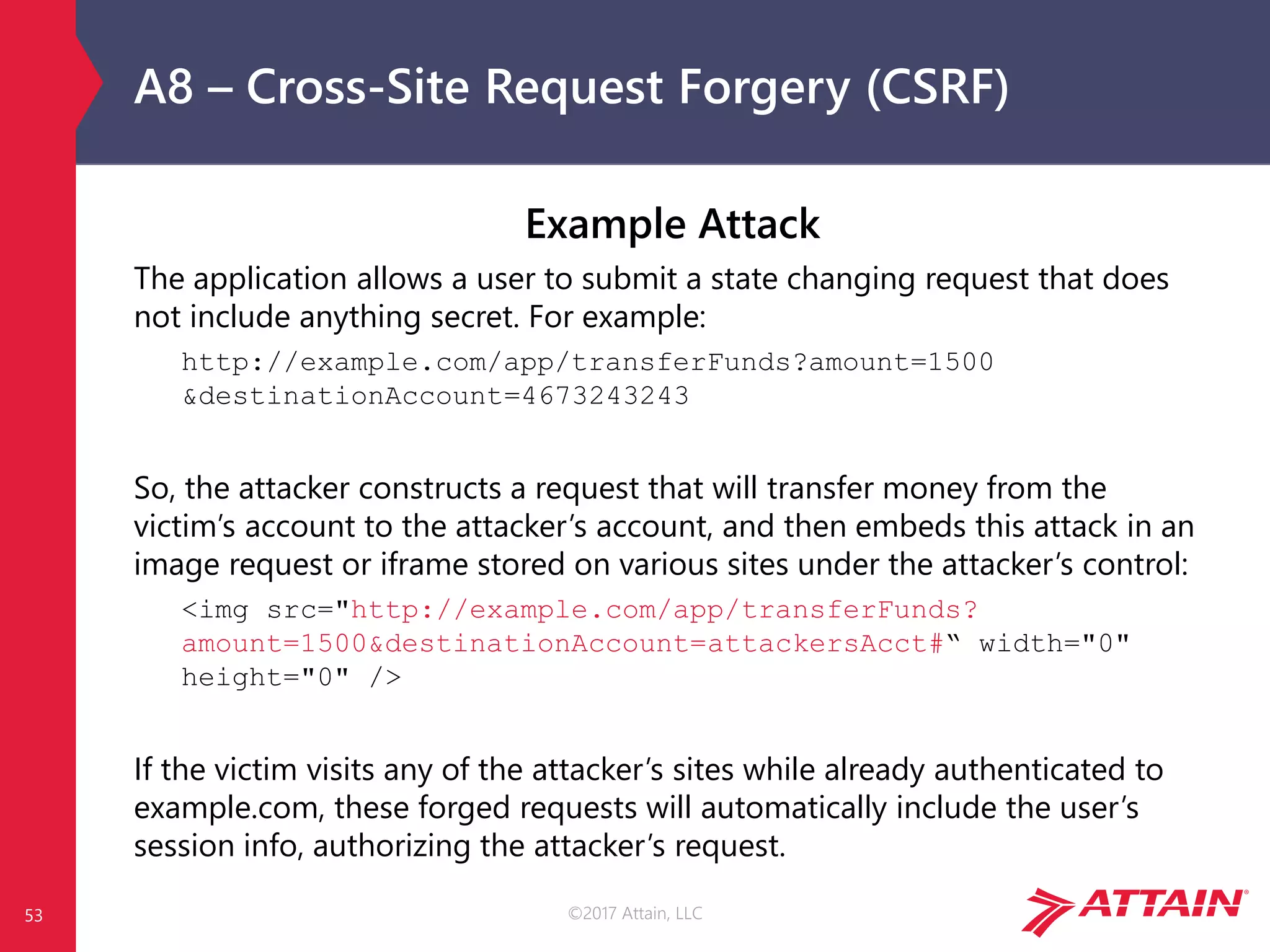
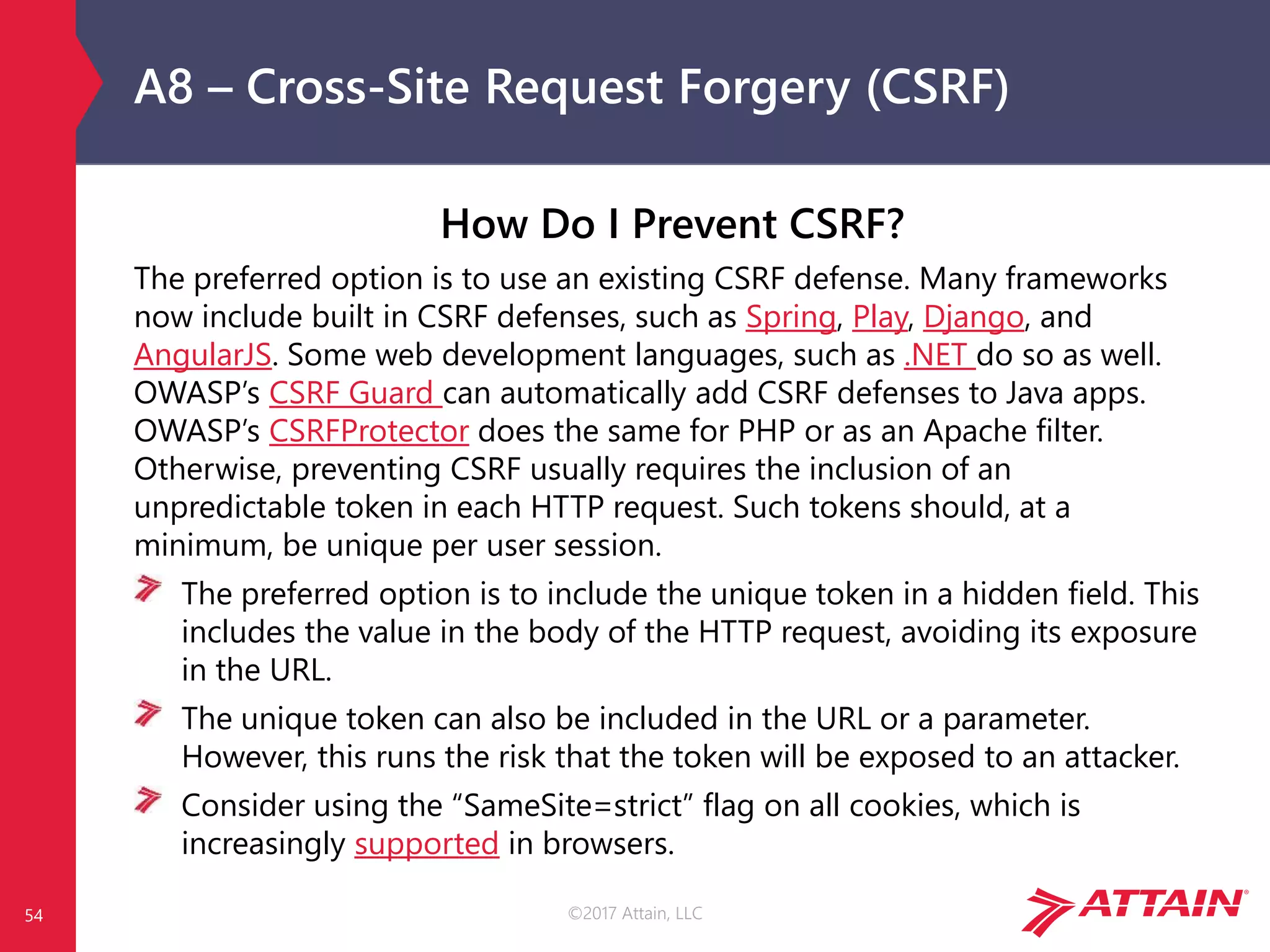
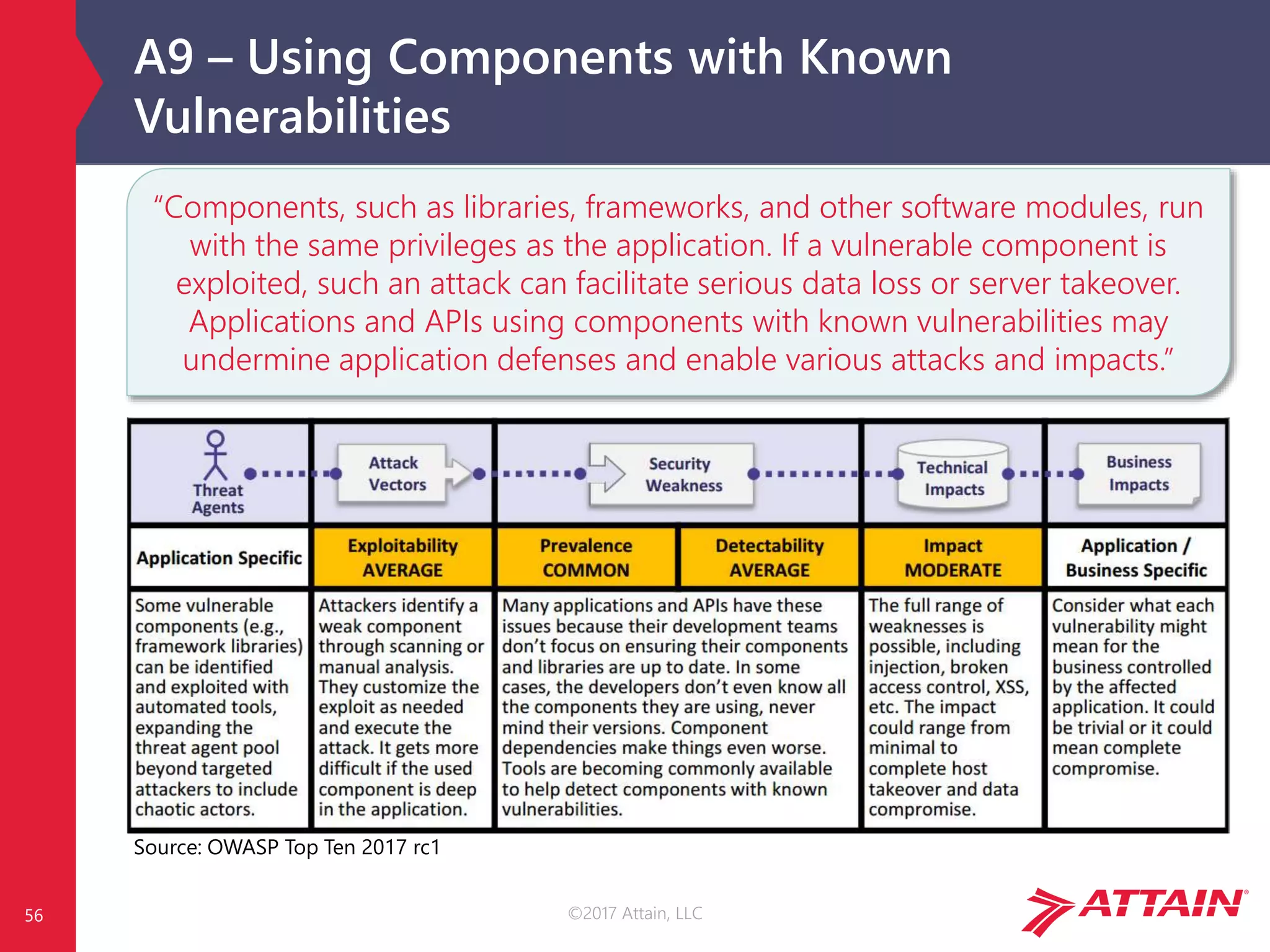
The document discusses the OWASP Top Ten, a prioritized list of the most critical web application security risks, aimed at raising awareness and providing a baseline for application security. It details risks such as injection, broken authentication, and security misconfiguration, along with strategies for prevention and relevant references. The OWASP Top Ten has been updated throughout the years, reflecting the evolving nature of web security threats.


![©2017 Attain, LLC
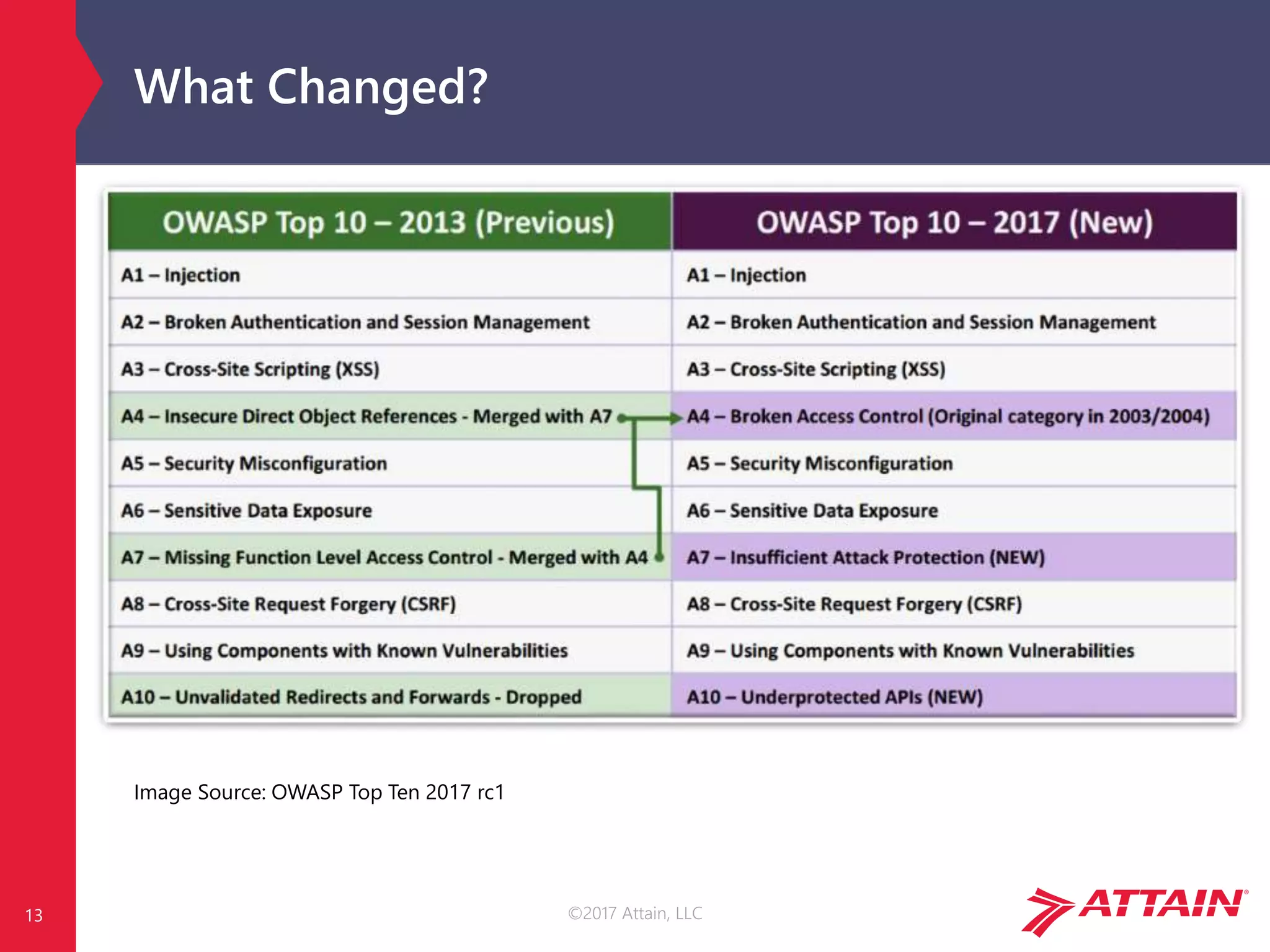
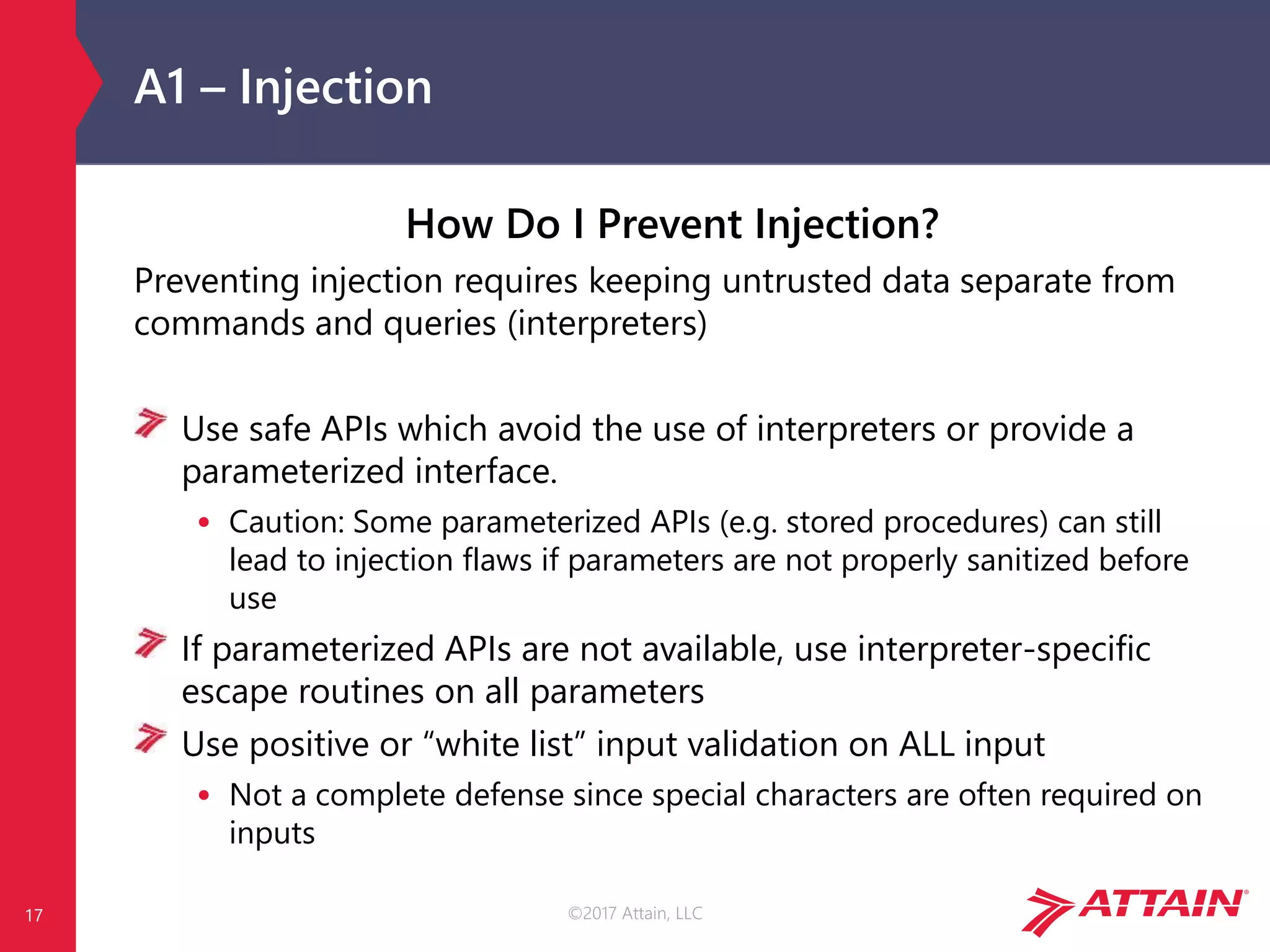
What is the OWASP Top Ten?
The OWASP Top Ten is a prioritized list of the top ten most critical
web application security risks.
It’s an awareness tool, not a standard
Released in 2003, 2004, 2007, 2010, 2013, 2017 (this Summer)
Developed using the OWASP Risk Rating Methodology [1]
2017 rc1 based on results from a 2016 open data call
It’s about risks, not (just) about vulnerabilities
Not intended to be “airtight, non-overlapping, or a strict
taxonomy”
Constantly changing….
1. https://www.owasp.org/index.php/OWASP_Risk_Rating_Methodology
6
“The Ten Most Critical Web Application Security Risks”](https://image.slidesharecdn.com/6-7-2017stlcyber-owasptopten2017-170608143335/75/OWASP-Top-10-2017-rc1-The-Ten-Most-Critical-Web-Application-Security-Risks-6-2048.jpg)


![©2017 Attain, LLC
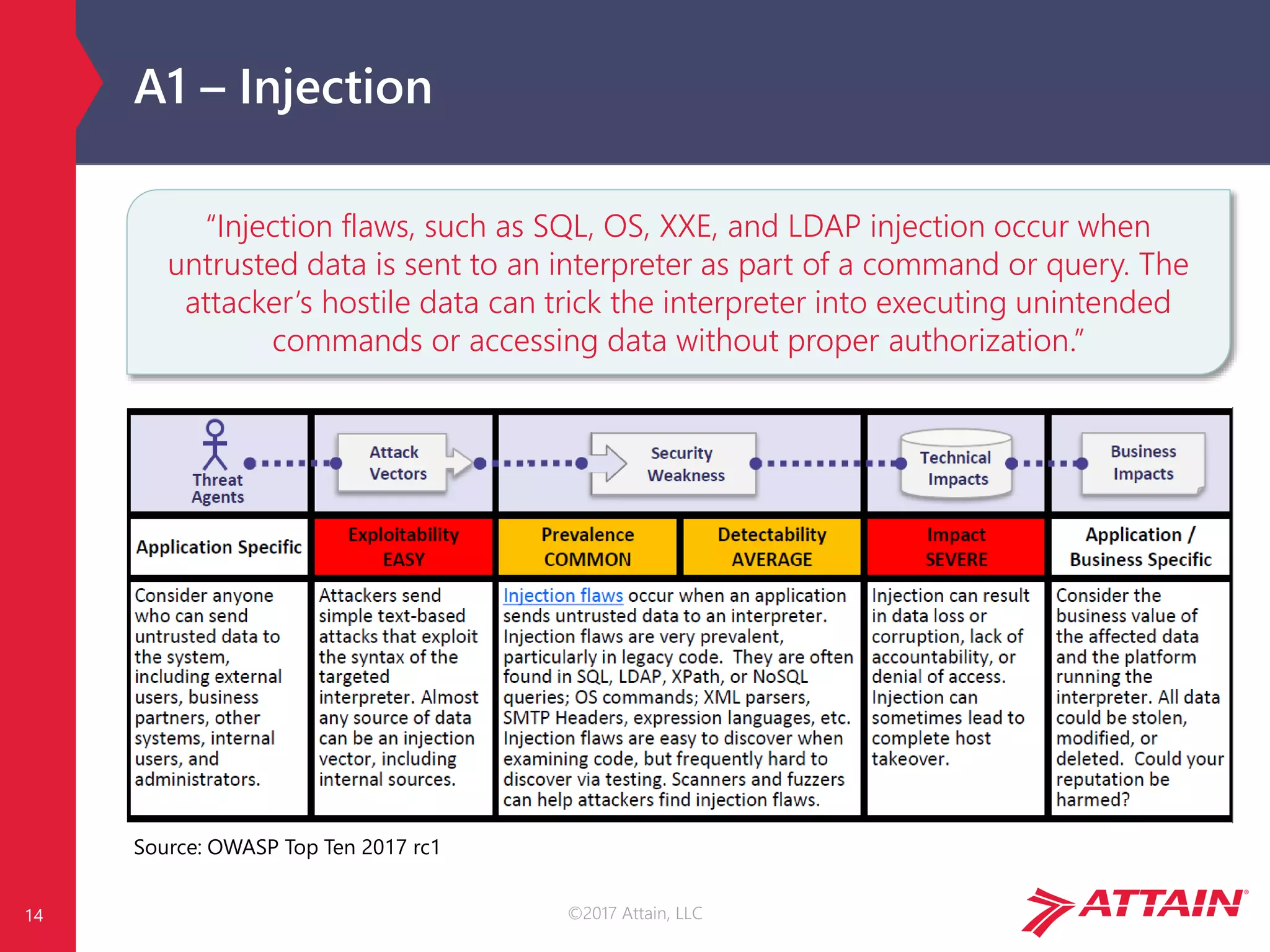
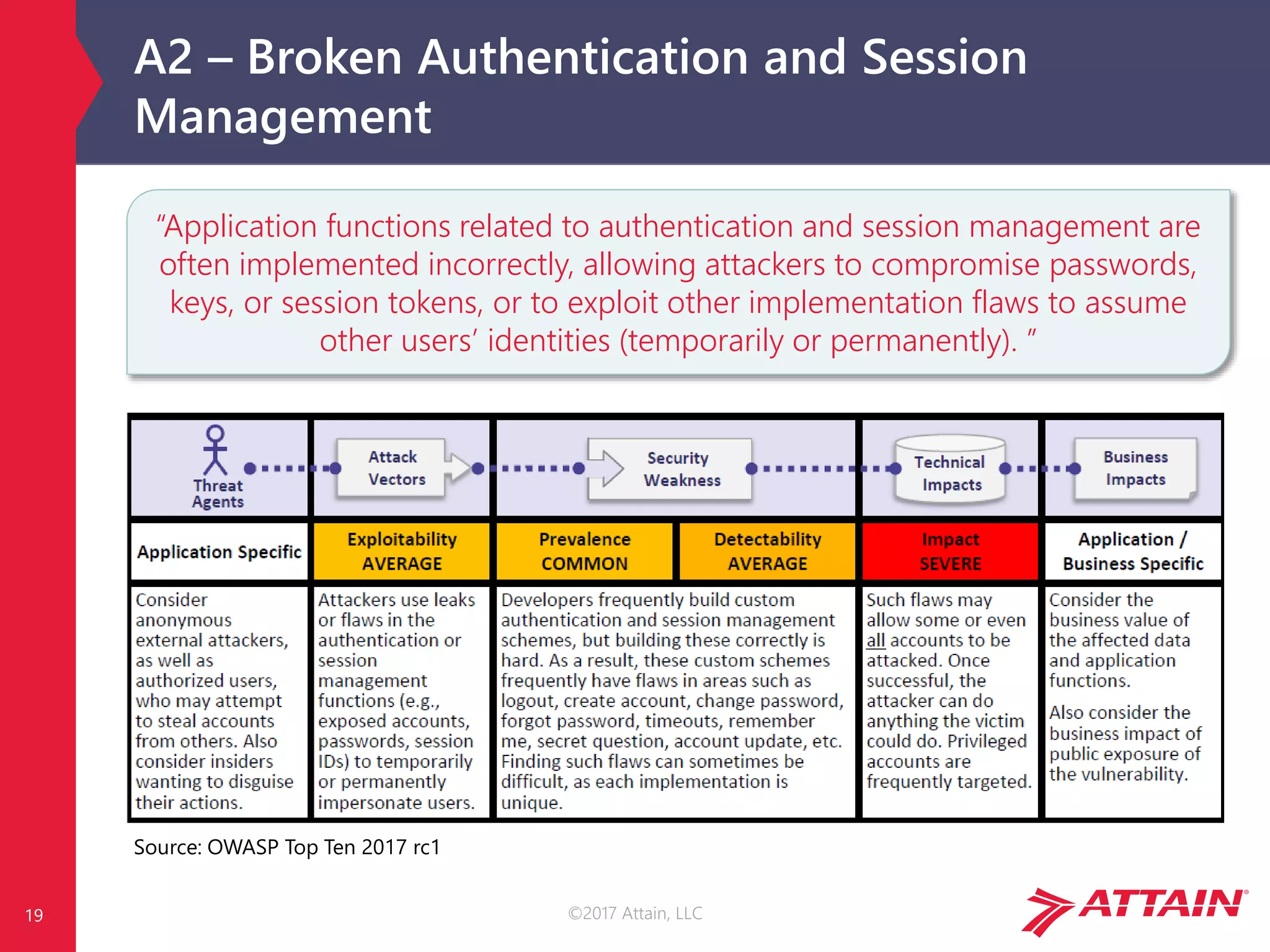
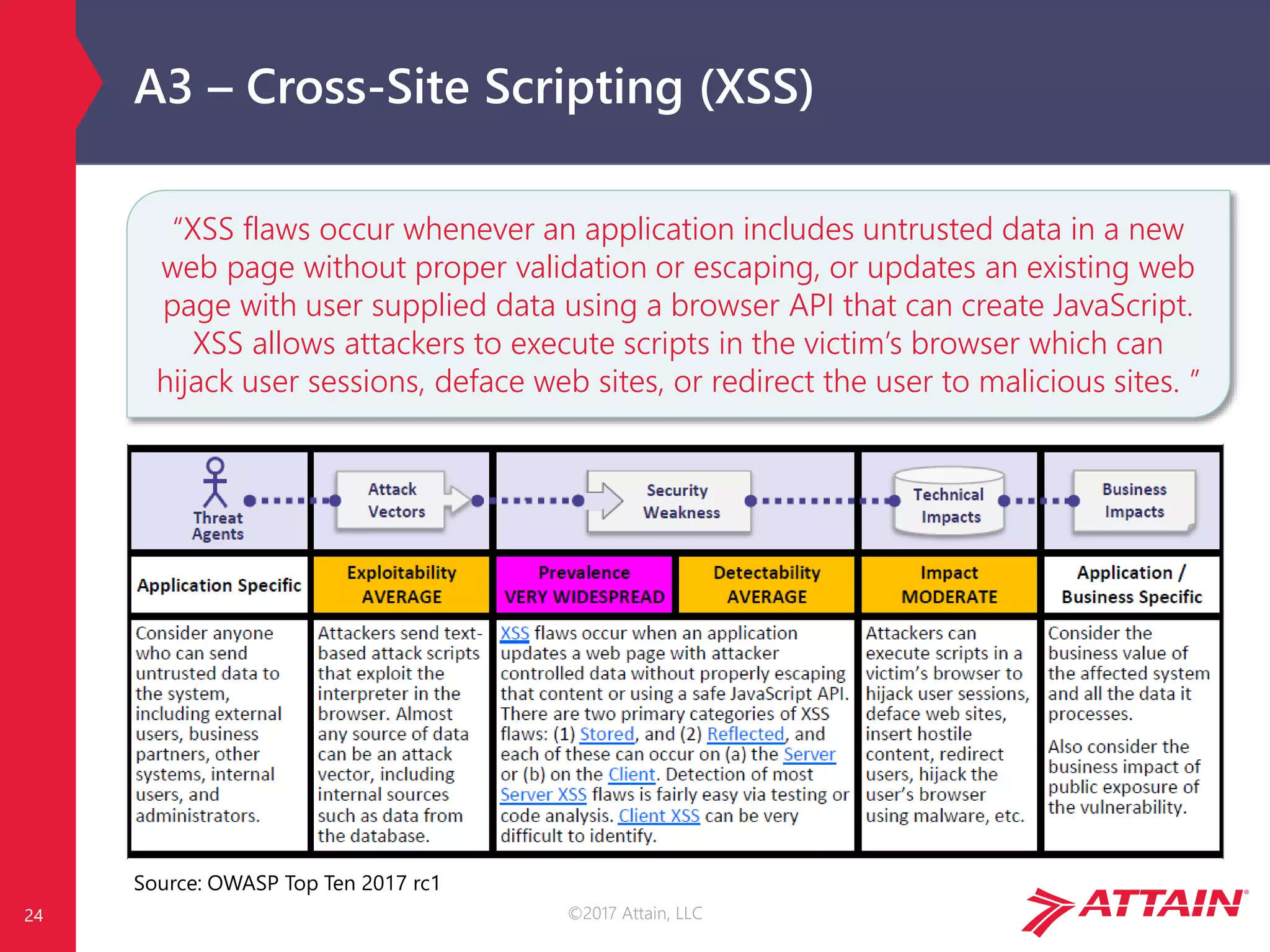
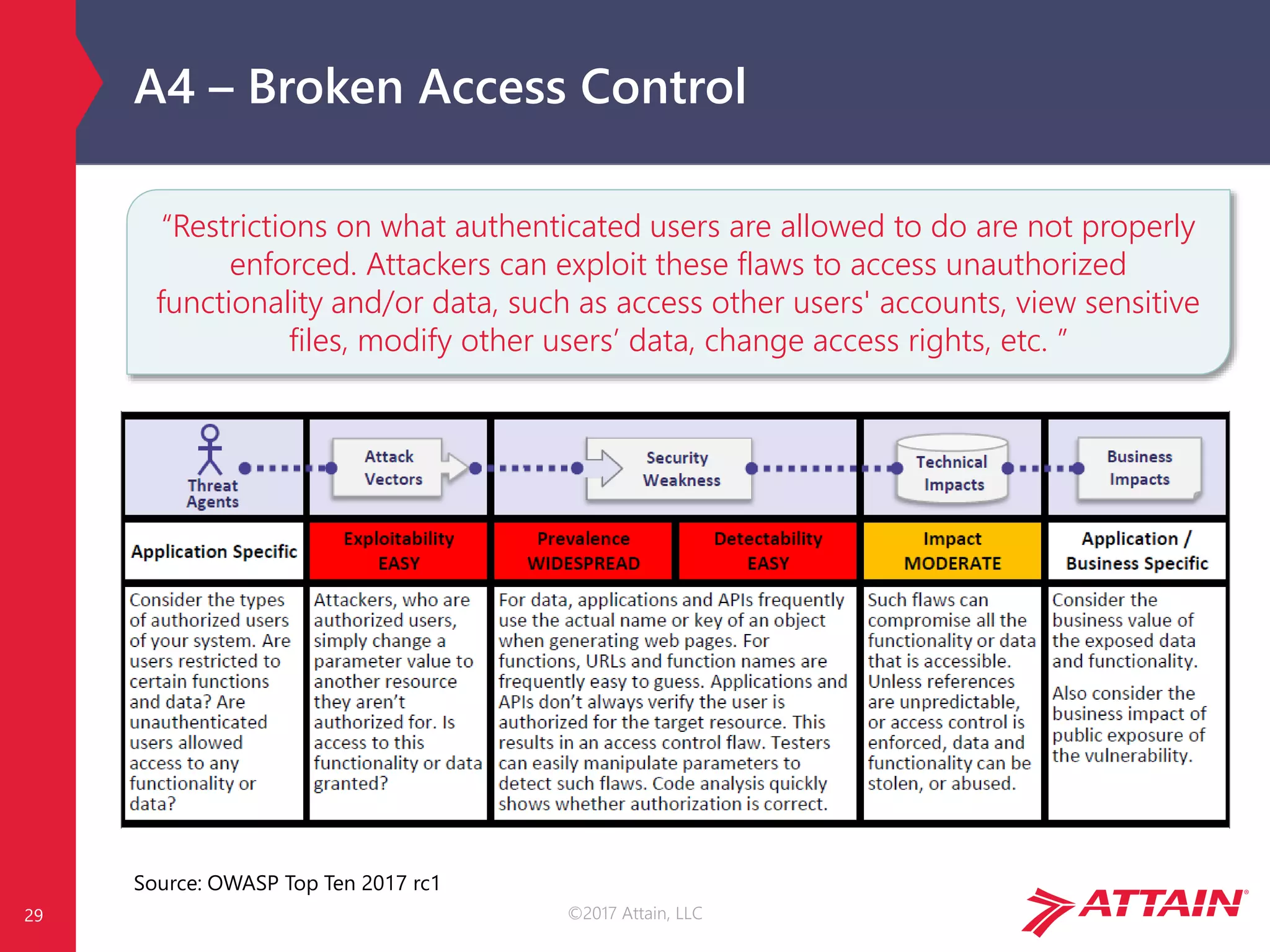
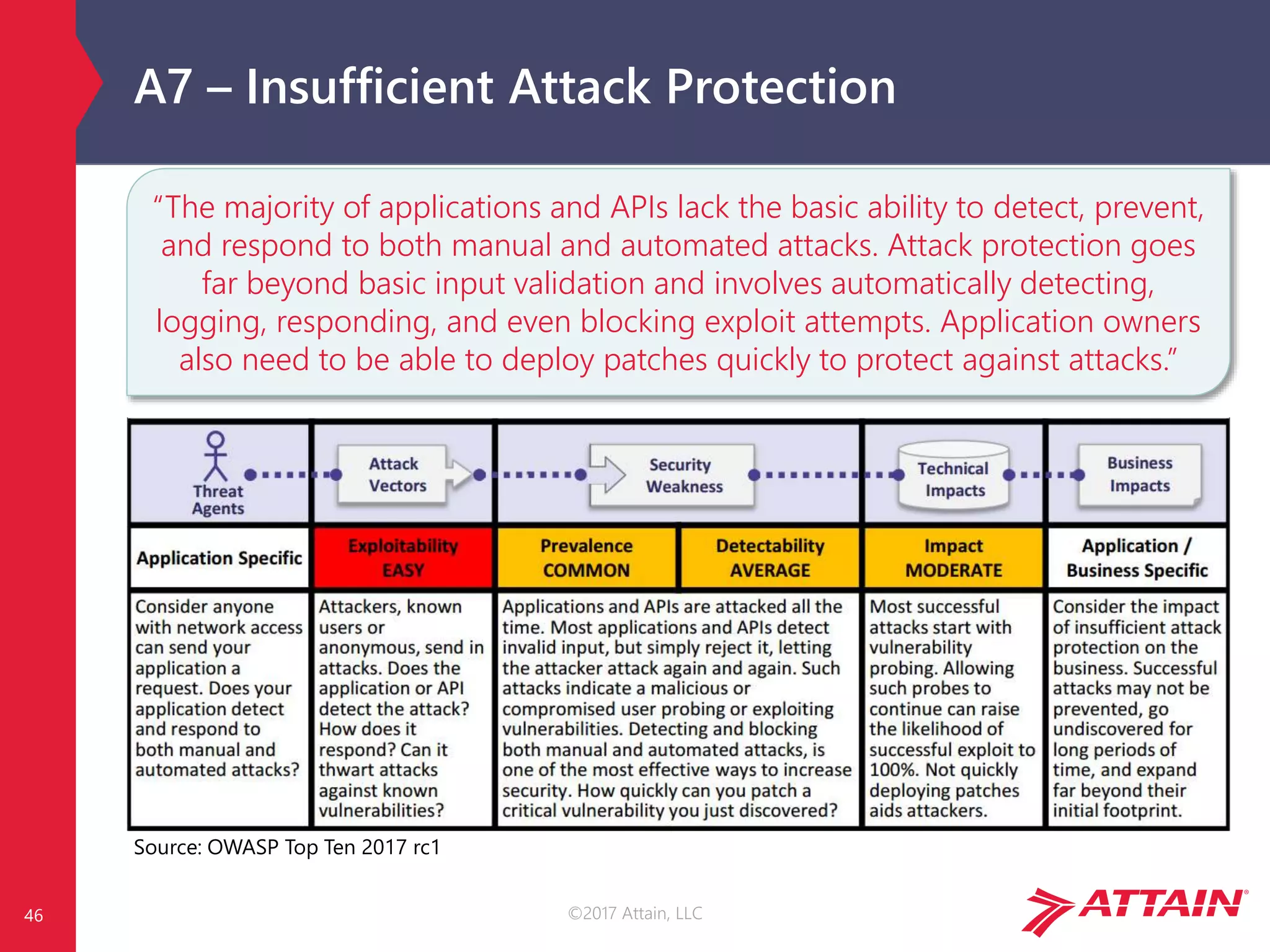
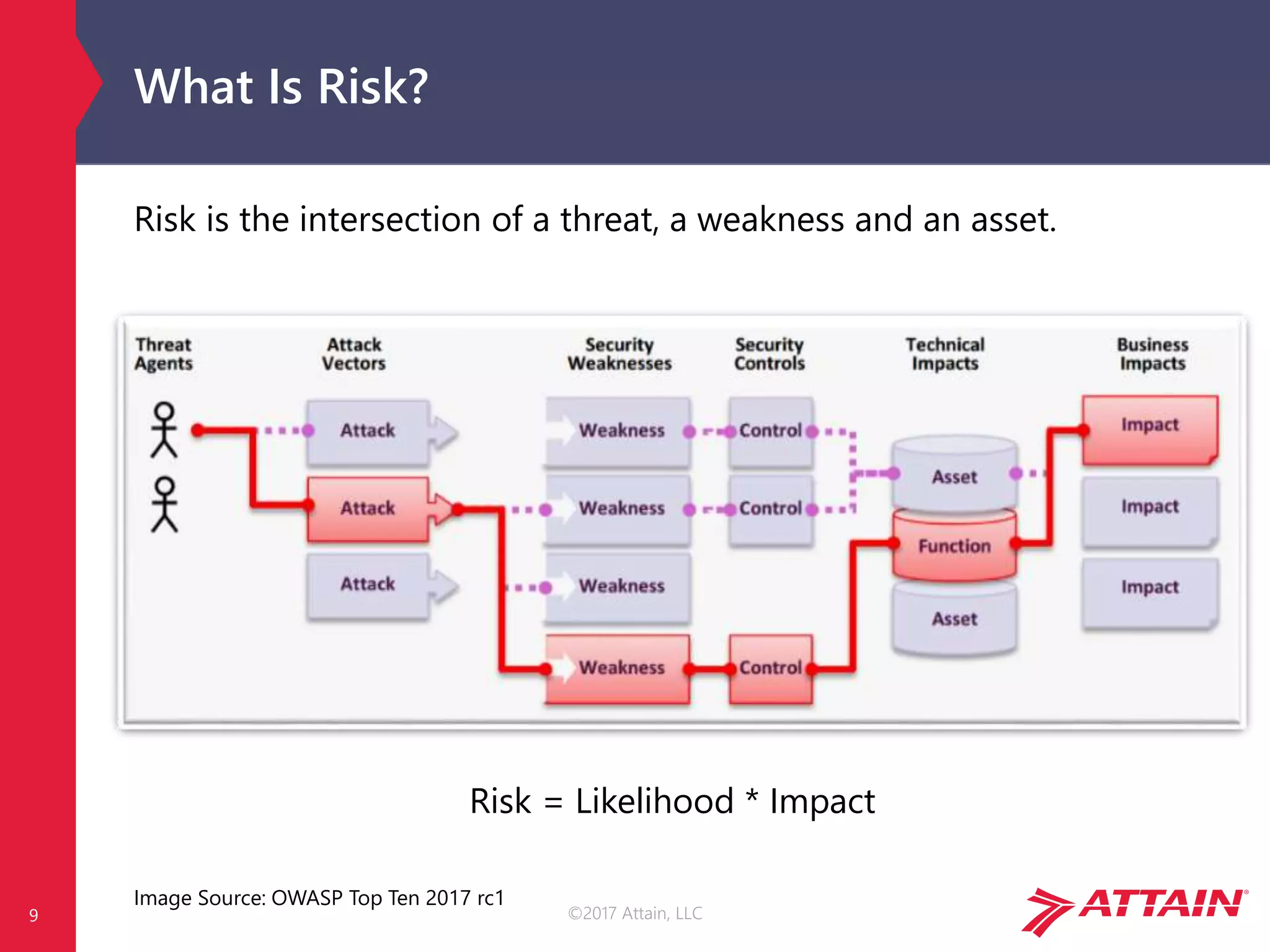
OWASP Risk Calculation
Each risk is calculated using generic vulnerability facts, based on the
OWASP Risk Rating Methodology [1]…
…but impact is environment and business specific!
Image Source: OWASP Top Ten 2017 rc1
1. https://www.owasp.org/index.php/OWASP_Risk_Rating_Methodology
10](https://image.slidesharecdn.com/6-7-2017stlcyber-owasptopten2017-170608143335/75/OWASP-Top-10-2017-rc1-The-Ten-Most-Critical-Web-Application-Security-Risks-10-2048.jpg)