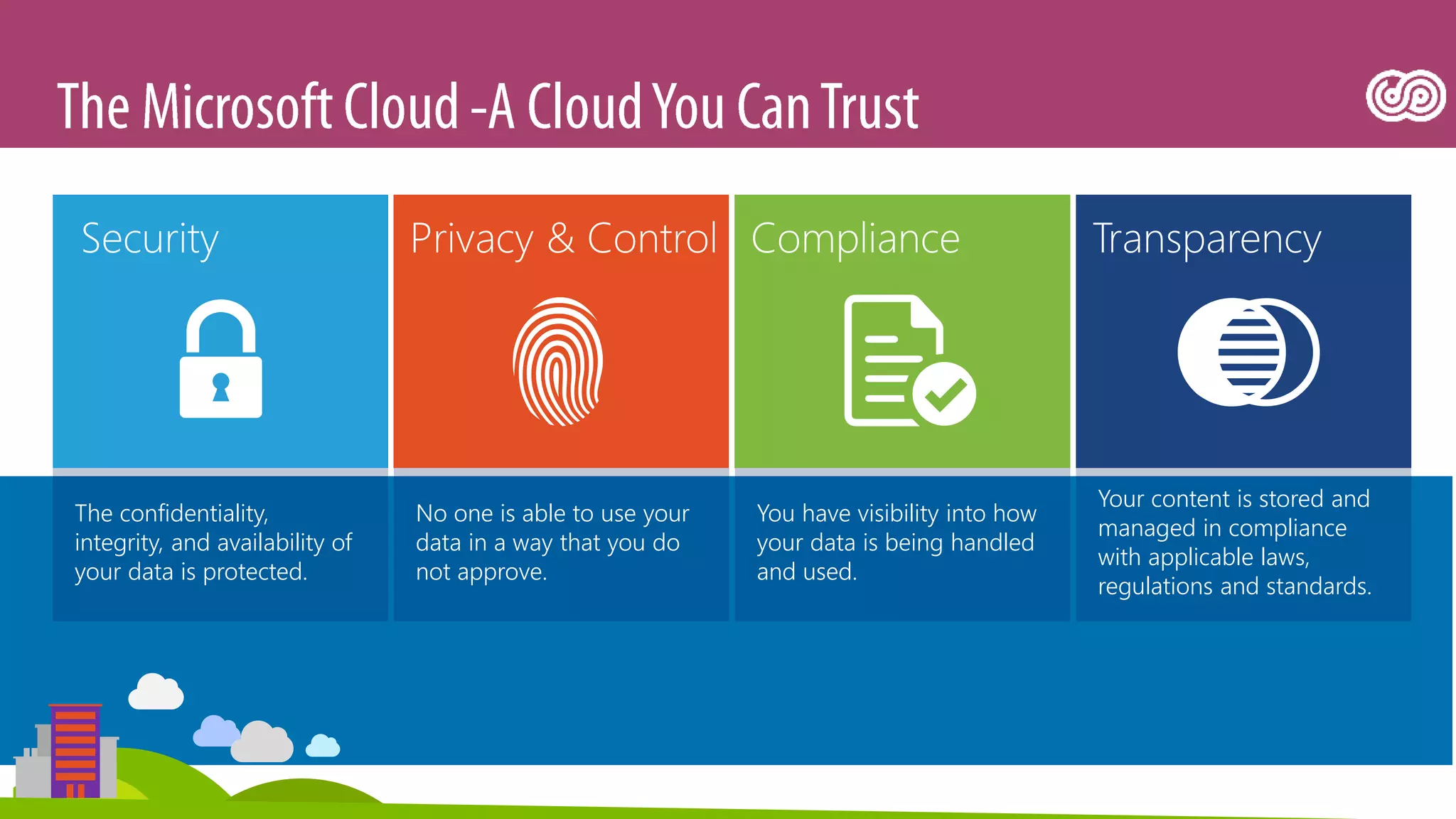
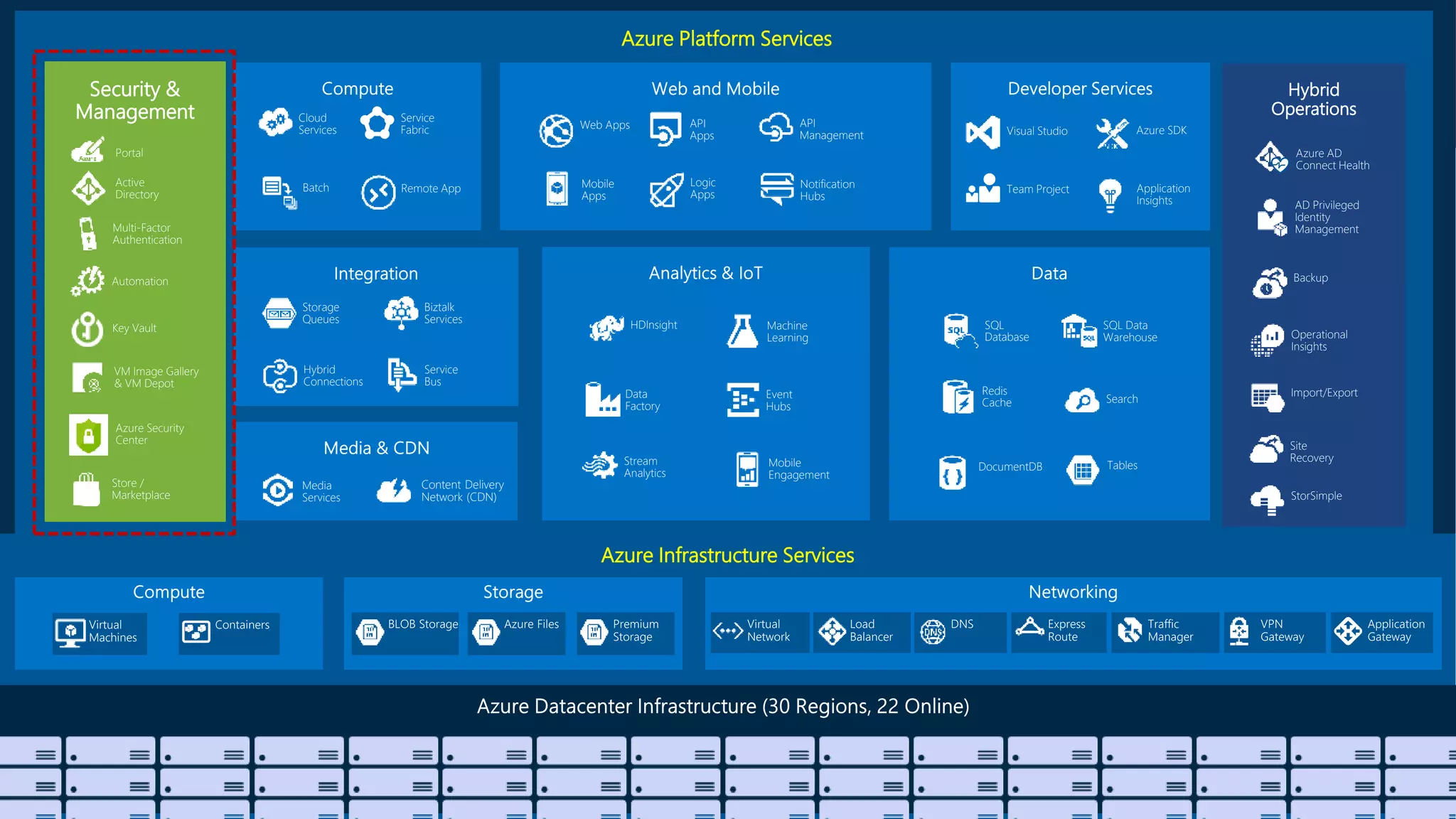
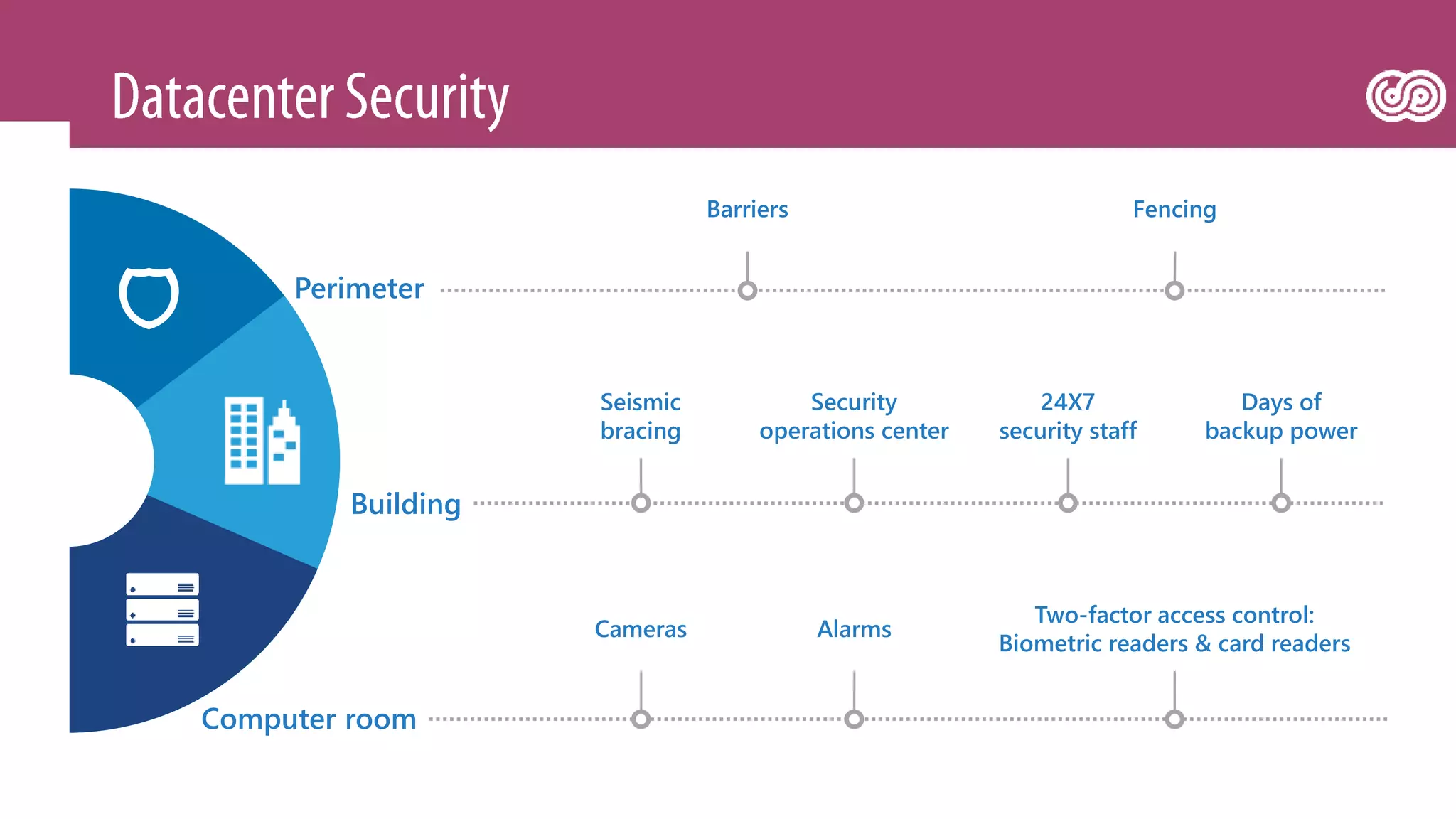
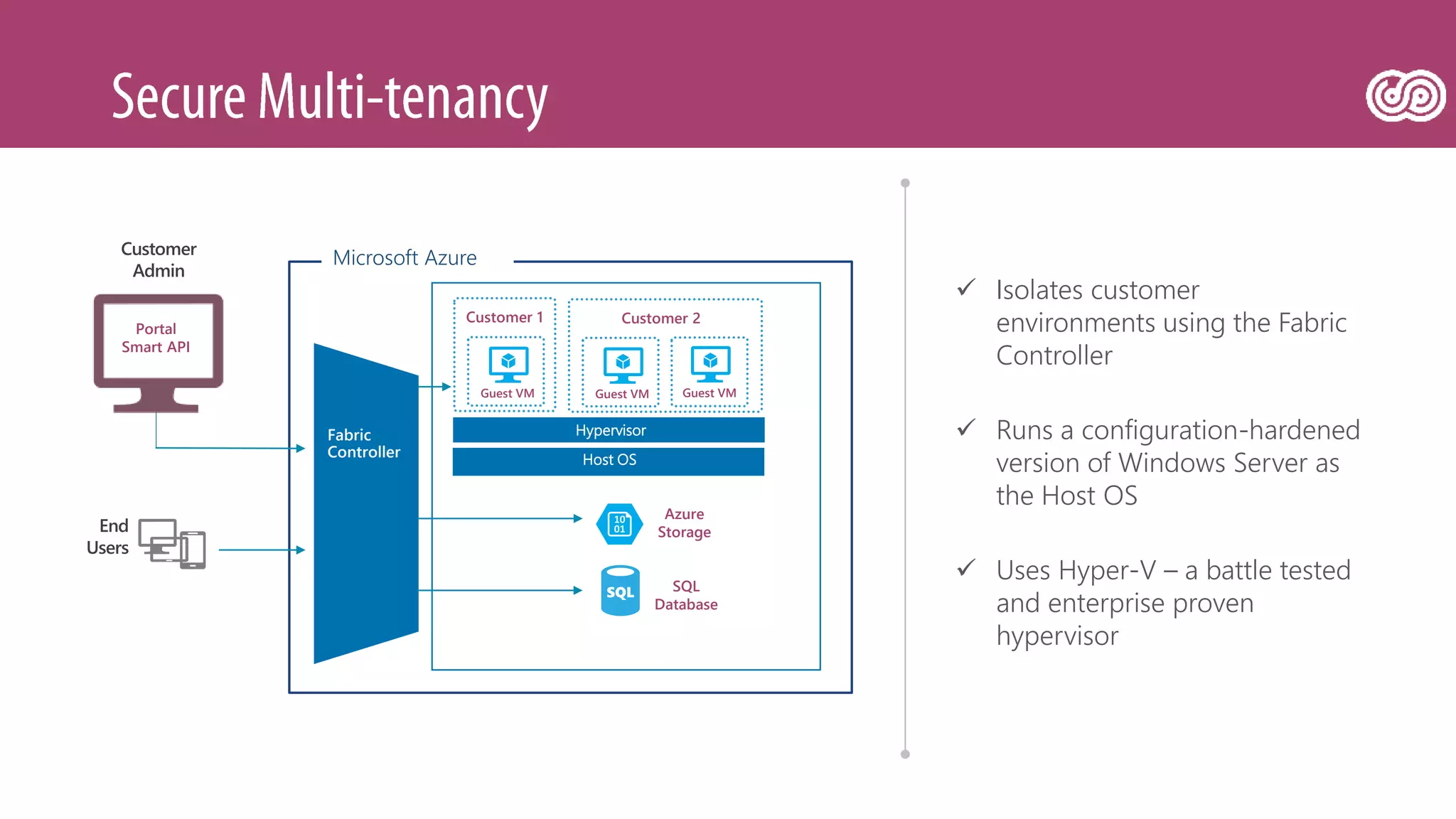
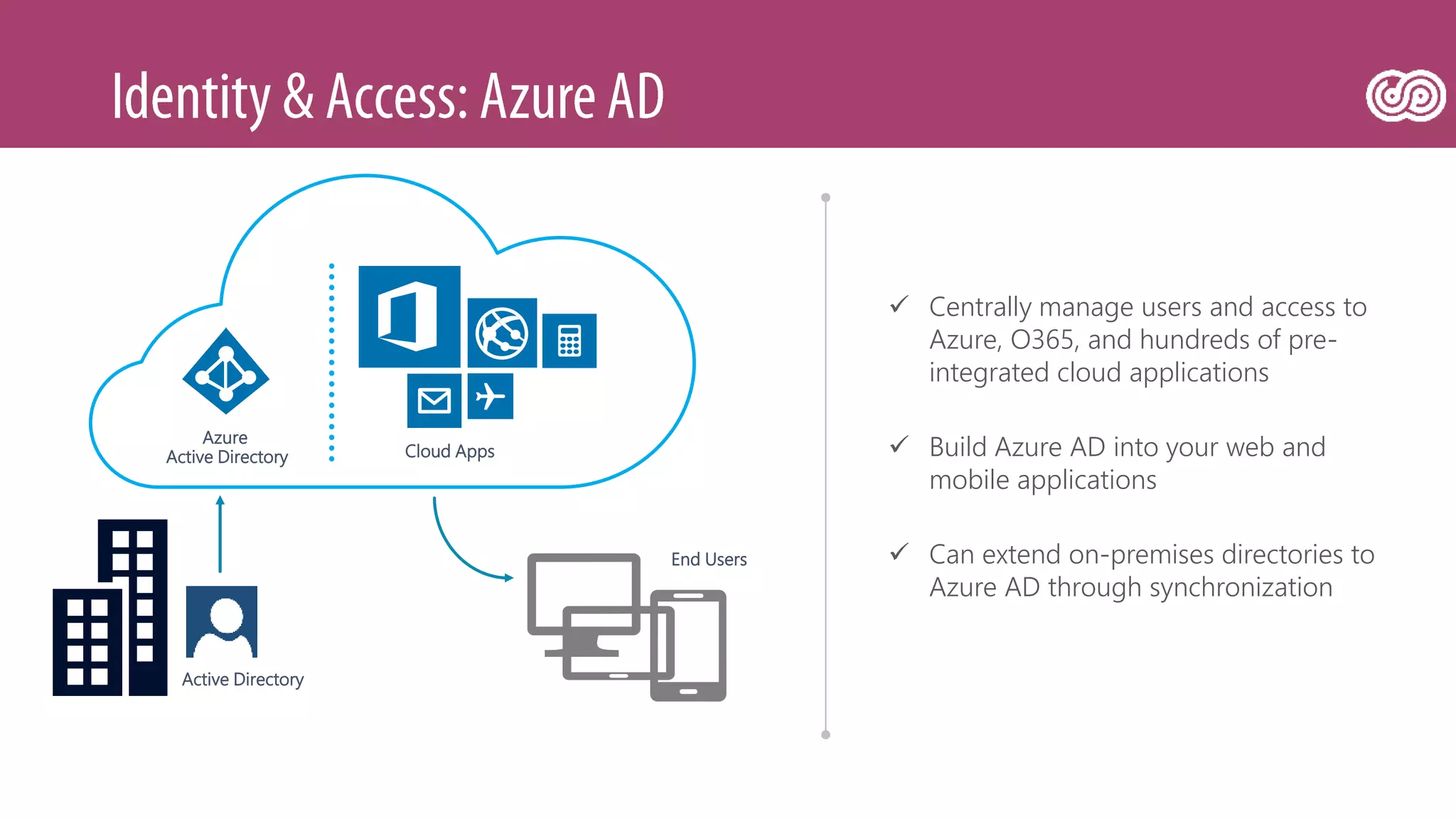
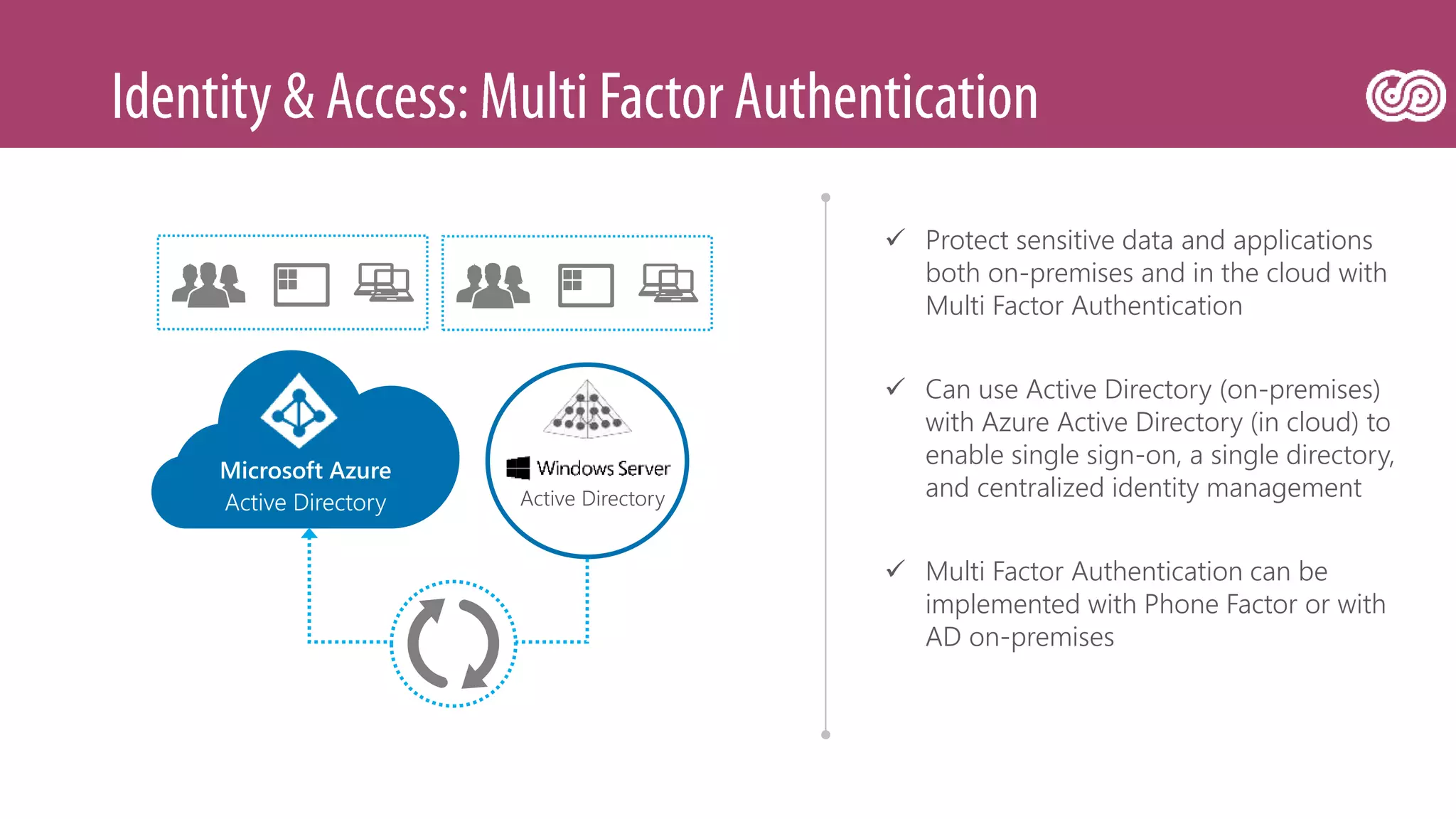
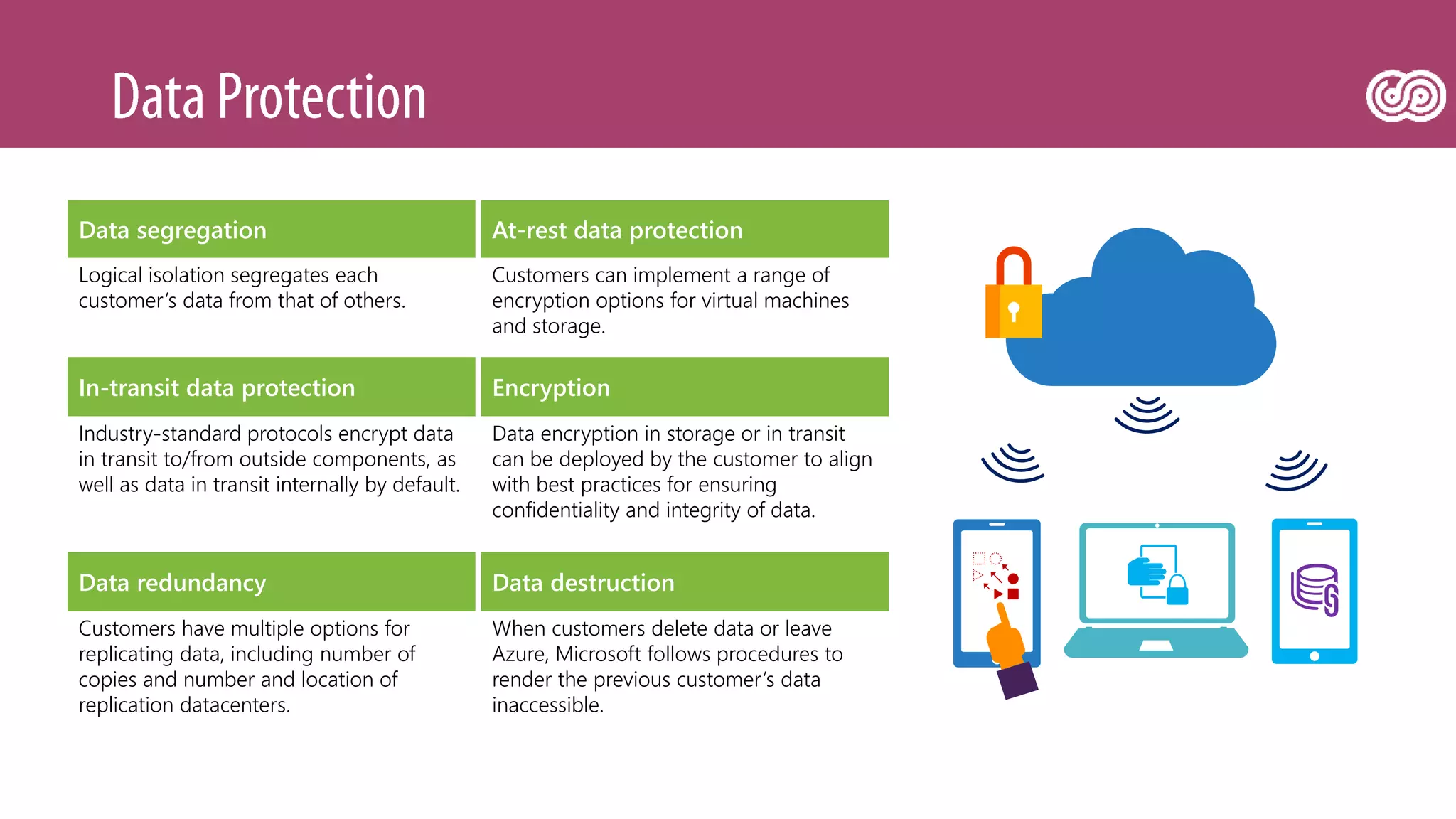
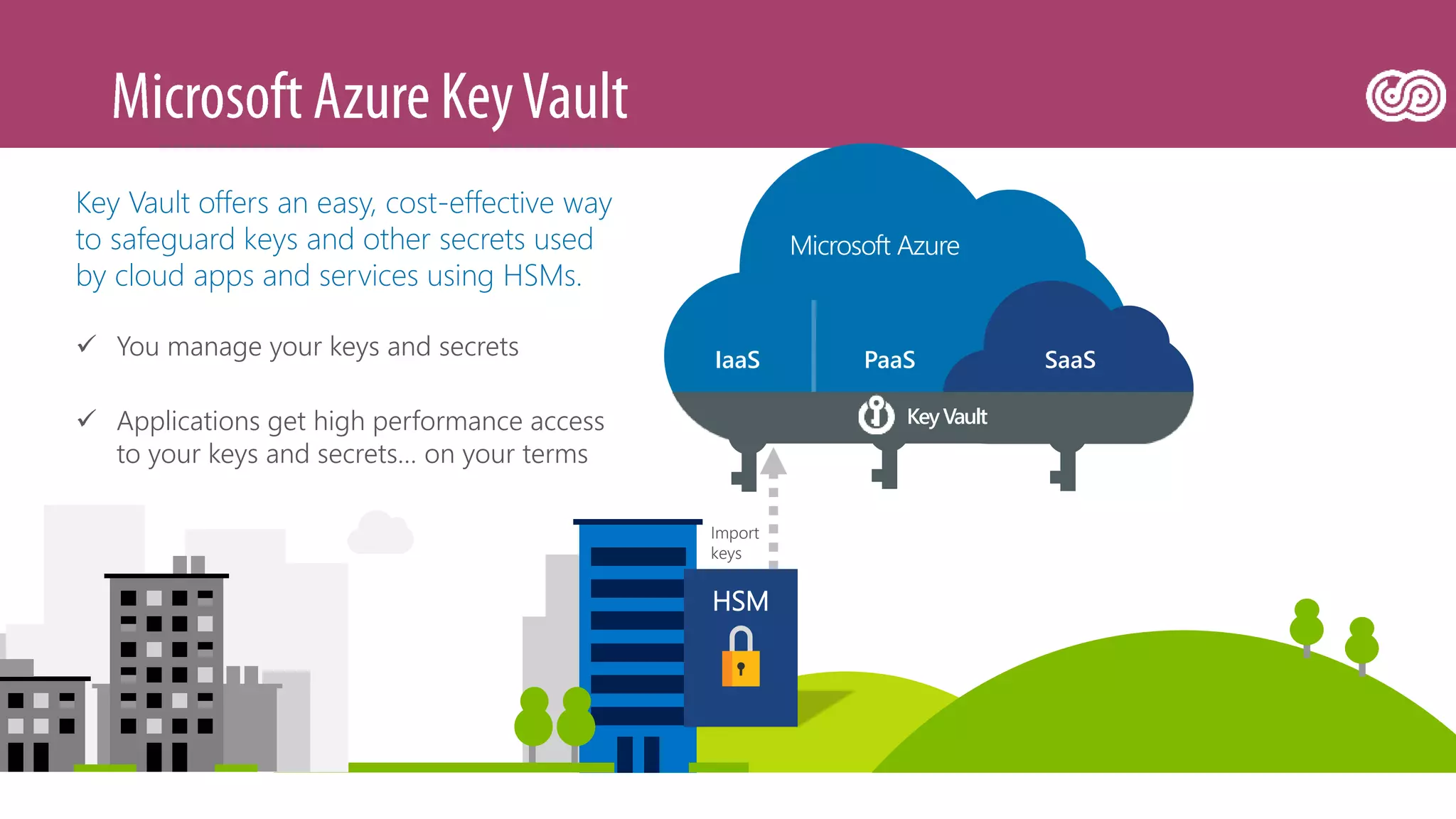
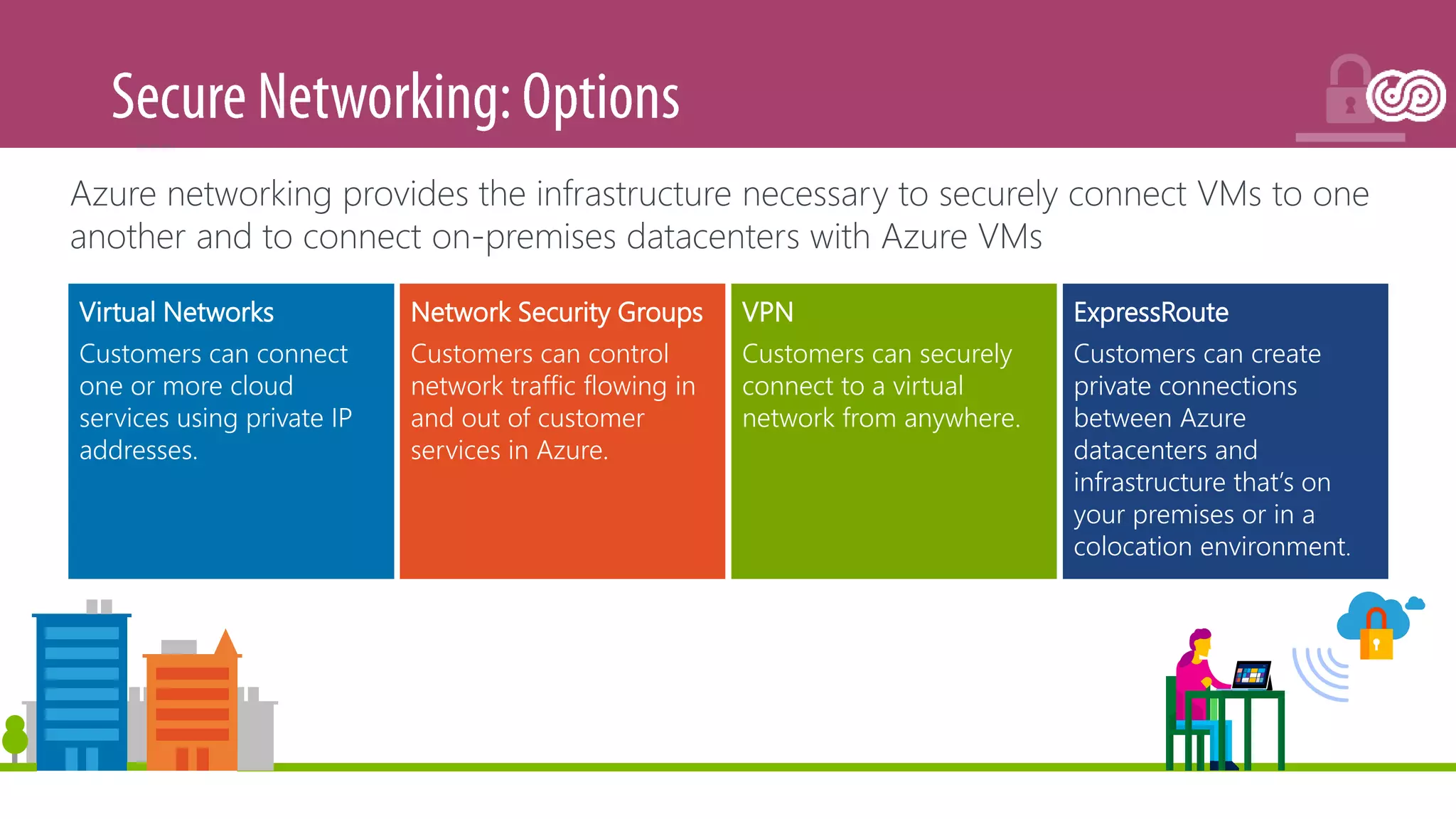
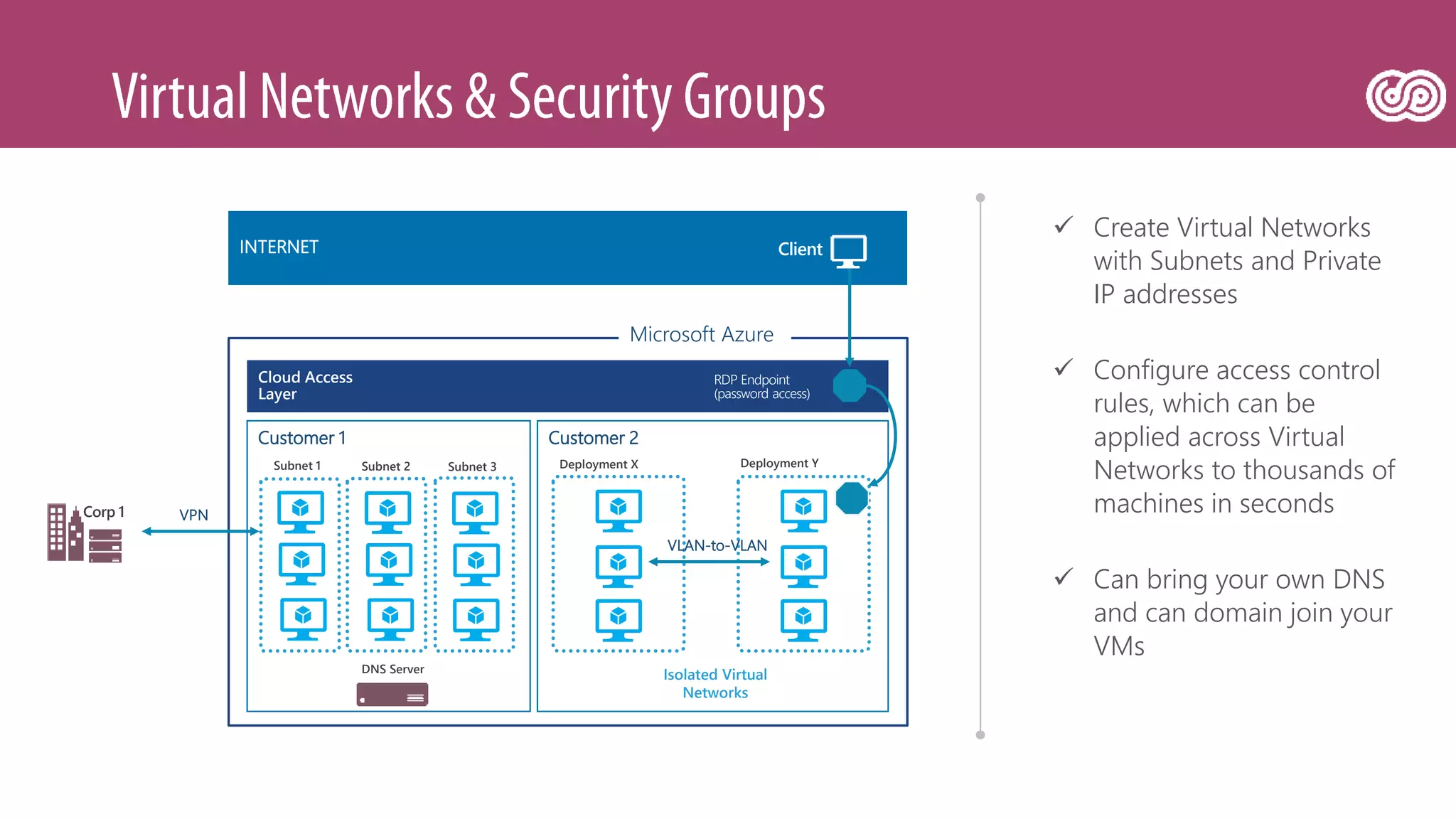
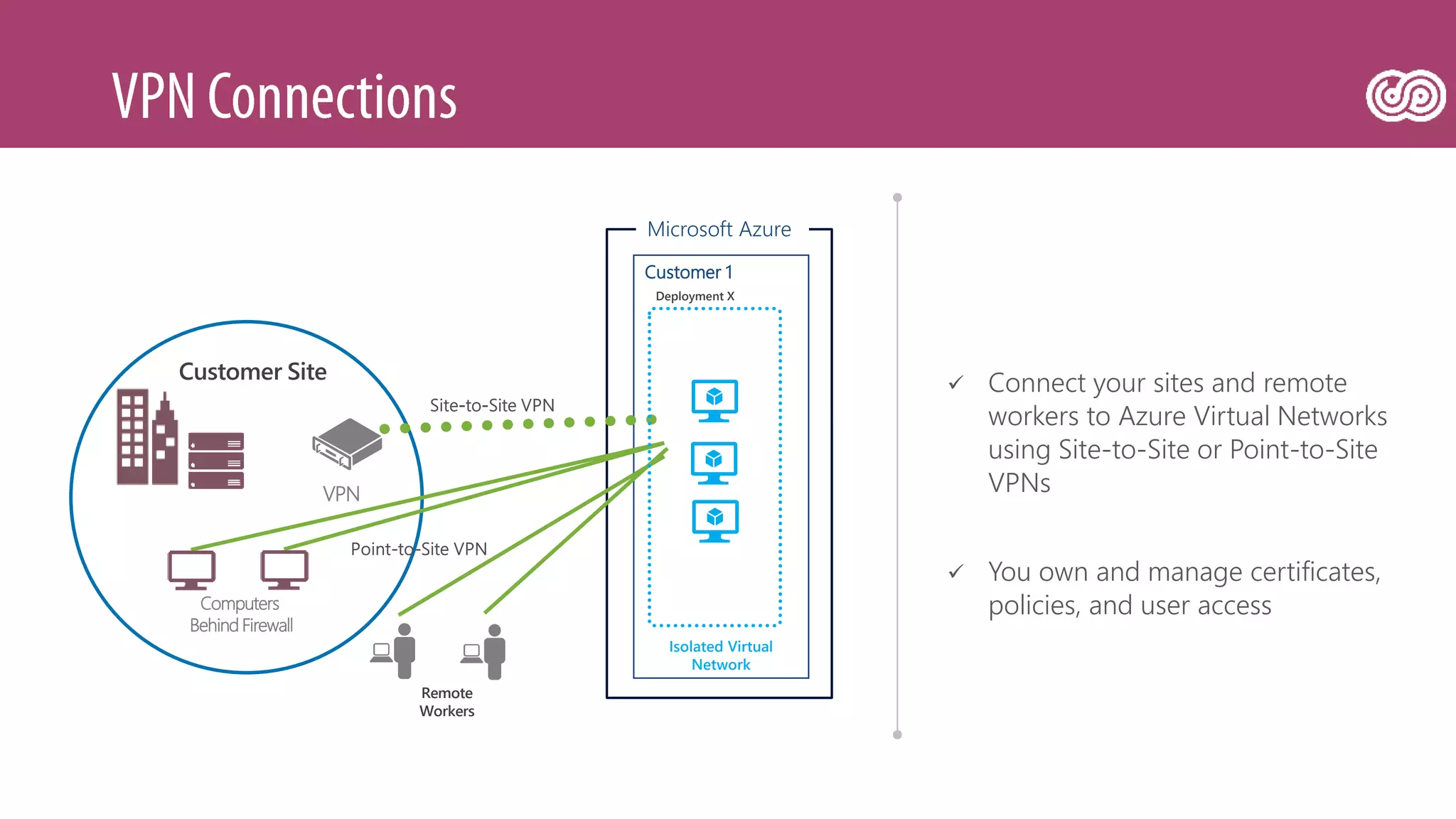
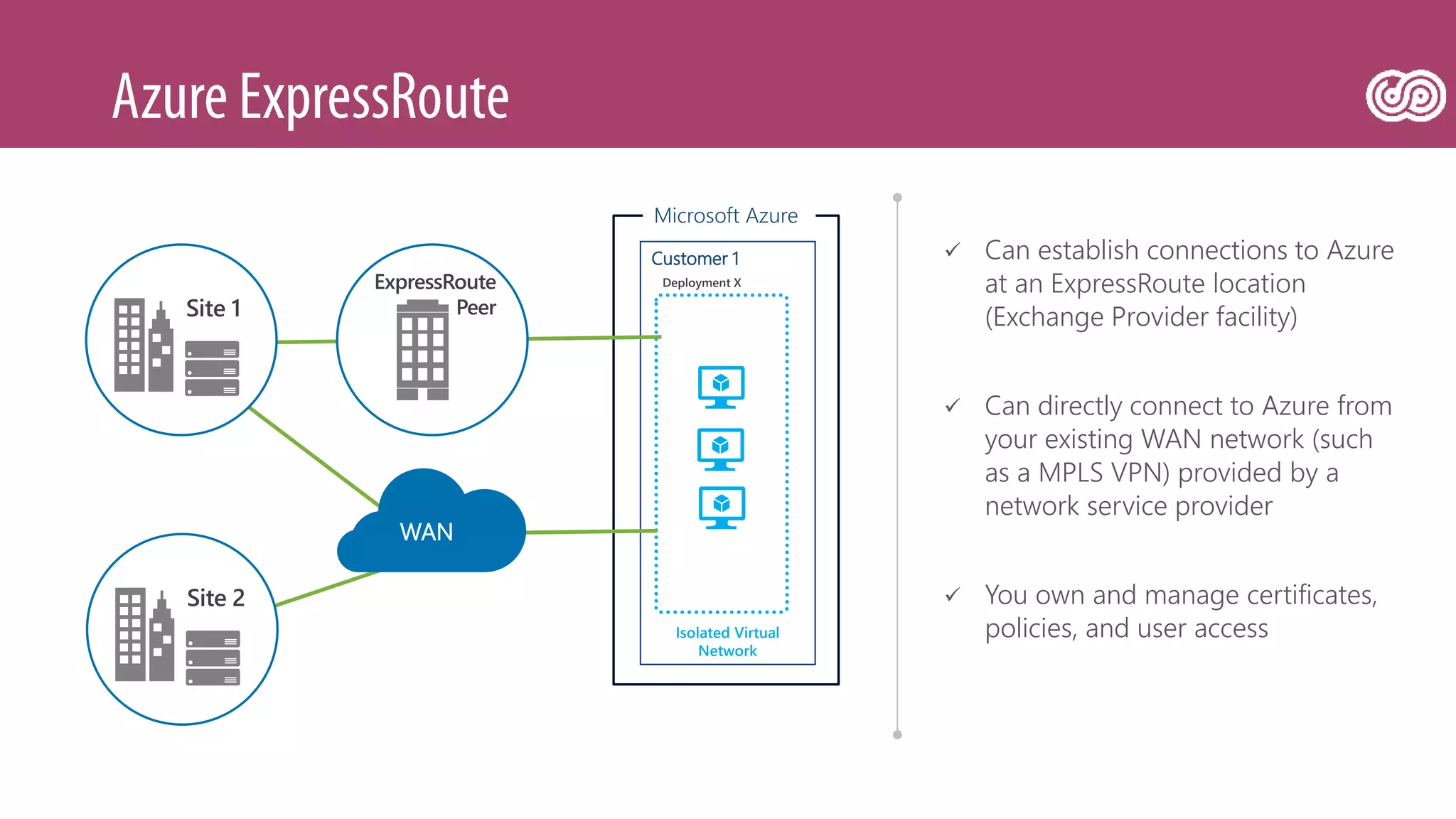
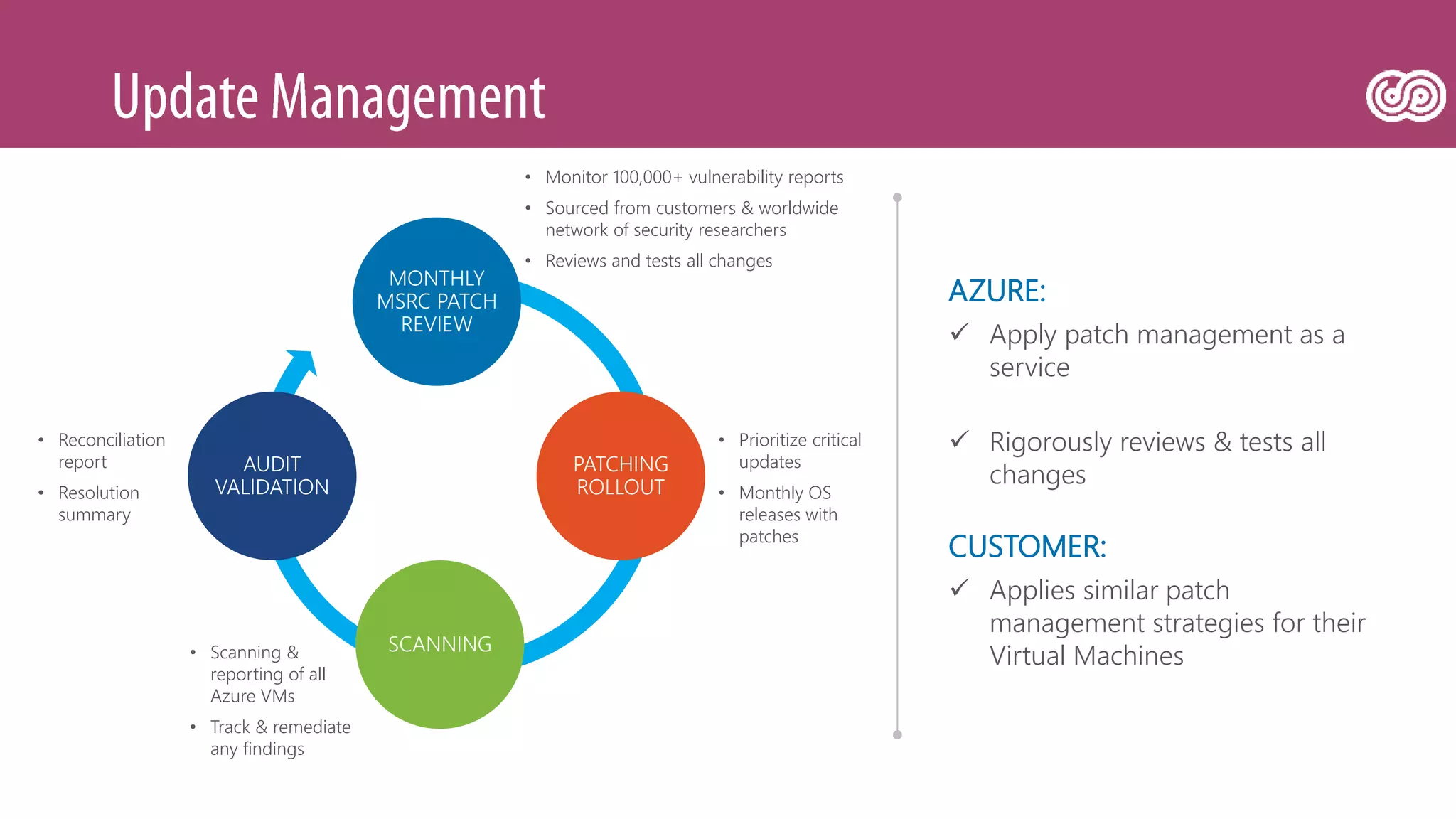
The document outlines Microsoft's Azure platform security measures, emphasizing data confidentiality, integrity, and availability through advanced encryption, multi-factor authentication, and compliance with regulations. It details various services such as Azure Active Directory, data protection during transit and at rest, and virtual network security features like VPN and ExpressRoute. Additionally, it covers proactive threat detection and patch management to safeguard customer environments against vulnerabilities.






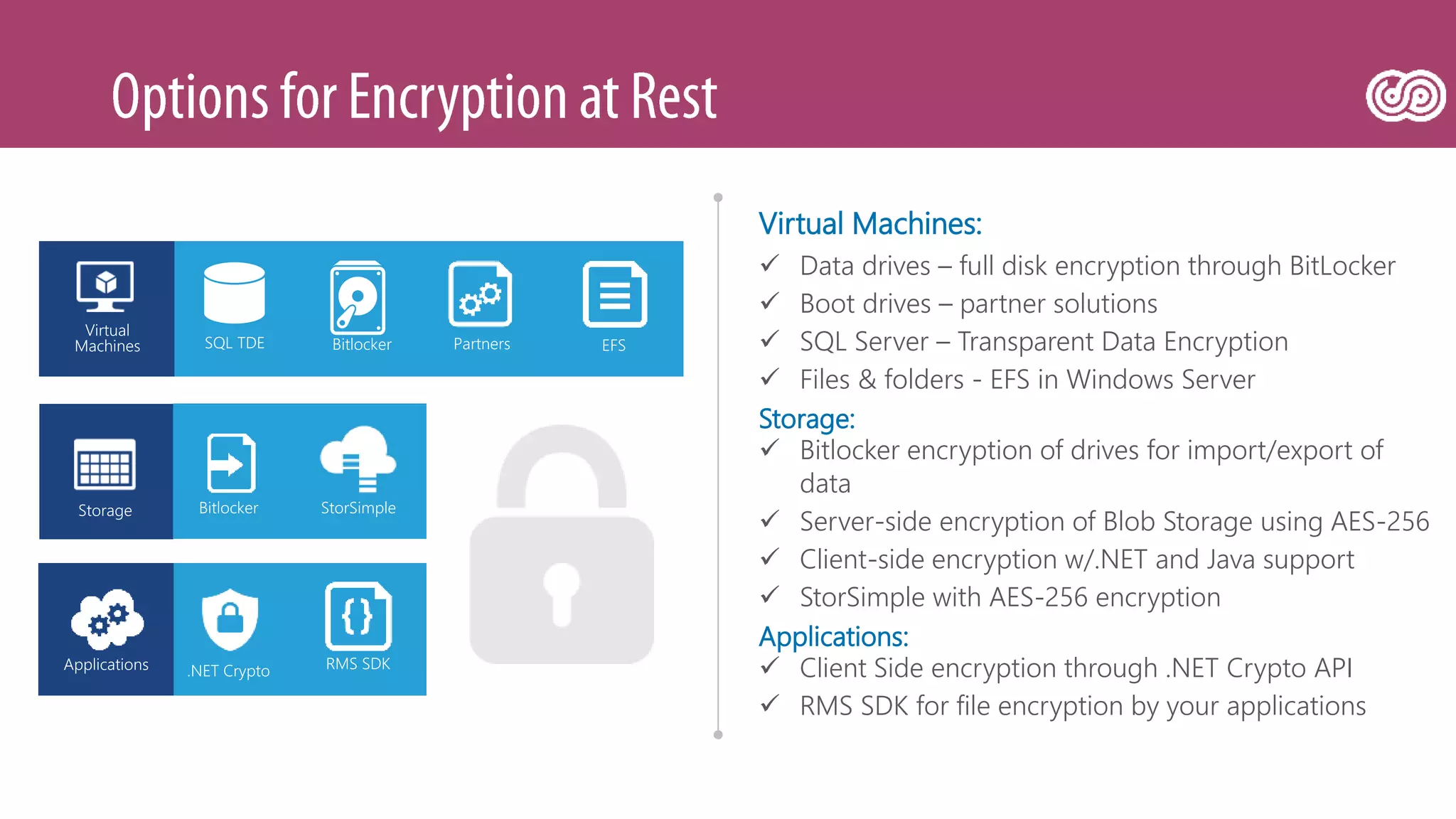



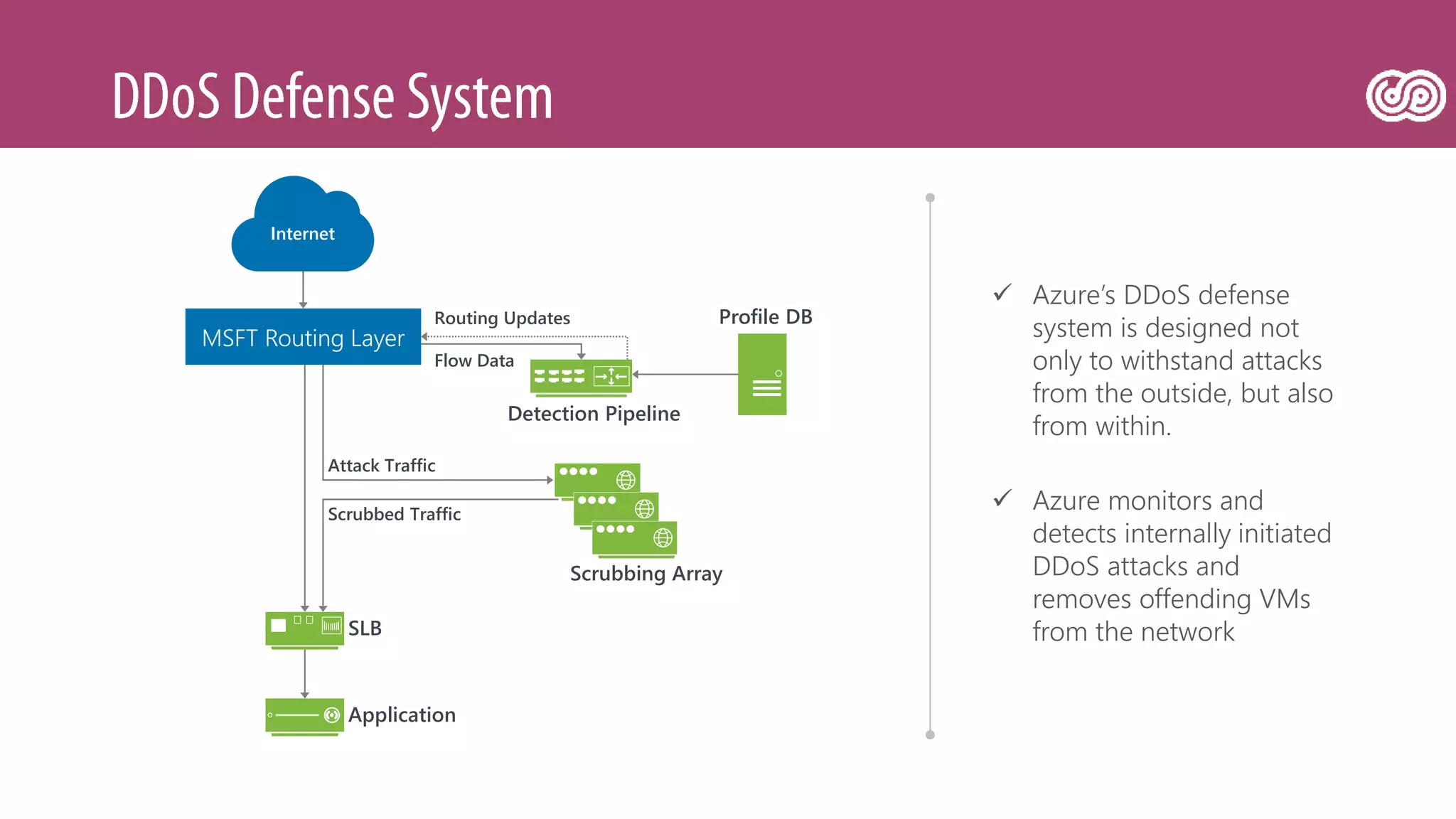

![[Toroman/Kranjac] Red Team vs. Blue Team in Microsoft Cloud](https://image.slidesharecdn.com/fs0fswrr36f3q9puu3u6-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121949/75/Toroman-Kranjac-Red-Team-vs-Blue-Team-in-Microsoft-Cloud-31-2048.jpg)
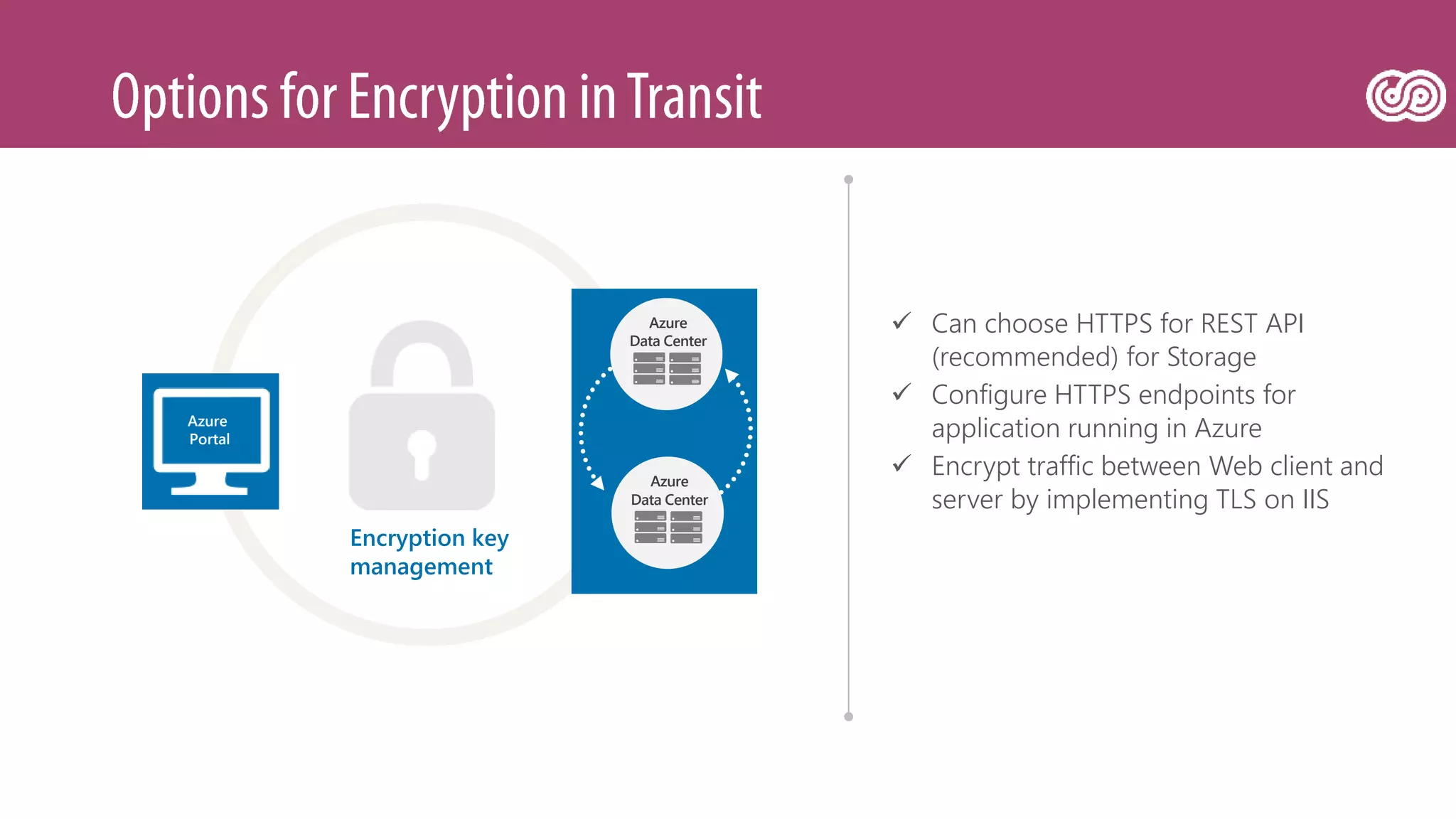
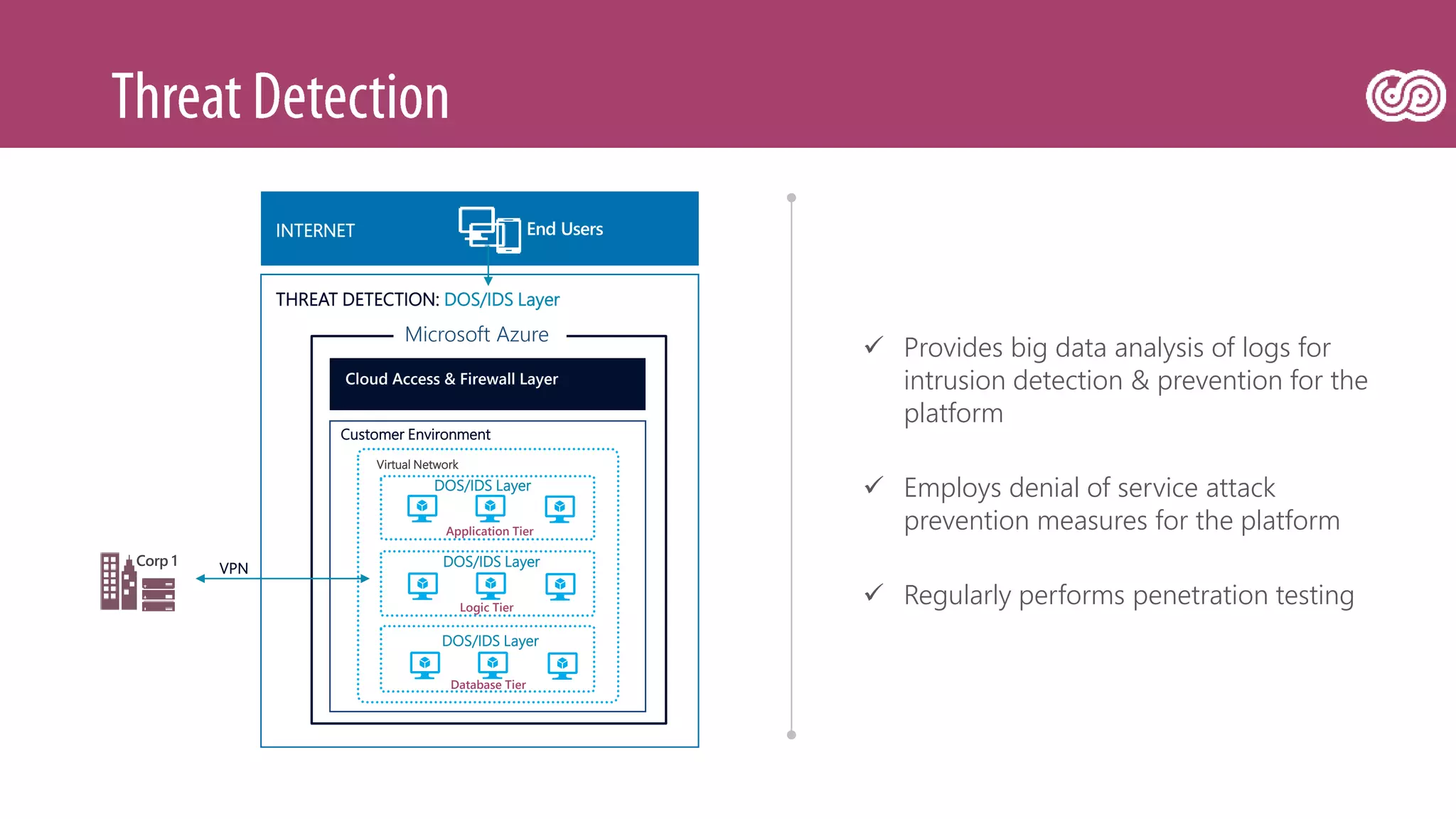
![[Toroman/Kranjac] Red Team vs. Blue Team in Microsoft Cloud](https://image.slidesharecdn.com/fs0fswrr36f3q9puu3u6-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121949/75/Toroman-Kranjac-Red-Team-vs-Blue-Team-in-Microsoft-Cloud-32-2048.jpg)
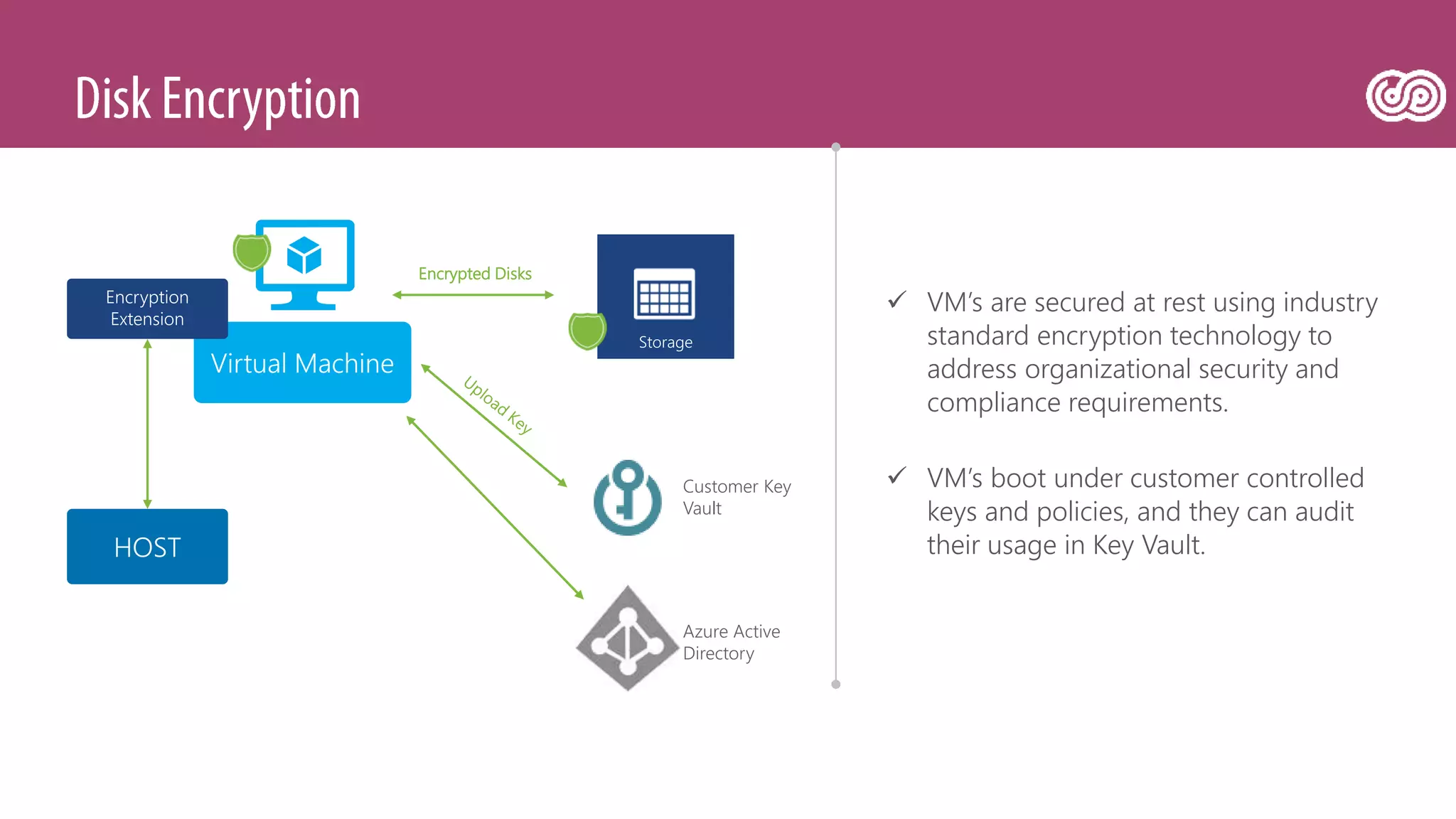
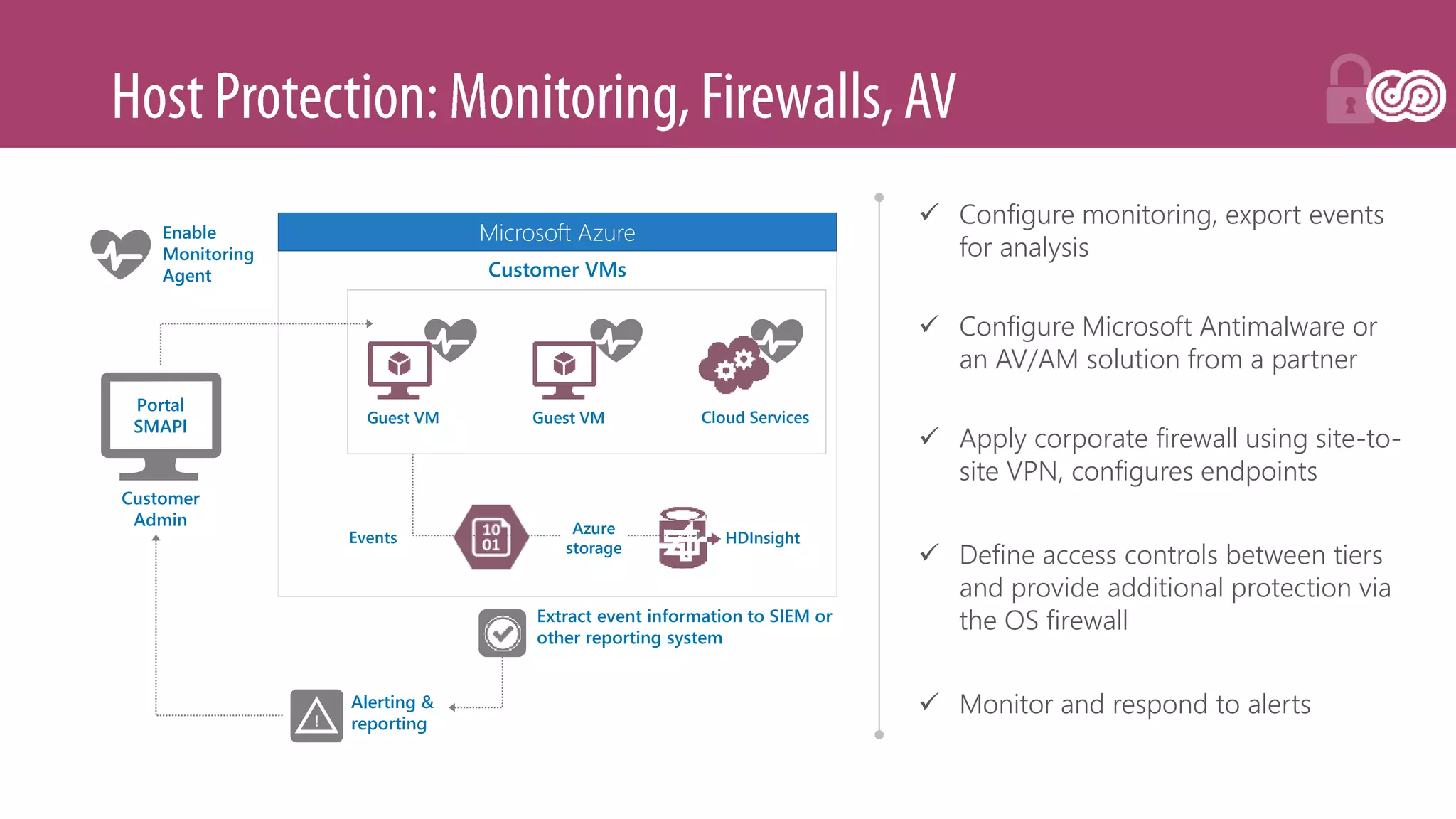
![[Toroman/Kranjac] Red Team vs. Blue Team in Microsoft Cloud](https://image.slidesharecdn.com/fs0fswrr36f3q9puu3u6-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121949/75/Toroman-Kranjac-Red-Team-vs-Blue-Team-in-Microsoft-Cloud-33-2048.jpg)