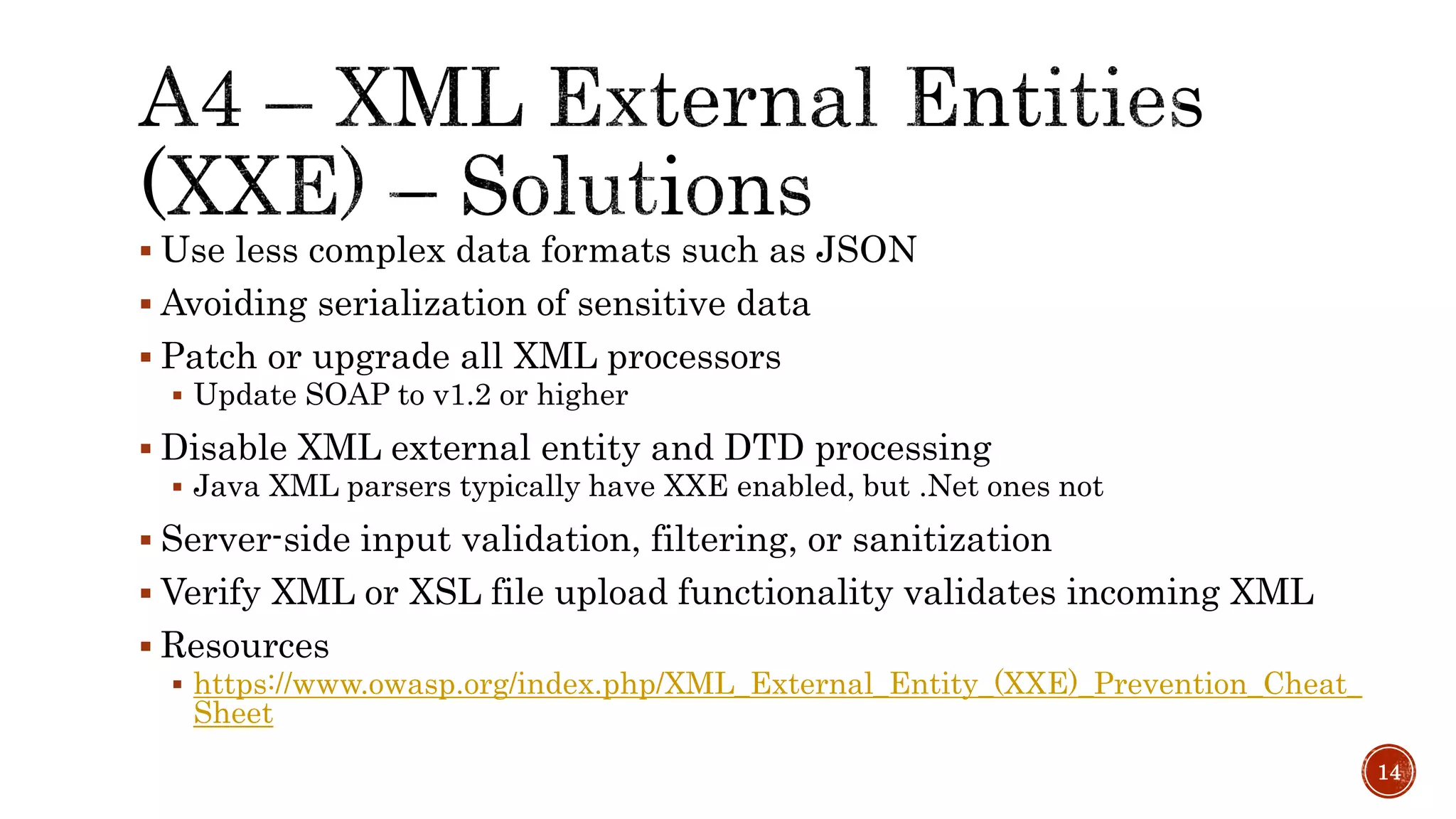
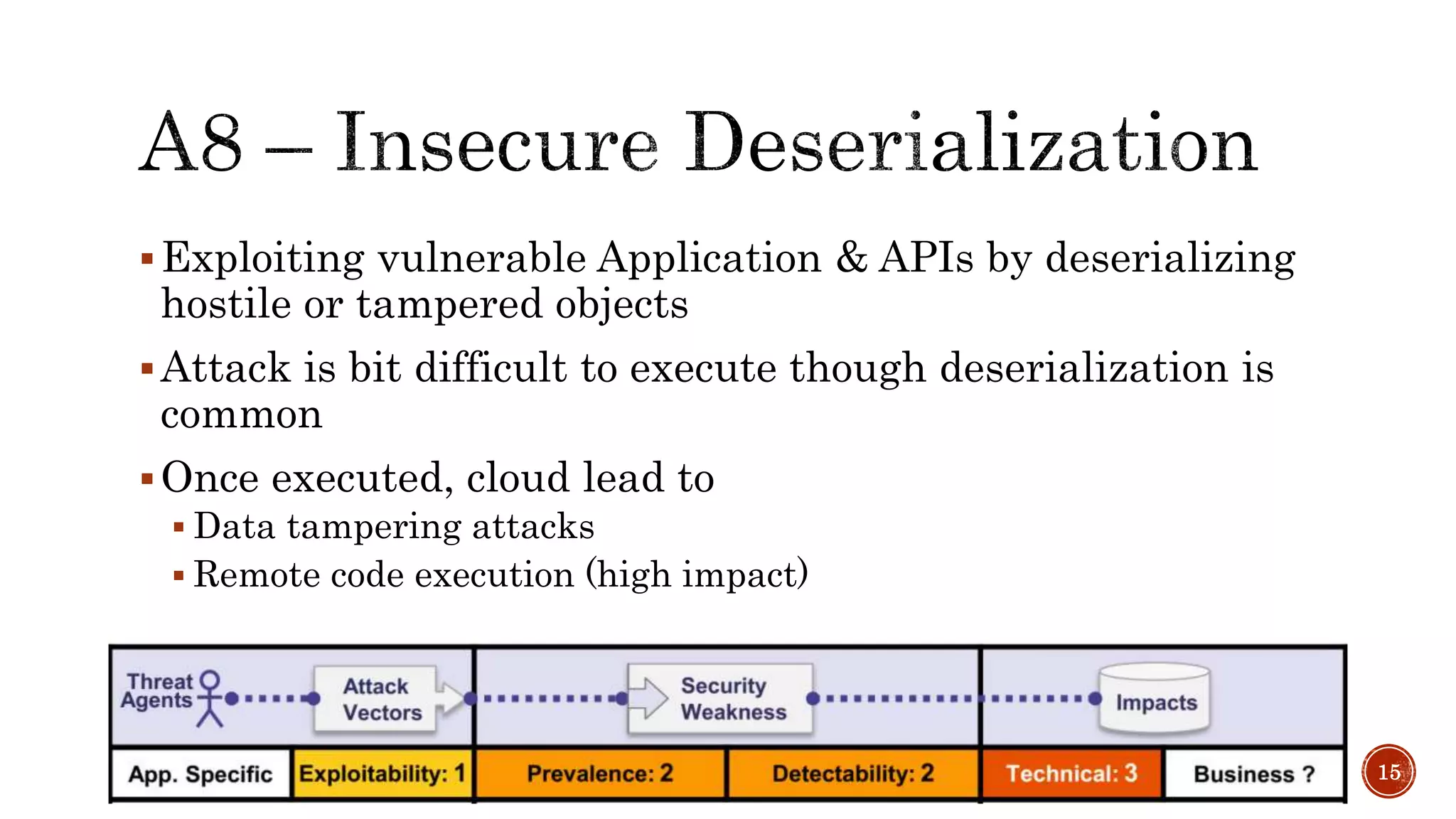
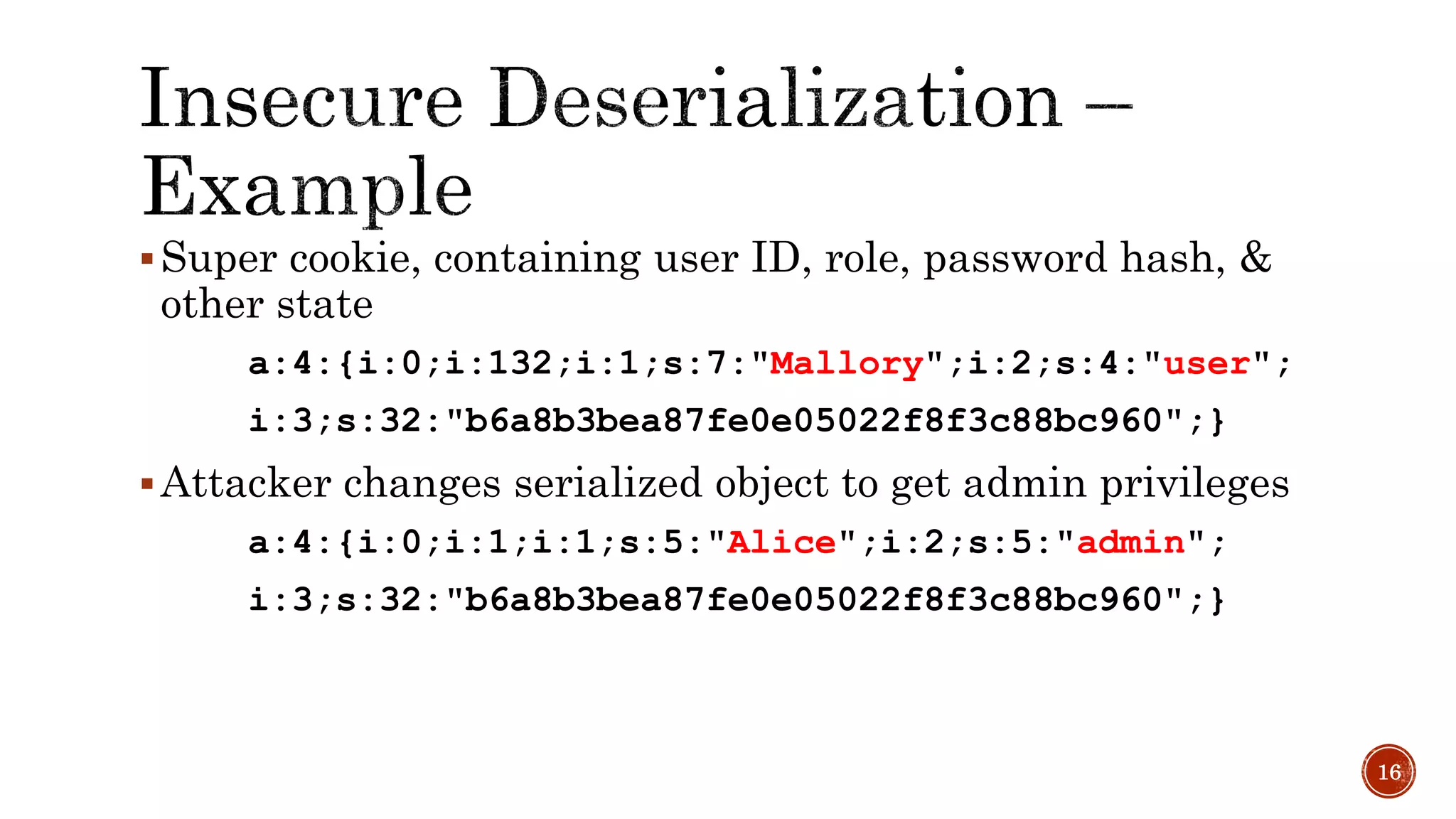
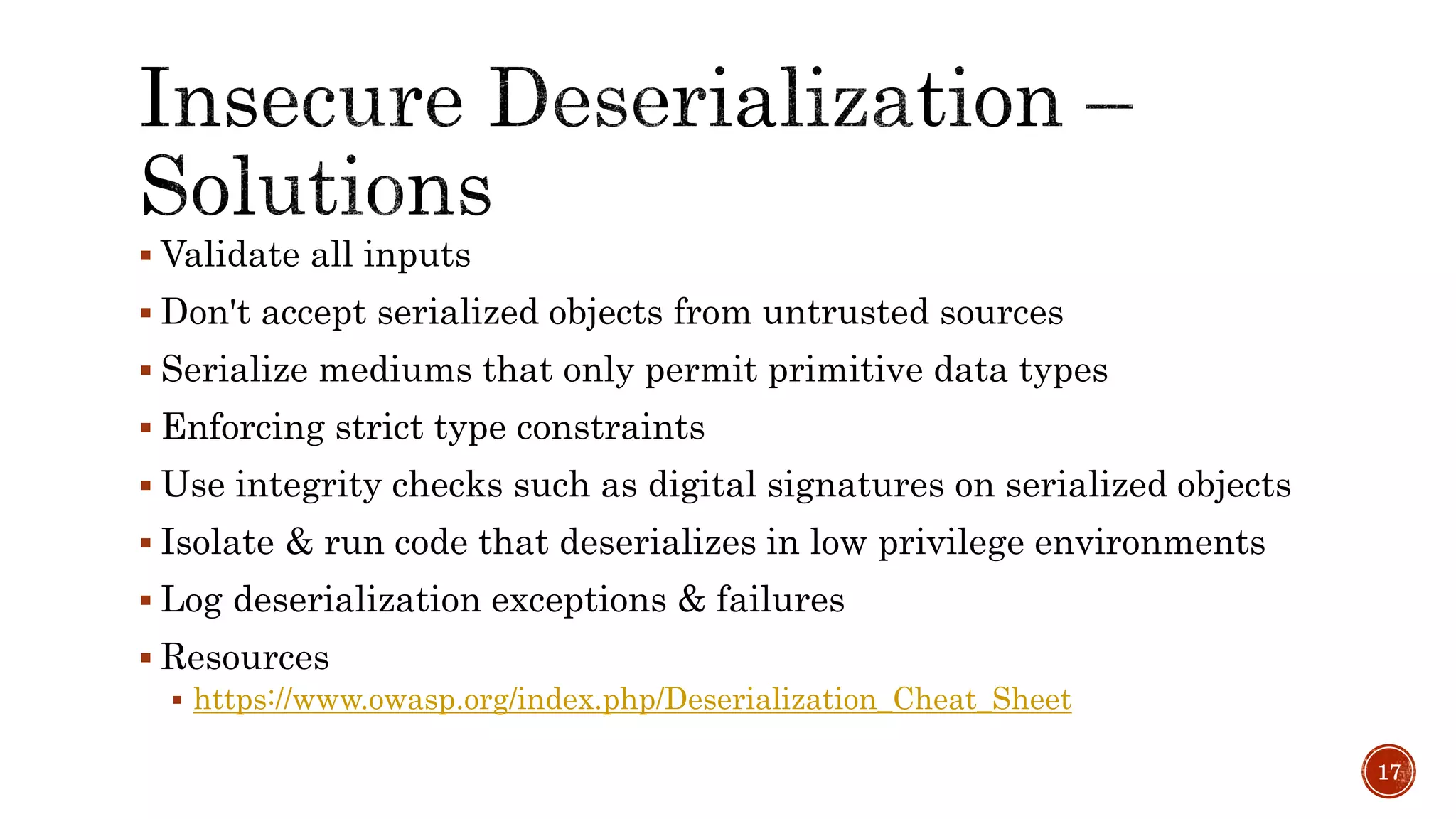
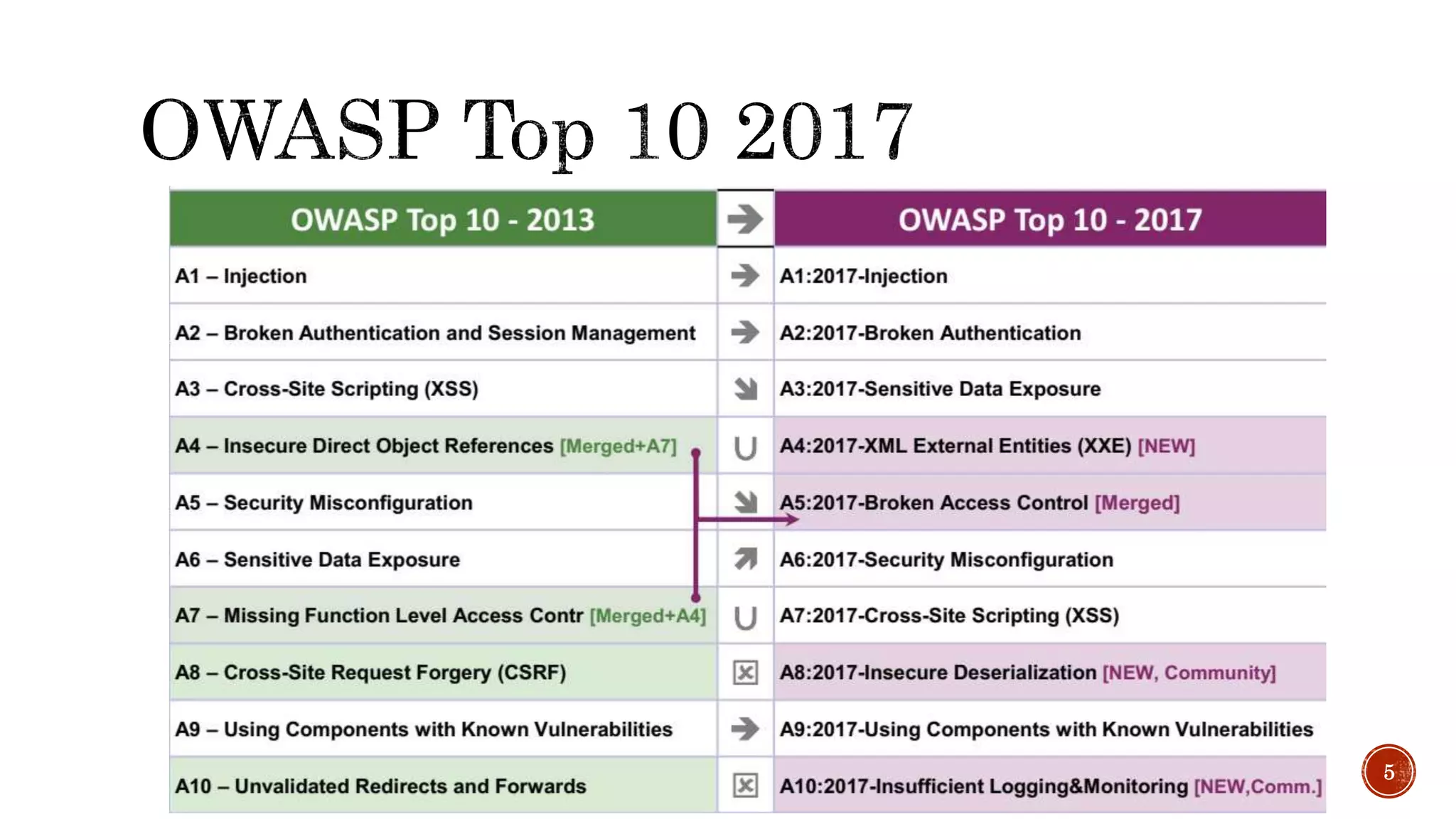
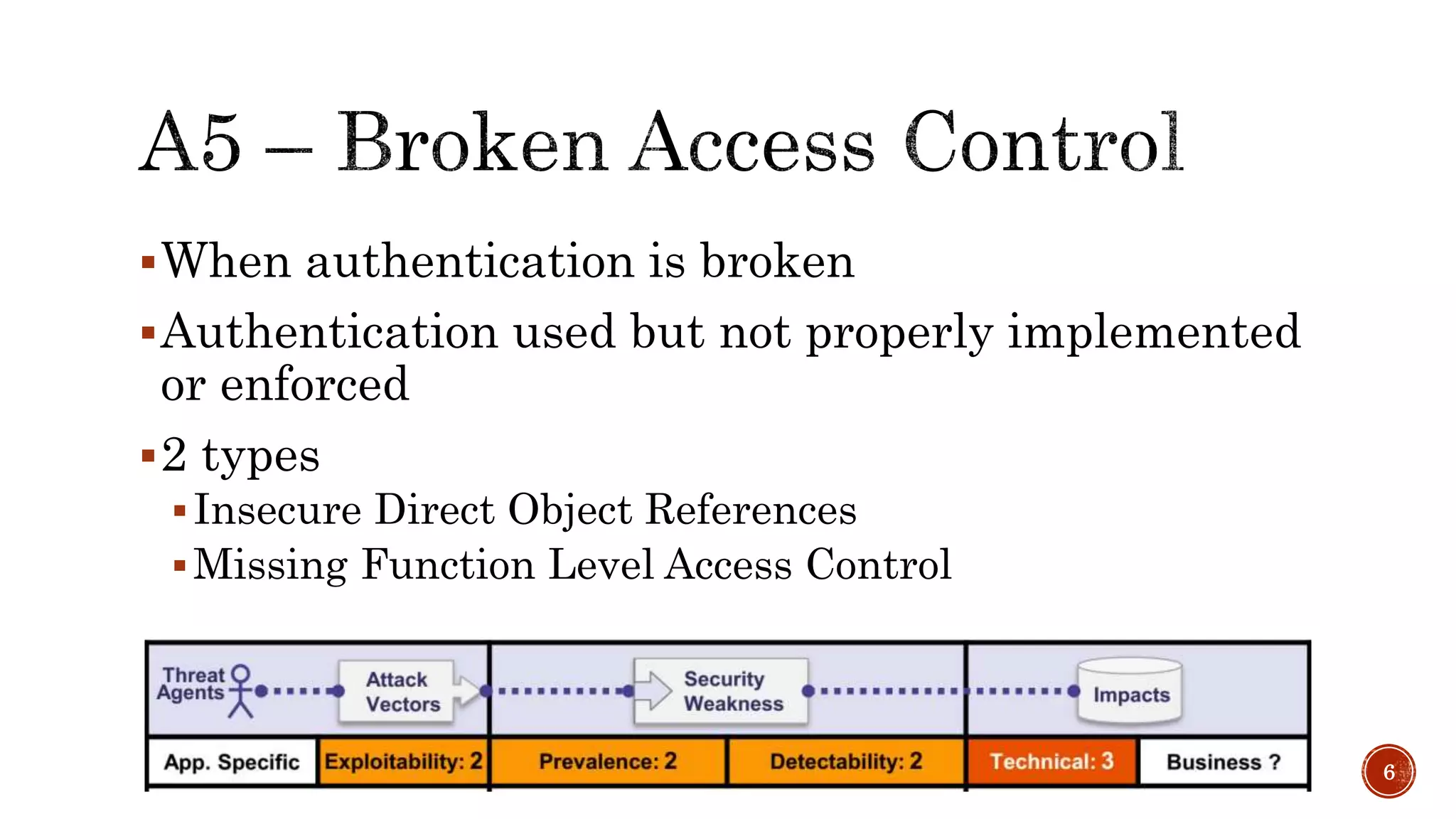
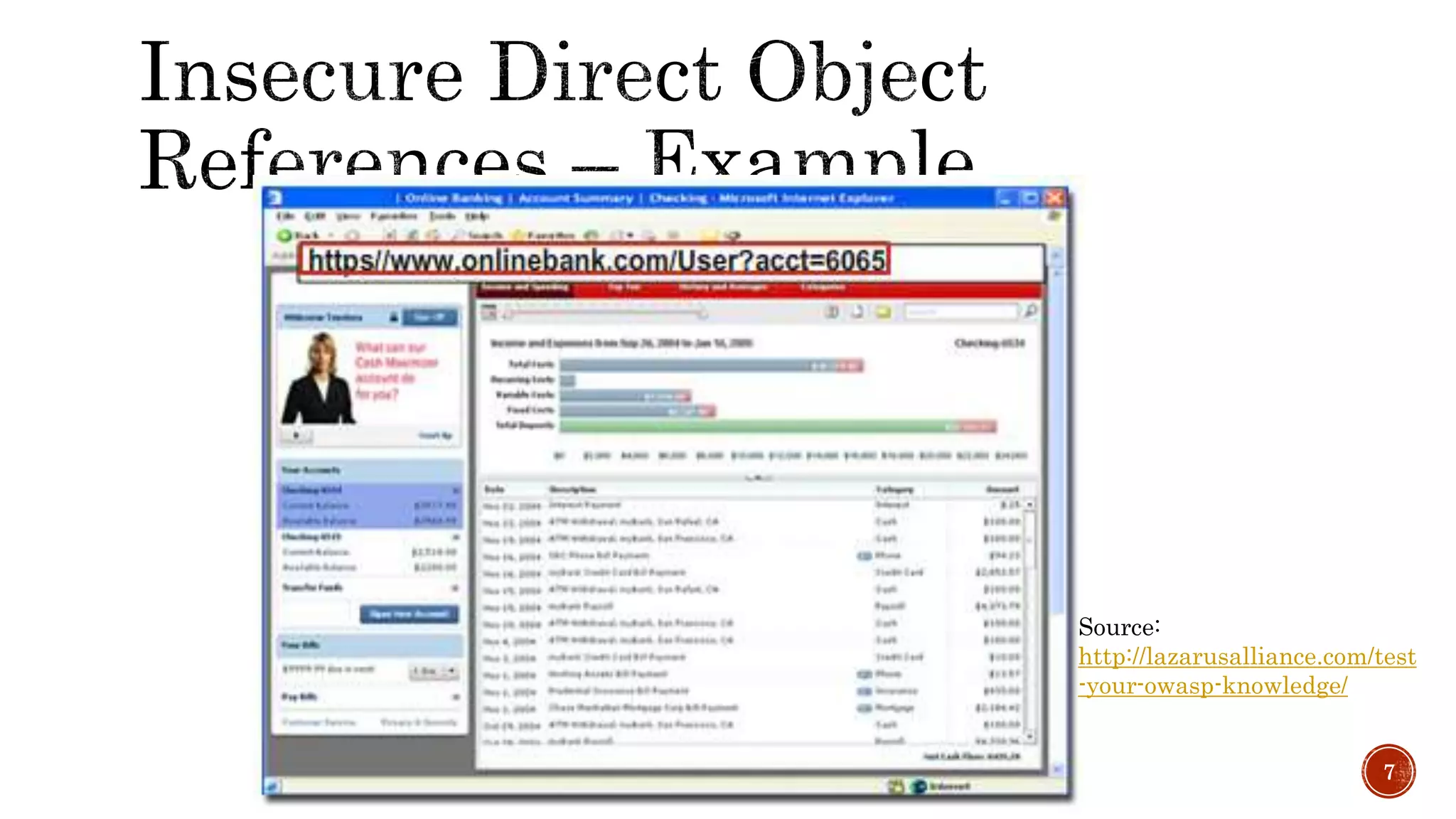
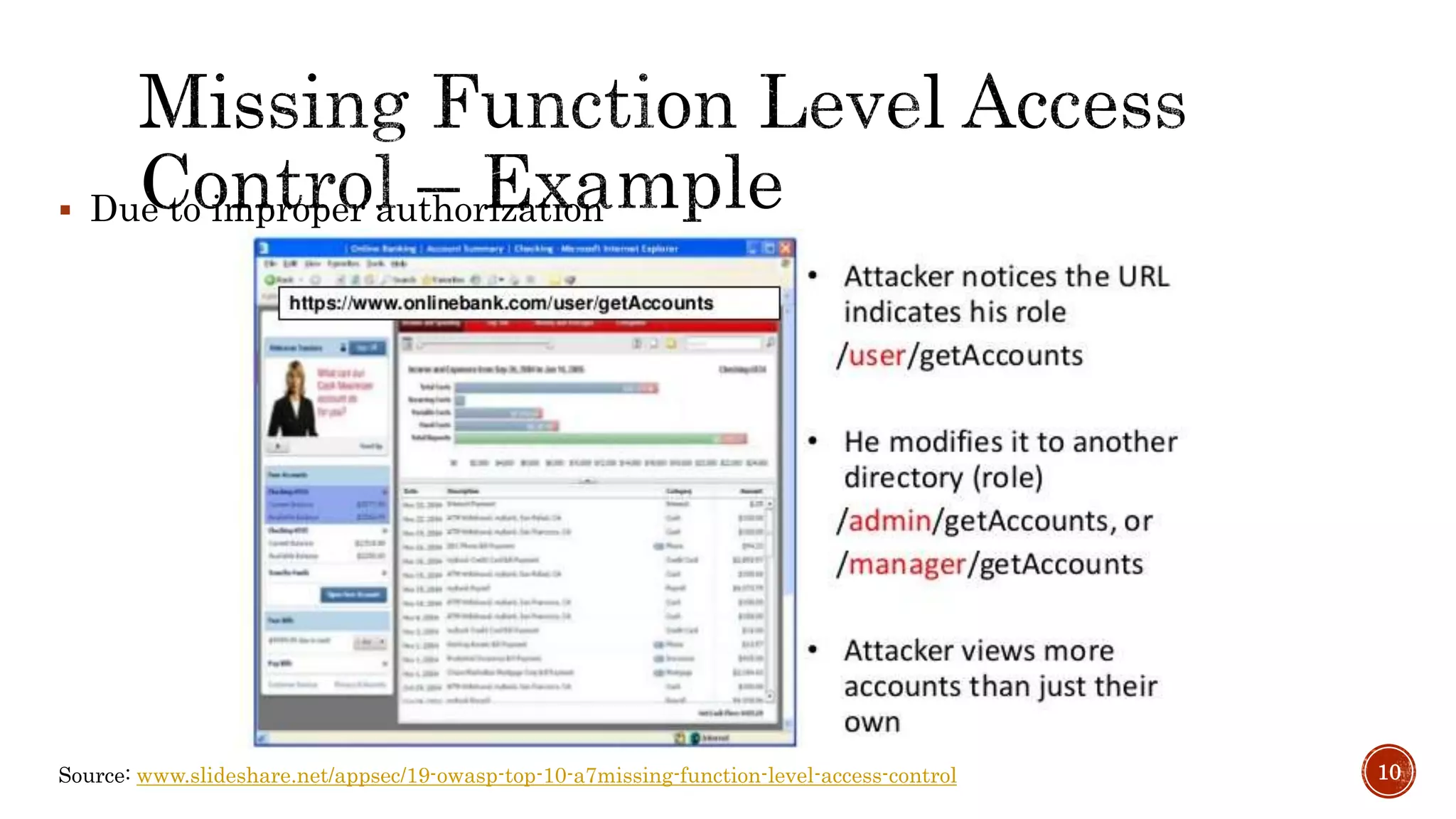
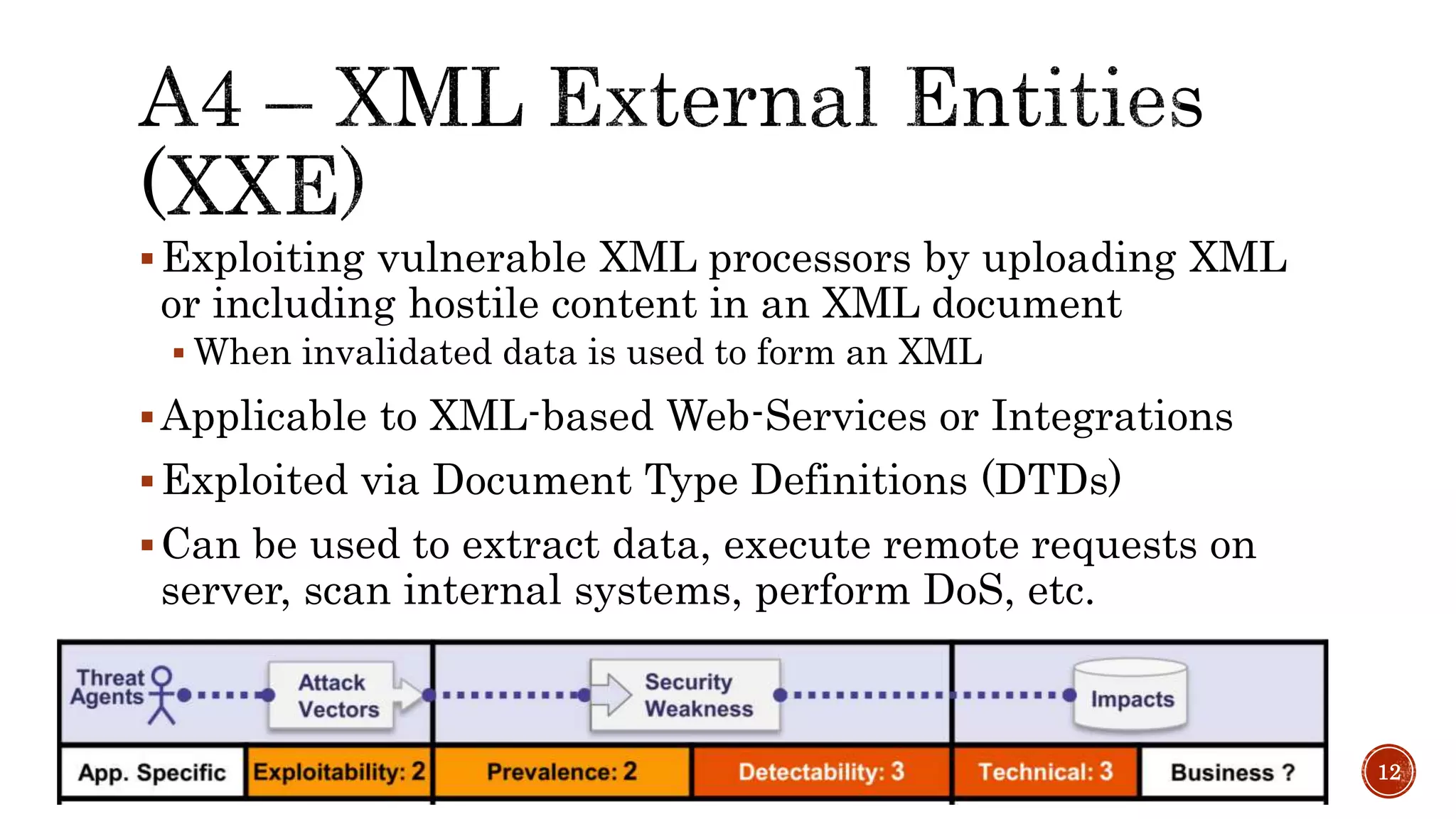
The document discusses the OWASP Top 10 - 2017, which outlines the most critical web application security risks based on global expert feedback. It emphasizes the importance of implementing proper authentication, authorization, and monitoring practices to mitigate risks like insecure direct object references and XML external entity vulnerabilities. The document also provides resources and recommendations for improving security measures in web applications.





![<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >
]>
<foo>&xxe;</foo>
13
<!ENTITY xxe SYSTEM "https://192.168.1.1/private">
<!ENTITY xxe SYSTEM "file:///dev/random">](https://image.slidesharecdn.com/owasptop102017-newvulnerabilities-180322152914/75/OWASP-Top-10-2017-New-Vulnerabilities-13-2048.jpg)