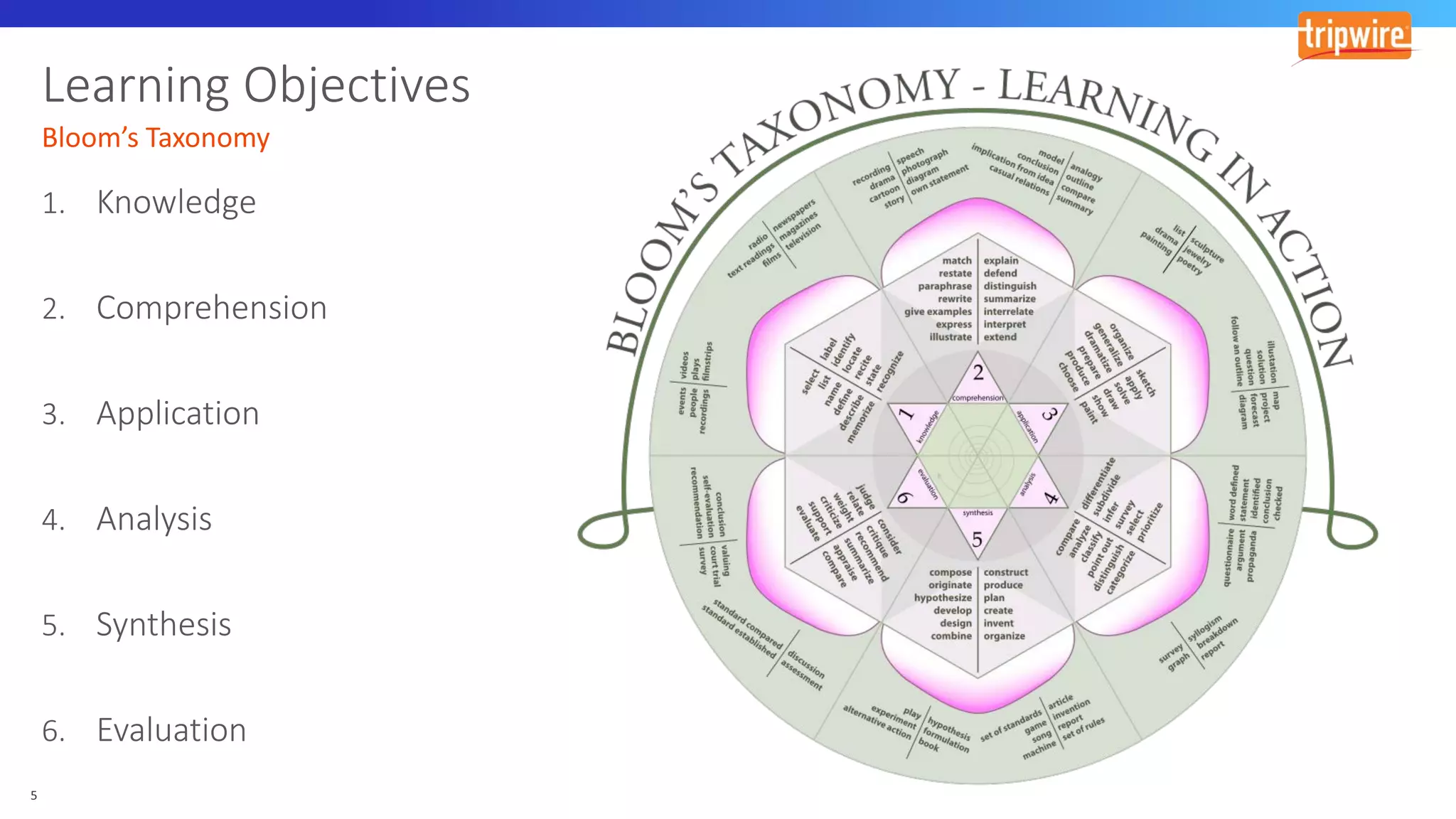
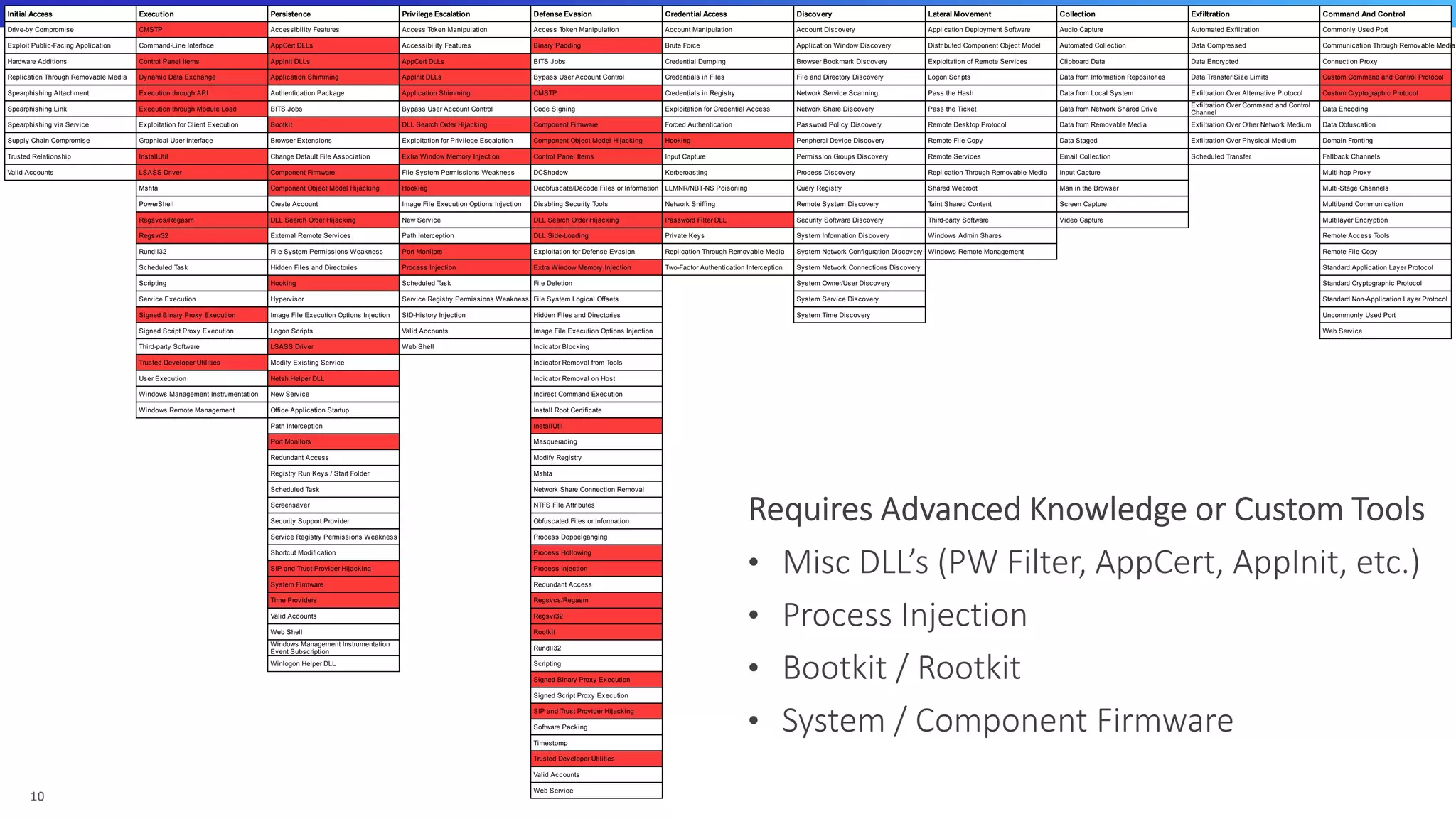
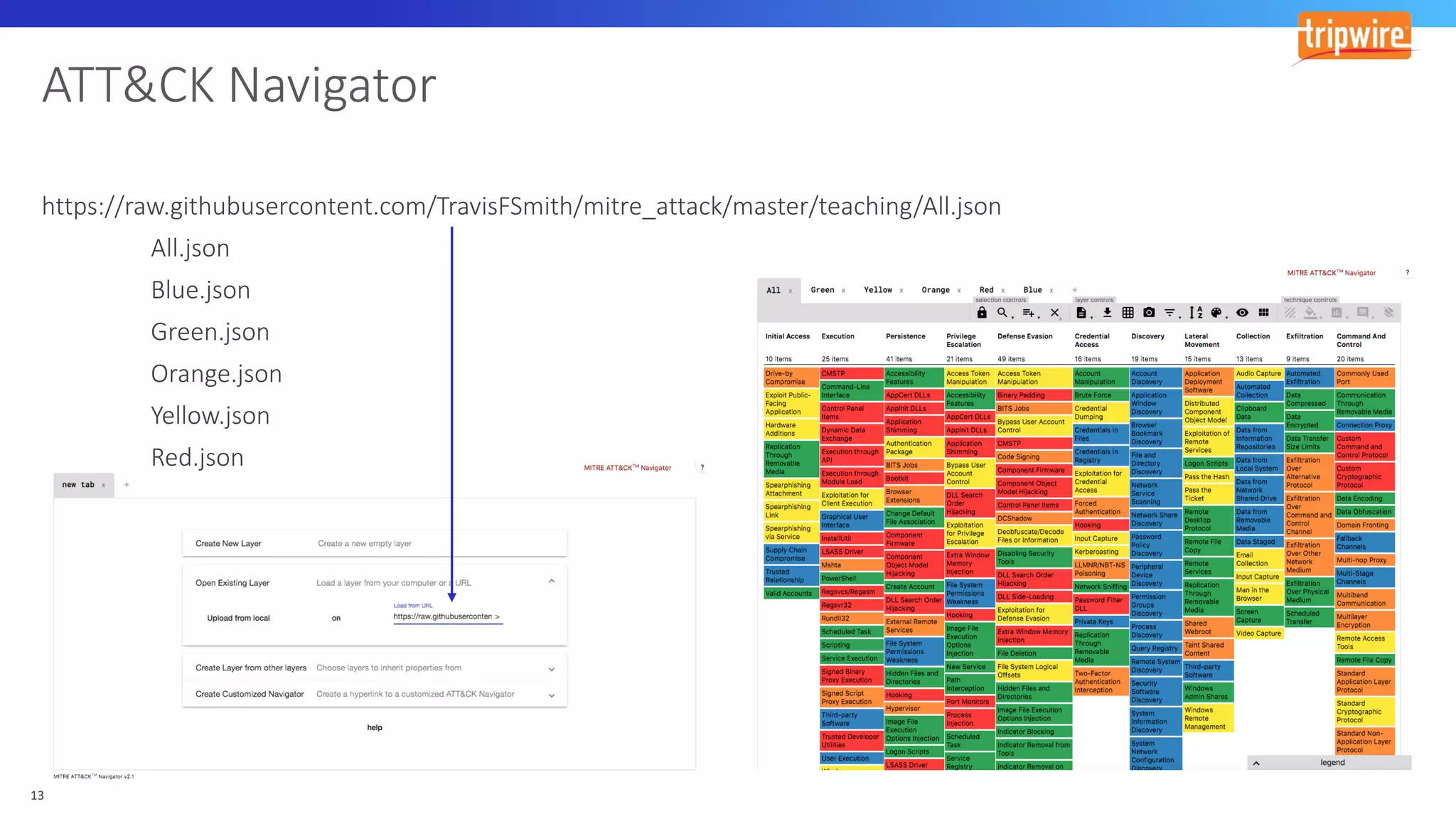
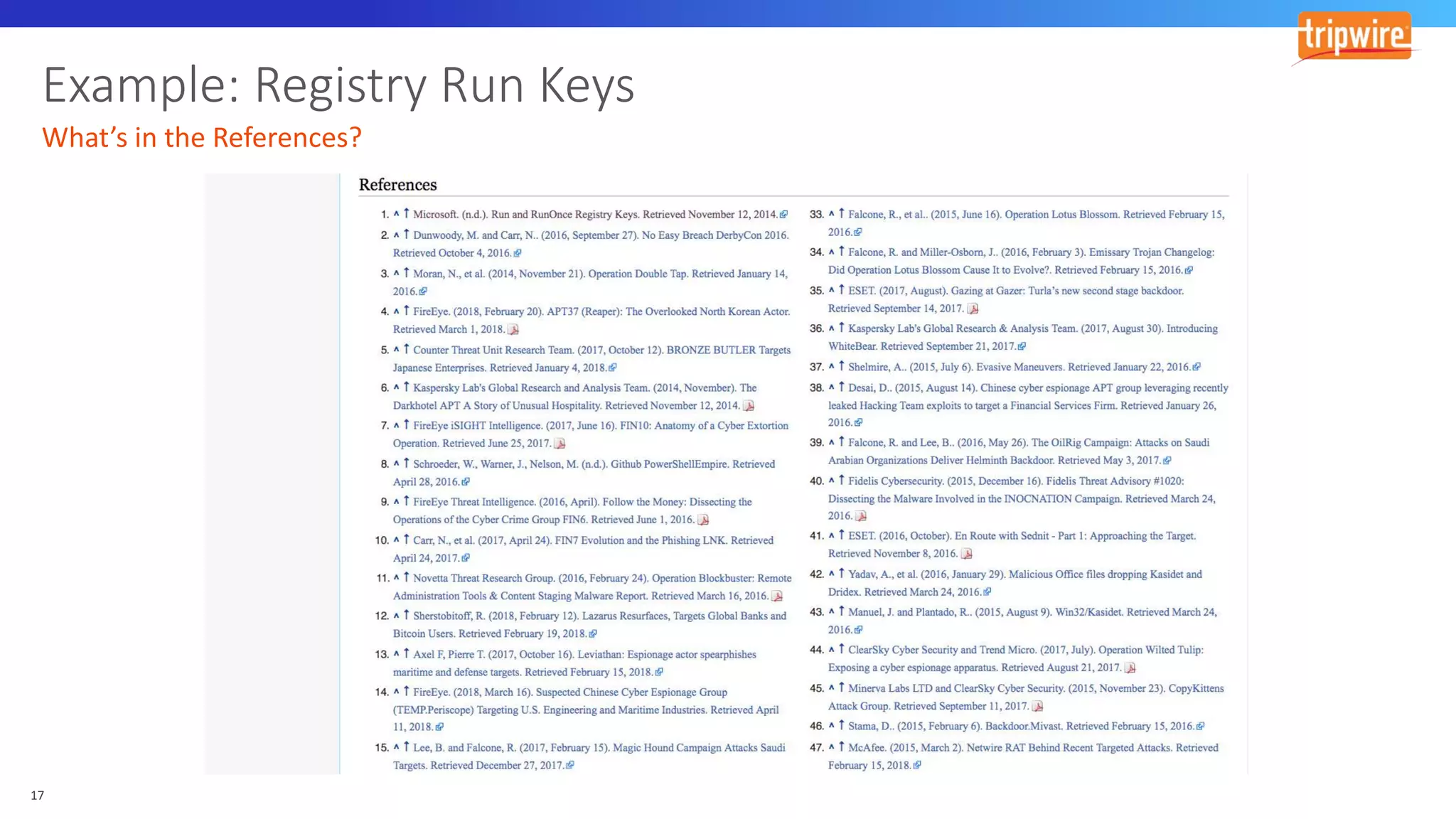
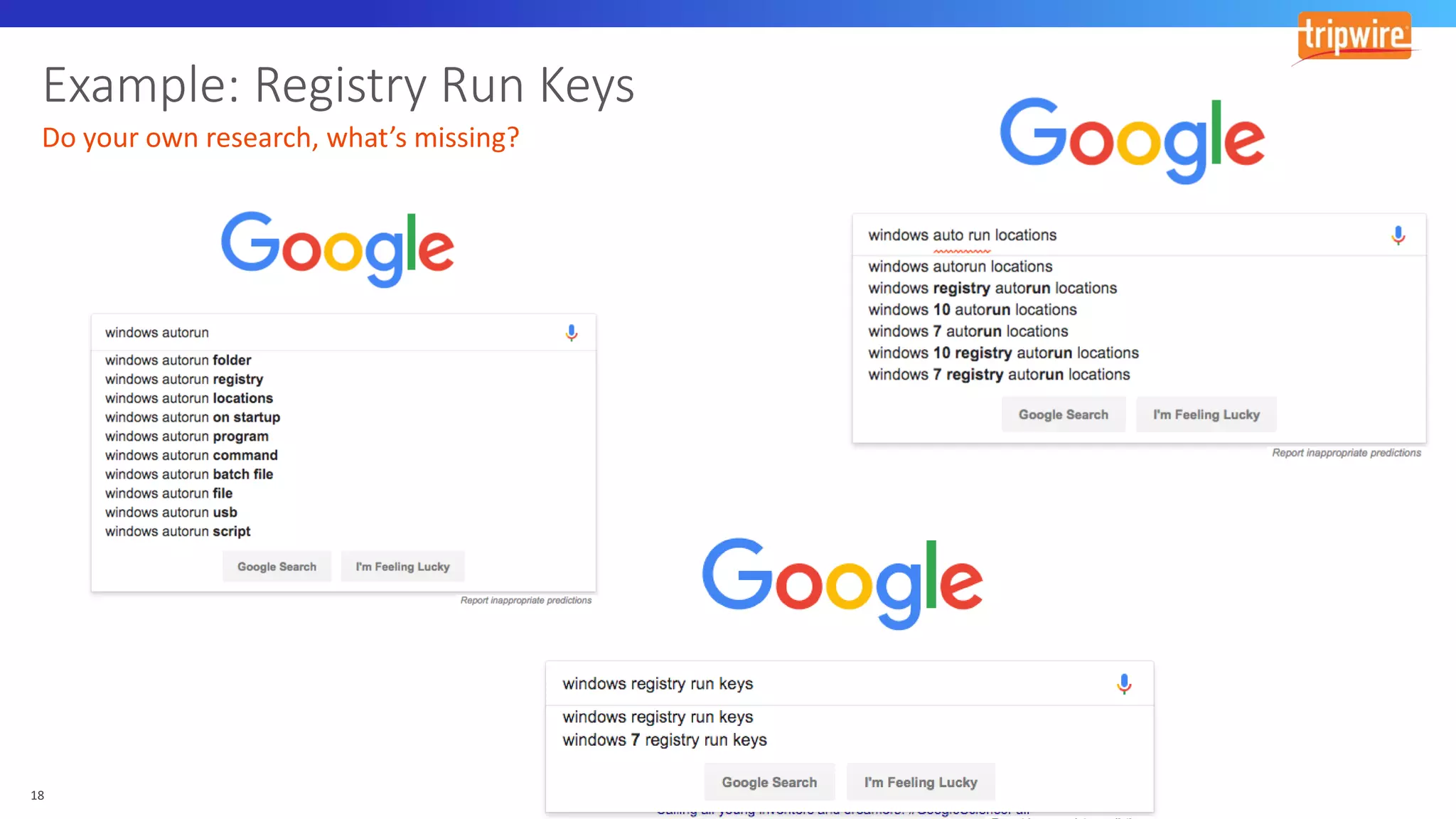
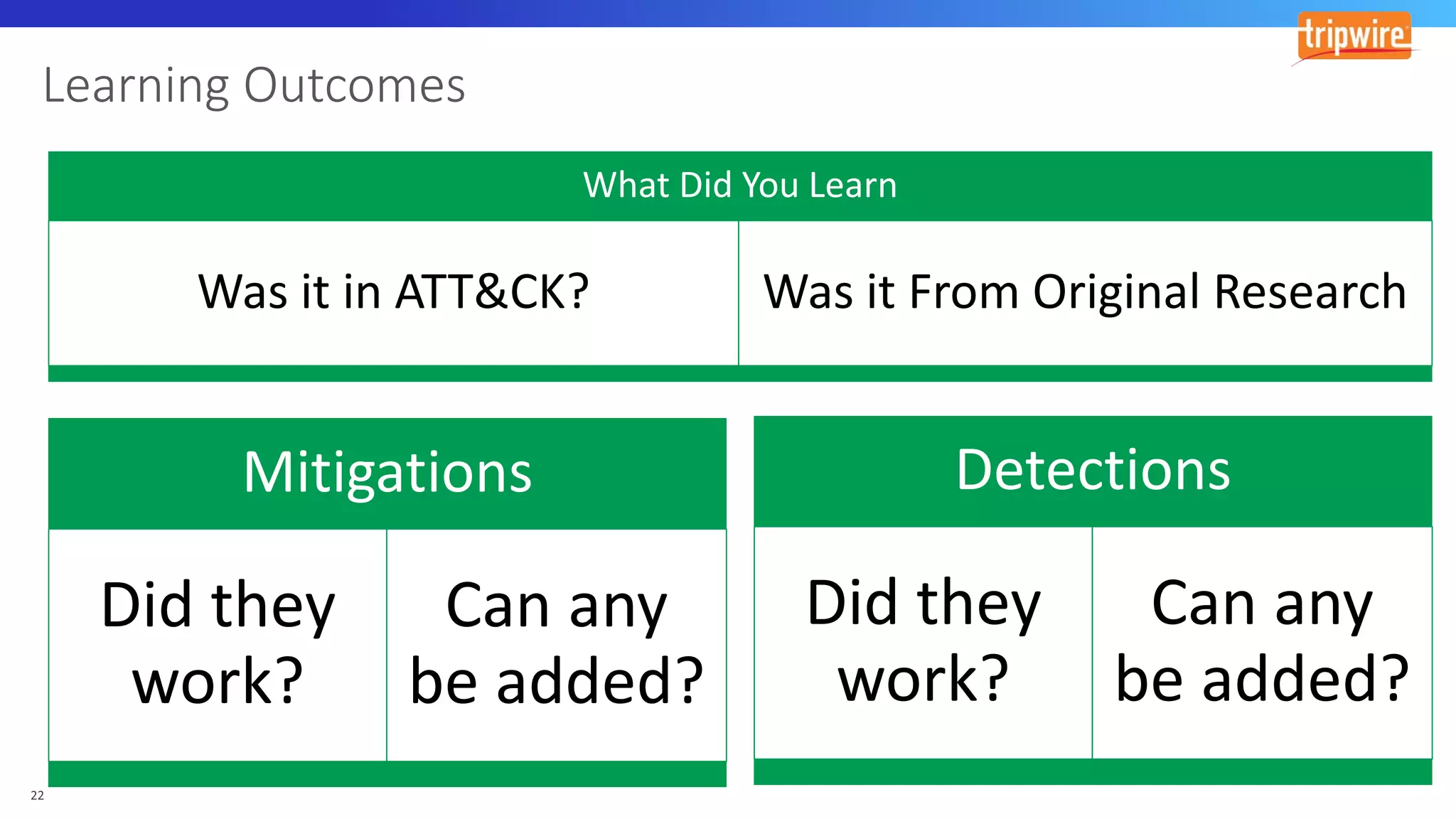
The document discusses various cyber exploitation techniques utilized by attackers, outlining their complexity and requirements for successful execution. It emphasizes the importance of understanding operating systems and potential infrastructures needed for methods such as process injection, web shell exploitation, and privilege escalation. Additionally, it highlights the procedures for initial access, lateral movement, and data exfiltration, while also mentioning the challenges and defenses against these techniques.