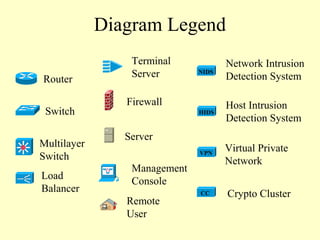
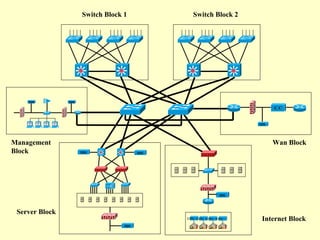
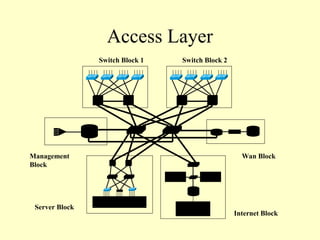
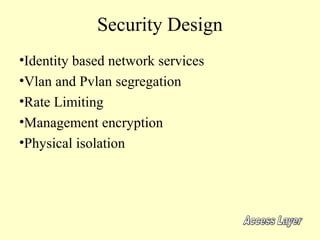
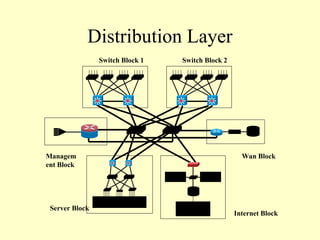
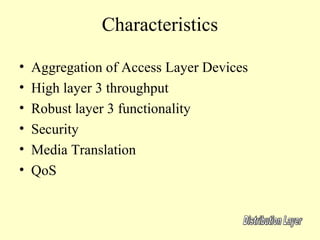
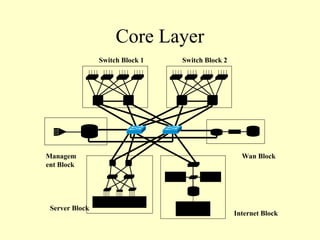
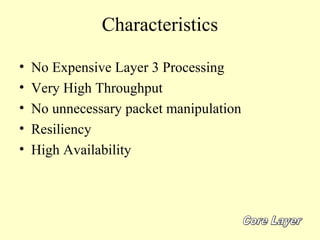
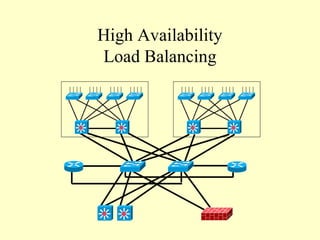
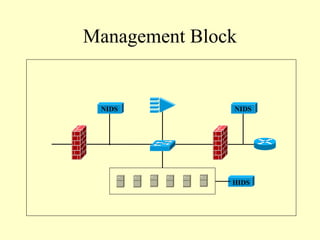
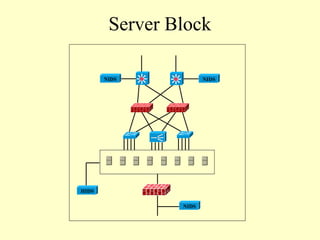
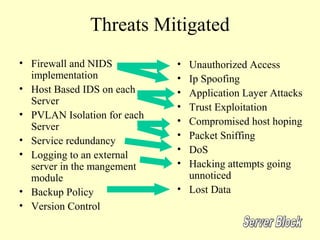
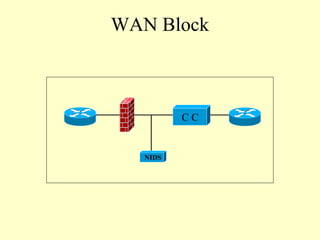
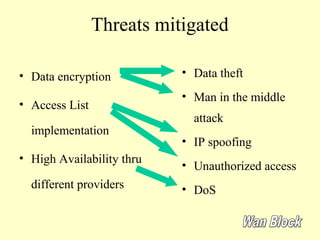
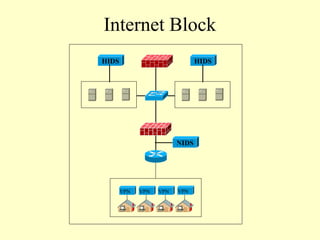
This document outlines a secure network design with layered security. It proposes a modular design with separate blocks for management, servers, WAN access, and the internet. Each block utilizes devices like firewalls, intrusion detection systems, and load balancers for security. Key recommendations include network segmentation, access controls, encryption, logging, and redundancy to mitigate threats.