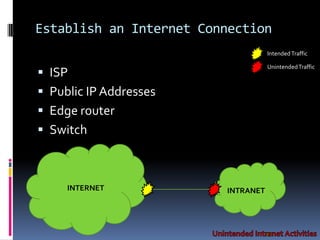
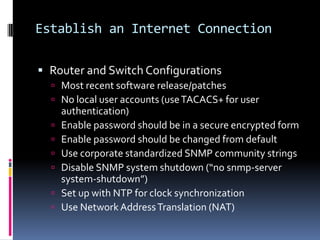
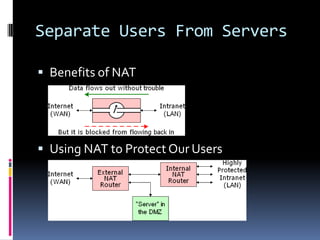
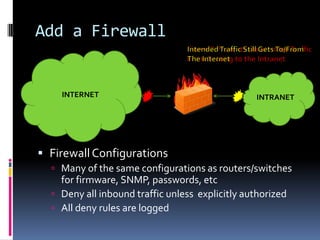
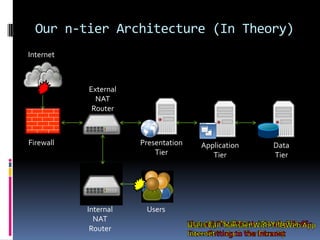
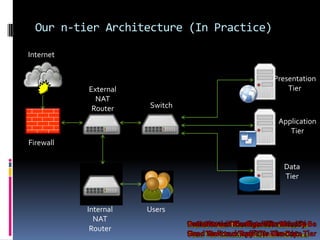
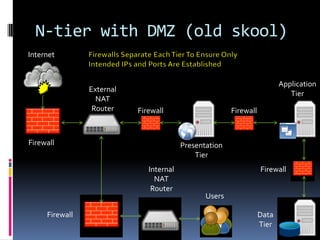
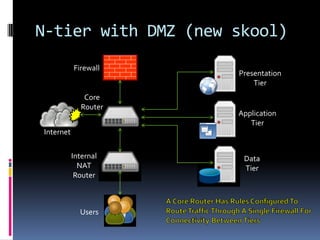
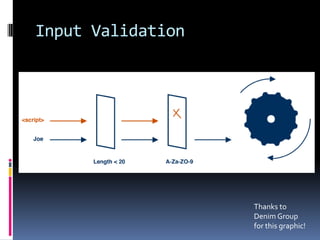
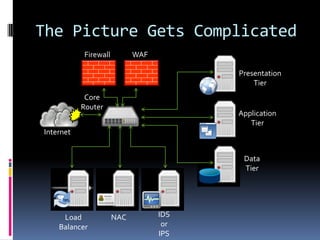
The document by Josh Sokol discusses best practices for architecting secure web systems, emphasizing a holistic approach to security that integrates various roles such as network, application, and database security. It outlines fundamental security principles and frameworks, such as least privilege, defense-in-depth, and the importance of proper planning and training for developers to mitigate security flaws. Additionally, it covers specific security measures for network configuration, server hardening, application development, and compliance with standards like PCI.